Social engineering scams on social media
Nobody likes being manipulated—and that’s exactly what happens to people when they fall victim to social engineering scams online. In addition to using more sophisticated malware, ransomware, and viruses, online criminals have become increasingly aware of the use and power psychology plays in weaving believable online fiction.

Nobody likes being manipulated—and that’s exactly what happens to people when they fall victim to social engineering scams online. In addition to using more sophisticated malware, ransomware, and viruses, online criminals have become increasingly aware of the use and power psychology plays in weaving believable online fiction. By ‘engineering’ a believable scenario, criminals are able to manipulate users to act on otherwise risky behavior. There’s a dark art to this skill, and it’s one that can cause you and your online network a great deal of distress should you become compromised.
Social media has made it easier for criminals to collect the necessary pieces they need to weave a story or fictional ruse. The common user rarely pays attention to the kinds of personal data they share on social media—from whom they regularly socialize with and where they like to vacation, to specific job information and educational background. However, all these things can paint an incredibly accurate portrait of a user and make him an easy target of a social engineering scam.
Individual Vs. Company Threats
Businesses in particular have a difficult job balancing company security and employee freedom on social media. While some business may have strict policies about what can/can’t be shared on social networking sites like Facebook or Twitter, others don’t have any policies at all.
The problem is that, combined with social media, social engineering scams become increasingly more difficult to spot because they’re coming from seemingly trusted sources: friends, professional references, and even family. If you think you can spot the social engineering scam on social media, you might want to think again.

Things to Avoid
Generally speaking, social engineering is all about the plot leading up to the installation of malware, computer viruses, Trojan horses, and the like. Once a criminal gets a user to activate the bug, the story ceases to be relevant. Understanding the types of behavior criminals will generally request from users will help you determine if you can trust inquires from trusted sources.
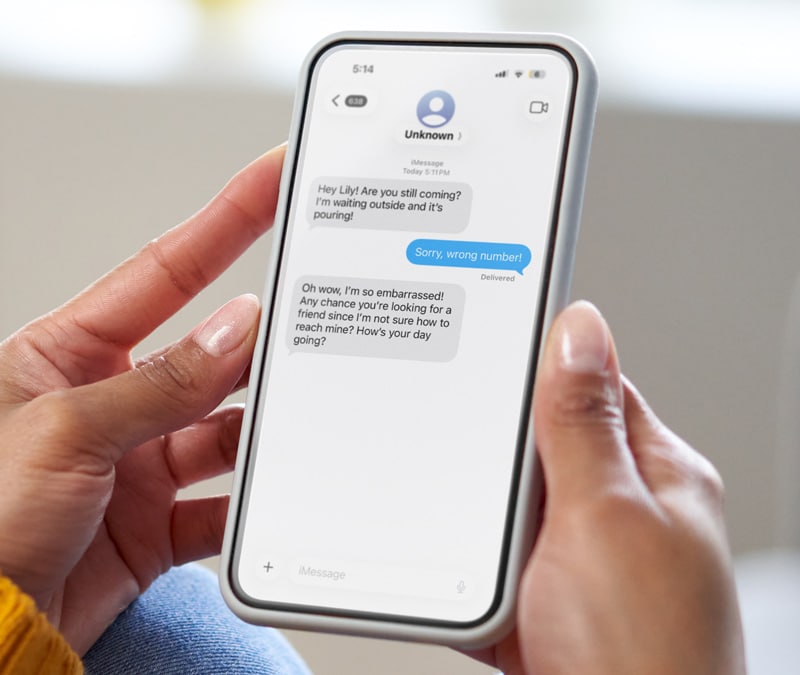
Avoid clicking on suspicious links from emails, online chartrooms, or instant messages. If the URL doesn’t look familiar, or if it’s sent to you from a friend as a shortlink (like a Bitly URL), double check with your source to make sure it’s safe to click on. Clicking on a bad link is like opening Pandora’s box—once it happens, you can’t be sure what you’re going to get. Avoid this type of behavior, even if the message appears to be from someone you know and trust.
Similarly, you should avoid sending money to fundraisers or charities that your friends or family forward to you in emails unless you double-check the source. This is a popular scam, especially around the holidays, when people are more likely to feel philanthropic.
Online scammers can also send bogus links from fake organizations through your friends’ contact lists to get to you. These emails might look normal, as they’re coming from personal contacts. Ask yourself, ‘Has this person ever sent me a message like this before?’ It not, avoid making donations unless you can verify the site. Also, if you suspect your friend’s contact list has been compromised, notify him or her right away.
Finally, you should always be aware of the information you make available on social media. There have been several instances in which security breaches were made in large institutions because of a social engineering scam primarily curated through social media. Always be vigilant. The best thing you can do is to stay current on security trends and install trusted online security software from an established brand like Norton Security.

Don’t wait until a threat strikes.
Security threats and malware lurk on Windows PCs, Macs, and Android and iOS devices. If you use more than one device – like most of us do – you need an all-in-one security suite. Meet Norton Security Premium.
Enjoy peace of mind on every device you use with Norton Security Premium.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.




Want more?
Follow us for all the latest news, tips, and updates.