The top social media threats
Social media connects us like never before, bringing us closer to friends, family… and cybercriminals. From data breaches to cyberbullying, the very platforms that foster community can also harbor dangers. Learn how to spot social media threats, and get Norton 360 to help protect you while you scroll.

Social media threats run the gamut from phishing scams to cyberbullying. Their purpose is typically to steal your money or personal data, spread misinformation, or intimidate other users.
What the experts say
"Each platform’s distinct features and audience shape the strategies cybercriminals use to exploit them... from phishing links on messaging apps to fake profiles on traditional social networks." - Gen 2024 Threat Report
Luis Corrons, Security Evangelist
More than half of the world’s population uses social media to connect with friends and family, network, share ideas, and consume news and entertainment. To stay ahead of fraudsters and social media threats, you need to learn which are the riskiest social media platforms (Facebook leads the pack), how to identify and protect yourself from fake romances, online harassment, counterfeit goods, misinformation, and more.
1. Phishing
Phishing is a cyberattack in which scammers use fake links and attachments to trick people into revealing sensitive information. On social media, these phishing attacks can appear in direct messages, posts, clickbait articles, ads, or comments. Other social media threats, like fake giveaways and impersonation scams, also employ phishing tactics.
Phishing attacks can guide users to malicious websites or trigger a malware download. In fact, scam ads leading to malicious websites were the top social media threat that Norton and other Gen Digital products protected users from, accounting for 30% of all cases across social media platforms, with other types of phishing accounting for 22% of social media threats.
Phishing scammers use social engineering to appear innocent, allowing them to request personal information without you suspecting that something is off.
- How it happens: The phisher comes up with a ruse to trick social media users into clicking a link that infects their device with malware or directs them to a dangerous site. Their ultimate goal is usually to steal your money or personal data.
- How to protect yourself: Be wary of unsolicited messages and closely review links for signs of phishing before clicking. If you get an unusual request from a friend, contact them on a different platform or communication channel to confirm they really sent it.
2. Identity theft
Social media can put you at risk of identity theft if you click a phishing link, overshare on your profile, or fall for a social engineering attack. Through these means, attackers can get their hands on information like your phone number, address, pet’s name, email address, passwords, financial details, Social Security number, and work history.
Once they’ve gathered enough personal information, scammers can:
- Create a new account to impersonate you and defraud your friends and family.
- Take over your social media accounts to spread misinformation, damage your reputation, or fool your followers.
- Create a synthetic identity to commit fraud, open credit accounts, file fraudulent tax returns, or even take out loans in your name.
- Sell your personal details on the dark web to other cybercriminals.
Depending on the scenario you find yourself in, you may end up dealing with financial, legal, and reputational damages.
- How it happens: Identity theft can occur on social media through phishing attacks, social engineering, poor account security, and data breaches.
- How to protect yourself: Be cautious of suspicious links, use strong, unique passwords, enable two-factor authentication, and make sure your accounts are private.
3. Social engineering
Social engineering describes any psychological manipulation a scammer uses to trick you into revealing personal information. On social media, this usually comes in the form of a direct message where a fraudster poses as a friend, family member, love interest, follower, professional connection, or organization to gain your trust and steal money or information.
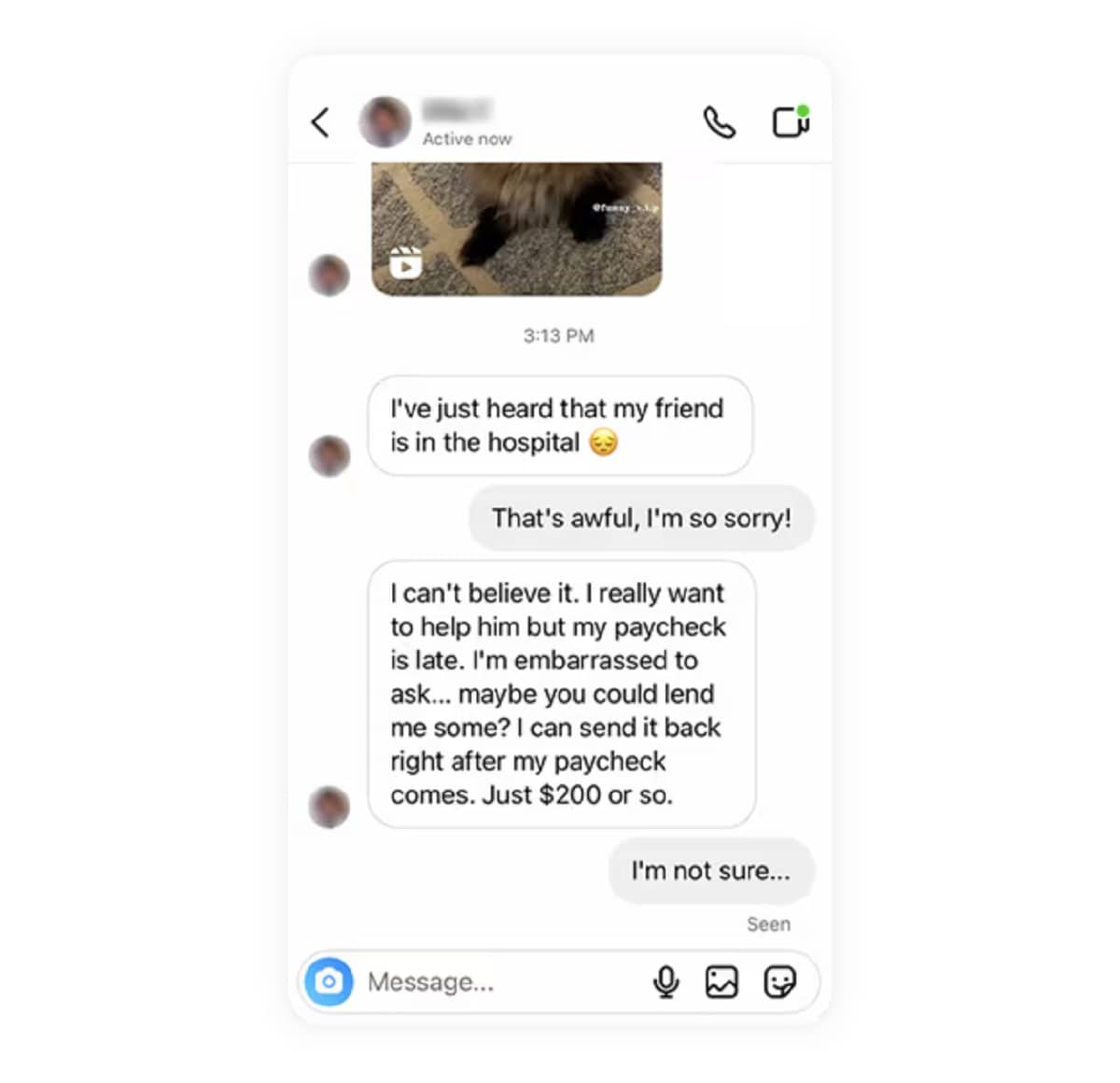

- How it happens: Social engineering uses impersonation and psychological manipulation to trick users into revealing personal information. The scammer might gather information about you before contacting you, making them seem more familiar and trustworthy.
- How to protect yourself: Be wary of unsolicited direct messages or unusual requests from your contacts, especially if they seem urgent or emotionally charged.
4. Cyberbullying
Cyberbullying on social media happens when someone uses the platform to harass, threaten, or intimidate their target. Bullies might send nasty messages and threats, spread rumors, or post embarrassing photos. In other cases, they may dox their target and encourage other social media users to do their dirty work for them.
Victims of cyberbullying can experience severe emotional distress, including anxiety, depression, and low self-esteem.
- How it happens: Cyberbullies threaten or harass their victim by posting hurtful content on the victim’s page or sending direct messages. Even if the victim blocks them, the bully could continue to post harmful content about the victim.
- How to protect yourself: Keep your social media accounts private, be careful about what you post, block and report bullies, and mute any words or phrases that cause you stress.
5. Cyberstalking
Cyberstalking on social media involves persistent and unwanted attention, threats, harassment, and monitoring of the victim. For example, a cyberstalker may repeatedly message their target, track their online activity, or share private information without their consent. This invasive behavior can have psychological consequences, causing fear, anxiety, and social isolation.


- How it happens: Cyberstalkers often start by monitoring a victim’s social media profiles; they then contact the target with messages or comments that are intended to do harm. Some cyberstalkers eventually attempt to manipulate or blackmail their victims.
- How to protect yourself: Make your social media accounts private, be cautious about what personal information and photos you share online, and report any cyberstalkers to the platform and local authorities.
6. Fake giveaways
With fake giveaways, scammers post fake competitions or prizes on social media to lure people to a spoofed website. Once you’re on their site, they may try to infect your device with malware or collect your banking information, emails, and other forms of personal data to exploit you.
- How it happens: Scammers might impersonate a business or create a random page, then create misleading contests or fake prize giveaways, posting them alongside phishing links to trick users into sharing personal information or downloading malicious software.
- How to protect yourself: Avoid clicking suspicious links in giveaways that sound too good to be true, you can’t verify are real, and aren’t posted on the business’s official social media account.
7. Fake goods and services
Social media platforms can be hotbeds for the sale of counterfeit goods and fake services. From “luxury” handbags and “brand name” electronics to fake services like catering and photography, these scams are often advertised through ads or posted on social media marketplaces.
- How it happens: Fraudsters peddle irresistible goods and services on social media at low prices. If successful, users are lured by good deals on supposedly high-value listings. But in the end, most will overpay for nonexistent, dangerous, non-functioning, or fake products.
- How to protect yourself: Check buyer reviews on marketplaces, don’t fall for too-good-to-be-true deals, only communicate on the marketplace, and only make payments through secure platforms with buyer protection.
8. Data breaches
Social media sites have been well-known targets for data breaches, even as popular platforms try to enhance their approach to protecting user data. Facebook suffered a big breach in 2019, and Twitter has also seen large amounts of user data leak online.
That’s why you need to take precautions to protect data like your passwords, credit card information, and other personal information.
- How it happens: Data can be stolen from social media platforms through hacking, phishing attacks, employee error, or system vulnerabilities. Once the data is breached or leaked, cybercriminals can use it in further attacks or sell it on the dark web.
- How to protect yourself: Share as little personal information as possible with the platform, to mitigate damage if there is a data breach. Monitor for data breaches regularly so you can secure any compromised accounts.
You should monitor your personal information on the surface web and the dark web. As soon as you see any breached data, help secure any compromised account by changing your login details straight away.
Norton 360 Standard comes with a powerful antivirus engine and a dark web monitoring feature that carefully scans the dark web and notifies you if your information is found. Get it now to help protect your data and your device.
9. Malware
Malware is harmful software that can infiltrate your device and steal personal information, encrypt files, cause system damage, and even lock you out. You may unknowingly download malware from malicious links found on social media.
There are several types of malware that can lurk on social media, including:
- Viruses: Self-replicating programs that spread to other devices and can corrupt files or damage operating systems.
- Worms: Self-multiplying malware that can spread rapidly across networks, often exploiting vulnerabilities in software.
- Adware: Programs that display unwanted advertisements, often slowing down devices and compromising privacy.
- Spyware: Software that secretly monitors user activity, collecting sensitive information like passwords and browsing activity.
- Trojans: Malicious programs disguised as legitimate software, often used to install other malware or provide backdoor access to a device.
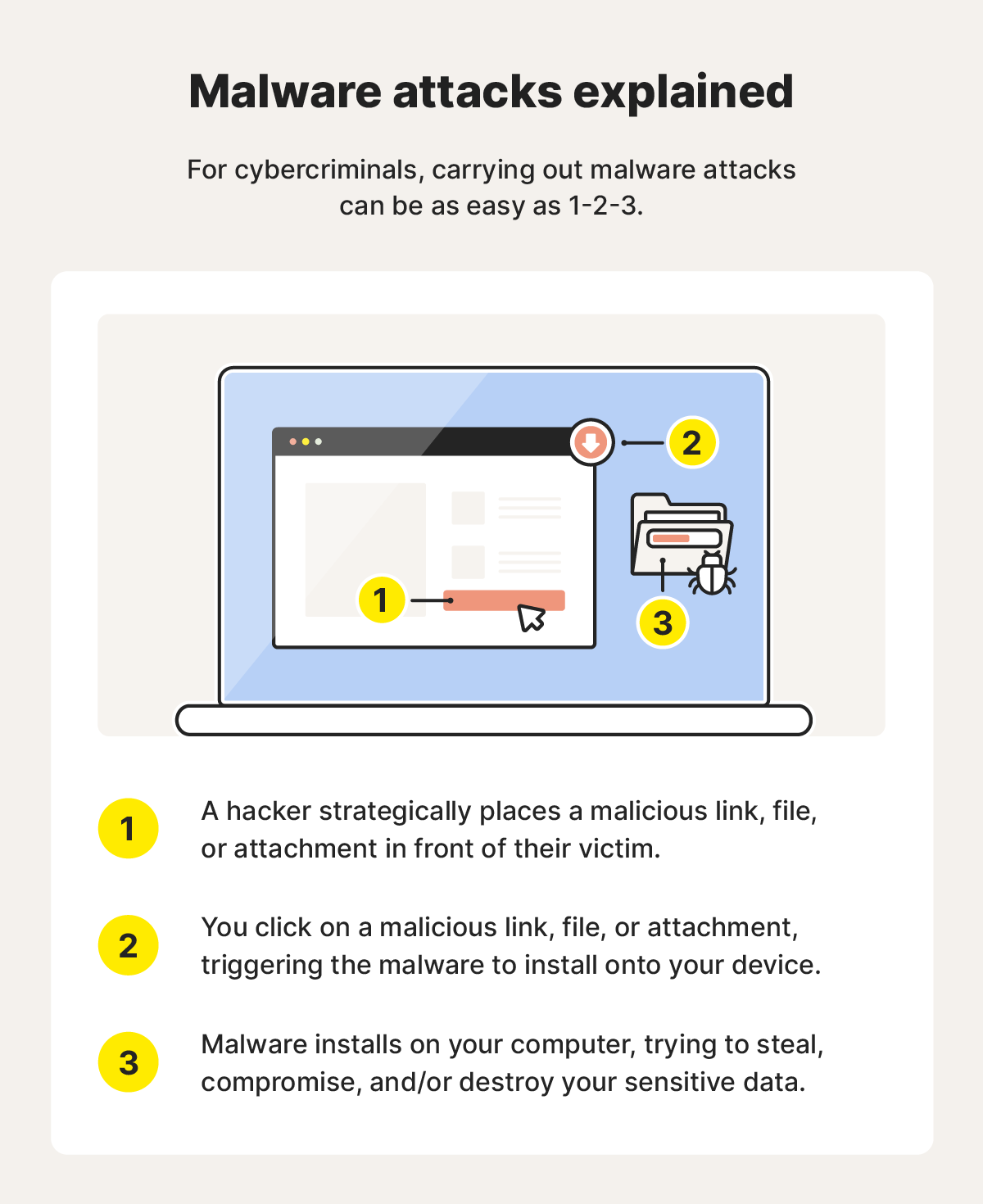

- How it happens: Malware can spread through malicious links, infected files, or deceptive advertisements.
- How to protect yourself: Don’t click suspicious links or download attachments from unverified sources on social media.
10. Catfishing
Catfishing is when someone creates a fictitious online persona to trick others into starting a fake relationship, often romantic. A catfisher or romance scammer usually does this to steal money or personal information, but their motives could also include revenge.
They may ask you to transfer money, share usernames and passwords, or make other suspicious requests. If you plan to meet in person or set up a video call, they usually flake at the last minute, offering some kind of excuse.
- How it happens: A scammer creates a fake online profile and contacts a target, building trust quickly. After they’ve established a relationship, the scammer asks for money to pay for something like airfare or a family emergency. Once they have the money, they either disappear or continue the ruse and ask for more money.
- How to protect yourself: Be wary of unsolicited friend requests and direct messages, especially if they look suspicious or are too forward. Never give money to a stranger, especially if you haven’t met them in person, and never share personal information.
11. Misinformation
Misinformation, like election disinformation, can spread like wildfire on social media, because algorithms often feed you information based on your interests rather than facts. This can ultimately lead you to lose trust in certain institutions, form beliefs that you otherwise wouldn’t, or make decisions that aren’t in your best interest.
- How it happens: Misinformation spreads through false or misleading content, manipulated images and videos, and propaganda accounts.
- How to protect yourself: Verify information from multiple reputable sources and don’t buy into sensationalized headlines or claims.
12. Clickjacking
Clickjacking is a malicious technique that tricks users into unintentionally clicking hidden links or buttons, often leading to unauthorized actions like installing malware or sharing sensitive information.
On social media, clickjacking can occur through deceptive posts or ads that contain invisible elements. When a user clicks the visible content, they unknowingly trigger hidden actions, such as liking a page, sharing a post, or downloading malware.
- How it happens: Clickjacking happens when cybercriminals use deceptive tactics to trick users into clicking malicious links or performing actions without their knowledge.
- How to protect yourself: Don’t interact with suspicious posts and avoid sensationalist headlines or too-good-to-be-true offers or giveaways.
13. Fake followers
Fake social media followers may not seem too threatening, but they pose risks nonetheless. Individuals should be wary of accounts with fake followers, as they are more likely to be dishonest or malicious. Conversely, businesses and influencers who buy or accept fake followers could face low engagement rates, damage to credibility, and violation of platform policies.
- How it happens: Social media account holders buy fake followers from third-party services. Individuals come across their page and think it’s a well-established account, so they follow it too. If the page is malicious, the owner might post fake giveaways or send phishing messages.
- How to protect yourself: As an individual, be skeptical of accounts with unusual follower-to-like ratios, minimal posts, and generic profile pictures. If a new account you follow requests personal information or promotes too-good-to-be-true offers, don’t give them any information or money. Don’t be tempted to buy followers yourself, it’s not worth it in the long run.
14. Social media school threats
Social media school threats occur when someone uses social media platforms to issue threats against schools or other students, resulting in closures and lockdowns. Although frequently hoaxes, they can lead to considerable disruption and distress.
- How it happens: Someone posts a threat against a school, students, or staff on social media, sometimes using a fake account to remain anonymous. The digital nature of the threat means it could be rapidly disseminated among students and communities. If authorities take the threat seriously, a SWAT team could be sent or the school closed.
- How to protect yourself: If you come across a school threat on social media, report it to the school’s administration and law enforcement.
15. Affiliate fraud
Affiliate fraudsters use deception to generate money through social media and affiliate marketing programs. They con companies by artificially inflating clicks, impressions, or sales. Ultimately, this results in much higher payouts for the scammers and lower returns on investment for the businesses involved.
- How it happens: A fraudster manipulates social media metrics to inflate payments, using tactics like click fraud that often involves automated scripts, botnets, or fake accounts, simulating clicks or engagement that never involved real human interest. They get money for their marketing “efforts” that they haven’t earned.
- How to protect yourself: Companies can defend themselves from affiliate fraud by implementing robust tracking and verification systems, carefully selecting and monitoring affiliates, and using fraud detection tools.
7 ways to help prevent social media threats
You can help defend against social media threats by protecting your personal information, enhancing account security, using secure connections, and installing antivirus software.
What the experts say
"The digital underground is a constantly shifting landscape, marked by rapid adaptation and ruthless innovation. Vigilance and adaptability remain our strongest assets." - Gen 2025 Threat Report
Jan Rubín, Threat Research Team Lead
Here are more details on how to protect yourself from social media scams:
- Never share personally identifiable information (PII) like your Social Security number, credit card numbers, or address on social media posts. Ignore and report requests for such information.
- Change passwords regularly and make them strong and unique to help protect against brute force and credential stuffing attacks. You can use a password manager to make it easier to remember your passwords without compromising security.
- Set accounts to private to control who can see the content you post. You can also consider further privacy settings like blocking others from posting on your wall or page.
- Use a VPN (virtual private network) to encrypt your internet traffic and mask your IP address, making it harder for hackers to find your location and spy on your online activity.
- Don’t accept friend requests from strangers, as they may be from malicious accounts designed to phish for personal information or spread malware.
- Avoid public Wi-Fi to reduce the risk of your internet traffic being intercepted through packet sniffing. If you have to check your social media on public Wi-Fi, make sure you’re using a VPN first.
- Use antivirus software for real-time protection against malware that can compromise your social media account and credentials. A robust cybersecurity solution can also keep you safer from phishing attacks and other online threats.
Help protect yourself from social media threats
You never know when you’re one click away from danger on social media. An adorable cat picture or a mouthwatering cake could be all it takes.
Protect against malware, phishing links, and other online threats with Norton 360 Standard. Our advanced AI-detection technology helps you identify and avoid online scams while scrolling through your feed. Enjoy greater peace of mind and a safer social media experience.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.