What is a brute force attack?
Even if you can’t see them, hackers are trying to muscle their way into anywhere private information is stored. Using brute force attacks, hackers can force their way into individual accounts and networks. Get Norton 360 Deluxe to help protect against malware, phishing, and other tactics hackers use to disrupt your life and online security.

The phrase “brute force attack” conjures images of invading armies smashing through fortifications using mounted rams made of gigantic tree trunks. And while the reality isn’t that dramatic, the results can be. With a bit of time and effort, a hacker can get into your bank and credit card accounts, or even infiltrate commercial networks to steal personal information, trade secrets, and more.
Keep reading to learn about this method of gatecrashing your online life, how these attacks happen, and how to avoid them.
What is a brute force attack?
A brute force attack is when a hacker tries to crack encryption keys, passwords, or login information through trial-and-error approaches. By using computing power, a hacker will test a large number of potential keys and logins to gain entry to accounts and networks.
Instead of picturing a large, pillaging force of barbarians splintering the ramparts of a keep, picture a single figure dressed in a dark cloak and armed with a ring of thousands of keys near the locked gates of a city. While it will take them some time to try every key, eventually they’ll find the right one and make it through.
Motivations for ‘bruteforcing’
Many brute force cyberattacks are motivated by money and a craving for power. But there are many other motivations, making it tough to predict where a brute force attack will occur. Unfortunately for us, that means no one is safe from being targeted. Here are some of the primary drivers for brute force hacking attacks:
- Financial gain: Whether stealing directly from people’s accounts, using stolen credit card numbers, siphoning traffic to generate money from ad sales, or selling the information they steal, making money is a big motivator.
- Data theft: Stealing information has financial benefits and gives hackers power over the people and organizations they hack.
- Unauthorized access: The thrill of breaking the law and flexing metaphorical muscles can be the overall goal of bruteforcing.
- Spreading malware: Hackers may gain access to place malware that damages systems, spyware to record user activity, and ransomware to encrypt and hold information hostage.
- Espionage: State- and corporate-sponsored hackers get paid to attack rivals for financial gain or to exert power.
- Identity theft: Hackers can simultaneously damage someone else’s finances and reputation while earning money selling or using other people’s identities.
Types of brute force attacks
There are a few different kinds of brute force attacks, but they all function by effectively guessing combinations of logins and passwords. How they perform these attacks and what data sets they use to guide them are what differentiates the different methods. Let’s look at these types of attacks and how they work.
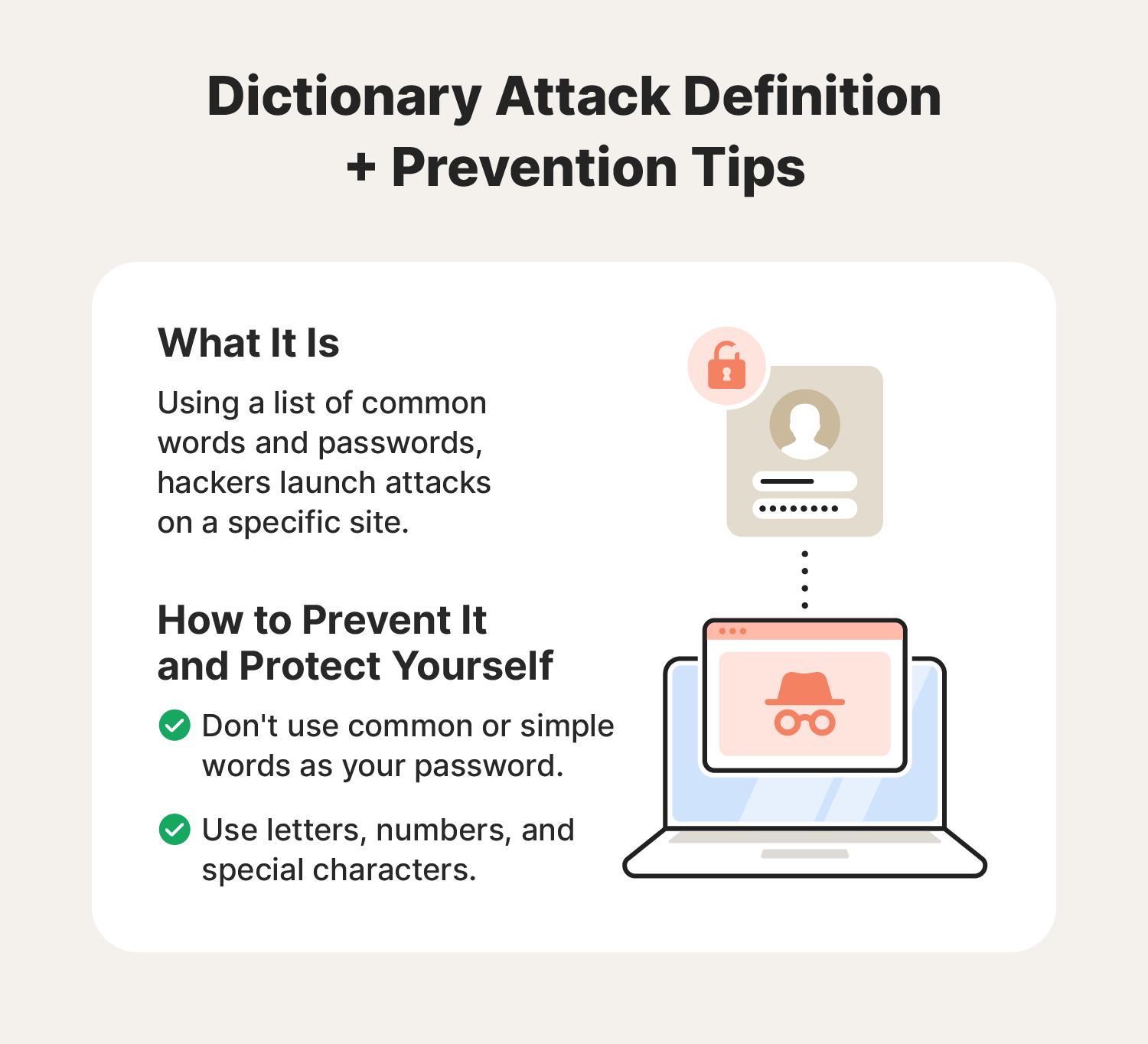
Dictionary attacks
In a dictionary attack, a hacker systematically tries a list of common words and phrases as passwords to break into a system. These password attacks require a predefined list of words or passwords, often pulled from dictionaries, movies, books, and online databases.
The hacker uses scripts to complete these attacks automatically. While cybercriminals can use a dictionary attack against any target, the amount of time it can take to mount one means that individuals and smaller organizations are easier targets.
Credential stuffing
In a credential stuffing attack, a hacker compiles a list of logins and passwords from existing databases found or purchased online (usually obtained via a data breach). Using that list, they deploy a botnet to use those credentials across many sites at once. Whenever the logins work somewhere, the hacker harvests the information to use or sell it.
Anyone can be the target of a credential stuffing attack, but those whose information was stolen in a data breach are more likely to fall victim to one of these attacks.
Norton 360 Deluxe patrols the dark web, and alerts you if it detects your personal information. That helps you prepare for and prevent attacks by changing your passwords and taking other digital security steps.

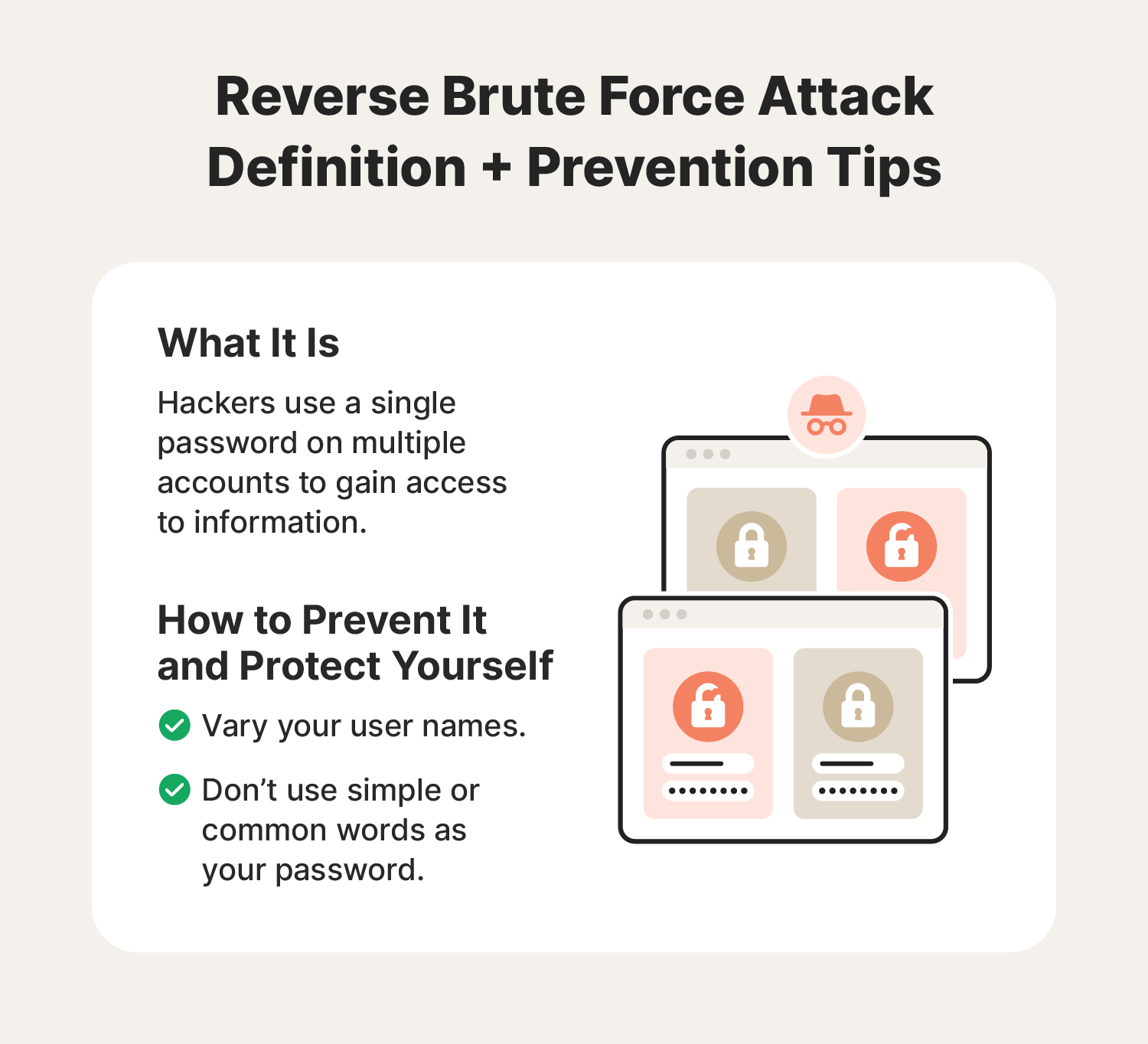
Reverse brute force attacks
With a reverse brute force attack, a hacker will use a single password for multiple user names instead of trying multiple passwords against a single user name. To increase the likelihood of success, hackers will start with a list of known or potential usernames, try a single password for those names, and then move to another password.
Individuals, businesses, and organizations of almost any size can be the target of a reverse brute force attack. However, sites with a larger user base could provide the hacker with better odds of cracking a system.
Hybrid brute force attacks
During a hybrid brute force attack, a hacker will use multiple methods to crack passwords and gain entry into a system. In addition to using a combination of brute force attacks (like a dictionary and credential stuffing attack), hackers may simultaneously launch other attacks, like a DDoS attack, to take parts of a system offline or provide cover for the brute force attack.
Attacks of this kind are less common than other types of bruteforcing, because they require significantly more time and resources. That means that large organizations and governments may be more likely to be attacked this way.

Rainbow table attack
Cybercriminals use a precomputed collection of hash values known as a "rainbow table" to reverse engineer the encryption of passwords (“hashes”) in a system. Hackers usually start a pass the hash attack by gaining entry to a system to scrape for hashes. Once they have enough hashes, they combine common passwords with hash values to force their way deeper into a network disguised as a legitimate user.
Businesses that use single sign-on systems are at a higher risk of this kind of attack. Hackers may gain initial access by phishing or malware installed on the authorized user’s devices.

What tools are commonly used in these attacks?
The internet is full of tools designed to help hackers break into things. Many are open-source, meaning anyone can change or add to the code to improve their success rates or get around stronger security. The following list of tools are just a few of the many ways a cybercriminal can try to force their way into a system:
- THC-Hydra: Attacks macOS, Windows, and Linux login pages using dictionary attacks.
- Hashcat: The Hashcat password cracker works on breaking the encrypted passwords (hashes) in a system.
- John the Ripper: This open-source tool works with many cipher and hash types, including MacOS, Windows, web applications, network traffic, and others.
- Aircrack-ng: These tools use Wi-Fi networks to examine data and create attacks through various methods.
Surprisingly, cybersecurity professionals often use those same tools to help prevent attacks before they happen. They also take advantage of the open-source nature of these scripts and tools to identify attacks and shut them down.
Examples of brute force attacks
Brute force attacks often target popular platforms where many users store data. Email domains, online tax services, or food delivery apps could likely be targets. Here are just a few real-world brute force attack examples:
- 2009 Yahoo attacks: A two-year-old security flaw allowed attackers a unique opportunity to target Yahoo Mail accounts with password-cracking attacks.
- 2013 WordPress attacks: As many as 60 million attempts were made in just one hour during waves of brute force attacks targeting WordPress platforms. Luckily, hackers breached very few sites.
- 2015 Dunkin’ Donuts attacks: Seeking to exploit reward program perks, hackers gained access to almost 20,000 Dunkin’ mobile app accounts.
- 2015 Alibaba’s Taobao attacks: Hackers used a list of 99 million stolen login credentials with a success rate of 1 in 5, showing how often accounts reuse poor passwords. Hackers breached nearly 21 million accounts.
- 2021 T-Mobile attacks: Cybercriminals combined brute force attacks with other means to hack into T-Mobile IT servers containing customer data.
Tips for defending against brute force attacks
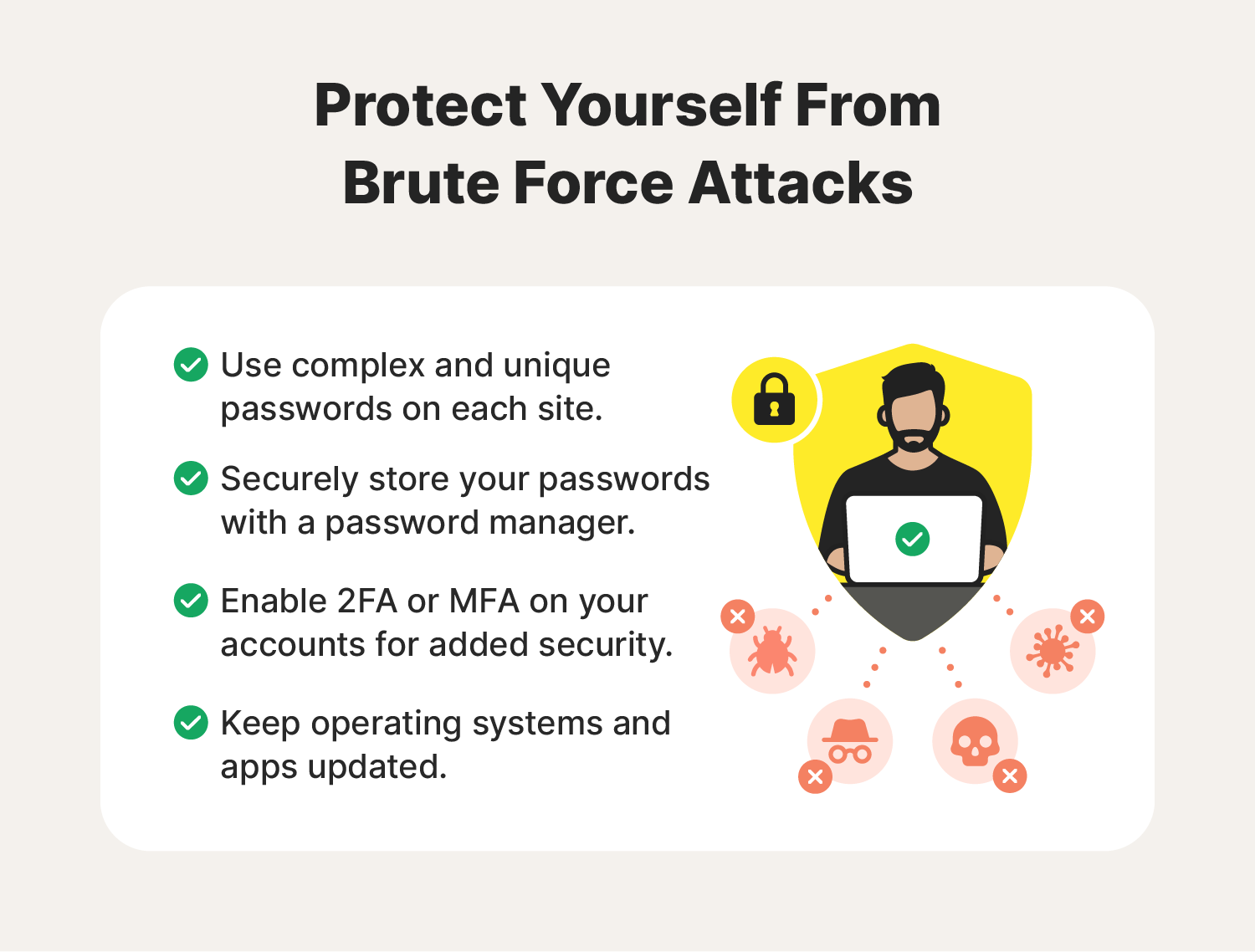
Many basic cybersecurity practices can help reduce the effectiveness of brute force attacks. Brute force attack prevention starts by focusing on good password security. Here are a few password tips and cybersecurity practices that can keep attackers at bay:
- Create strong, unique passwords: Avoid using common words and phrases when you create your passwords, and never use the same password on more than one site for better password security.
- Use a password manager: Password managers help you create strong passwords that combine numbers, special characters, and letters in random combinations and store them securely.
- Use 2FA/MFA: 2FA (two-factor authentication) or MFA (multi-factor authentication) adds layers to confirm your identity.
- Update apps and operating systems: Software updates remove weak points and can even add extra levels of security.
Fortify your data
Because hackers tend to use brute force attacks against targets with lax security, taking the time to learn how to secure your account can make these kinds of attacks impractical and uneconomical for hackers. You don’t have to be the only thing standing between your data and brute force password attacks.
Comprehensive security software like Norton 360 Deluxe helps protect you from hackers, malware, and data theft thanks to a suite of tools including a Password Manager for a more convenient and secure way to store your passwords. It even comes with a built-in VPN to encrypt your browsing and help keep you private online.
FAQs about brute force attacks
Have more questions about these cyberattacks? We have answers.
How common are brute force attacks?
Brute force attacks are fairly common. Some research suggests that as much as 50% of all breaches are caused by hackers stealing credentials.
Is it illegal to crack passwords?
It is generally illegal to crack passwords that aren’t your own. Because cracking a password is usually done to gain unauthorized access and steal or extract data, it is a form of hacking.
How long can a brute force attack last?
Depending on the information a hacker has to start with, it can take days, weeks, or months for a brute force attack to run its course. Even if a hacker spends months trying to crack passwords, there is no guarantee that they’ll be successful. For example, the AES 256 encryption used by Norton VPN is so complex that it would take a supercomputer millions of years to crack.
What are the hardest passwords to crack?
Long passwords (15+ characters) with random combinations of lowercase and uppercase letters, numbers, and special characters are the toughest passwords for hackers to crack. Avoiding sequential combinations of characters (123456 or qwerty, for example) helps reinforce password security, too.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.