What is a pass the hash attack? + How to mitigate an attack
What is a pass the hash attack?
A pass the hash attack is when a hacker steals stored user credentials and uses them to impersonate legitimate users and gain unauthorized access to a network.

Let’s face it: The thought of someone gaining unauthorized access to your information can be frightening.
From family photos to private financial information, many aspects of our lives lie behind the security of a password.
An often overlooked example of password security occurs in the workplace. Whether it’s remote computer access or a shared drive with company documents, some business networks rely on user logins and passwords to ensure that only authorized users can access company files.
While this type of security can make life easier for employees, hackers have found a way to exploit it by carrying out pass the hash attacks.
Follow this guide to learn more about how pass the hash attacks work, real-life examples, and how you can help mitigate an attack.
How pass the hash attacks work
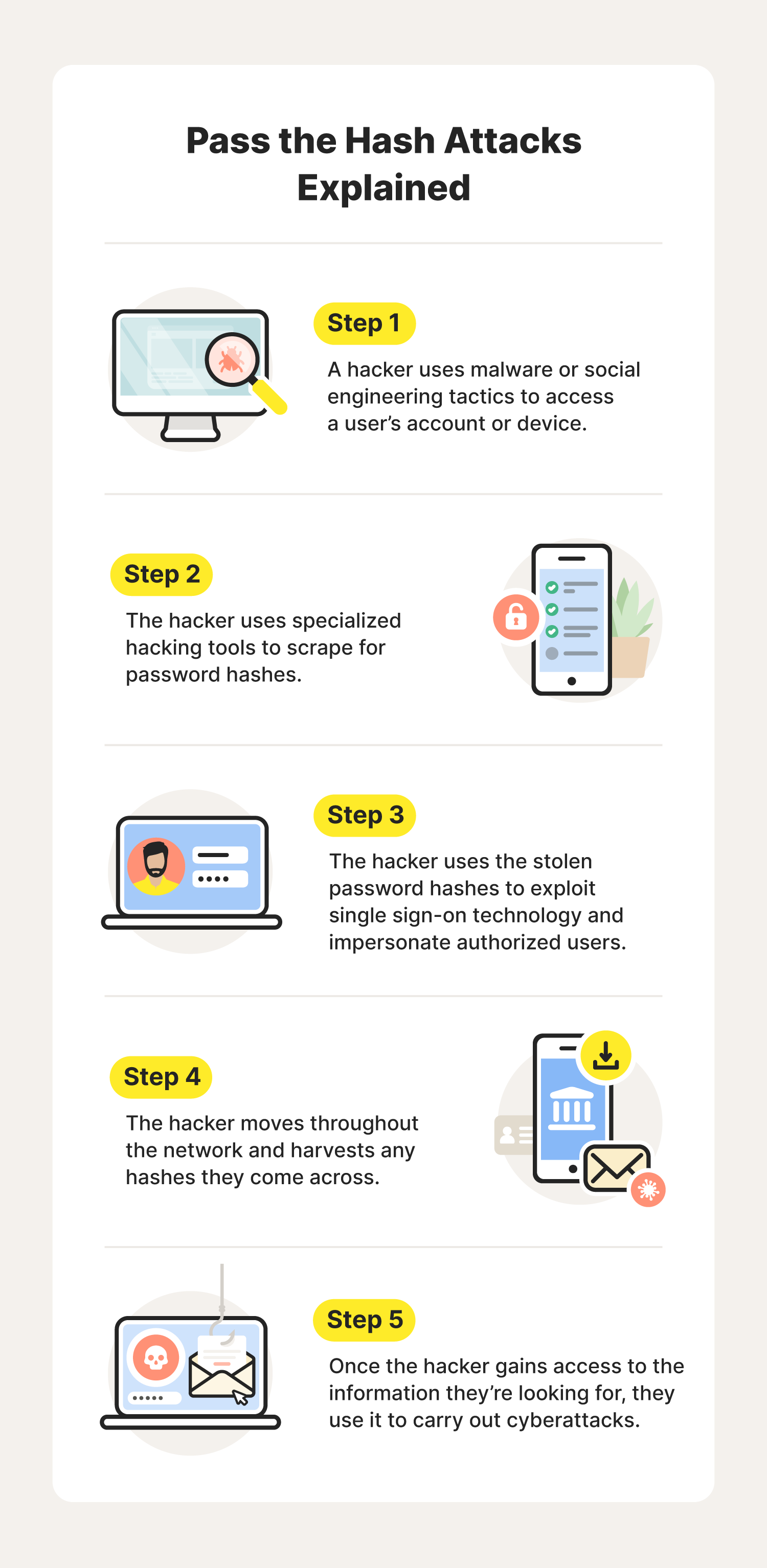
Pass the hash attacks involve the theft and use of password hashes. A password hash is the result of password hashing, which is a one-way process of converting a password into ciphertext, or an encrypted version of the password. Because this is a one-way process, you cannot easily decrypt the hash to reveal the original password.
Password hashes help to validate and encrypt passwords. This provides great security benefits, as it prevents the storage of passwords in plain text, which could more easily be picked apart by hackers in the event of a data breach.
Let’s say you set your password as “Gr@y#F0x!”. Behind the scenes, your password will be hashed as something entirely different. For example’s sake, let’s pretend your hashed password is “83645902.” As far as the hash authentication mechanism is concerned, your password is “83645902.”
These password hashes are used for single sign-on (SSO) systems. In these systems, a user can log into a system once, and password hashes will work in the background to continuously authenticate users as they access different applications and servers, without having to sign in another time. An example of this may be a network of shared storage drives or applications used by a business and its employees.
To steal these hashes, hackers will begin by gaining access to a single user’s account or device, often by using malware or social engineering tactics such as phishing. Once they have gained access, the hacker will use hash hacking tools to scrape for stored password hashes.
If a hacker successfully finds password hashes, they can pass the hash from one login to another, impersonating legitimate users and creating authenticated sessions in their name. In these attacks, hackers will attempt to move laterally, going from application to application and harvesting as many hashes as possible.
As they continue stealing hashes throughout the network, they hope to find the password hashes of users who have the most privileges within the business’s network. For example, an IT administrator likely has greater access to the business’s network than an intern does.
By stealing the password hash of someone with administrative access, the hacker will then have greater access to the network and all of its data, from customers’ personal information to confidential files.
Once a hash hacker gains access to what they’re looking for, they may then carry out malicious cyberattacks for their own benefit, including data breaches, different types of ransomware attacks, or identity theft.
Pass the hash attacks: Real-life examples
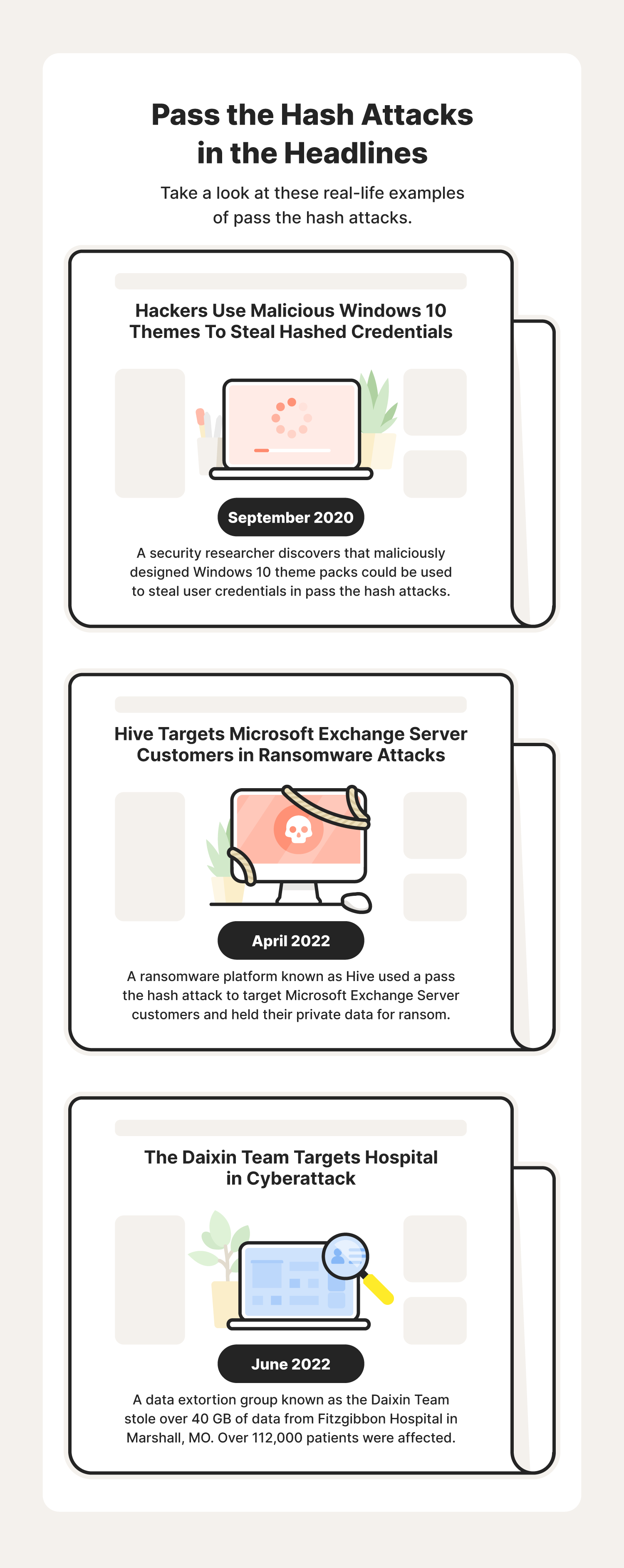
Unfortunately, these types of attacks can have serious consequences and may even affect the customers of a business. To better understand the impact of these attacks, check out these recent real-life pass the hash attack examples:
- Windows Themes: In September 2020, a security researcher discovered that hackers could share malicious Windows 10 theme packs to assist in pass the hash attacks. Theme packs are customizable themes you can share with others containing specific sounds, colors, and wallpapers. In this type of pass the hash attack, an unsuspecting user clicks on the theme pack and is instead directed to a resource that requires the use of their password hash to access. During this process, the attacker will try to intercept the user’s hashed credentials.
- Hive: In April 2022, a ransomware platform known as Hive used a pass the hash attack to target Microsoft Exchange Server customers. Similar to the infamous Cryptolocker attack in 2013, this attack involved the encryption of stolen data held for ransom.
- The Daixin Team: In June 2022, a data extortion group known as the Daixin Team stole over 40 GB of data from Fitzgibbon Hospital in Marshall, MO. This data included sensitive patient information, including patient names, dates of birth, Social Security numbers, and medical records. Following the attack, the hospital confirmed that over 112,000 patients were affected.
As you can see, these attacks can lead to devastating consequences for companies and their customers alike. Fortunately, businesses and employees can follow some mitigation tips to help reduce the risk of an attack.
How to prevent pass the hash attacks: 7 mitigation tips
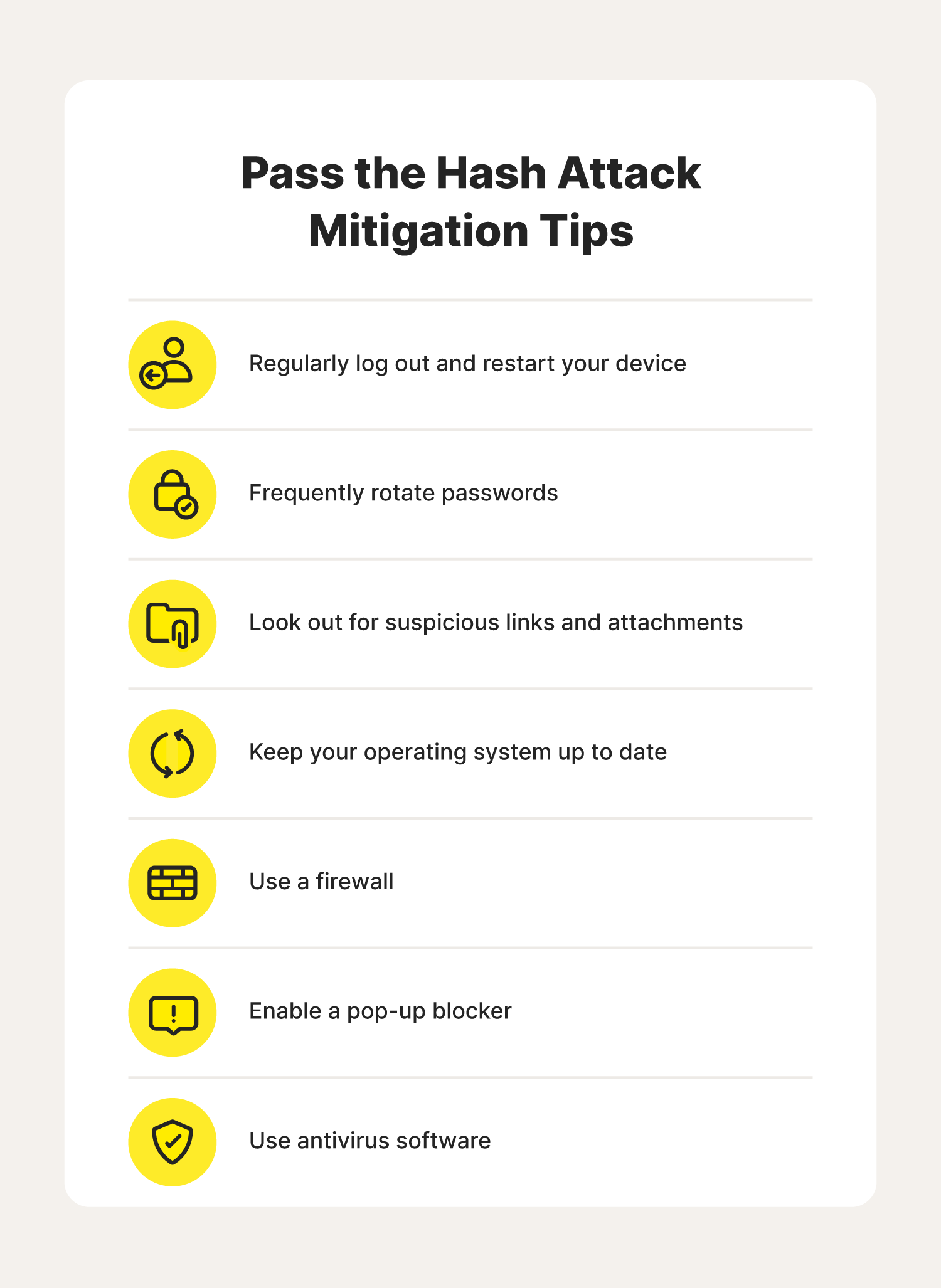
While a pass the hash attack can affect the security of an entire organization, they often start with the exploitation of a single user’s device or account. In addition to implementing organizational cybersecurity measures, following these pass the hash mitigation tips can help reduce the risk of being compromised by an attack.
1. Regularly log out and restart your device
Whenever you’re finished using your device, log out of your current session. This can prevent someone else from accessing your device while you’re away. You should also regularly restart your device to help clear stored hashes from your device’s active memory, which may be scraped by hackers during an attack.
2. Frequently rotate passwords
Frequently rotating passwords can help prevent the risk of a pass the hash attack, as it shortens the window in which a stolen hash is valid. For example, if you change your password, it will require a new password hash to match, therefore invalidating the old password hash.
3. Look out for suspicious links and attachments
Because pass the hash attacks often begin with different types of phishing, you should always be cautious of any links or attachments you receive, as clicking on them could accidentally infect your device with malware or direct you to an unsafe website.
4. Keep your operating system up to date
In addition to new features and performance enhancements, software updates often include security patches that fix security vulnerabilities and help minimize the risk of being affected by malicious cyberattacks, including pass the hash attacks.
5. Use a firewall
A firewall is a security feature that can help protect your device and network by filtering out unauthorized traffic. Fortunately, all major operating systems include built-in firewall features that can help protect your system from security threats such as malware. To ensure your device is as safe as possible, enable your device's firewall.
6. Enable a pop-up blocker
In addition to being extremely annoying, pop-up windows may lead you to different types of malware or unsafe sites that can assist in a pass the hash attack. By enabling your web browser’s pop-up blocking features, you can limit the risk of accidentally clicking a dangerous link within a pop-up window.
7. Use antivirus software
Using a trusted antivirus software can help protect your device from viruses, ransomware, malware, spyware, and other online threats that may be used to gain initial access in a pass the hash attack.
While some pass the hash mitigation strategies may need to be implemented at an organizational level, following these mitigation tips can help you minimize the risk of being exploited by a pass the hash attack. To help increase your Cyber Safety across the web, be sure to educate yourself on other password attacks.
FAQs about pass the hash attacks
Continue reading to learn the answers to some common questions surrounding pass the hash attacks.
What is a password hash?
A password hash is the result of password hashing, which is a one-way process of converting plain text information into ciphertext. Once a password has been hashed, it is converted into nondescript hash symbols. That way, if the password is leaked in a data breach, it will be much more difficult to recognize than a password stored in plain text.
Are pass the hash attacks becoming more common?
As the use of SSO technology increases, so does the possibility of pass the hash attacks. Because of this, it’s important to employ good cyber hygiene habits and cybersecurity measures to help mitigate these attacks.
Who is vulnerable to pass the hash attacks?
Organizations that use Windows New Technology LAN Manager (NTLM) are likely the most vulnerable to pass the hash attacks. This is because NTLM does not use some of the more advanced algorithms and encryption techniques that can help prevent these attacks.
What is NTLM hash?
NTLM is a Windows technology that helps authenticate users' identities within SSO technology. An NTLM hash is the hashed password NTLM uses to verify that the user has permission to access whatever it is they are trying to access.
Do pass the hash attacks work on Mac computers?
While Mac computers can be affected by pass the hash attacks, Windows devices are targeted more often, as hackers look specifically to exploit Windows password hash.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.