What is biometrics + is sensor-based security safe?

Biometrics is a measurement based on our physical and behavioral characteristics. And many modern devices have these biometrics-based security systems—as well as a few risks associated with them. Follow this guide to learn more about biometrics, and explore how Norton™ 360 with LifeLock™ Select can help protect your device and reduce the risk of someone accessing your biometric data.
What is biometrics?
You can break down the term "biometrics" to get a better understanding of what it is. “Bio” stems from biology, while “metrics” are units of measurement. Put the two together and you have biometrics, which measure the unique physical and behavioral characteristics of a living creature.
Biometric data is information that can help identify you based on your physical or behavioral traits. For example, hospitals can use biometric data to identify patients and monitor their well-being. Companies like Apple add biometric sensors to many of their devices that can identify users via fingerprint and facial recognition software.
How do biometrics work?
When using biometrics on your personal devices, the device will first ask you to complete an initial scan to build a profile around your biometrics. Your biometric data will then be collected and stored for later use. From that point on, your device will compare all future login attempts with the data linked to your profile.
For example, a fingerprint recognition system will initially ask you to scan different sides of your fingertip. Once this initial scan is complete, you'll be able to quickly log in with a tap of your finger. Two-factor authentication (2FA) can use biometric data to verify your identity, typically via a fingerprint scanner like those found on many smartphones.
The most secure biometric security systems will store data directly on a device and protect it through a process known as encryption. Should you erase the data from your phone or computer, it’s gone forever.
Types of biometric data
Biometrics is based on our behavioral and physiological data. Behavioral biometrics can recognize users based on what they do, while physiological biometrics can detect our attributes. Here are some common examples of both types.
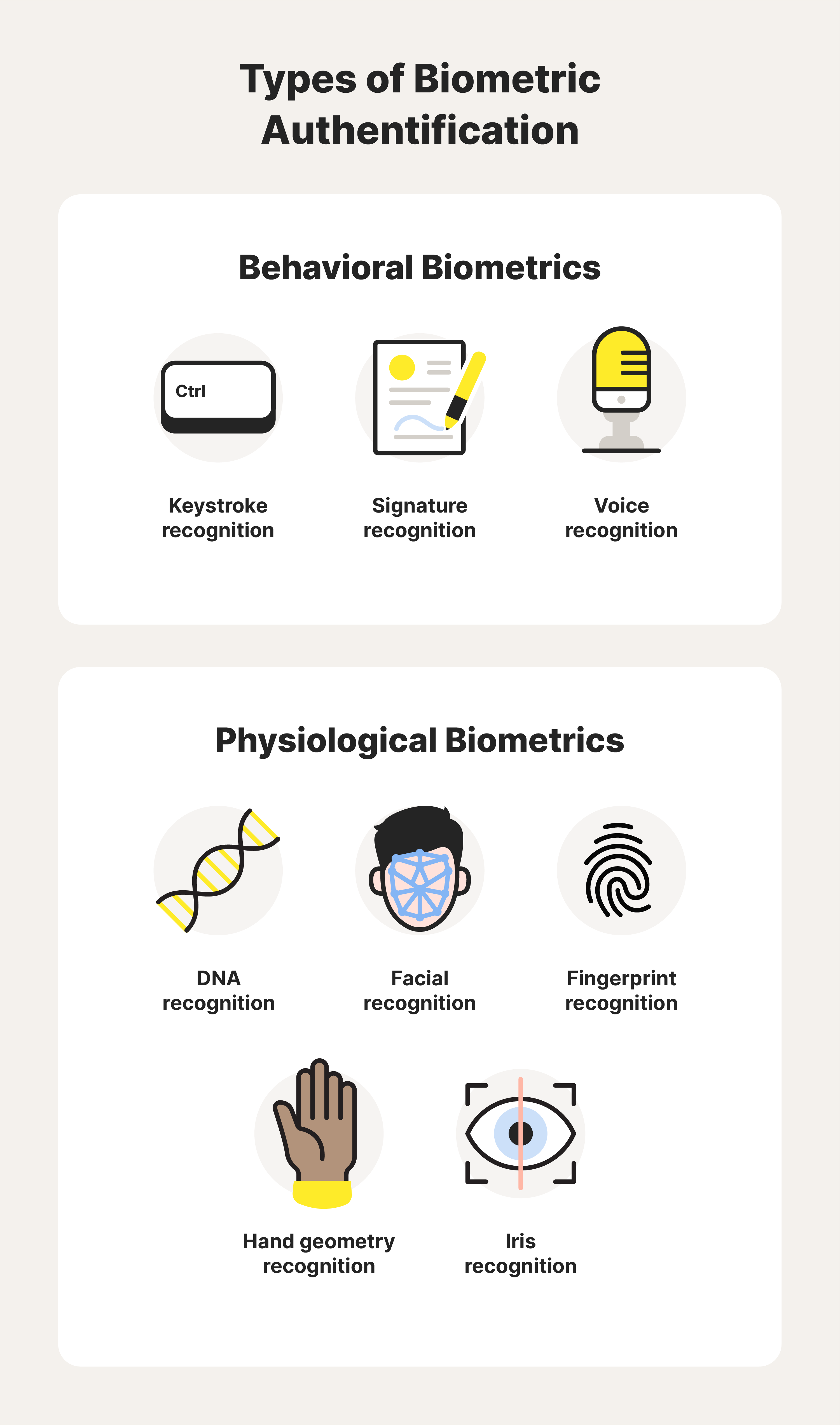
Behavioral biometrics
The way we speak, type, and sign documents are all traits that are unique to every individual. Here are three of the most common behavioral biometric systems.
- Keystroke recognition: verifies users based on their typing tendencies, like speed and rhythm
- Signature recognition: authenticates users based on their penmanship
- Voice recognition: identifies users based on their diction and speech patterns
We’re all capable of recognizing a person based on their voice or the way they jot down their name. Behavioral biometric systems can essentially do the same thing.
Physiological biometrics
Physiological biometrics can recognize our physical attributes. Several prominent examples include:
- DNA recognition: identifies people based on DNA found in their blood, hair, and mucus
- Facial recognition: detects users based on their facial features
- Fingerprint recognition: creates a profile by mapping the ridges on your fingertips
- Hand geometry: verifies users via the shape and size of their hands
- Iris recognition: relies on distinct iris patterns to identify users
Our genes play a big part in determining our physical features—which means they’re also an important factor for systems that rely on physiological biometrics.
Are biometrics safe? 3 cybersecurity risks
Biometric security systems are often much safer than password-based systems because biometric data is distinct and unique. However, there are still several noteworthy biometric security concerns.
Biometric data breaches
Hackers can illegally gain access to sensitive information through a biometric data breach. However, cybercriminals will have a hard time abusing data that's based on our bodies. Biometric data breaches are also very rare—and government organizations like the Federal Trade Commission (FTC) regularly create new policies to protect consumers.
Misinterpretation bias
Bias might be a potential drawback of a biometrics-based system if diverse training methods aren’t implemented. For example, if we only train a system with biometric data from members of a specific age range, ethnic group, or gender, that system might not take anyone who falls outside of those parameters into account.
Selling biometric data
Many tech companies ask to collect data from their users to improve the functionality of their products. However, concerns can arise if a company sells a user’s data to a third-party data broker. The FTC consistently takes action against companies that misuse data—including biometric data.
How to protect your biometric data
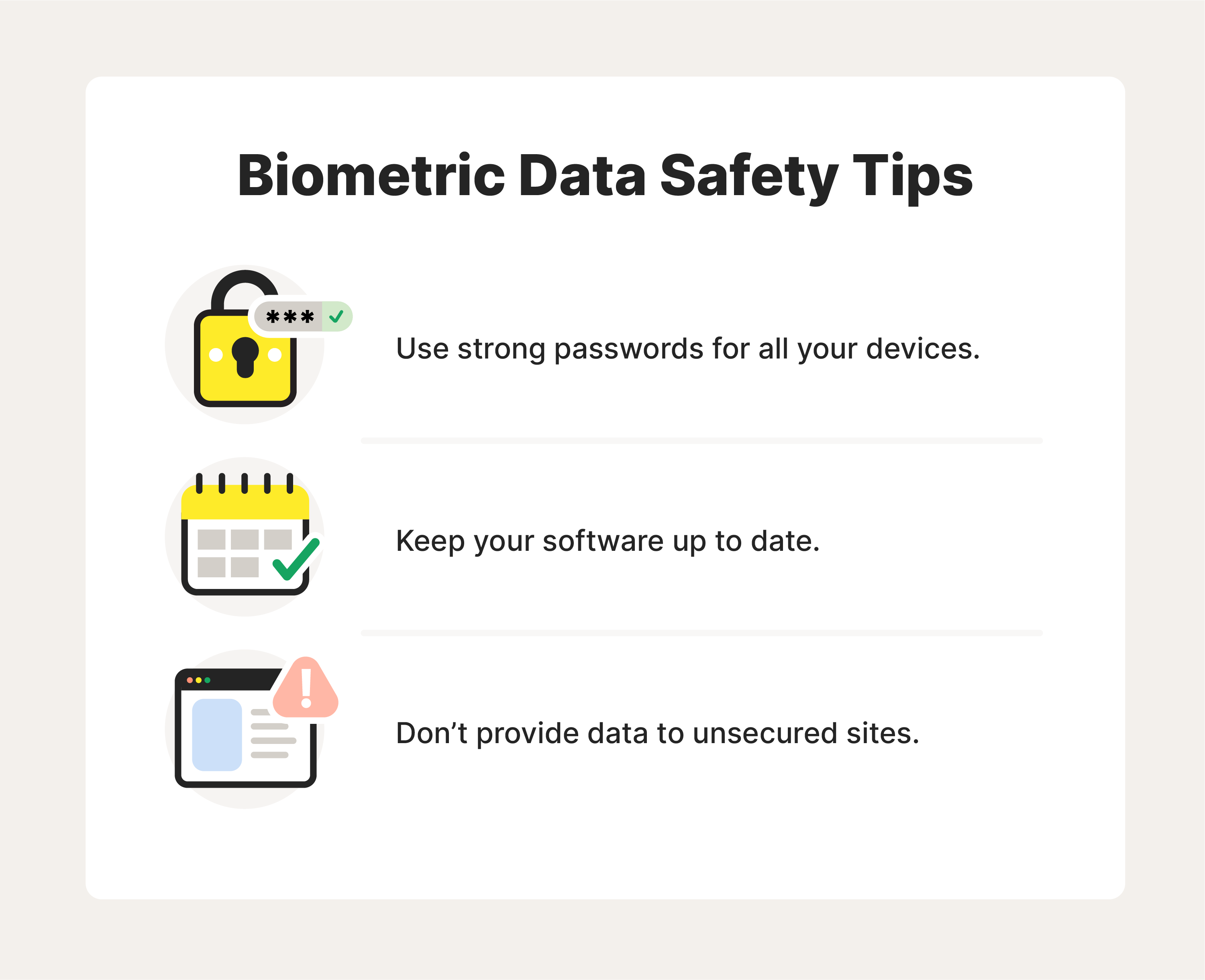
When it comes to securing your biometric data, start by considering where it’s stored. We’ve mentioned earlier that biometric data is typically stored on your devices. Here are several best practices that apply to mobile devices, laptops, computers, and more.
- Use strong passwords to make it harder for hackers to steal your data. Reinforcing your password and using different logins for various sites gives hackers fewer ways to access your information—including biometric data stored on your phone or computer.
- Keep your software current to improve your device’s security. When an update or patch becomes available, try to install it immediately. Manufacturers often release these updates to combat new threats, which they’ll include in their patch notes.
- Only provide biometric data to secure websites. Most browsers will use several methods to let you know that a site isn’t secure. Google Chrome and Safari will add the words “Not Secure” to a faulty website’s URL. You may also receive a “Your connection is not private” alert before the page can even load.
Protecting your devices will also protect your biometric data. Setting aside the time to install updates and change passwords can be worthwhile in the long run.
Help protect your biometric data by using Norton 360 with LifeLock Select
Consider using Norton 360 with LifeLock Select to help secure your device and biometric data with comprehensive malware protection and a secure VPN that encrypts your connection to help protect the sensitive data you send and receive online. That way, you can use your device knowing you’ve taken the extra steps to help protect your biometrics.
FAQs about biometrics
There are many misconceptions about biometrics, namely regarding the pros, cons, and uses of biometric data. Here are answers to some of the most common questions we’ve encountered.
What is the benefit of biometric data?
Complexity is the main benefit of biometric data, which is why biometric security systems are much harder to hack than traditional passwords. The likelihood of two fingerprints matching is extremely rare.
Are there any security concerns with biometrics?
Data beaches are the primary security concern for biometric systems. Other concerns, such as someone lifting your fingerprints from a restaurant menu, aren't as common or practical. Companies must also handle data responsibly.
How is my biometric data used for security?
You might press your finger against a sensor in the back of your phone before you can unlock your device. Your phone or laptop might scan your face before it will let you log in. Biometrics is essentially a replacement for standard passwords.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips and updates.