115 cybersecurity statistics and trends to know
Explore these 115 cybersecurity statistics to understand the latest cybercrime rates and cybersecurity trends currently shaping the hacking industry.

From cryptocurrency wallets replacing physical billfolds to a worldwide effort to recover from a global pandemic, the digital trends and world events of 2022 transformed the ways we engage with technology like never before.
It also transformed the current state of cybersecurity as we knew it, with new cyberattacks dreamt up, victims targeted, and best practices realized.
For perspective, we’ve rounded up over 100 cybersecurity statistics and facts for digital citizens to ponder and, in turn, pivot their online behaviors. These are the headline-making cybersecurity trends you need to know, cybercrime costs to consider, and cyberthreats to avoid in 2025 and beyond.
Top cybersecurity statistics to know
Cybercrime is on the rise around the world. And while cybercriminals continue to use some of their most tried-and-true tactics — phishing, vishing, or ransomware, for instance — they’re also targeting new victims, including entire industries like healthcare.
- Cyberattacks are more likely to bring down F-35 jets than missiles. (Interesting Engineering, 2021)
- Over 75% of targeted cyberattacks start with an email. (RoundRobin, 2020)
- In 2020, the FBI received 15,421 internet crime complaints related to tech support fraud and from victims in 60 countries. (FBI, 2020)
- Global cybercrime costs are expected to grow by 15% per year over the next five years, reaching $10.5 trillion annually by 2025. (Cybersecurity Ventures, 2020)
- More than half of all consumers have experienced a cybercrime, with around one in three falling victim in the past year alone. (Norton, 2021)
- In 2020, the FBI received more than 2,000 internet crime complaints per day. (FBI, 2020)
- The healthcare industry is expected to spend $125 billion on cybersecurity from 2020 to 2025. (Cybersecurity Ventures, 2020)
- The first half of 2021 saw a 102% increase in cybercrime involving ransomware compared to the beginning of 2020. (Check Point, 2021)
Headline-making cyberattacks and cybersecurity trends in 2022

Recent cybersecurity incidents show that it’s not just user data cybercriminals are after. Instead, they’re wreaking havoc on infrastructures like hospitals, pipelines, meatpacking plants, and water supply centers. Worse yet, these cyberattacks can cause serious physical harm.
9. The first reported death by ransomware occurred in September 2020, when a ransomware attack caused IT failure at a hospital in Düsseldorf, Germany. (Associated Press, 2020)
10. 53% of adults agree that remote work has made it much easier for hackers and cybercriminals to take advantage of people. (Norton, 2021)
11. Hackers tapped into the U.S.'s Colonial Pipeline in April 2021 through a VPN that lacked multi-factor authentication, resulting in a $5 million Bitcoin payment to regain access. (Reuters, 2021)
12. A hacker accessed and attempted (unsuccessfully) to poison the water supply in Oldsmar, Florida, in February 2021. (Wired, 2021)
13. A successful Russian ransomware attack on JBS, renowned as the world’s largest meatpacking company, affected nearly 10,000 workers in June 2021 and caused an uptick in meat prices. (Newsweek, 2021)
COVID-19 cybersecurity stats
There’s no denying it: The COVID-19 pandemic flipped the world on its head. And hackers seized opportunities to take advantage of it.
14. Spam was the most popular type of threat leveraging COVID-19, with 65.7% of COVID-19 related threats being spam email. (ENISA, 2020)
15. 44% of adults feel more vulnerable to cybercrime than they did before the COVID-19 pandemic began. (Norton, 2021)
16. About one in five consumers fell victim to scams in the last year, with 4% clicking a fraudulent COVID-19 contact-tracing link and another 4% paying a fee to receive COVID-19 relief money, and 3% paying to get an illegitimate COVID-19 vaccine. (Norton, 2021)
17. Nearly two in five adults took steps to protect online activities and personal information because of changes to lifestyle since the COVID-19 pandemic began. (Norton, 2021)
18. Since COVID-19, the FBI has reported a 300% increase in cyberattacks. (The Hill, 2020)
19. The COVID-19 pandemic has been connected to a 238% surge in cyberattacks against banks. (Carbon Black, 2020)
20. One-quarter of all employees have noticed an increase in fraudulent emails, spam, and phishing attempts in their corporate email since the beginning of the COVID-19. (Deloitte, 2021)
Cryptocurrency cybersecurity stats
As consumers cozy up to cryptocurrency as an alternative payment method, so too are cybercriminals, especially as forms of ransomware payments.
21. There has been a rise in ransomware campaigns requiring payment in cryptocurrency — a 35% increase from late 2020 to early 2021. (Norton, 2021)
22. In 2020, the FBI received 19,369 business email compromise or email account compromise internet crime complaints, an increasing number of which related to the use of identity theft and funds being converted to cryptocurrency. (FBI, 2020)
23. Crypto criminals stole $1.9 billion in 2020, down from $4.5 billion in 2019. (Finaria, 2021)
24. $76 billion of illegal activity per year involves Bitcoin. (SSRN, 2018)
25. Bitcoin accounts for 98% of cryptocurrency ransomware payments. (Coveware, 2019)
Online privacy and cybersecurity perceptions

Most cyberattacks can be considered an invasion of privacy. And consumers are increasingly taking notice, expressing growing concerns around online privacy and how our data is collected and by whom. What’s more, online users are also expressing uncertainty over how to react if their data or — worse yet — identity is stolen.
26. 58% of adults are more worried than ever about being a victim of cybercrime. (Norton, 2021)
27. 13% of consumers use a VPN to protect their online privacy. (Norton, 2021)
28. Nearly two in three adults say they are spending more time online than ever before, with a similar portion saying they have taken more precautions online because of cybercrime concerns. (Norton, 2021)
29. Online users in India and the U.S. are more likely to take precautions online. (Norton, 2021)
30. Online users in Japan are most likely to struggle with understanding when information is from a credible source. They're also most likely to be worried about cybercrime. (Norton, 2021)
31. 62% of adults admit it's difficult to determine if the information they see online is from a credible source. (Norton, 2021)
32. 53% of adults admit they don't know how to protect themselves from cybercrime. (Norton, 2021)
33. 63% of consumers are very worried their identity will be stolen. (Norton, 2021)
34. 38% of consumers have never considered their identity could be stolen. (Norton, 2021)
35. More than three in five consumers say they accept certain risks to their online privacy to make their life more convenient. (Norton, 2021)
36. 78% of consumers are concerned about data privacy. (Norton, 2021)
37. 63% of consumers are alarmed more than ever about their privacy. (Norton, 2021)
38. 27% of consumers have stopped using public Wi-Fi to protect their online privacy. (Norton, 2021)
39. 83% of consumers want to do more to protect their privacy, but 47% don't know how. (Norton, 2021)
40. 46% of Americans would have no idea what to do if their identity was stolen, and 77% wish they had more information on what to do if it were. (Norton, 2021)
41. 91% of people know the risks of reusing passwords across their online accounts, but 66% do it anyway. (LastPass, 2020)
42. 41% of people don't think their accounts are valuable enough to be worth a hacker's time. (LastPass, 2020)
43. Four in five Americans have concerns about putting their confidential data on cloud-based platforms. (Norton, 2021)
Costs of cybercrimes
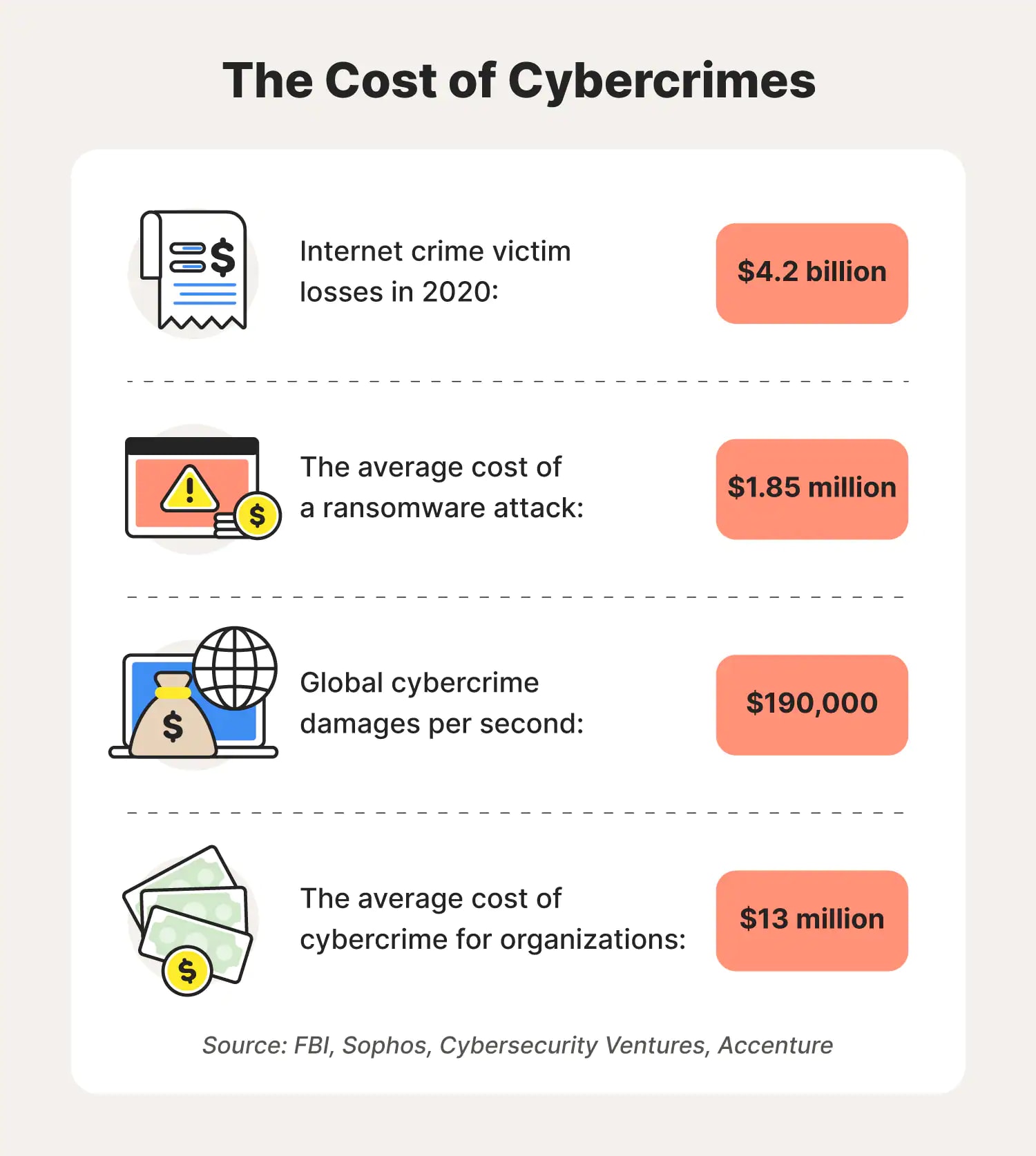
Considering most cybercrimes are financially motivated, successful cyberattacks can cost people and companies a pretty penny. Pore over how much victims have had to pay.
44. 47% of cybercrime victims lose money as a result of a cybercrime committed. (Norton, 2021)
45. It's estimated that global ransomware damage costs will reach $20 billion in 2021. (Cybersecurity Ventures, 2019)
46. Tech support frauds amounted to over $146 million, a 171% increase in losses from 2019. (FBI, 2020)
47. Victims of compromised personal and business email accounts experienced a loss of $1.86 billion in 2021. (FBI, 2020)
48. The average cost of cybercrime for organizations is $13 million. (Accenture, 2019)
49. The average ransom paid by mid-sized organizations is $170,404. (Sophos, 2021)
50. The average cost of a ransomware attack was $1.85 million in 2020, doubling the year before at $761,106. (Sophos, 2021)
51. Globally, those who experienced cybercrime in the past year spent an average of 6.7 hours resolving it for an estimated 2.7 billion hours lost in total. (Norton, 2021)
52. By 2021, global cybercrime rates involving damages will amount to $6 trillion per year, $500 billion per month, $115.4 billion per week, $16.4 billion per day, $684.9 million per hour, $11.4 million per minute, and $190,000 per second. (Cybersecurity Ventures, 2020)
53. In the last five years, the FBI has fielded over 2.2 million internet crime complaints, amounting to $13.3 billion in losses for victims of these crimes. (FBI, 2020)
54. Internet crime victims lost $4.2 billion in 2020. (FBI, 2020)
55. In 2020, internet crime victims over the age of 60 experienced $966 million in losses, while victims under 20 experienced almost $71 million in losses. (FBI, 2020)
56. Californians lost the most to internet crimes in the U.S. in 2020, amounting to more than $500 million. (FBI, 2020)
57. On the dark web, Social Security numbers might go for $1 each, a credit card number could sell for up to $110, and a U.S. passport might cost up to $2,000. (Experian, 2018)
Cybersecurity stats by device and platform

Computers like desktops and laptops have long been targets of cyberattacks. They’ve also evolved into devices that can fit into the palms of our hands or even around our wrists — and so have the cybersecurity risks associated with them and their platforms.
Mobile devices and apps
When it comes to mobile devices, it’s often the apps downloaded on them that put us at risk.
58. 70% of online fraud is accomplished through mobile platforms. (RSA, 2019)
59. There has been a 680% increase in fraud transactions originating from mobile apps from 2015 to 2018. (RSA, 2019)
60. 82 rogue apps are identified each day on average, and one in five cyberattacks are attributed to rogue mobile apps. (RSA, 2019)
61. One in 36 mobile devices have a high-risk app installed on them. (SECURE-D, 2020)
Video games
Like social media sites, gaming can be a social lifeline for online users. As such, gamers need to be aware of the cyberthreats associated with their consoles, computers, and handhelds and increase their video game security accordingly.
62. Gaming was the No. 1 category for fraudsters in 2020. (SECURE-D, 2020)
63. Nearly three-quarters of U.S. gamers (73%) say they would never fall for a gaming scam, with about half (51%) bravely thinking their gaming account(s) will never be hacked. (Norton, 2021)
64. Three in five (62%) American gamers admit they worry gaming will become less secure in the future. (Norton, 2021)
65. In addition to phishing campaigns, “trojanized” crack campaigns are an increasing threat targeting the gaming community. (Norton, 2021)
IoT devices
The Internet of Things (IoT) has become a rather broad term, comprising any device that can be connected to the internet. And the potential cybersecurity risks of these devices are also far and wide.
66. There was a 30% rise in IoT malware in 2020, a total of 32.4 million worldwide. (SonicWall, 2021)
67. Infected routers account for 75% of IoT attacks, and connected cameras accounted for 15% of them. (Broadcom, 2019)
68. It takes all but five minutes for IoT devices to be attacked. (Netscout, 2019)
69. 63% of people find IoT devices "creepy" in the way they collect data about people and their behaviors. (Internet Society, 2019)
70. 53% of people distrust IoT devices to protect their privacy and respectfully handle their information. (Internet Society, 2019)
71. 28% of people who do not own a smart device will not buy one due to security concerns. (Internet Society, 2019)
Social media
Social media sites can be a breeding ground for online scams and privacy-compromising habits alike.
72. There was a 43% increase in social media fraud attacks in 2018. (RSA, 2018)
73. 11% of consumers have deleted a social media account to protect their online privacy. (Norton, 2021)
74. 34% of U.S. adults don't trust social media companies at all with safeguarding their personal data. (Statista, 2021)
75. Corporate social media account takeover attempts occur nearly 30 times per year on average for every institution. (ZeroFox, 2021)
Cyberattack statistics by type
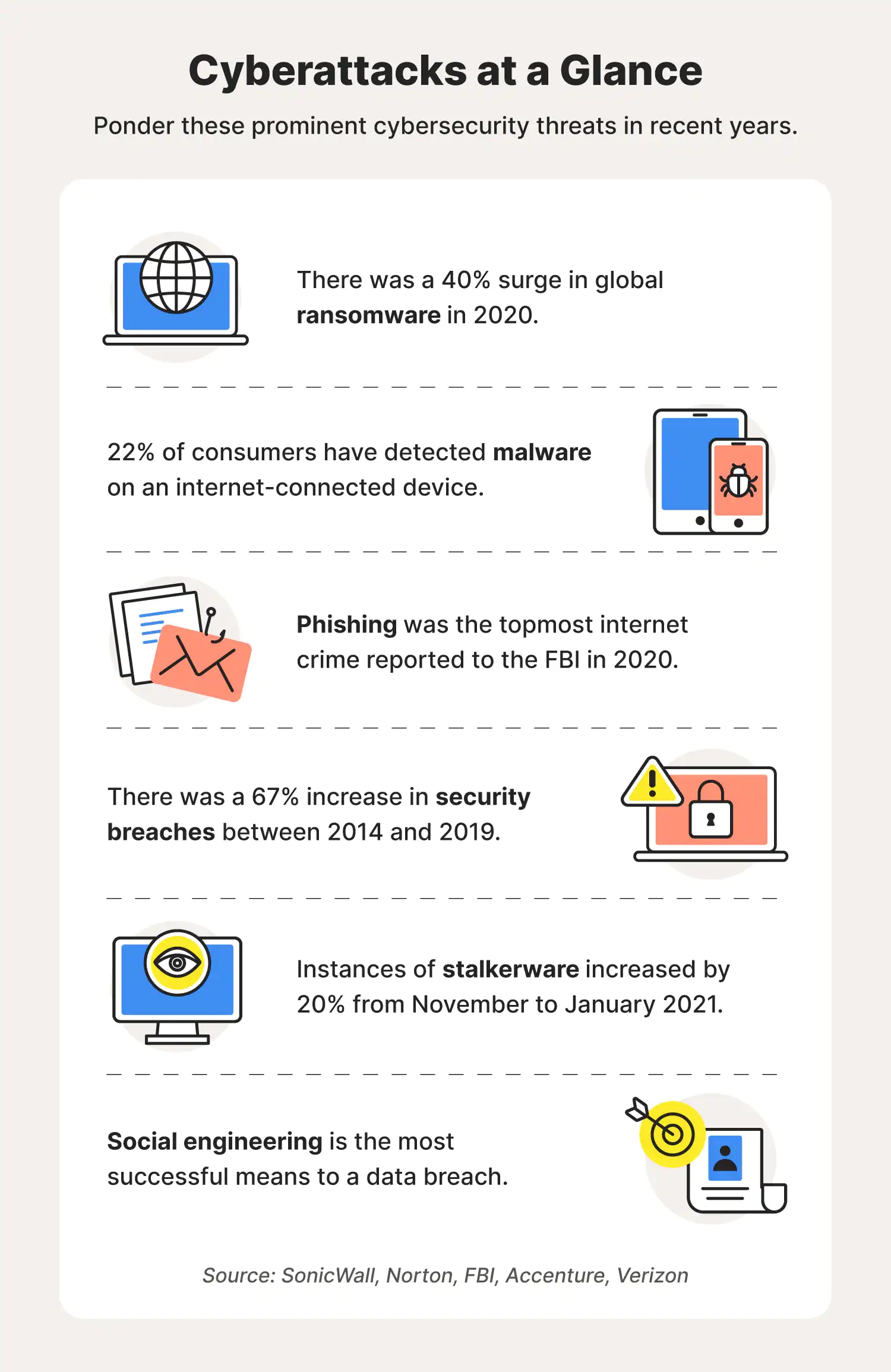
It’s been long noted that a hacker attacks every 44 seconds, but their methods of attack are ever evolving. Here are some of the most prominent cyberattack types in recent years.
Ransomware statistics
Ransomware attacks are essentially gaining access to your device or a network, and then locking and encrypting the data stored on it. It often happens when victims mistakenly download malware through email attachments or links from unknown sources — which happen to be hackers.
76. 2020 saw a 40% surge in global ransomware. (SonicWall, 2021)
77. The U.S. saw 145.2 million ransomware hits in 2020, a 139% increase over 2019. (SonicWall, 2021)
78. On average, only 65% of the encrypted data is restored after ransoms are paid (Sophos, 2021)
79. 37% of organizations were hit by ransomware in 2020, a 14% decrease from 2019 when 51% of organizations were hit. (Sophos, 2021)
80. 10% of data breaches involve ransomware. (Verizon 2022 Data Breach Investigations Report)
Malware statistics
Malware is an abbreviated form of “malicious software,” a software that is specifically designed to gain access to or damage a computer, usually without the knowledge of the owner. And it can come in many forms, including ransomware, spyware, and viruses, to name a few.
81. Malware is the most expensive attack type for organizations. (Accenture, 2019)
82. There was a 39% decrease in malware worldwide in 2020. (SonicWall, 2021)
83. 22% of consumers have detected malicious software on a computer, Wi-Fi network, smartphone, tablet, smart home, or other connected devices. (Norton, 2021)
Phishing statistics
Phishing is when scammers try to lure sensitive information or data from you by disguising themselves as trustworthy sources. And phishers use multiple platforms to achieve these cyberattacks, including emails, texts, and phone calls.
84. Nearly 60% of Americans have reportedly been exposed to fraud schemes, including 26% exposed to email phishing scams. (AICPA, 2018)
85. 36% of data breaches involved phishing. (Verizon 2022 Data Breach Investigations Report)
86. Phishing is one of the top causes of data breaches, followed by the use of stolen credentials and ransomware. (Verizon 2022 Data Breach Investigations Report)
87. 50% of data breach incidents involved phishing and social engineering. (Trustwave, 2020)
88. Phishing was the topmost internet crime reported to the FBI in 2020, with 241,342 victims filing complaints. (FBI, 2020)
Data breach statistics
A data breach is a security incident in which information is accessed without authorization, sometimes using other cyberattack methods like phishing or social engineering.
89. There was a 67% increase in security breaches between 2014 and 2019. (Accenture, 2019)
90. 85% of data breaches involve a human element. (Verizon 2022 Data Breach Investigations Report)
91. Data breaches are most commonly financially motivated. (Verizon 2022 Data Breach Investigations Report)
92. External cloud assets are compromised more than on-premise assets during data breaches. (Verizon 2022 Data Breach Investigations Report)
93. Credentials are one of the most sought-after data types in data breaches, followed by personal information. (Verizon 2022 Data Breach Investigations Report)
Stalkerware statistics
Stalkerware is similar to spyware in that it’s software that’s often unknowingly installed on a user’s device for the purpose of spying or stalking.
94. 86% of adults are unaware of stalkerware or have only heard the name, meaning only 14% are familiar with stalkerware or creepware. (Norton, 2021)
95. One in five adults in a romantic relationship believe their partner is at least somewhat likely to plant stalkerware on them. (Norton, 2021)
96. Instances of stalkerware increased by 20% from November 2020 to January 2021. (Norton, 2021)
Other cybercrime statistics
In addition to the above cyberattacks, tech support fraud, identity theft attempts, and social engineering attacks are other cyberattacks to watch for in 2023 and beyond.
97. 55 million consumers were victims of identity theft in the past year. (Norton, 2021)
98. 66% of tech support fraud victims are reportedly over 60 years old, they lost over $116 million to frauds in 2020. (FBI, 2020)
99. Ad fraud is expected to trigger losses of $100 billion globally by 2024. (Juniper Research x Statista, 2020)
100. 14% of consumers have detected unauthorized access on an email account. (Norton, 2021)
101. Archive files, like .zip and .jar, represent around 37% of all malicious file extensions. (CISCO, 2018)
102. Social engineering is the most successful means to a data breach. (Verizon 2022 Data Breach Investigations Report)
Cybersecurity stats for businesses to know
Cyberattacks on businesses are, well, big business for cybercriminals. For the businesses that are victims, cyberthreats aren’t only costly to recover from, but they also can create consumer distrust.
103. It's estimated that there will be a ransomware attack on businesses every 11 seconds in 2021. (Cybersecurity Ventures, 2019)
104. 70% of consumers believe businesses aren't doing enough to secure their personal information. (Arcserve, 2020)
105. 68% of business leaders feel their risk of a cyberattack is increasing. (Accenture, 2019)
106. 47% of organizations have had at least one employee download a malicious app. (Checkpoint, 2021)
107. More than half of all cyberattacks are committed against small to midsize businesses. (Cybersecurity Ventures, 2020)
108. 57% of all organizations have experienced a mobile phishing incident. (Wandera, 2020)
109. Three-quarters of businesses have experienced data loss from a cloud service more than once. (Oracle, 2020)
110. 59% of consumers are likely to avoid companies that suffered from a cyberattack in the past year. (Arcserve, 2020)
111. The most affected industries by breaches targeting payment card data are retail, finance, and insurance. (Trustwave, 2020)
112. Nearly two-thirds of financial services companies have over 1,000 sensitive files open to every employee. (Varonis, 2021)
113. The banking industry incurred the most cybercrime costs in 2018 at $18.3 million. (Accenture, 2019)
114. Financial services businesses take an average of 233 days to detect and contain a data breach. (Varonis, 2021)
115. The average cost of a financial services data breach is $5.85 million, among the highest of any industry. (Varonis, 2021)
5 cyberattacks on the rise, plus how to help protect yourself
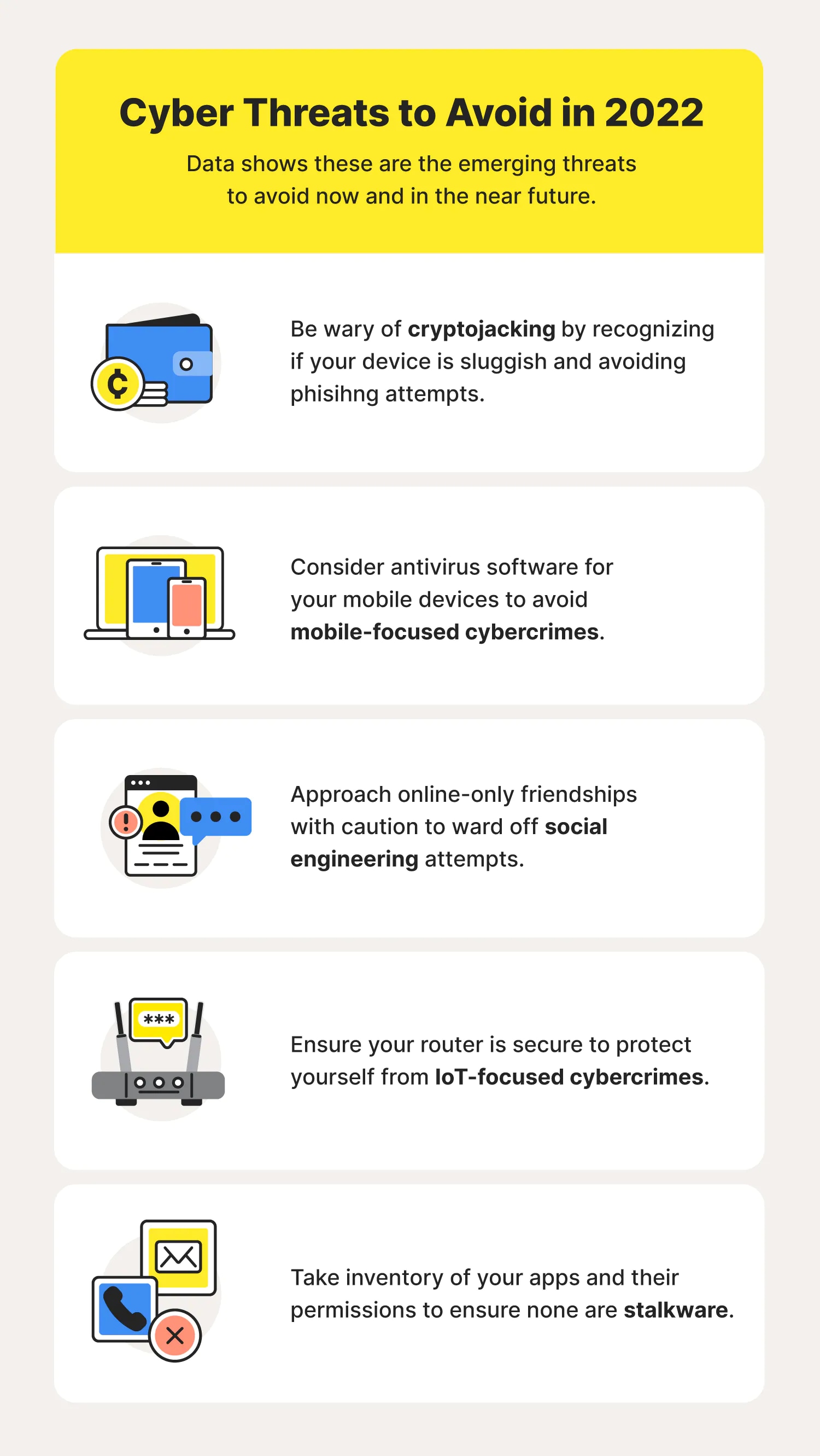
Online user habits and cybersecurity statistics indicate that these are some emerging and existing cybersecurity threats you’ll likely hear more about this year.
1. Cryptojacking
Considering the rise of cryptocurrencies, cybercrimes associated with cryptocurrency are something to be aware of in 2023 and beyond.Cryptojacking is a form of malware that gives cybercriminals unauthorized access to someone’s cryptocurrency database or wallet so that they can steal their cryptocurrency. Like most malware, it can be installed via phishing attempts or even by a malicious individual who has physical access to a device.
2. Mobile-focused cybercrimes
Mobile devices are a part of our daily lives — we use them for alarms, navigation, even to order groceries. As these devices evolve, so do the cybersecurity threats that come with them.Those can come in the form of phone scams, malicious third-party apps, even spyware that’s installed on our devices and potentially collecting data without our permission.
3. Social engineering
Social engineering is the art of manipulating someone to divulge sensitive or confidential information, usually through digital communication, that can be used for fraudulent purposes.Unlike traditional cyberattacks that rely on security vulnerabilities to gain access to unauthorized devices or networks, social engineering techniques target human vulnerabilities. For this reason, it’s also considered human hacking.
4. IoT-focused cybercrimes
IoT refers to electronic devices that can connect to the internet and share data with other internet-enabled devices. This can include smartphones, laptops, fitness trackers, smart TVs, or even gaming consoles, each with its own cybersecurity vulnerabilities.One of the largest risks of IoT devices is the ways in which they collect our data and potentially infringe on our privacy.
5. Stalkerware
As the name indicates, stalkerware is software used for cyberstalking. It’s often installed on victims’ devices unknowingly and with the goal to trace all of their activities.
And it can be installed by cybercriminals, perhaps via phishing, or even by someone close to you like a romantic partner, potentially by putting a stalkerware app on your device.
You needn’t commit these 115 statistics on hacking to memory, but knowing the degree to which a cyberattack can affect our digital and physical world just might encourage you to reevaluate your online habits and go head-to-head with the hacking industry.
Bottom line: Don’t become a cybersecurity statistic.
Cybersecurity statistics FAQs
Cybersecurity statistics can sometimes cause online users to have even more questions. Luckily, we have answers.
How many cyberattacks happened in 2021?
There were nearly 1,900 cyberattacks within the U.S. in 2021.
How many cybersecurity attacks are there per day?
Since 2013, there have been an estimated 3.8 million records stolen from cybersecurity attacks every day.
How many businesses are targeted by spear phishing attacks each day?
There isn’t a clear answer to how many businesses are targeted by spear phishing attacks each day. For reference, 88% of organizations face spear phishing attempts in a single year — that means many businesses could be targeted by spear phishing attacks every day.
How many people get hacked a year?
There isn’t concise data on how many people get hacked a year. However, considering there are around 2,200 cyberattacks per day, that could equate to more than 800,000 people being hacked per year.
Are cybersecurity breaches increasing?
While the number of successful breaches is not increasing, according to some reports, breaches are becoming more costly, especially for businesses.
How common are cyberattacks?
Estimates show that there is a cyberattack every 44 seconds throughout the day.
Where do most cyberattacks come from?
China and Turkey are reportedly most at fault for cyberattacks.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.
- Top cybersecurity statistics to know
- Headline-making cyberattacks and cybersecurity trends in 2022
- Online privacy and cybersecurity perceptions
- Costs of cybercrimes
- Cybersecurity stats by device and platform
- Cyberattack statistics by type
- Cybersecurity stats for businesses to know
- 5 cyberattacks on the rise, plus how to help protect yourself
- Cybersecurity statistics FAQs





Want more?
Follow us for all the latest news, tips, and updates.