Hacktivism: Definition, types, + newsworthy attacks
Hacktivism is the act of using technical hacking skills to fight for a cause or expose a perceived injustice. Follow this guide to learn more about hacktivists, their motivations, and hacktivist attacks making headlines. While hacktivists rarely target everyday internet users, cybersecurity software like Norton 360 Deluxe can help protect your device against various types of hackers, no matter their motivation.

What is hacktivism?

Made up from the two words “hacking” and “activism,” hacktivism is a term used to describe hacking into unauthorized networks to expose a perceived injustice. Hacktivism is much like activism in our physical world, whereby people cause disruption to bring about change. With hacktivism, the disruption is entirely online and usually conducted anonymously. While not all hacktivists have malicious intent, their attacks can have real-life consequences.
For example, personal information exposed by hacktivists may be picked up by other bad actors to carry out cyberattacks. Not only that, but hacktivist attacks can expose sensitive information, like where a person lives, which can be dangerous if found by the wrong people. In some cases, hacktivists may use their skills to fight for a cause, even if the outcome is malicious.
Who do hacktivists target?
People who carry out hacktivism attacks are hacktivists, and their targets include government agencies, multinational corporations, and powerful individuals. Hacktivists may target any group or individual they consider unjust or in the way of a particular cause.
What motivates hacktivists?
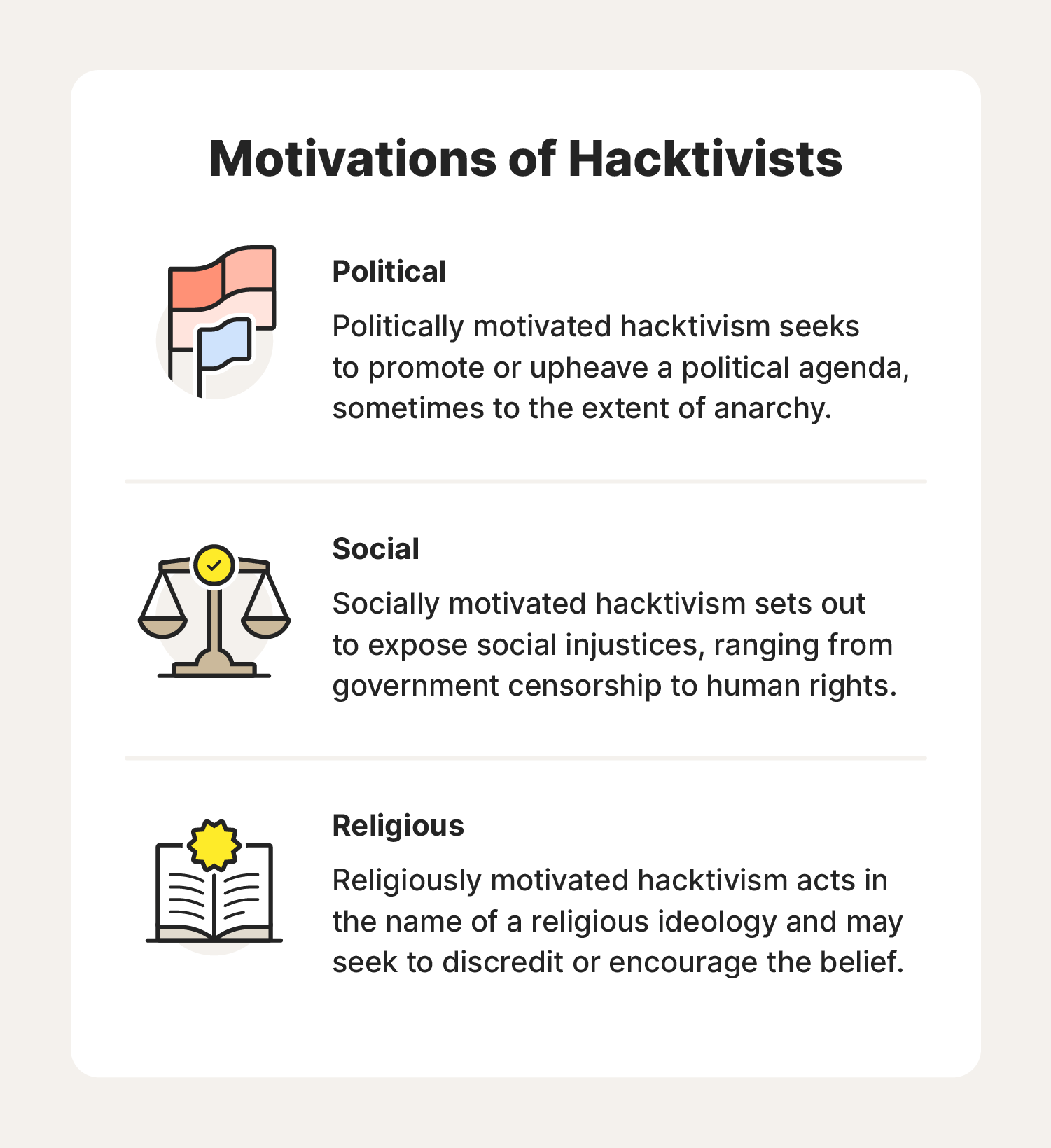
Hacktivists may be a single person or a group of hackers fighting for a specific cause. The exact motivations of a hacktivist can vary from case to case, but may include:
- Politically motivated hacktivism seeks to promote or upheave a political agenda, sometimes to the extent of anarchy.
- Socially motivated hacktivism sets out to expose social injustices, ranging from government censorship to human rights.
- Religiously motivated hacktivism acts in the name of a religious ideology and may seek to discredit or encourage a certain belief system.
Similar to activism in our physical world, online activists seek to bring public attention to a cause that’s important to them in hopes they’ll invoke change, no matter their specific motivation.
Types of hacktivism
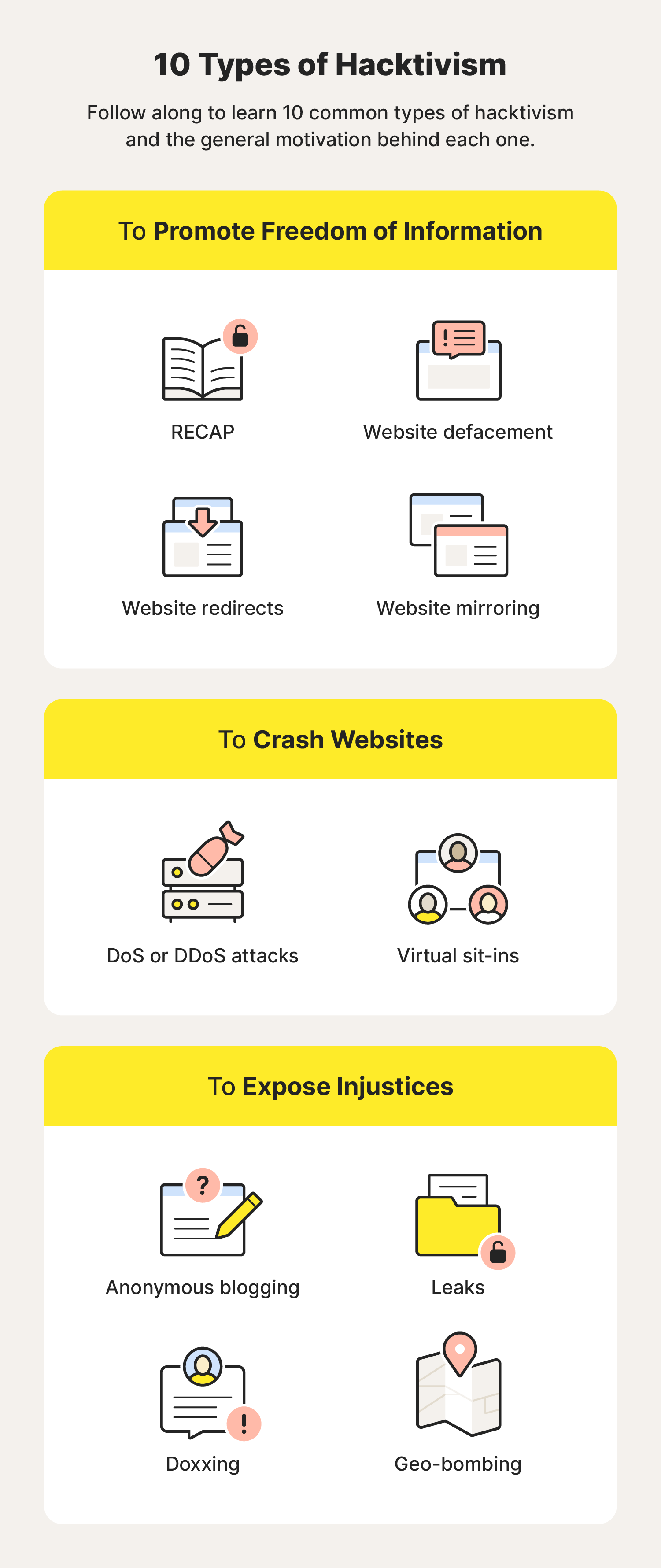
Hacktivism comes in many forms, each with its own way to support a hacktivist’s intentions. That might be promoting free speech and information, crashing websites, or exposing incriminating information. Here are 10 common types of hacktivism:
- RECAP is software that provides free access to documents stored on a database used by US federal courts known as Public Access to Court Electronic Records (PACER)—RECAP is PACER spelled backward—to push a freedom-of-information agenda.
- Website defacement is when hacktivists change the visual appearance of a website to push messaging that underscores a cause important to the hacktivist group.
- Website redirects change the address of a website to redirect visitors to a site that supports a hacktivist’s agenda.
- Website mirroring is a workaround for censored websites whereby hacktivists copy a censored website and post it on a site with a modified URL for all to see. It promotes freedom of information.
- Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks prevent targets from accessing their computers and sometimes crash websites by installing traffic-inundating malware.
- Virtual sit-ins are like manual DoS or DDoS attacks executed by individual users, not software, who repeatedly load webpages to overwhelm a site to the degree that the site crashes.
- Anonymous blogging is when a hacktivist blogs under an anonymous name, often to protect a whistleblower who is exposing an injustice. It could be considered a form of free speech.
- Leaks are usually the result of an inside source sharing classified intelligence with hacktivists, who then share the intel publicly in hopes of causing incrimination, embarrassment, or change.
- Doxxing is similar to a data leak in that hacktivists gather and expose intelligence in hopes of causing incrimination, embarrassment, or change. In some cases, doxxing can have dangerous real-world consequences as it may lead to the exposure of your home address, informing strangers of where you live.
- Geo-bombing exposes the Google Earth location where YouTube videos are filmed. It’s been used to reveal the location of political prisoners and detained human rights activists.
Some hacktivist groups may specialize in one type of hacktivism, whereas others may use whatever combination of hacktivist methods they need to achieve their end goal.
Hacktivism in the news: 10 high-profile attacks
Since the first known hacktivism attack in 1989, hacktivism has evolved exponentially—attacks are more frequent, with newsworthy attacks happening seemingly every week. Follow along to learn more about 10 different hacktivism examples that have made headlines in the past two decades.
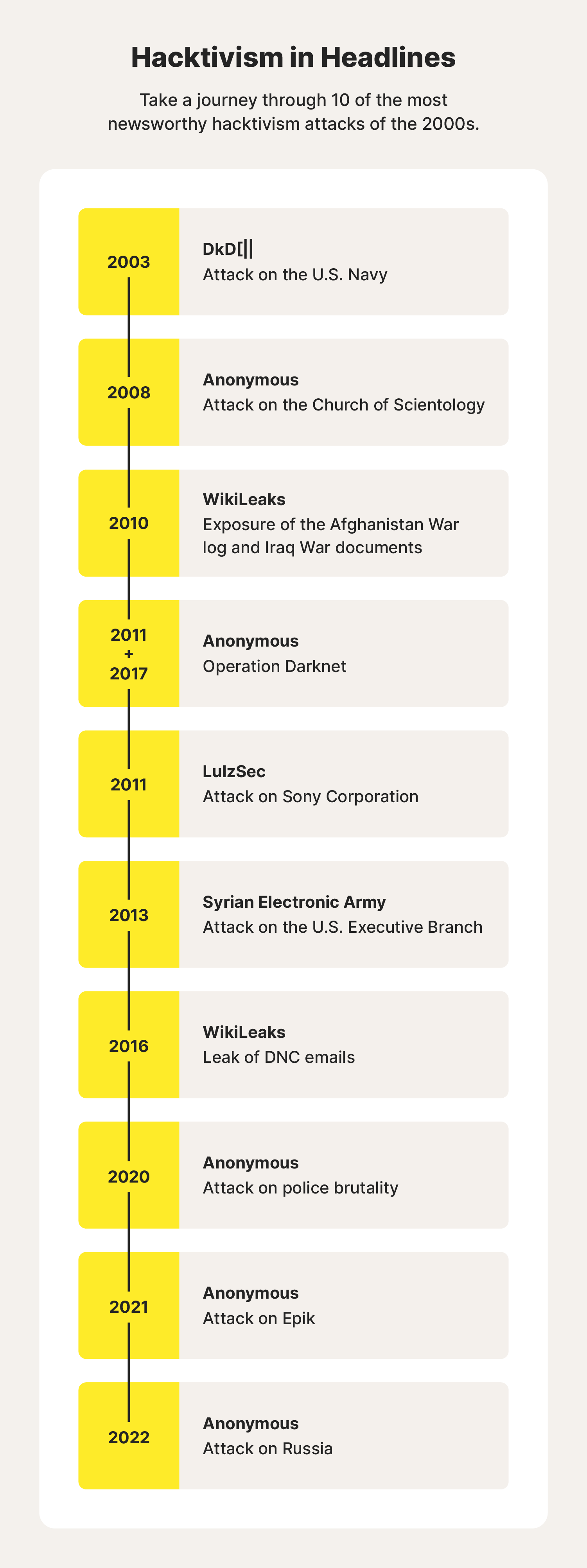
1. DkD[||’s attack on the U.S. Navy, 2003
- Motivation: Political
- Type of attack: Defacement
DkD[|| is a French hacktivist whose preferred attack type is website defacing, including the U.S. Navy site, among thousands of others.
Motivated by politics and spreading messages against U.S. military policies, the single actor was once among the most-wanted hacktivists in France. He also was allegedly a 17-year-old, leading some to believe the attacks were motivated by a desire to show off technical skills rather than to express political viewpoints.
Among DkD[||’s most high-profile hacktivist attacks was the defacement of a U.S. Navy server in 2003 with an anti-Bush message. Following the attack, DkD[|| was arrested, and his website was taken over by a message that the U.S. government now owned it.
2. Anonymous’ attack on the Church of Scientology, 2008
- Motivation: Social and religious
- Type of attack: DDoS attack and doxxing
When people think of hacktivism, many think of Anonymous. This international hacktivist group grew out of the online message board 4chan in 2003 and continues to make headlines. It aims to keep the internet transparent and favors more brazen hacktivism attack types to do it.
Regarded as their first high-profile attack, the group performed a DDoS attack on the Church of Scientology in protest of censorship after the church removed a video of Tom Cruise affirming his affiliation with the church. The DDoS attacks spurred an onslaught of prank calls and black faxes toward the church, and Anonymous rounded out its attack by doxxing the church.
3. WikiLeaks’ exposure of the Afghanistan War log and Iraq War documents, 2010
- Motivation: Political and social
- Type of attack: Leaks
Founded by Julian Assange, WikiLeaks is essentially a whistleblowing organization. As the name indicates, its preferred hacktivism attack type is leaks, and it has been a hosting domain of leaked documents since its launch in 2006.
The first of many high-profile attacks by WikiLeaks, the hacktivist group published around 75,000 pages about the U.S. War in Afghanistan, aka the “Afghan War Diary,” in 2010. The classified documents contained intel on airstrikes that harmed civilians.
The purpose of this attack was to promote the freedom of information and government transparency. It worked to some degree—WikiLeaks released the logs to media outlets such as The Guardian and The New York Times that ran with the story.
A few months after the Afghan War Diary leak, WikiLeaks published nearly 400,000 field reports from the Iraq War. The documents exposed that the civilian death count was much higher than initially reported. The Iraq War documents leak is one of the largest classified document leaks in U.S. history.
4. Anonymous’ Operation Darknet, 2011 + 2017
- Motivation: Social
- Type of attack: DDoS attack
In a move to oust illicit content from the dark web, Anonymous carried out Operation Darknet in 2011. The result? Anonymous DDoSed around 40 anonymously hosted child pornography sites and published the usernames of roughly 1,500 people who visited them.
The group relaunched Operation Darknet in 2017 when it hacked servers on Freedom Hosting II—50% of which were hosting child pornography, according to Anonymous. Based on some reports, this hack disabled 20% of the dark web.
5. LulzSec’s attack on Sony Corporation, 2011
- Motivation: Social
- Type of attack: Doxxing (via SQL injection)
Formed in 2011 by former members of Anonymous, LulzSec is also known as Lulz Security. The Anonymous spin-off group has targeted high-profile entities, often to draw attention to weakened cybersecurity systems and poor privacy protections.
In an attempt to make an example of Sony’s weak security measures, LulzSec committed a string of hacks on the company in 2011 that compromised the personal information of more than 1 million Sony users.
The group did this using SQL injection to gather users’ confidential information like email addresses, passwords, birthdays, and home addresses, and then posted that information on its website, essentially doxxing Sony. As a result, around 100,000 Sony users saw their privacy compromised, and it cost Sony at least $600,000 to recover from the disaster.
6. Syrian Electronic Army’s attack on the U.S. Executive Branch, 2013
- Motivation: Political
- Type of attack: Defacement
The Syrian Electronic Army emerged in 2011, supporting Syrian President Bashar al-Assad. The group commits attacks it believes protect the president and Syria. Its preferred hacktivism attack type is DDoS attacks, including against U.S. agencies.
To tone down what they viewed as fabricated news about the Syrian government in 2013, the Syrian Electronic Army defaced Western news organizations by posting fabricated news on their websites and social media accounts.
One instance involved a fake tweet from the Associated Press about an injury President Barack Obama sustained in an explosion at the White House. This resulted in the Dow Jones dipping by about 140 points.
7. WikiLeaks’ leak of DNC emails, 2016
- Motivation: Political
- Type of attack: Leaks
In the lead-up to the 2016 presidential election, WikiLeaks worked with a foreign intelligence agency to publish almost 20,000 emails and 8,000 email attachments from the Democratic National Committee (DNC).
This included emails sent by presidential hopeful Hillary Clinton and correspondences with DNC donors containing confidential information like Social Security numbers. As a result, at least 12 Russian hackers were indicted by the U.S. Department of Justice.
8. Anonymous’ attack on police brutality, 2020
- Motivation: Political and social
- Type of attack: DDoS attack and defacement
Following the death of George Floyd in 2020, Anonymous sought to expose perceived corruption within the Minneapolis Police Department. It used a DDoS attack to do just that, disabling the department’s website. To further condemn police brutality, Anonymous crashed police department sites around the country and defaced other networks.
9. Anonymous’ attack on Epik, 2021
- Motivation: Political and social
- Type of attack: Doxxing
In 2021, hackers who identified themselves as members of Anonymous targeted the web hosting company Epik in a data breach. The leaked data included purchase records, internal company emails, and customer information.
This attack was politically motivated, as Epik is known for doing business with far-right groups, including the Oath Keepers and the Proud Boys. By leaking this information, researchers and journalists could more easily identify those affiliated with these extremist groups.
10. Anonymous’ attack on Russia, 2022
- Motivation: Political and social
- Type of attack: Defacement and doxxing
Anonymous has also carried out several hacktivist attacks against various Russian targets since the 2022 invasion of Ukraine. These attacks varied from defacing state-owned websites to leaking the personal information of Russian soldiers. Anonymous carried out these attacks to help spread anti-propaganda messages and speak against the invasion of Ukraine.
With a better idea of what hacktivism is, how it works, and what it looks like in the news, you can quickly identify it and better understand the intentions of popular hacktivism groups like Anonymous.
Help keep your device free of hackers with Norton 360 Deluxe
While it is unlikely that hacktivists would target the average person, there are plenty of everyday hackers looking to carry out cyberattacks on unsuspecting internet users. With features like comprehensive malware protection, dark web monitoring, and a VPN that can help keep your internet activity private, cybersecurity software like Norton 360 Deluxe can help protect you and your devices from hackers, no matter their intentions.
FAQs about hacktivism
Read through our FAQ section to help bring clarity to the wild world of hacktivism.
What’s the difference between hacktivism and cyberterrorism?
Hacktivism involves using hacking skills for political or social activism, often to raise awareness or advocate for a cause. Cyberterrorism, on the other hand, involves using similar hacking techniques to cause fear, harm, or disruption. In severe cases, cyberterrorism may involve targeting critical infrastructure or systems to cause loss of life or severe economic damage.
It’s important to remember that not everybody has the same opinion on hacktivism and cyberterrorism. For example, what one person perceives as an act of hacktivism might be seen as an act of cyberterrorism by someone else.
Is hacktivism ethical?
The ethical nature of hacktivism is a subject of debate and depends on one's perspective. While some examples of hacktivism may be seen by some as ethical, hacking itself is always illegal. Additionally, hacktivism attacks can have real-world consequences and put targeted people at risk if their personal information is exposed.
What are the differences between hacking and hacktivism?
A hacker may use their technical expertise for legal or illegal purposes, such as gaining unauthorized access to systems or spreading different types of malware. On the other hand, a hacktivist is a hacker with a specific political or social agenda, using their skills to promote a cause or protest against perceived injustices.
Is hacktivism illegal?
Despite any altruistic intentions, hacktivism attacks are hacking attacks, which means they’re illegal. But they’re also difficult to prosecute because they’re mostly conducted anonymously.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





![15 infamous hacker groups to look for [1981 to 2024]](/content/dam/blogs/images/norton/am/hacker-groups-hero-706w.jpg)

Want more?
Follow us for all the latest news, tips, and updates.