What is spyware? How to detect it and protect yourself
Spyware is malicious software that secretly monitors your activity and collects sensitive information, like passwords, location data, or browsing habits, without your consent. Learn more about how it works and what the signs of infection are. Then, get security software to help protect your devices against spyware and other online threats.

Spyware is a dangerous type of malware that can give criminals a direct view into your private life, offering access to sensitive data they can use to steal money, take over accounts, or even commit identity theft.
While notable spyware attacks are often focused on high-profile individuals, like journalists or politicians, this sneaky malware can be used to target anyone. Keep reading to learn how spyware works and what you can do to help keep your devices and privacy protected.
What is spyware?
Spyware is a type of malware that cybercriminals secretly install on your mobile device or computer without your permission. They can then monitor your activity, collect sensitive data like your passwords or location, and use it to commit fraud or identity theft.
While spyware traditionally targeted computers and laptops, attacks on mobile devices have become increasingly common. In the spring of 2025, for example, Apple warned users in over 100 countries about a mercenary spyware attack targeting iPhones.
A recent Gen Threat Report revealed that mobile threats were on the rise more broadly, with 25% more users targeted by adware and spyware. Additionally, a separate study reported that 2.5 out of every 1,000 mobile devices targeted in scams were infected with Pegasus spyware, a significantly higher rate than previously recorded.
Types of spyware
Some of the most common types of spyware include adware, Trojans, internet trackers, and system monitors. Here’s a closer look at tactics each type uses to monitor or steal your data.
- Adware: Adware tracks your browser history and downloads to predict what products or services you’re interested in. This data may be sold to advertisers or used directly to serve targeted ads, often in the form of intrusive pop-ups or banners.
- Trojans: Trojans are a type of malware disguised as legitimate software. Much like the Trojan horse from Greek mythology, Trojans get access to devices by disguising themselves as benign updates or files. When in place, they can disrupt your system, steal your data, or grant a hacker remote access.
- Internet tracking: Internet tracking is widely used by many legitimate types of software to monitor your browsing history and downloads, usually for marketing or analytics. But some spyware, like malicious browser extensions or compromised apps, can secretly track your activity without your consent for more invasive purposes.
- System monitors: System monitors are designed to capture usage data from your computer. Keyloggers, for example, can record your keystrokes, meaning hackers could read your emails or steal your login credentials. System monitors are often disguised as freeware or safe shareware.
- Rootkits: Rootkits hide deep within your system to avoid detection. They give attackers remote access to your device to steal data, install other malware, or control system functions.
- Web beacons: Web beacons are tiny, invisible graphics embedded in emails or websites. They track whether you’ve opened a message or visited a page. They are often used for legitimate marketing analytics, but criminals can also exploit them for surveillance.
- RedShell: RedShell is a controversial analytics tool previously bundled with certain PC games. It tracked user behavior for marketing purposes, without clear consent, by linking online activity to game usage, raising privacy concerns.
- Tracking cookies: Tracking cookies can log your activity across websites. First-party tracking cookies are usually benign and help personalize your experience, while third-party cookies can act like spyware by collecting and sharing your data for targeted advertising.
How does spyware work?
Spyware infiltrates your device without your permission, often getting installed after you click a deceptive link or download a legitimate-looking app that has been compromised.
Once installed, it monitors your activity and collects sensitive data like your passwords, browsing history, location, or IP address. That information is then transmitted to a third party (often the cybercriminal or hacker who distributed the spyware) who can use it to surveil you, try to take over your accounts, or steal your identity.

Some spyware is created to target specific individuals, like journalists, business executives, or politicians. Other types are more widespread and aim to collect massive amounts of data from everyday users.
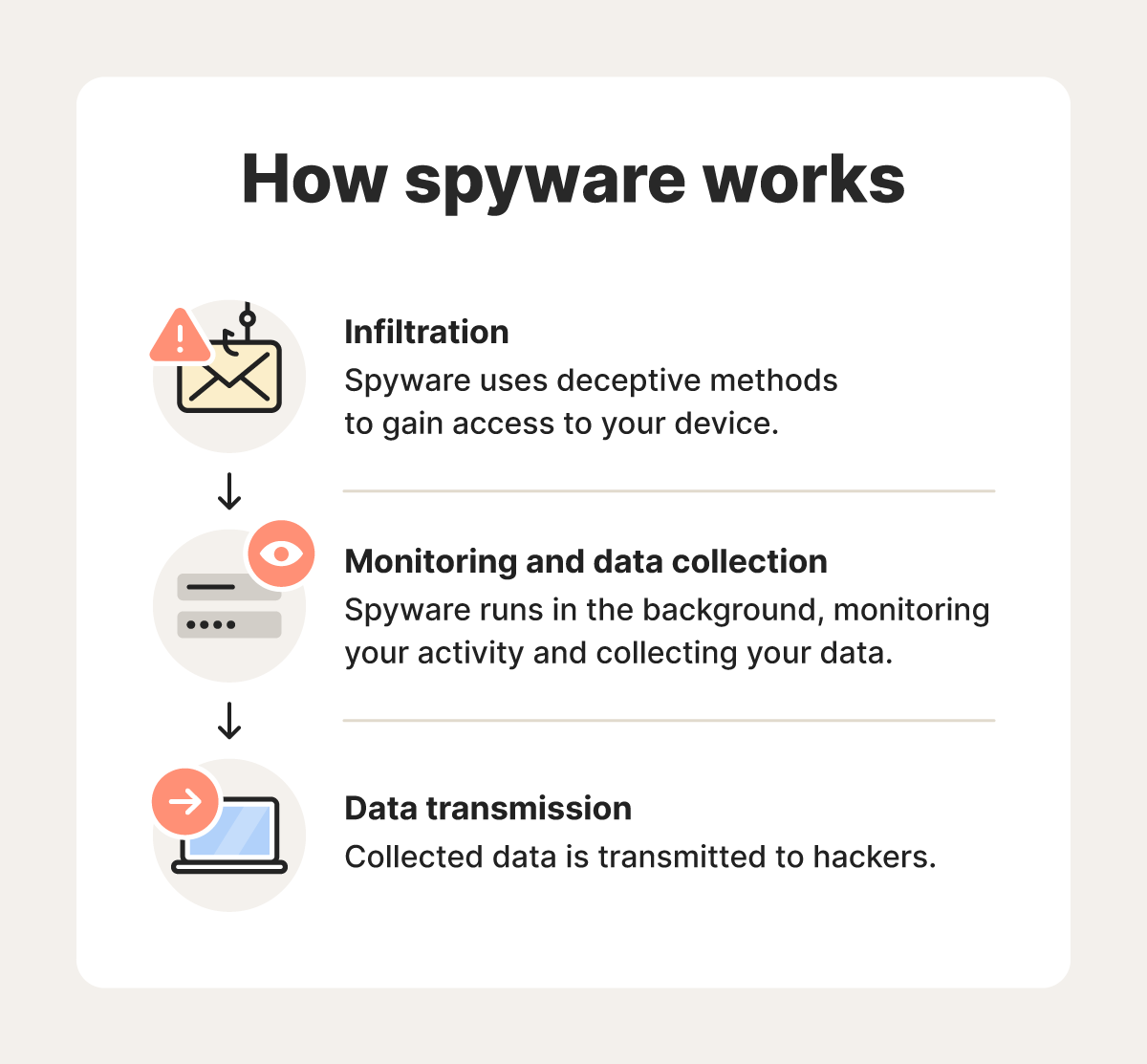
Here’s a closer look at how spyware works.
1. Infiltration
Your device might get infected with spyware if you click a dangerous link, download an infected file, or visit a fake website. Cybercriminals will often try to trick you into taking one of these actions during a phishing attack or online scam. You can also be exposed to spyware if you download legitimate software that has been compromised by a hacker.
These are some of the main methods of spyware infiltration to be aware of:
- Opening phishing emails: Phishing scams may trick you into clicking malicious links or downloading infected files.
- Having network vulnerabilities: Criminals can take advantage of unpatched software flaws to silently install spyware.
- Visiting spoofed websites: Spoofed websites designed to look like the original website they’re impersonating may trick you into clicking an infected link.
- Visiting malicious websites: Visiting compromised or malicious websites can trigger spyware to install automatically.
- Downloading free or bundled software: Spyware hides inside free or seemingly harmless software to sneak onto your device when you install it.
- Clicking suspicious ads: Malicious ads can infect your device with spyware if you click them, or sometimes even if you don’t.
- Downloading fake apps: Malicious apps often mimic legitimate ones to trick users into downloading spyware. Once installed, they can monitor activity, steal data, or grant attackers remote device access.
- Downloading harmful software: Hackers may exploit vulnerabilities to create hidden entry points in software, letting them bypass normal security protocols and install spyware without the user's knowledge.
2. Monitoring and data collection
Once installed, spyware runs silently in the background without your knowledge. It continuously monitors your activity, collecting your browsing history, keystrokes, login credentials, emails, location, and screenshots or recordings. Some programs can even activate your microphone or webcam.
While spyware is designed to avoid detection, it may cause device issues, like slower performance, unexpected pop-ups, or unusual data usage. Monitoring for these warning signs can help you take proactive steps to prevent your privacy or security being compromised.
3. Data transmission
Spyware doesn’t just collect your sensitive information, it also transmits it to servers controlled by the attackers. They may then use it to steal your identity, hijack your online or financial accounts, commit fraud, or sell your details to other cybercriminals on the dark web.
Problems caused by spyware
If spyware infiltrates your device, it can compromise your personal data and potentially lead to significant privacy breaches or financial losses. Here's a closer look at some of the problems a spyware infection can cause.
- Data theft: Spyware can collect sensitive information like login credentials, emails, and personal documents, compromising your privacy.
- Identity theft: After collecting your personal data, cybercriminals may be able to steal your identity, possibly leading to financial harm or loss of accounts.
- Financial losses: Stolen financial information can result in unauthorized transactions, drained bank accounts, and credit card fraud.
- Damage to your device: Spyware consumes system resources, causing slower performance, frequent crashes, and reduced battery life.
- Browsing disruptions: Some spyware alters browser settings, redirects search queries, or injects unwanted advertisements, disrupting your online experience.
Beyond the tangible consequences of a spyware infection, it can also negatively impact your mental health.
According to a 2022 Forbes article, victims of spyware report feeling constantly watched, even in their most private spaces, leading to anxiety, isolation, and loss of trust in their own devices. Domestic abuse victims, in particular, are increasingly targeted by consumer-grade spyware installed by their abuser, causing persistent fear.
How to spot spyware
You can spot spyware by looking out for suspicious links on websites or pop-up ads, checking reviews and permissions before installing software or apps, and ignoring emails from unknown senders. Here are some common red flags that may indicate you’re encountering spyware.
- Suspicious pop-ups: Unexpected pop-ups, especially any that appear when you’re not browsing, may contain fake warnings or ads designed to trick you into clicking a link and accidentally installing spyware on your device.
- Software from an unreliable source: Downloading official software from a non-official source, like a torrenting site or third-party app store, could put your privacy at risk. These downloads could bundle spyware or other malware along with a legitimate program. Check reviews of the platform and scan any downloads before installing to help protect yourself.
- Excessive app permissions: Apps requesting access to your camera, microphone, contacts, or location without a clear reason could be spyware. Be cautious if a simple game or tool requests high-level permissions that don’t seem connected to its functionality.
- Poor or suspicious reviews: Apps or tools with bad reviews, or vague, overly positive, and repetitive reviews, might be fake. Take a closer look if you see unusually high ratings without detailed feedback or if many reviewers seem to say the same thing.
- Email attachments from unknown senders: Attachments in emails from senders you don’t recognize, or even from known contacts that seem out of character, can contain spyware. Avoid opening any files unless you're sure of their origin and purpose.
- Suspicious links: Links in emails, texts, or social media messages that are urgent, misspelled, or unrelated to the conversation could lead to spyware. Hover over links to preview the destination URL and avoid clicking if anything feels off.
Signs of a spyware infection
Unexplained phone slowdowns, strange behavior, or new software on your device can indicate a spyware infection. Here are some specific symptoms to watch for if you suspect your device is compromised.
- Slow device: Spyware runs in the background, using up processing power and slowing down ping speed, load times, and overall system performance.
- Low hard drive space: Spyware can install large hidden files or duplicate your data, quickly eating up your device’s available storage and leading to hard drive failure.
- Unusual network activity: Unexpected spikes in data usage, especially when you’re not actively using your device, may indicate spyware is transmitting information in the background.
- Changes to your settings: Spyware may hijack your homepage, search engine, or security settings to weaken system defenses or redirect traffic.
- Battery drain: Spyware running continuously can quickly drain your battery, even when your device is idle or in sleep mode.
- Phone overheating: Continuous background activity from spyware can overwork your device, causing your phone to overheat even if you're barely using it.
- Persistent pop-ups: Frequent, intrusive pop-ups, especially outside of normal browsing, can indicate that spyware is operating behind the scenes.
- Suspicious new programs: Unfamiliar software or browser extensions that appear on your device may have been installed by spyware to track your activity. If you don’t remember installing them, treat them as suspicious.
If you notice any of these signs, it’s important to act quickly before spyware collects more of your sensitive data. A trusted cybersecurity tool like Norton 360 Deluxe can help, with real-time threat protection that can help you defend against spyware, malware, and ransomware. You’ll also benefit from a secure VPN and dark web monitoring to help keep your personal information safer from prying eyes.
How to remove spyware
If you suspect your device has spyware, try running a security scan, using a trusted spyware removal tool, and uninstalling any apps you don’t recognize. Here’s a guide to removing spyware from your devices:
From your computer
If you suspect that spyware has infected your desktop computer or laptop, take these steps to identify the infection and remove it:
- Review installed programs: Check your list of installed programs and browser extensions for anything unfamiliar or suspicious. Spyware can sometimes disguise itself as legitimate software. If you spot something you don’t recognize, uninstall it.
- Run a security scan: Use antivirus software, like Norton 360 Deluxe, to scan your device. The scan will help detect and remove any spyware or other malware.

If the problem persists after these steps, consider performing a factory reset to fully wipe your system and remove spyware. Just remember to back up important files first to avoid losing them for good.
Once you've cleaned your system, invest in robust antivirus software to monitor your system continuously, detect potential risks, and help guard against spyware from accessing or modifying your personal information.
From your phone
If you've noticed signs of mobile spyware, follow these steps to find and remove the infected apps or programs.
- Uninstall apps you don't recognize: If you’re on Android, go to your phone's settings, click “Apps,” and uninstall any apps you find suspicious. On iPhones, press and hold the app icon on your home screen, then tap “Remove App.”
- Run an antivirus or malware scan: Use your phone’s default security app or install a reputable security app, like Norton 360 Deluxe, to run a full scan and remove any spyware found.
If uninstalling apps and running a malware scan doesn't fix the problem, consider backing up your data and factory resetting your phone.
How to protect yourself from spyware
You can help protect your devices against spyware by combining good digital habits with the right security tools. Below are a few practices that can help keep your computer, mobile device, and personal data safe.
- Use antivirus software: Reliable antivirus software, like Norton 360 Deluxe, can help detect and block cyberthreats, like infected links, and identify spyware on your device.
- Use a pop-up blocker: Blocking pop-ups helps prevent you accidentally clicking malicious ads that could trigger a spyware download.
- Update operating systems: Regular software updates patch security vulnerabilities that spyware often exploits.
- Don’t open suspicious messages: Unexpected texts or emails, especially with attachments, can be phishing attempts that deliver spyware.
- Don’t click suspicious links: Avoid clicking links from unknown sources, as they can redirect you to spyware-laced websites.
- Only download from trusted sources: Stick to official app stores and reputable websites to reduce the risk of downloading infected software.
- Review app permissions: Apps asking for unnecessary access, like your camera, mic, or location, may be collecting more data than they need.
Protect your data from spyware
With a better understanding of what spyware is and how it functions, you can take steps to keep your devices safer. For added protection against hackers and cybercriminals, get Norton 360 Deluxe. It can help you keep your devices even more secure, with real-time threat protection and advanced AI-powered scam detection.
FAQs
Is spyware a virus?
Spyware and computer viruses are in the same family — they're both types of malware (malicious software). But there are some key differences. Spyware aims to steal your personal information or data without your consent. Viruses are designed to spread from device to device, causing harm along the way.
Can spyware be detected?
Advanced security or anti-malware software can detect spyware. If you've noticed your computer or phone behaving differently (such as running slowly or displaying unusual or especially intrusive pop-ups), run a scan to identify and remove the threat.
Are tracking cookies spyware?
Some tracking cookies can act as spyware. First-party cookies usually enhance your browsing experience. However, third-party cookies, often used by advertisers, can track your activity across sites and may collect or sell your data without your explicit consent.
Is spyware illegal in the US?
Spyware is illegal in the U.S. when used to secretly collect data without a person’s consent. Laws like the Computer Fraud and Abuse Act and state-level statutes ban unauthorized surveillance, especially for malicious or commercial purposes. However, some forms of monitoring software are legal with proper disclosure and consent.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.