High-profile people and companies among Twitter accounts hacked in Bitcoin scam: Here’s what to watch out for
Twitter hit with hack involving high-profile accounts of billionaires, celebrities, and politicians, in cryptocurrency scam. Learn what happened.

Hackers engineered a broad attack on Twitter on July 15, taking over the accounts of high-profile people and companies including those of Joe Biden, Elon Musk, Kanye West, and Apple, and posting messages requesting money in a Bitcoin scam.
The attack illustrates how companies remain vulnerable to data breaches and how consumers may be susceptible to cryptocurrency scams. The hackers’ fake tweets appeared to generate Bitcoin deposits worth more than $100,000 in the first hour.
Here’s one example of a bogus tweet posted during the Twitter hack.
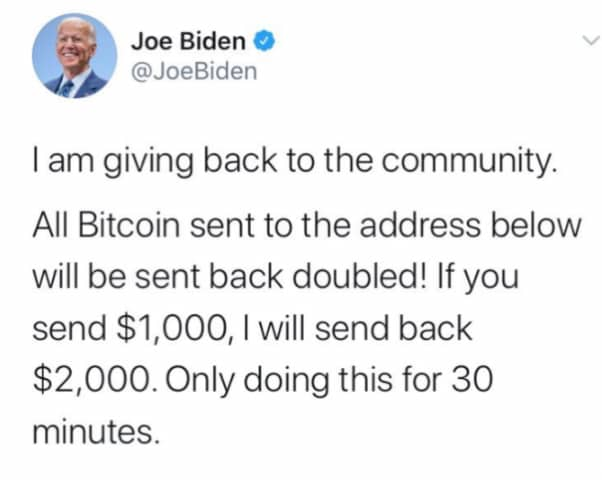
The Twitter hack was reportedly the largest in the history of the San Francisco-based social media company.
The hack could be especially alarming because many world leaders use Twitter — and some, like President Trump, use it to announce major policy decisions. It raises the possibility that scammers might gain access to a powerful tool in an election year.
Cybercriminals and other people — sometimes using what are known as Twitter bots — use social media platforms to scam the public and spread misinformation.
What Twitter accounts were hacked?
The Twitter hack targeted the personal accounts of billionaires, celebrities, business leaders, and companies. Some of the personal accounts have millions of followers.
Here’s a partial list of hacked accounts.
Apple
Jeff Bezos
Joe Biden
Michael Bloomberg
Warren Buffett
Bill Gates
Wiz Khalifa
Elon Musk
Barack Obama
Uber
Wendy’s
Kanye West
Kim Kardashian West
The attack at first took over the accounts of several cryptocurrency-related companies such as Bitcoin, Ripple, and Coinbase. It spread to the accounts of prominent figures and companies.
How did the Twitter hack happen?
Twitter said it believed the attack occurred after hackers targeted certain employees who have access to the company’s internal systems
“We detected what we believe to be a coordinated social engineering attack by people who successfully targeted some of our employees with access to internal systems and tools,” the company wrote in a tweet.
While attackers took over Twitter accounts, it was unclear what other internal information, if any, they may have been able to access.
How does a Bitcoin scam work?
Hackers then used the Twitter breach to take over accounts of high-profile individuals and companies to spread a cryptocurrency scam. Here’s how the scam works.
The scam is straightforward and relies on the large number of people it reaches.
Cybercriminals used the accounts of prominent people or organizations to send tweets claiming that followers can double their money by sending funds to a designated cryptocurrency account. The scam is sometimes described as an “investment.”
Some Twitter users may follow the tweeted instructions. But instead of doubling their money, they lose it entirely to scammers in an often-untraceable cryptocurrency account.
This scam tweet in the Twitter hack, fraudulently sent from Tesla CEO Elon Musk’s account, shows how scammers combined their cryptocurrency scam with a COVID-19 scam.
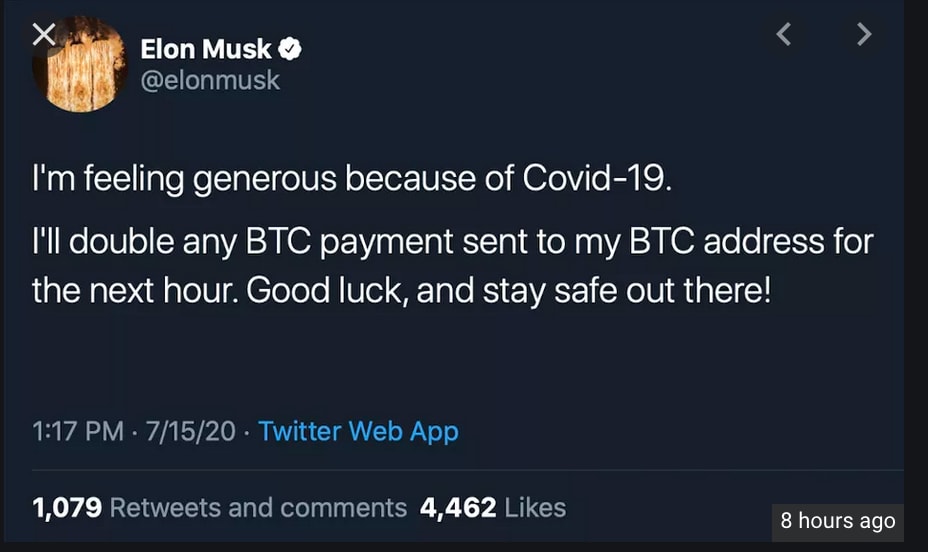
Signs of a scam
The cryptocurrency scam is just one of many ways that scammers try to target people into providing money or sensitive personal information.
Online scams abound. Most of them are designed to access personal and financial information that can be used to commit fraud or sold on the dark web.
Here’s a partial list of online scams:
- Phishing emails.
- Malware and ransomware scams
- Tax-refund scams
- Romance scams
It’s a good idea to learn to know how to recognize online scams and protect yourself against falling for them.
How to keep your social media accounts safer
The Twitter hack is a reminder how cybercriminals might target social media accounts.
If you have social media accounts on platforms such as Twitter, Facebook, Instagram and Snapchat, you won’t be able to prevent cyberattacks on those companies. But you can control the information you post, which cybercriminals may also value.
Tips for protecting your social media privacy include these:
- Reading a social media site’s privacy policy and terms of service.
- Adjusting your privacy settings on each social media platform
- Not sharing private information such as your full name, date of birth, address, or employer.
- Staying on top of privacy concerns in the news.
How to watch out for scams
It’s smart to know how to recognize online scams. One sign is urgency — scammers want you to act quickly. But it’s important to pause and think about whether the request is legitimate.
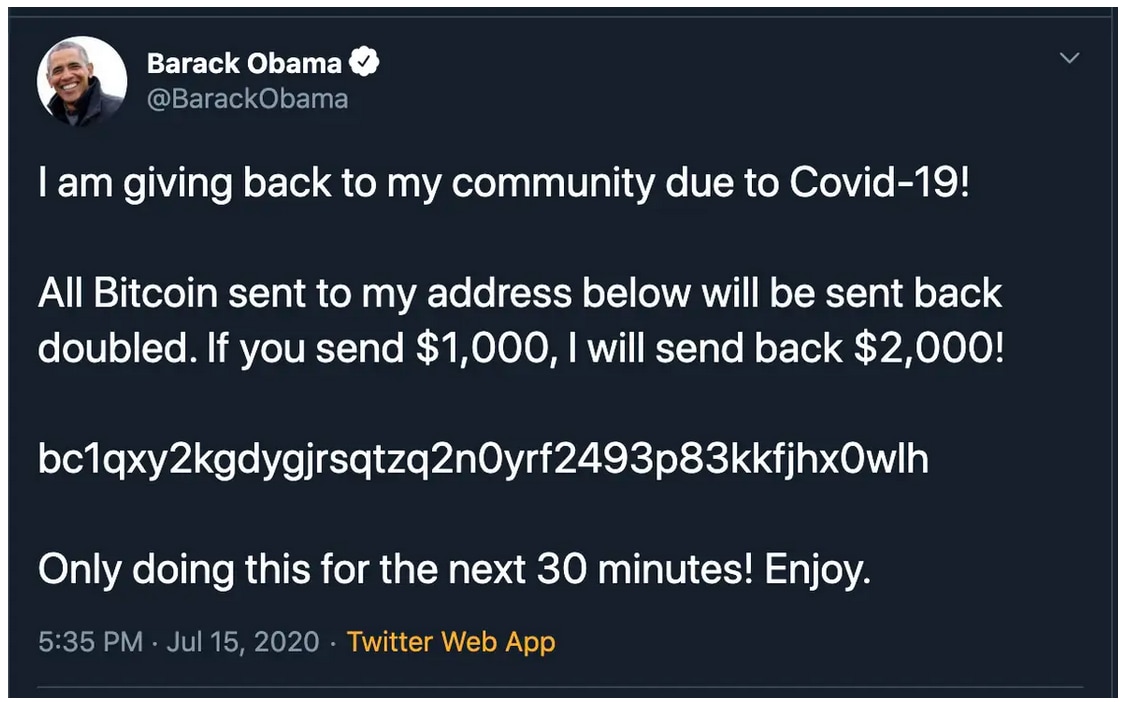
For example, here’s a tweet from Barack Obama’s account in the Twitter hack. It raises the question, Why would a former president of the United States want to double my money? If the answer makes no sense, it’s likely a scam.

Try BotSight for Twitter - FREE Bot Detector Tool
Flag suspected bot accounts on Twitter in real-time. Available on iOS and as a browser extension.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips and updates.