What are drive-by downloads + drive-by attack prevention tips
What are drive-by downloads? Use this complete guide on drive-by attacks to help protect your data from drive-by hacking and other dangerous online threats.

Many of us have been there. Twelve shopping tabs deep on your browser as you're researching the just-right product to purchase. Then, a window pops up that encourages you to play a game of cards or accept a gift you just won. This is a classic example of a drive-by download—cyberattacks that install malware onto your devices without your knowledge. And with over 1.1 billion sites currently active on the internet, we want you to be well-versed when it comes to this very relevant cybersecurity threat.
For this reason, we created an all-encompassing guide to drive-by downloads. In this post, we'll explain what drive-by downloads are and how they work, in addition to giving some real-life drive-by attack examples. You can also use the provided drive-by attack prevention tips to learn how to protect your private information.
How do drive by downloads work?
While there is a specific process, it’s important you first understand the goal of these cyberattacks so that you know what you’re protecting yourself from. Hackers carry out drive-by downloads in order to:
- Hijack computers and other IoT devices
- Spy on your network activity and traffic
- Destroy data or render devices inoperable
Now, there are two methods used to infect devices with drive-by downloads and complete one of the goals mentioned above. These include:
- Authorized downloads (without knowledge of full implications): Social engineering and/or phishing scams trick you into clicking on a dangerous link or site. These rely on the user to initiate the download.
- Unauthorized downloads (without any warning or notification): You come across a compromised website and download a virus without notice or warning. These do not rely on the user to initiate the download.
To help you understand how each method works, here’s a breakdown of their infection process:
How authorized drive-by downloads work
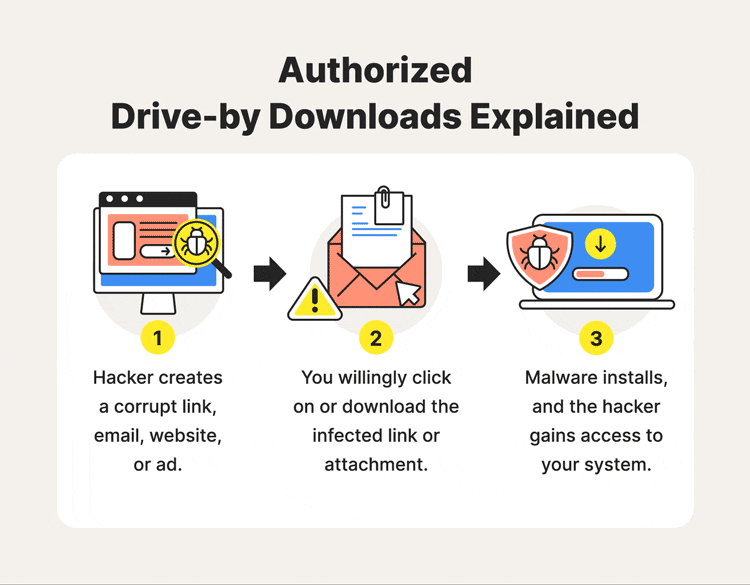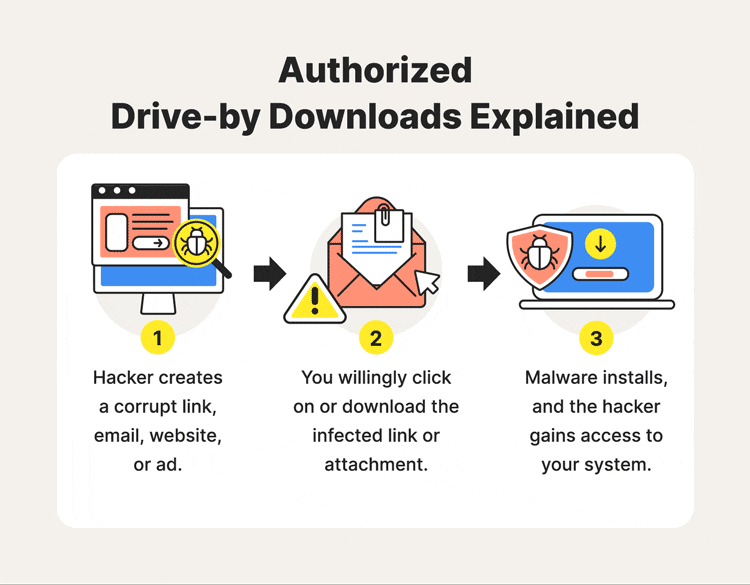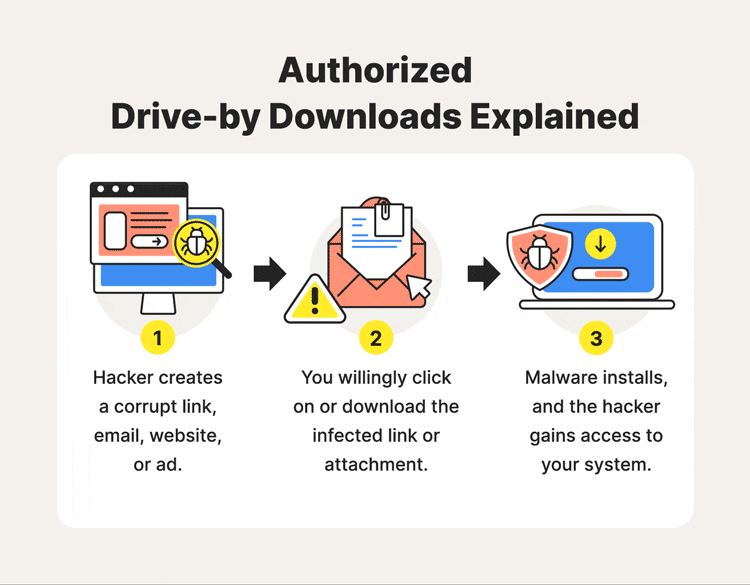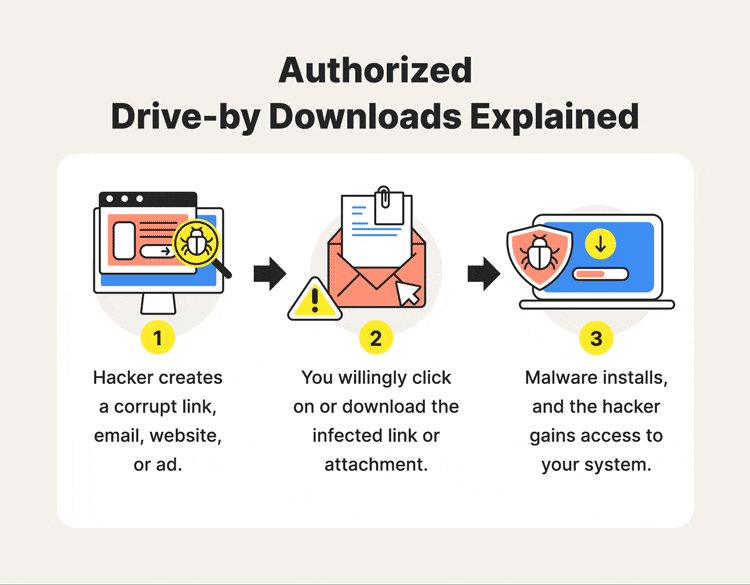
Authorized drive-by downloads rely on the user to initiate the download. Cybercriminals often leverage phishing and/or social engineering approaches to trick you into doing just this. This is typically how it goes:
- A cybercriminal lures internet users with compromised websites, links, or ads.
- You click on or visit infectious material.
- Malware installs onto computer or mobile device.
- Tour system and network is potentially compromised.
An important thing to remember is that bundleware is often attached to authorized drive-by downloads. These are secondary programs hidden within the program you intended to install, concealing other types of malware.
- Authorized drive-by download protection tip: Only download free software from legitimate sources and providers.
How unauthorized drive-by downloads work
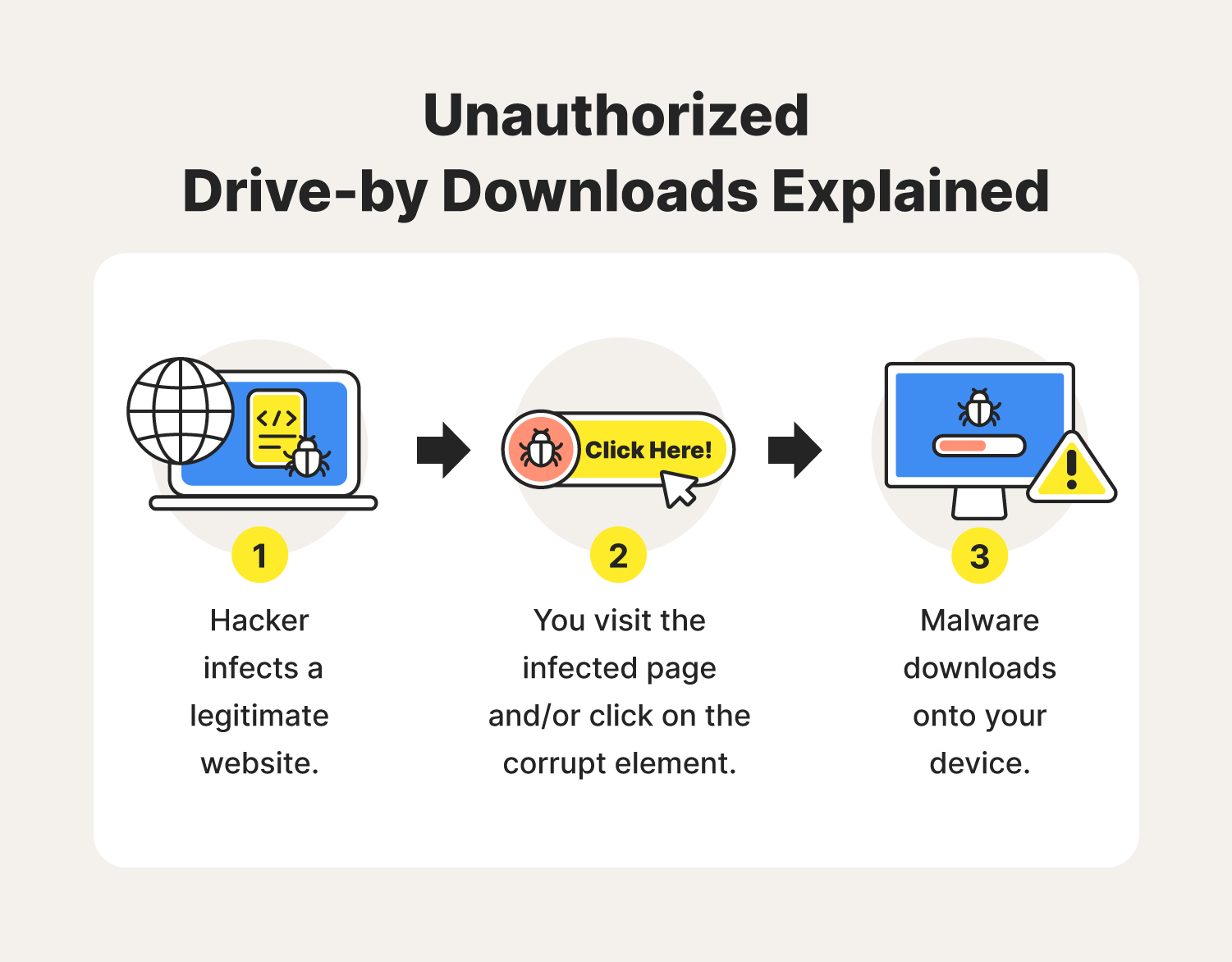
Unauthorized drive-by downloads could be considered the worst of the bunch in that they do not rely on the user to initiate the download. They’re stealthier than that and have a straightforward infection process:
- A hacker infects a webpage using its security flaws.
- You visit the website and interact with the infected link, ad, or attachment.
- Malware downloads onto your device.
- The virus spreads and potentially compromises data.
With this drive-by attack method, the cybercriminal focuses on compromising frequently visited webpages to increase their number of potential victims. They use zero-day exploits to identify security flaws that will grant them access to site controls so they can set up their attacks.
- Unauthorized drive-by downloads protection tip: Install antivirus software that can keep you informed of potential cyberthreats while browsing online.
Types of malware hidden in drive-by downloads
Cybercriminals often use drive-by download attacks to imbed malware onto their victims’ devices. The malware hidden within drive-by downloads often include:
- Trojans: Malware that appears legitimate but can give hackers remote control over your device.
- Ransomware: Malware designed to encrypt your data and hold it for ransom.
- Keyloggers: Malware capable of tracking and recording keystrokes made on your device.
- Botnets: Malware designed to infect devices and connect your device to a hacker’s network.
- Data transfer tools: Applications that permit hackers to transfer sensitive files onto their devices from yours.
Having one or more of these types of malware on your computer’s system could compromise the personal information stored within, potentially making you susceptible to crimes like identity theft or blackmail.
Below are some drive-by attack examples to further educate you on the risks these cyberattacks pose on your data.
Examples of drive-by download attacks
The reach of the internet isn’t slowing down, and, neither is the danger of drive-by downloads. With an average number of 640,000 new internet users each day, hackers can expose more and more people to potentially dangerous websites.
So, if you’re still wondering what a drive-by download attack might look like and what is an example of a drive-by download attack, just look to these well-known instances:
- Gootloader, 2021: A hacking group known as the “Gootkit” family developed a drive-by download software responsible for increased malware infections in the U.S, South Korea, France, and Germany.
- Microsoft, 2021: In January, Microsoft reported new ransomware dubbed “WhipserGate” delivered via drive-by download that destroyed and encrypted company data in their Ukraine offices.
These unfortunate situations emphasize the importance of learning the best ways to protect yourself against drive-by download attacks. You can use the tips listed below to avoid becoming another unexpected victim.
How to prevent drive-by downloads
Though it can be hard knowing whether a website is safe or hosting malicious programs, there steps you can take to protect yourself and your devices from online threats such as drive-by downloads.
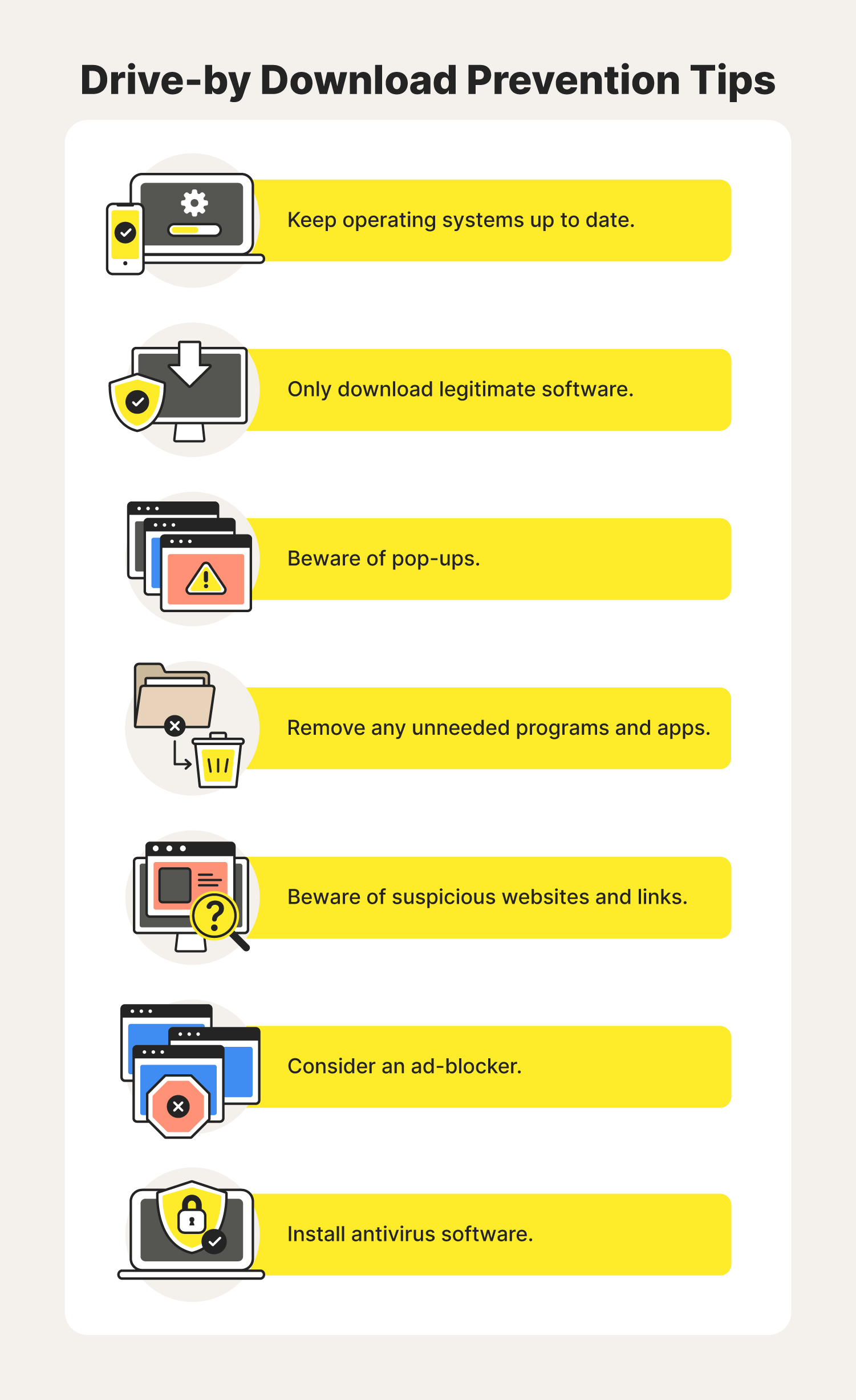
Keep operating systems up to date
Remember to update operating systems with the latest security patches. These can help prevent hackers from using drive-by downloads to infect your devices and get ahold of your sensitive information.
Only download legitimate software
When downloading programs onto your computer, especially ones free of charge, always verify their source and/or creator. Hackers can create seemingly legitimate programs that trick people into thinking they are downloading something they are not.
Beware of popups
If you enter a website and several pop-up windows appear, close them all and leave the site immediately. These windows could be trying to lure you into clicking a button that will deploy a drive-by download onto your computer, compromising your data and network.
Remove any unneeded programs and apps
Only use software you trust to lessen the likelihood of a cybercriminal finding their way onto your device. The more applications and plug-ins you have on your computer, the more security vulnerabilities you must manage.
Beware of suspicious websites and links
One of the best ways to protect yourself from drive-by downloads is by being cognizant of the websites you visit. Try to stay on mainstream sites you know and trust and avoid sites with suspicious and/or outdated layouts. You’ll know you're on a safe site if you see “https://” or padlocks in your address bar.
Consider an ad-blocker
Drive-by download attacks frequently use ads and popups to infect devices with malware. Installing an ad-blocker could prevent these windows from appearing and reduce your chances of infection.
Install antivirus software
Antivirus software could act as your first defense against drive-by downloads and other emerging online threats With a watchful eye protecting your information, you’ll be able to surf the web with confidence and an extra layer of security.
Now that you are aware of drive-by downloads, you can browse safely knowing how to identify and prevent future attacks. Because with our emerging digital age, there's nothing more important than having measures in place to protect our identity, data, and privacy.

The freedom to connect more securely to Wi-Fi anywhere
With Norton™ VPN, check email, interact on social media and pay bills using public Wi-Fi without worrying about cybercriminals stealing your private information
Try Norton VPN for peace of mind when you connect online
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.