What is CryptoLocker? An overview + prevention tips
CryptoLocker is ransomware that encrypts your files and requests payment to decrypt them. To learn more about CryptoLocker and how it works, follow this guide.

CryptoLocker is ransomware that encrypts files on Windows computers and then requests payment to decrypt them.
To put it into simpler terms, picture this:
You have hundreds of family photos and important financial documents stored on your computer.
You pull up a seat to access one of them only to find that after turning on your computer, all of your files are locked away and out of your reach. Worse yet, a message pops up that you have to pay a hefty fee to get them unlocked — and you do to regain access to your most meaningful files.
This is what happens in a successful CryptoLocker attack. But you don't always need to be on that receiving end if you know how to avoid CryptoLocker attacks in the first place.
It’s worth noting that this cyberattack first gained notoriety in 2013 and was dismantled in May 2014 by a collection of law enforcement agencies. While the original strain of CryptoLocker is no longer operational, different versions of CryptoLocker and similar types of ransomware still circulate the internet today.
To learn more about CryptoLocker and how it works, as well as detection, removal, and prevention tips, follow this complete guide.
How does CryptoLocker ransomware work?
CryptoLocker ransomware is typically delivered through malicious email attachments and links. In some cases, these phishing emails will come from an unknown sender or by imitating a FedEx or UPS tracking notice. If you click on one of these attachments or links, the CryptoLocker malware will begin installing onto your device.
Once CryptoLocker has been installed, it will begin encrypting your files using an asymmetric encryption method. This type of encryption is a two-key system, meaning there is one public key for encryption and a second private key for decryption. In this case, the cybercriminals behind CryptoLocker will have both keys, leaving you unable to access your files.
During CryptoLoc ker’s installation process, it will not only scan your computer, but any other devices it can access on your network in search of files to encrypt. This process can take hours, so your device might not show symptoms right away.
After CryptoLocker is done encrypting your files, it will display a ransom message on your screen, claiming you have to pay a fee to restore your files. So what exactly does a CryptoLocker attack look like? We’ve gathered some common warning signs to help you spot one.
How to spot a CryptoLocker attack: 3 warning signs
Now that you know what a CryptoLocker attack is, let’s take a look at how you can easily spot one.
Here are a few common warning signs of CryptoLocker ransomware.
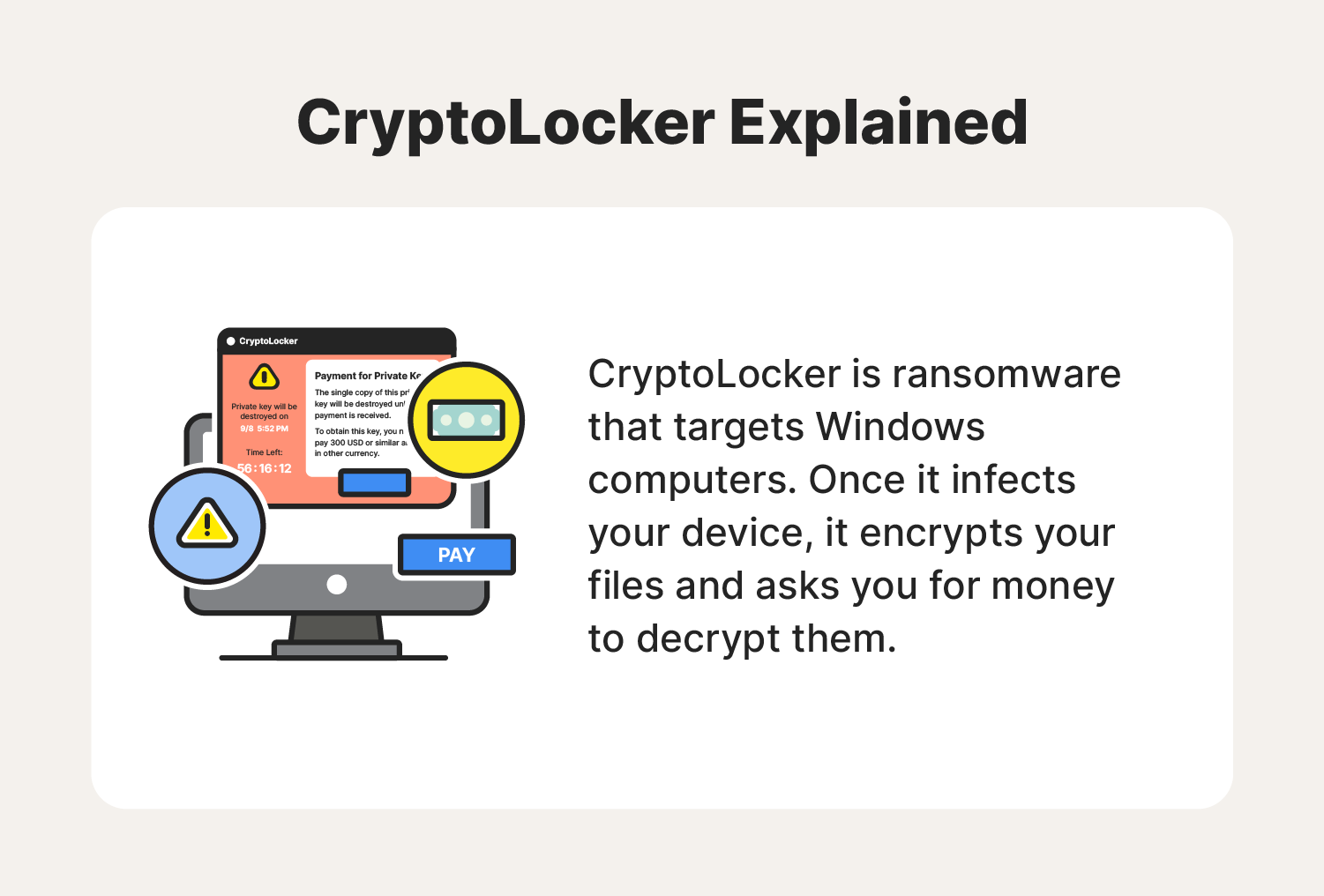
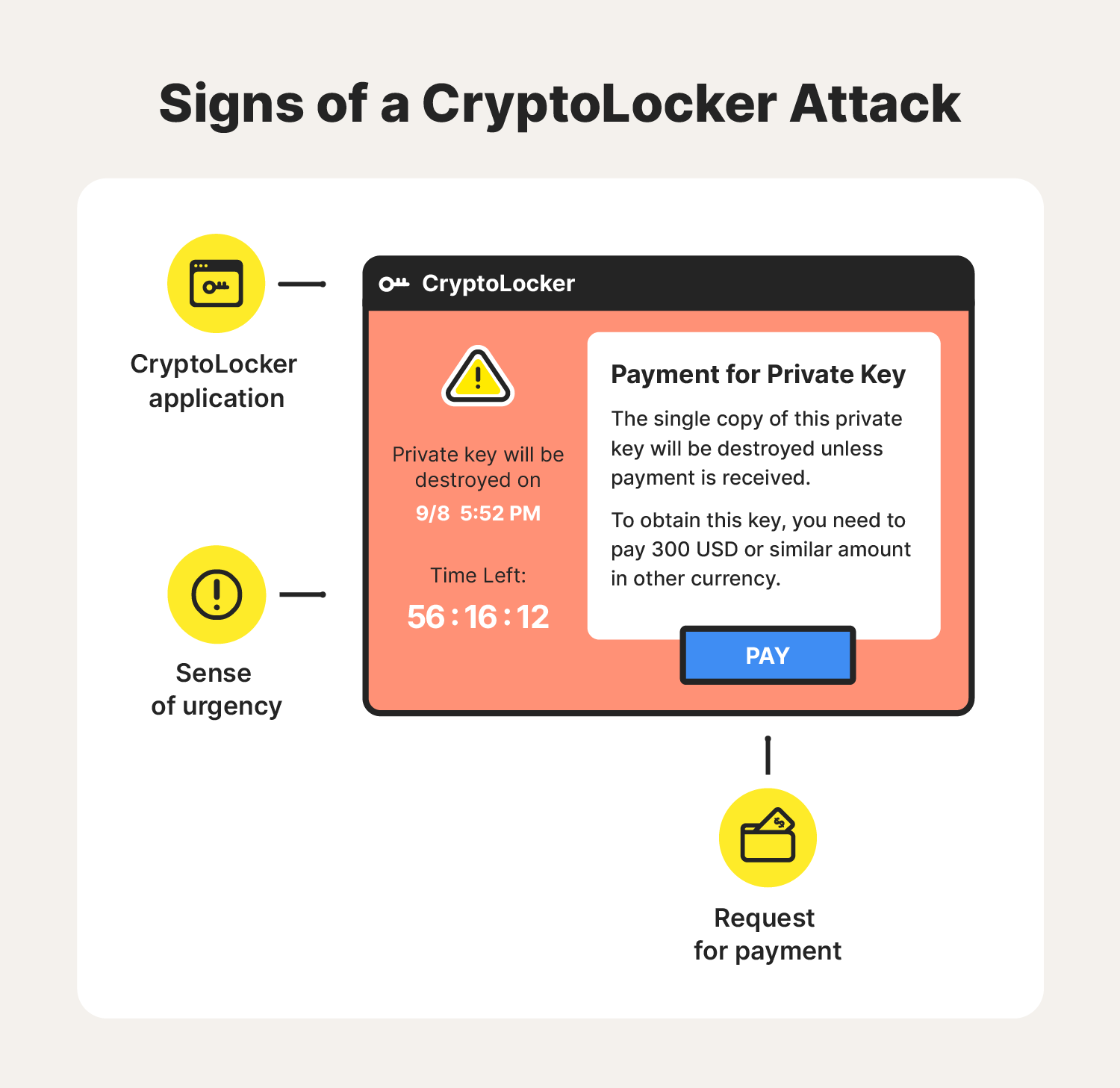
- CryptoLocker application: Perhaps the biggest indicator of a CryptoLocker attack is having the CryptoLocker application on your device. If you see an application or open window with CryptoLocker in the title, then the ransomware has already been installed.
- Request for payment: Like other types of ransomware, CryptoLocker’s main goal is to get you to pay them, oftentimes with cryptocurrency. If you suspect you’ve encountered a CryptoLocker attack, keep aneye out for a ransom note.
- Sense of urgency: CryptoLocker ransom notes use social engineering tactics to get you to act quickly. In many cases, the ransom note will contain a countdown timer, leading you to believe that you will permanently lose access to your files unless you pay them before time runs out.
With an understanding of what CryptoLocker ransomware looks like, you can quickly identify an attack. But what should you do once you find one? Continue reading to find out.
What to do if you encounter a CryptoLocker attack

After coming across a CryptoLocker attack, your first instinct may be to pay the ransom to avoid losing your files. While this may seem like a quick solution, the cybercriminals may just take your money and run, leaving you stuck right where you started.
Instead, it’s best to close the CryptoLocker program and use antivirus software to get rid of the ransomware. Running an antivirus program can help effectively remove CryptoLocker, stopping it from encrypting additional files. But, it’s important to note that this step will not decrypt your files.
When CryptoLocker was first shut down, there were online decryptor tools you could use to attempt to decrypt your files. Unfortunately, CryptoLocker has many clones and variations, making it difficult for an online decryptor tool to work for every situation.
As an alternative, the best way to decrypt your files is to restore them from a data backup. By regularly backing up your meaningful files, you can be sure you’re prepared in the event of such attacks.
If you don’t have a backup, don’t delete your files, as it is possible that an online decryptor tool can help. If you decide to use one, be sure to choose one offered by a trusted source or cybersecurity professional.
6 tips for how to help prevent a CryptoLocker attack
As with other types of cyberattacks, prevention can be the best form of protection. To help protect yourself from CryptoLocker and other forms of ransomware, follow these cybersecurity protection tips.
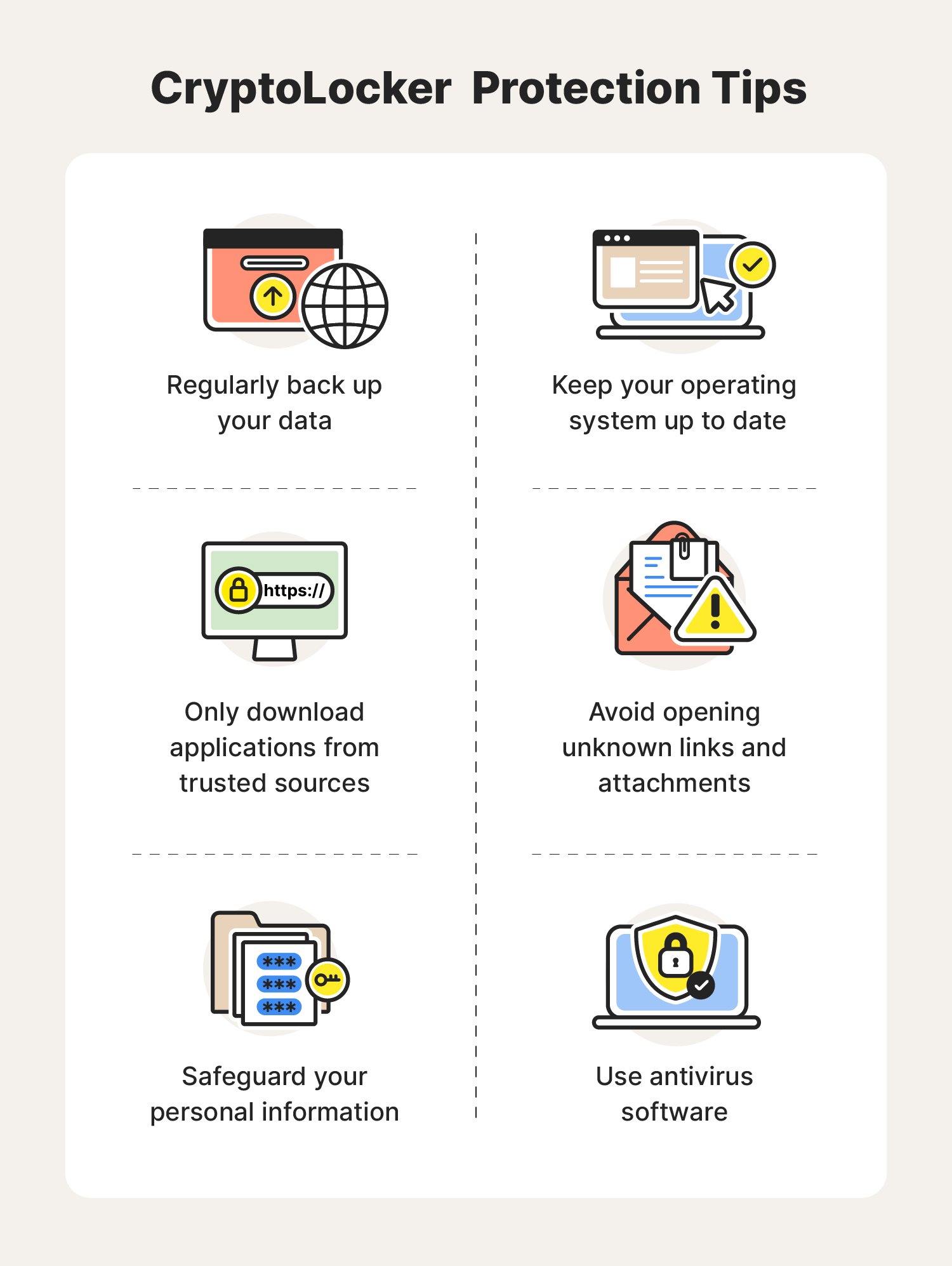
- Regularly back up your data: Because CryptoLocker and other variations of ransomware often target your files, keeping a backup of your data has never been more important. That way, you always know you have a second copy of your files if anything goes wrong.
- Avoid opening unknown links and attachments: By making a habit of avoiding any unknown links and attachments, you can reduce the risk of accidentally exposing yourself to a CryptoLocker attack.
- Only download applications from trusted sources: Because CryptoLocker looks and acts like a normal computer program, it is possible someone could trick you into downloading it from a malicious site. To protect yourself from accidentally downloading CryptoLocker or other malware, only download applications from trusted sites.
- Keep your operating system up to date: Many types of cyberattacks thrive on vulnerabilities within your computer’s operating system. Luckily, operating systems consistently receive security patches and software updates. By staying on top of these updates, you can be sure your device has the strongest security available, reducing your risk of a CryptoLocker attack.
- Safeguard your personal information: It's important to always protect your personal information online. If it ends up in the wrong hands, cybercriminals may take advantage of it and target you with CryptoLocker and other types of ransomware attacks.
- Use antivirus software: Using antivirus software can help detect and remove CryptoLocker as well as many other types of internet threats. This can allow you to surf the web knowing you have the best line of defense between your device and any cybercriminals lurking around on the internet.
Now that you know more about CryptoLocker and what to do if you experience a ransomware attack, you can browse the web confidently and safely. To help stay even more Cyber Safe, learn about the different types of ransomware existing on the internet today.
FAQs about CryptoLocker
Looking for more answers to your CryptoLocker questions? We’ve got you covered.
Is CryptoLocker ransomware still a threat?
As of 2014, the U.S. Department of Justice announced that CryptoLocker is effectively nonfunctional and is unable to encrypt devices. Despite this, other variations of CryptoLocker and similar ransomware attacks still exist on the internet today.
How was CryptoLocker stopped?
After CryptoLocker surfaced in 2013, law enforcement agencies from all over the globe collaborated to put a stop to it. This mission was known as Operation Tovar. In 2014, the Department of Justice announced that they had successfully dismantled CryptoLocker’s infrastructure by targeting Gameover Zeus, a botnet known for distributing CryptoLocker as well as stealing banking credentials.
How much money did CryptoLocker make?
Some sources indicate that CryptoLocker garnered around $3 million from victims of the ransomware attack.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.




Want more?
Follow us for all the latest news, tips, and updates.