What is a smurf attack? How it works and prevention tips
A smurf attack is a type of DDoS attack where hackers disrupt a computer network by flooding it with an overwhelming number of Internet Control Message Protocol (ICMP) packets. Find out more about how smurf attacks work, and get Norton 360 Deluxe to help protect against hacking attacks and other online scams.

Just because it sounds cute doesn’t mean it’s harmless. Like its animated counterpart, a smurf attack relies on many small parts joining forces in a distributed denial-of-service (DDoS) attack to take out larger systems.
The name “smurf attack” might conjure up images of the little blue cartoon characters, and there’s a fitting comparison. Just like a village of Smurfs can take down larger enemies by working together, a smurf attack can bring down large networks by flooding them with traffic from many ICMP packets.
In the simplest terms, a smurf attack can overwhelm a network to the point that it stops working.
Keep reading to get a breakdown of what a smurf attack is, the parts that play into smurfing, plus pointers for smurf attack prevention.
The history of smurf attacks
Smurf attacks started in the 1990s as a simple yet effective method to disrupt and overwhelm networks with excessive traffic. Here’s a timeline to help you understand the history of smurfing:
- 1997: Hacker Dan Moschuk, aka TFreak, is believed to have created the code used in smurf attacks.
- Late 1990s to early 2000s: Smurf attacks became more advanced; attackers also used botnets to amplify the impact of their attacks.
- Mid 2000s: More sophisticated DDoS attack methods emerged and smurf attacks became less prevalent.
- Current day: Smurfing attacks are relatively rare due to improved network configurations and security measures.
Though smurf attacks are less common today, they still pose a potential threat and serve as a cautionary example of the need for robust network security. Newer types of DDoS attacks are still prevalent, so the threat is real — knowing how they work and how to help protect your network is key.
How does a smurf attack work?
Smurf attacks work by flooding a network with a large number of spoofed ICMP packets or echo requests, overwhelming the target and causing the network to become inoperable.
Here’s a step-by-step breakdown of how a smurf attack works:
- Sending a spoofed ICMP Echo Request: The hacker sends an ICMP Echo Request to the broadcast address of a network. The source IP address of the packet request is spoofed to appear like it came from the target victim’s network.
- Broadcasting to all devices: The ICMP Echo Request reaches all devices on the network via the broadcast address. Each device interprets the request as legitimate and prepares a response.
- Devices generate ICMP Echo Replies: The devices on the broadcast network respond with an ICMP Echo Reply, directed at the spoofed IP address (the smurf attack victim).
- The victim is flooded with replies: The victim receives an overwhelming flood of ICMP packets (Echo Replies) that saturate the target network’s bandwidth and exhaust its processing capacity, leading to service disruption or complete denial of service.
Smurf attack vs. fraggle attack
Smurf attacks and fraggle attacks are both DDoS techniques, except fraggle attacks send User Datagram Protocol (UDP) Requests instead of ICMP Echo Requests. Despite using different protocols, both exploit IP vulnerabilities, leveraging broadcast networks to overwhelm victims with traffic, and achieve similar disruptive results.
Types of smurf attacks
Generally, smurf attacks can be categorized as basic or advanced. The difference lies in the degree of the DDoS attack that follows.
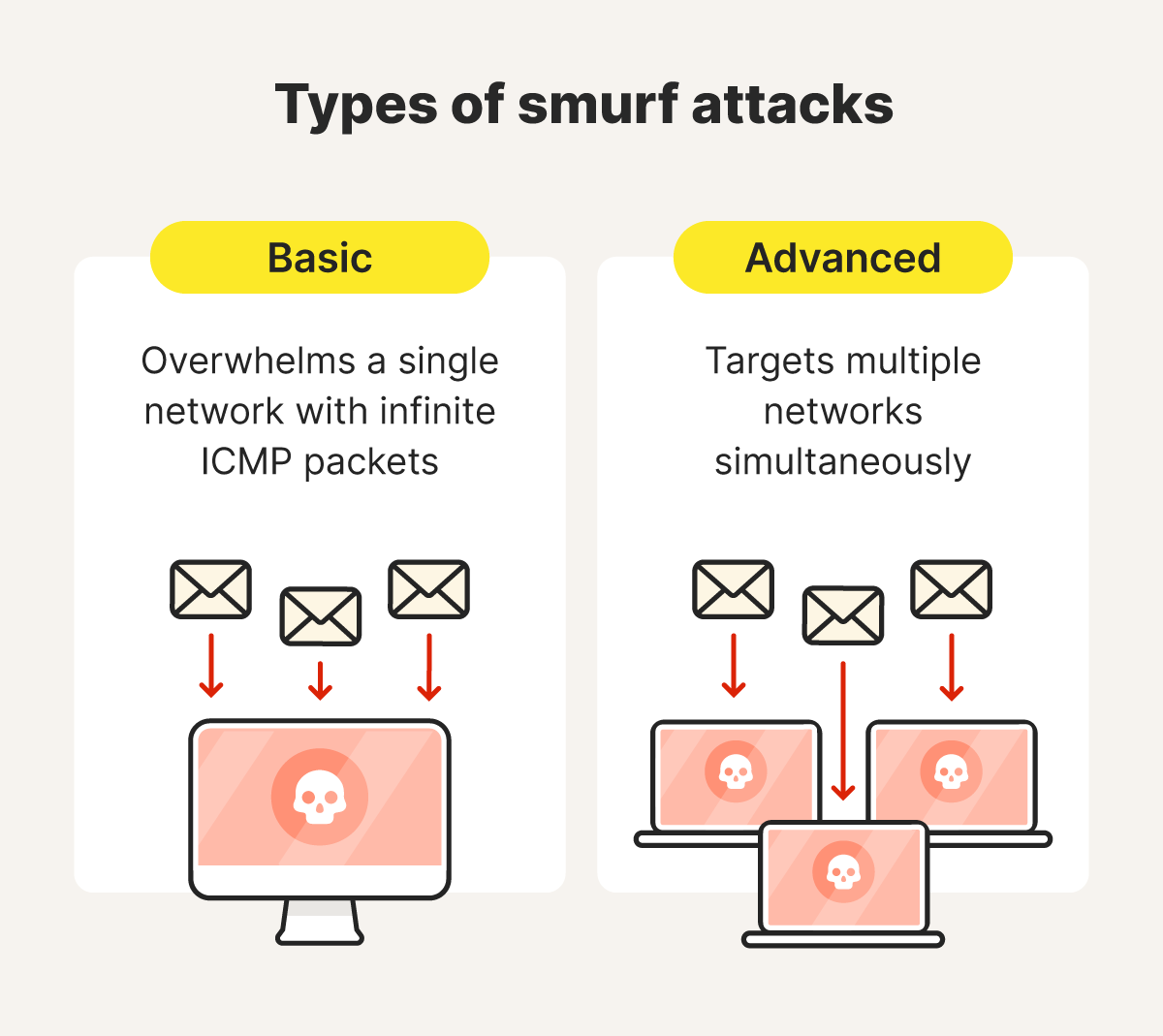

Basic smurf attacks
A basic smurf attack overwhelms a single network by sending fake ICMP Echo Requests to its broadcast address, using the victim's IP address. The network devices respond with Echo Replies, flooding the victim with traffic until their server or network becomes overloaded and inoperable.
Advanced smurf attacks
An advanced smurf attack targets multiple networks simultaneously. They often involve botnets, amplifying the attack’s scale and causing disruptions across networks and devices, leading to widespread internet issues.
Causes and effects of smurf attacks
The main causes of a smurf attack lie in the exploitation of network vulnerabilities and misconfigurations. For companies, smurf attacks can cripple servers indefinitely, resulting in disruption, loss of revenue, and potentially reputational damage.
Here are some of the causes or issues that can leave computer systems vulnerable to smurfing:
- Misconfigured networks: Networks that allow broadcast traffic enable attackers to send ICMP Echo Requests to all devices within the broadcast range.
- Lack of ingress filtering: Without proper ingress filtering, routers cannot block packets with spoofed source IP addresses.
- Legacy network protocols: Older devices and networks often have vulnerabilities in protocols like ICMP, which attackers can exploit.
- Unsecured devices: Devices on networks with poorly configured firewalls or security settings can amplify attacks by responding to spoofed ICMP requests.
These days, it’s relatively easy to protect against smurf attacks and the disruption they bring.
How to mitigate smurf DDoS attacks
While it is rare that individuals are targeted, it’s always a good idea to protect your network and make it harder for smurfing and other DDoS attacks to succeed. The best ways to help protect against smurf attacks are to configure network devices to block ICMP echo requests, update your router and firewall settings, and implement intrusion detection systems to monitor for suspicious network activity.
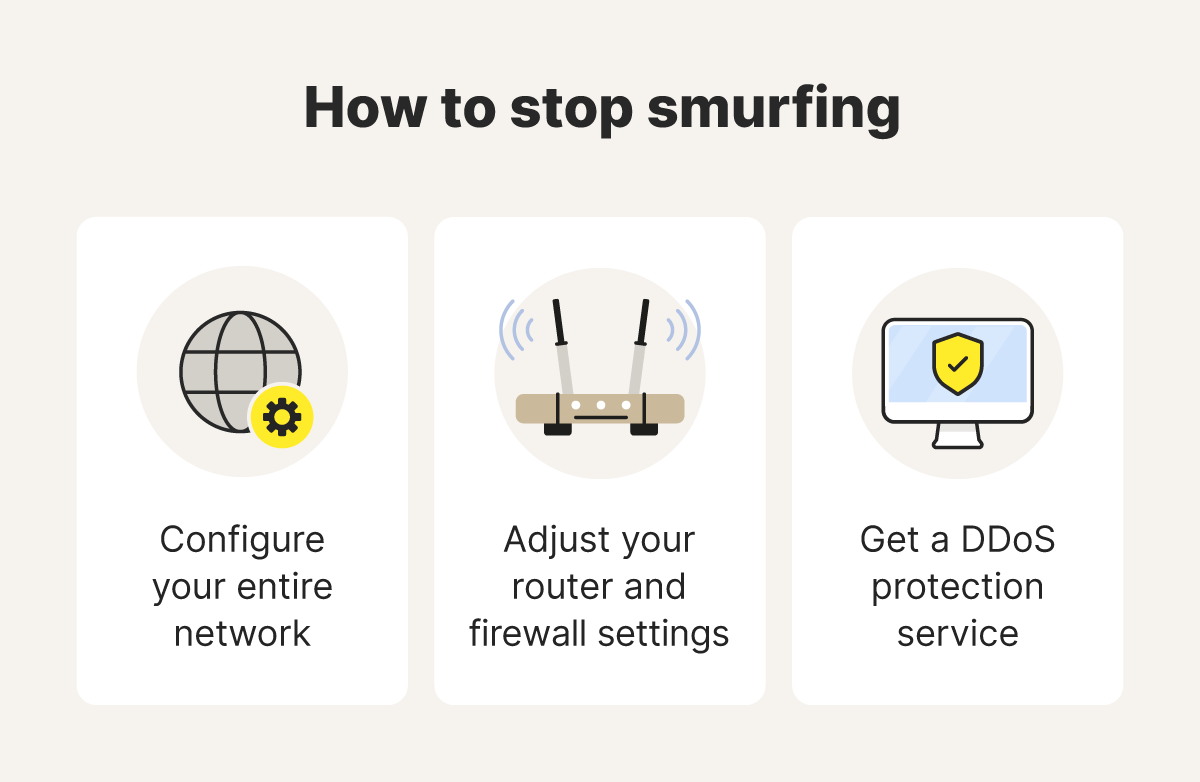

Here’s what you need to know to get started:
- Network configuration: The first thing to do is check that IP broadcast addressing is disabled on your router. This is typically disabled by default on modern home routers, but some older routers don’t do this.
- Router and firewall configuration: Improve the security of your router and firewall by configuring them so they don’t forward or respond to ICMP Echo Requests. Also, make sure you keep your router firmware updated to benefit from security patches.
- DDoS protection services: Use a service that can help protect against DDoS threats like smurfing by blocking suspicious traffic and monitoring network activity.
Smurf attacks don’t usually target individuals, because they’re designed to overwhelm systems or networks. Some more common targets include organizations, internet service providers (ISPs), and online services like e-commerce sites.
But there are plenty of online threats that do target individuals, including different types of hacking attacks that threaten networks and devices.
Get protection against modern-day online threats
Online threats these days are much more sophisticated and harder to spot than they were in the internet’s early days. That’s why you need Norton 360 Deluxe and its powerful, heuristic threat-detection engine, which helps to keep your devices safe against today’s advanced online threats. Install Norton 360 today and see why it’s trusted by millions of customers around the globe.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.