Sensitive information: Types, definitions, and examples
Your sensitive information isn’t just precious to you, it’s also valuable to identity thieves. Learn what counts as sensitive information, how and why criminals steal it, and how you can protect it. Then, get security software to help detect threats like malware and scams that could expose your data to cybercriminals.

What is sensitive information?
Sensitive information is any data that could harm, expose, embarrass, or otherwise compromise you if it’s shared, altered, or destroyed without your authorization. This includes information like your Social Security number, financial details, medical history, and other data that requires protection due to its potential for misuse.
It’s a step up from personal information, which is data related to you that doesn’t necessarily pose an immediate or significant risk if disclosed in isolation but could expose you to risk if combined with sensitive information.
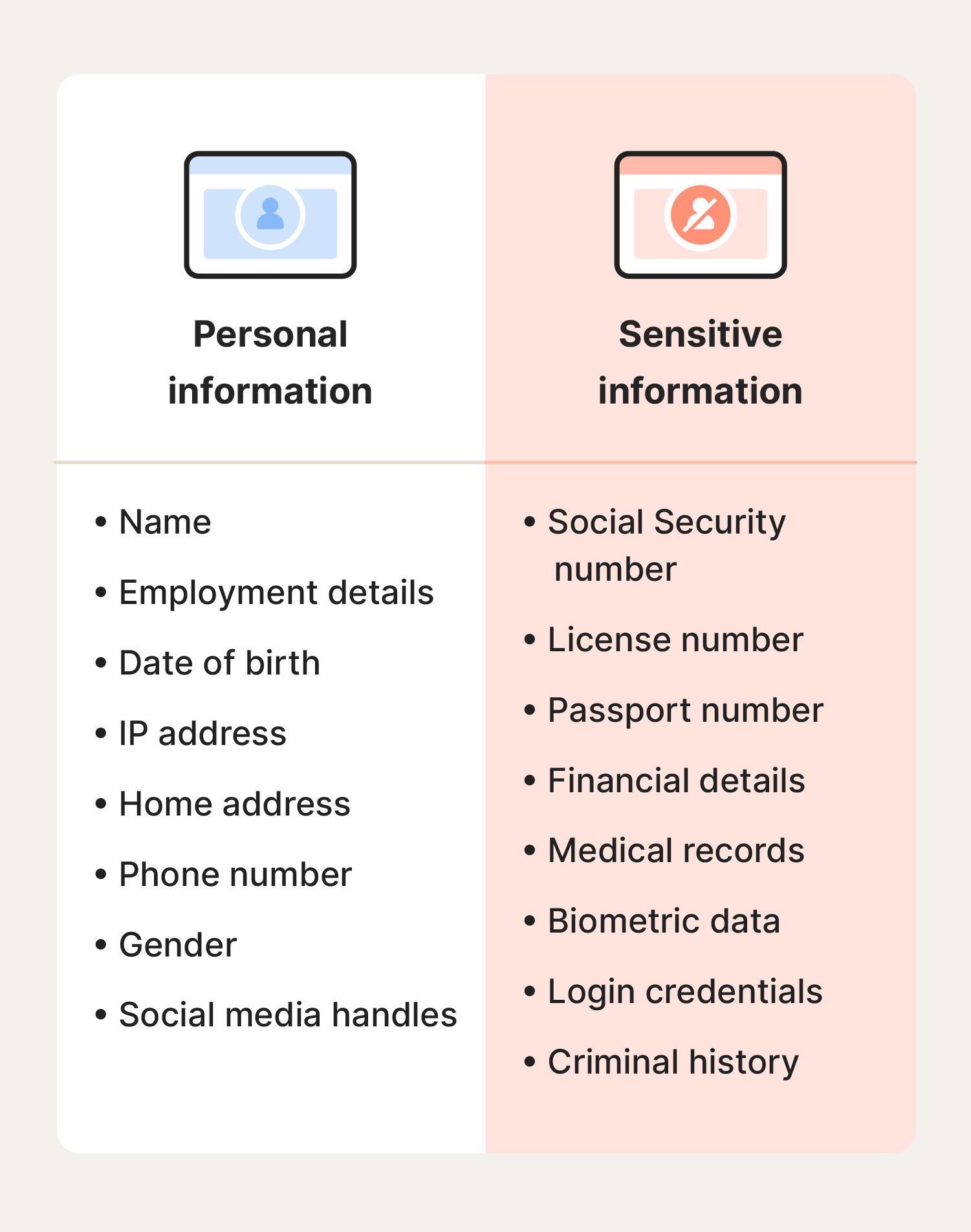

6 common types of sensitive information
Sensitive data can include, but isn't limited to, personally identifiable information (PII), health data, financial information, biometrics, and business information. Some examples of sensitive information include:
- Personally identifiable information like your Social Security number, driver’s license number, or passport number.
- Biometrics like fingerprints, retina scans, voice patterns, DNA, or facial recognition data.
- Health information like medical records, prescriptions, and insurance details.
- Financial information like bank account details, credit card numbers, and tax records.
- Security credentials like passwords, PINs, two-factor authentication codes, and security tokens.
- Sensitive demographic identifiers like race, religious beliefs, sexual orientation, or political opinions.
Reasons you should care about protecting sensitive information
The exposure of sensitive personal information, often facilitated by hackers or data leaks, can lead to identity theft. In turn, the consequences of identity theft can include financial losses, credit score damage, employment issues, legal difficulties, and reputational harm.
On average, it takes 277 days for organizations to detect and resolve data breaches. That’s a lot of time for your information to be exposed. And, in 2024, around 26% of identity theft victims lost more than $5,000, highlighting just one of the potential consequences you face if you don’t take steps to protect your information.
Here’s a closer look at why protecting your private data is so important:
- To avoid credit score and financial damage: Protecting your sensitive information minimizes the risk of identity theft and fraud, which can lead to the opening of unauthorized accounts, fraudulent charges, and credit score damage.
- To protect yourself from reputational damage: Protecting your personal sensitive information can help curb reputational damage by preventing the exposure of compromising information or potentially embarrassing data.
- To prevent legal issues: Protecting your sensitive information can help you avoid legal issues like criminal identity theft, fraud, and other related offenses that can result from stolen data.
How is sensitive information stolen?
Criminals use diverse attack vectors to access sensitive information, including stealing login credentials, extorting targets, installing spyware or ransomware, exploiting system vulnerabilities, launching phishing attacks, leveraging insider threats or errors, stealing physical documents, and pretexting.
Here’s a summary of some of the main ways sensitive information is stolen:
- Stolen credentials: Thieves can try to steal login credentials through phishing, social engineering attacks, system vulnerabilities, and different types of malware. If they get access to one account, they can then try to extract more information to commit identity theft.
- Extortion and ransomware: Attackers may use ransomware to view personal details on your computer and threaten to release it unless you meet their demands.
- Exploit vulnerabilities: Hackers may take advantage of vulnerabilities in software or systems to bypass security measures and access databases of sensitive information. This information can sometimes be leaked in bulk in a data breach, exposing hundreds, thousands, or millions of people at once.
- Phishing: When you open malicious links or attachments sent with a phishing message, attackers may be able to redirect you to a fake login page that steals your data or install malware on your device that grants a hacker access to your sensitive information.
- Insider threats and errors: Insider threats can be either malicious or accidental. Some involve bad actors gaining unauthorized access to sensitive information and intentionally stealing data for personal gain. Others can occur if an employee mishandles files, misconfigures certain systems, or falls victim to a phishing attack.
- Pretexting: This type of social engineering attack involves a criminal fabricating a scenario to trick someone into sharing sensitive information. For example, a criminal might impersonate a bank representative calling to “verify” account details to “secure” a user’s account.
- Malware: Malware like spyware can be used to steal sensitive information by logging keystrokes, capturing screenshots, or granting hackers remote access to files.
- Physical theft: The physical theft of devices like laptops, smartphones, or external hard drives can lead to stolen information, as can the theft of improperly stored or discarded documents.
- Skimming: Skimming is a method of stealing credit card or debit card information by using a device to illegally scan and capture the data encoded on the card's magnetic stripe or chip. This tactic is usually employed at gas pumps and ATMs.
How to protect sensitive information
You can help protect your sensitive information with effective password management, smart document handling, regular software updates, antivirus software, and a commitment to safeguarding your information online.
Here’s some more detail on how to use each strategy to take better care of your sensitive information:
- Set strong passwords: A strong password should be a minimum of 15 characters in length and should never be reused across different accounts.
- Use a password manager: A password manager helps store and manage all your login credentials, making it easier to set strong passwords without fear of forgetting them. Some tools even include features to help you generate new secure passwords.
- Enable two-factor authentication: Two-factor authentication (2FA) protects your accounts by requiring a second form of verification, like a code from your phone, in addition to your password. This helps keep attackers out of your accounts, even if they have your login credentials.
- Lock your devices: Locking your devices with a PIN or biometric authentication prevents unauthorized access if they’re lost or stolen.
- Destroy sensitive documents: Physical documents containing sensitive information like bank statements, medical records, and tax forms should be shredded before you discard them.
- Keep your systems updated: Software updates often include security patches that fix vulnerabilities hackers could exploit to access your data. Install them when they become available to keep your data safer.
- Recognize phishing attempts: Be wary of unexpected emails, especially if they ask for personal information or contain suspicious links. You should also verify the sender's identity before clicking anything.
- Detect and help avoid scams: Phishing attacks and scams can also start on texts or websites — these often have malicious links aimed at capturing your sensitive information. Use antivirus software like Norton 360 Deluxe, which includes an AI-powered scam assistant, to help you avoid suspicious websites and texts.
- Use a VPN on public Wi-Fi: Using a VPN like Norton VPN creates an encrypted connection, shielding your online activity from packet sniffers who may be lurking on public Wi-Fi networks waiting to steal sensitive data.
- Limit what you share online: Avoid sharing information that could easily identify you or your location. Also, be cautious about sharing general details like your pet’s name or maiden name that you may use for security questions and photos that may give attackers insights into your private life.
- Make your online accounts private: Most social media platforms offer the option to make your profile private, which means it’s much harder for strangers to see what you post and misuse the information. The less data about you available publicly, the better.
Monitor for sensitive information exposure
As well as watching out for data-stealing scams, you should monitor your personal information on the internet. Norton 360 Deluxe helps automate this process. It has privacy monitoring capabilities that let you know if we find any of your personal information on the dark web* or people search sites so you can take action to secure your accounts or data.
* Monitoring is not available in all countries and varies based on region.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.










Want more?
Follow us for all the latest news, tips, and updates.