Block threats at network level
Smart Firewall and Intrusion Prevention System (IPS) work together to help stop threats before they reach your devices, forming a powerful, layered defense.

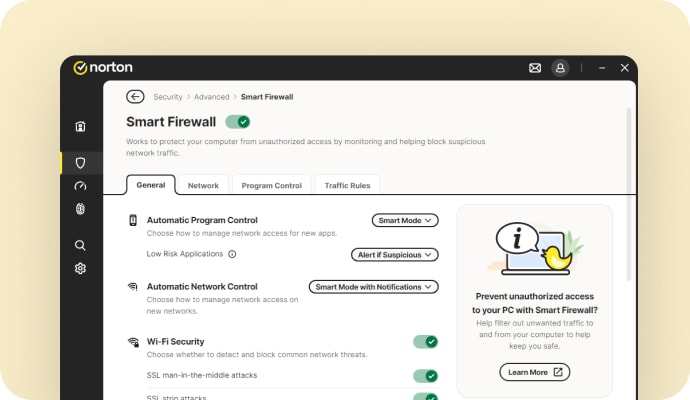
What is Smart Firewall?
Think of it as a security guard for your internet connection, watching every incoming and outgoing connection, stopping suspicious activity before it can cause harm. It works quietly in the background, helping to protect your devices without slowing you down.
Our Smart Firewall and IPS work together to stop threats
Built into Norton 360, Smart Firewall and IPS help block hackers, intrusion attempts, and other online threats before they reach your device. Working with the rest of Norton 360’s protection, this technology creates a multi-layered defense to help keep you safer online.
Why do you need a firewall?
A firewall acts as a barrier between your device and potential online threats. While antivirus removes threats already on your device, a firewall blocks suspicious connections before they get in, and stops malicious programs from sending your data out.
Blocks unauthorised users
Monitors network traffic to prevent hackers or harmful software from getting into your device.
Warns you about connection attempts
Alerts you to suspicious or unexpected network activity so you can choose whether to allow it.
Protects your data
Helps stop cybercriminals from stealing sensitive details like passwords, banking information, or personal files.
Adds Wi-Fi protection
Provides extra security on public or unsecured Wi-Fi by blocking risky activity.

Norton™ 360 plans
Smart Firewall is part of your Norton 360 protection
Smart Firewall is just one layer of protection. With Norton 360, you get a full suite of security tools designed to safeguard your devices, privacy, and identity. Find a plan to fit your digital life.
A firewall monitors network traffic, enforces rules about which traffic is allowed or blocked, and helps block unauthorized access to your computer. It helps block hackers or malware from entering your device over the network.
A firewall protects you from unsolicited and unwanted incoming network traffic. It evaluates incoming traffic for malicious threats, such as hackers and malware, to prevent them from infiltrating your computer or network.
Most computers come with a built-in firewall, such as Windows Defender Firewall or macOS Firewall. Norton Smart Firewall adds stronger, two-way protection that monitors both incoming and outgoing connections, blocking suspicious apps and helping prevent cyberthreats that built-in firewalls can miss.
Firewalls inspect data to keep your connection safe, but the Smart Firewall from Norton is designed to do this efficiently, so you have protection without noticeably slowing down your internet speed.
Windows Firewall offers basic protection, but the Smart Firewall from Norton adds advanced features like two-way traffic monitoring, intrusion prevention, and intelligent threat detection. It’s built to work seamlessly with the other features offered by the security suite of Norton, to give you stronger, more comprehensive protection online.
A cybercriminal can potentially hack any device or system connected to the internet. Firewalls are more susceptible to being hacked if they’re poorly configured, running outdated software, or zero-day vulnerabilities arise.
Firewalls don’t protect against viruses on their own. They manage access to your network, whereas antivirus software serves as cyber protection from malicious viruses. However, some software firewall suites, like Norton 360 Deluxe, include virus protection.
Yes, your home needs a firewall. Without a firewall, you could leave yourself open to accepting every connection to your home network without a way to detect and reject incoming threats. Intruders could engage in malicious activities like gaining control over your computer or network, deleting your data, or using your personal information to commit identity theft and other online frauds.
Related articles
System requirements
Windows™ Operating Systems
Microsoft Windows 11 (all versions).
Microsoft Windows 10 (all versions).
Microsoft Windows 8/8.1 (all versions). Some protection features are not available in Windows 8 Start screen browsers.
Microsoft Windows 7 (all versions) with Service Pack 1 (SP 1) or later.
Mac® Operating Systems
MacOS 10.13 or later.



