Ransomware protection: What it is and how to protect yourself
Imagine waking up to find your files locked away, held hostage by cybercriminals demanding a ransom. To pay or not to pay? Learn about ransomware protection and how to keep your files safe. Then get Norton 360 Deluxe for powerful ransomware protection to help prevent this living nightmare.

In 2023, the FBI’s Internet Crime Complaint Center (IC3) received over 850,000 cybercrime complaints, with ransomware losses among these estimated at nearly $60 million. For many cybercriminals, spreading ransomware isn’t just a crime — it’s a business model.
Ransomware statistics like these remind us why it’s essential to stay safe from malware. This guide will explain how to help protect against ransomware, secure your data, and reduce the risk of becoming the next victim of this growing criminal enterprise.
What is ransomware protection?
Ransomware protection refers to security measures designed to prevent ransomware attacks, which is when hackers deploy file-encrypting malware to lock users out of data and systems and demand payment in exchange for a decryption key. Any actions taken to protect against this type of malware (ransomware) are part of this process.
Ransomware protection methods include regular data backups, anti-malware software, user access management and education, response plans, and data recovery strategies.
How does ransomware protection work?
Ransomware protection includes a proactive action plan that covers what to do before, during, and after an attack. It’s a multi-layered approach that includes installing antivirus software, securing accounts, and having a recovery plan to mitigate risks associated with ransomware attacks.
Here is more detail on how the three-stage ransomware protection process works:
1. Prevention:
- Antivirus software: Install and maintain comprehensive security software that actively monitors for and helps block ransomware attempts.
- Regular backups: Create regular backups to secure cloud storage or external drives to protect your data so you always have access even if your devices are compromised.
- Avoid suspicious links: Be wary of suspicious links that could lead to malware. Exercise caution with links in emails and web pages. Hover over links to verify their legitimacy, especially in unsolicited communications.
2. Management:
- Isolate devices: Disconnect infected devices from networks to prevent the ransomware from spreading.
- Remove the malware: Use trusted security tools to eliminate the ransomware from affected devices or systems.
- Secure accounts: Immediately change passwords for all affected accounts using a secure device.
- Inform relevant parties: Notify those who are impacted or could be potentially impacted, such as family members or coworkers.
3. Recovery:
- Report the incident: File reports with relevant authorities, including local law enforcement, the Federal Trade Commission (FTC), and the Internet Crime Complaint Center (IC3).
- Investigate the cause: Analyze how the attack occurred to strengthen defenses against future incidents.
- Assess the damage: Document all affected systems and data to guide recovery efforts.

Benefits of anti-ransomware software
The main benefit of anti-ransomware software is protection. Since prevention is always better than cure, this is its main goal. Some anti-ransomware software offers other benefits too, like secure cloud storage, multiple device protection, and keeping your internet browsing private.
Norton 360 Deluxe is a great example of a comprehensive anti-ransomware solution. Here are some of the benefits it offers:
- Antivirus software: Includes a malware scanning tool to help detect and remove ransomware and other types of malware.
- Online security: Goes beyond antivirus to offer you other essentials all in one package, including a firewall and a password manager.
- Online privacy: Comes with a VPN to help keep your online connection encrypted and secure. It also includes Privacy Monitor, which scans data broker sites for your personal information, so you can ask to have your data removed and stay more private.
- Covers multiple devices: Protects up to five desktops, laptops, or mobile devices with one subscription.
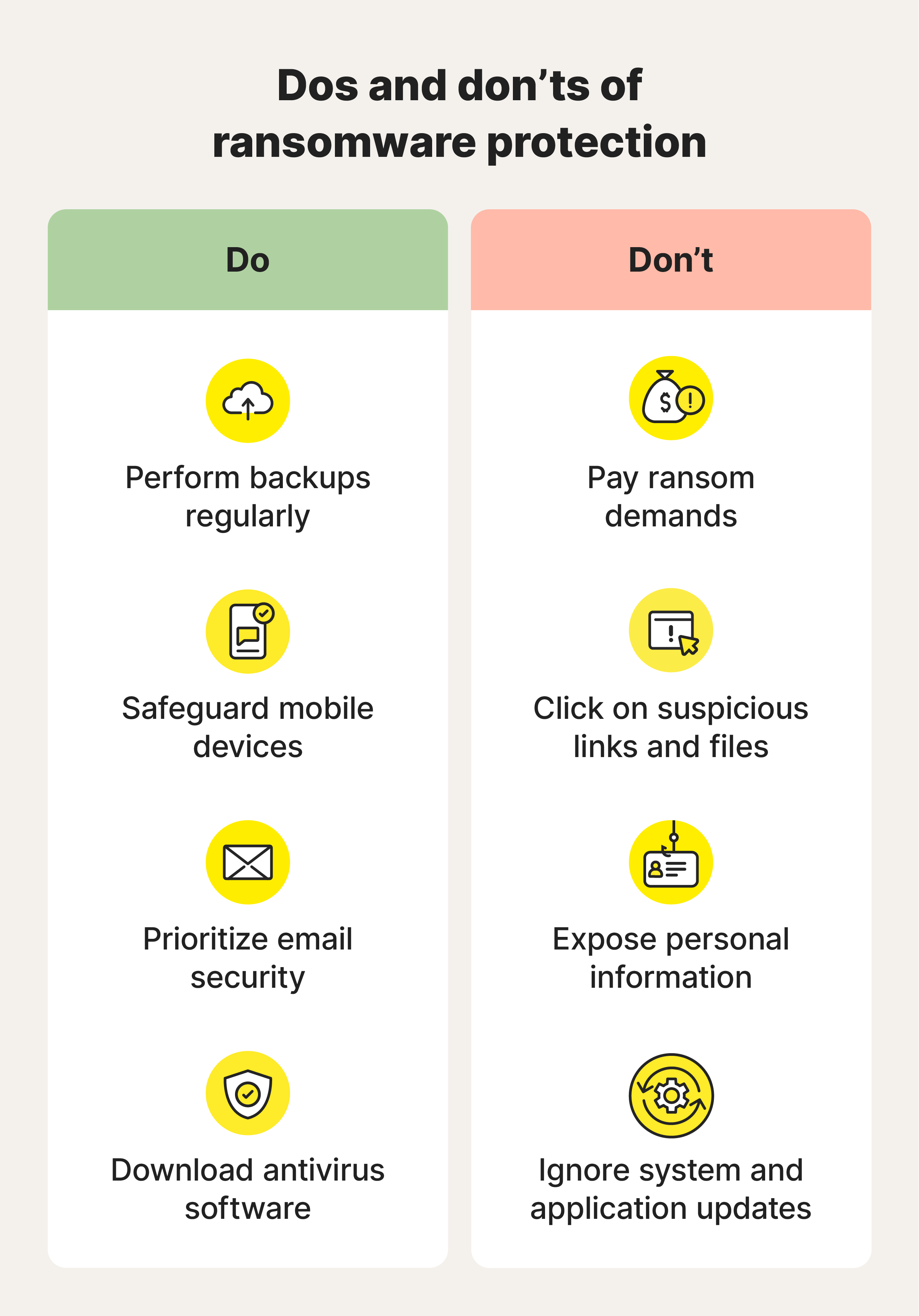
10 tips to protect against ransomware
We have 10 tips you can use to help protect against ransomware. Many of these tips, such as never exposing data, avoiding suspicious websites, and keeping software updated, focus on what to do before you’re affected by ransomware, as prevention is always better than cure. But we have tips to cover all stages, starting with the first rule of never paying the ransom.
1. Do not pay ransom demands
Except in extenuating circumstances, ransomware demands shouldn’t be paid. Paying up encourages cybercriminals to continue their activities. It rewards their organized crime efforts, making them more likely to target others — and you — again in the future.
Reasons why you shouldn’t pay ransomware demands:
- It gets expensive: In one study, 80% of victims who paid the ransom were targeted by another ransomware attack.
- No guarantee of recovery: Cybercriminals have no reason to honor their promises, even if you pay.
- Ethical concerns: Paying ransoms often funds further illegal activities, potentially supporting crimes beyond ransomware attacks.
- Potential violations: Paying attackers from sanctioned countries could have legal ramifications and even violate federal law.
- Compromised data: Criminals may still leak your data on the dark web, even if they give your information back.
2. Never expose personal information
Safeguarding your personal information can help protect you from ransomware attacks. Details like your address, Social Security number, login credentials, and banking information are valuable to cybercriminals. They can use this info in a phishing attack, which could trick you into clicking a link or downloading an attachment with ransomware.
Tips to protect your personal information:
- Check your social media: Make sure your social profiles are private to prevent strangers from easily accessing personal details.
- Secure your accounts: Use strong, unique passwords for each account and enable two-factor authentication (2FA).
- Use a VPN: A virtual private network encrypts your internet connection, keeping your in-transit data safe when browsing on public Wi-Fi.
- Remove metadata from shared files: Files can contain hidden metadata, like location information and time stamps.
3. Avoid questionable websites
Malicious websites are a common entry point for ransomware. Knowing how to identify and avoid risky sites can help protect you from infections.
Tips to avoid ransomware websites:
- Check the URL: Ensure the website matches the correct URL and starts with HTTPS. Be wary of spoofed websites where the URL can look nearly identical to the site it’s impersonating.
- Spot fake download buttons: Exit sites with misleading buttons in ads that trick you into clicking them or where it’s hard to close them.
- Look for file extensions: Be cautious if a link leads to unusual file types, like .exe files, that can be used to deliver malware.
- Avoid sites with re-directs or pop-ups: Avoid sites that bombard you with pop-ups or redirects to different pages.
If you want to effortlessly dodge dangerous websites while enjoying a smooth ride free from pesky ads and trackers, use Norton’s free private browser. Its built-in anti-fingerprinting protection helps keep your online activity under wraps, while the Web Shield feature helps block phishing attacks, malware, fake websites, suspicious URLs, dangerous downloads, and scams — for free.
4. Avoid suspicious emails
Emails can be spoofed (faked) to mimic trusted people or companies. Interacting with spoofed emails, especially clicking links or opening attachments, can expose your device to ransomware.
Tips to avoid interacting with suspicious emails:
- Enable spam filters: They should catch and block most phishing attempts and suspicious emails before they reach your inbox.
- Avoid suspicious attachments: Ransomware can hide in all sorts of attachments, such as PDFs, Word documents, and ZIP files. If you get an attachment in an unexpected email, scan it for malware before opening it, or avoid it.
- Check contact details: Look carefully at the sender’s address to help determine if it’s legitimate. Look for discrepancies between the displayed name and the email address, which can indicate spoofing.
- Be careful with suspicious links: Follow the advice from earlier sections by double-checking URLs and never click a link in an unsolicited email unless you’re certain it’s safe.
You can take further action against suspicious emails by manually labeling unwanted emails as spam. While it’s impossible to eliminate email scams completely, every report helps your inbox stay safer.
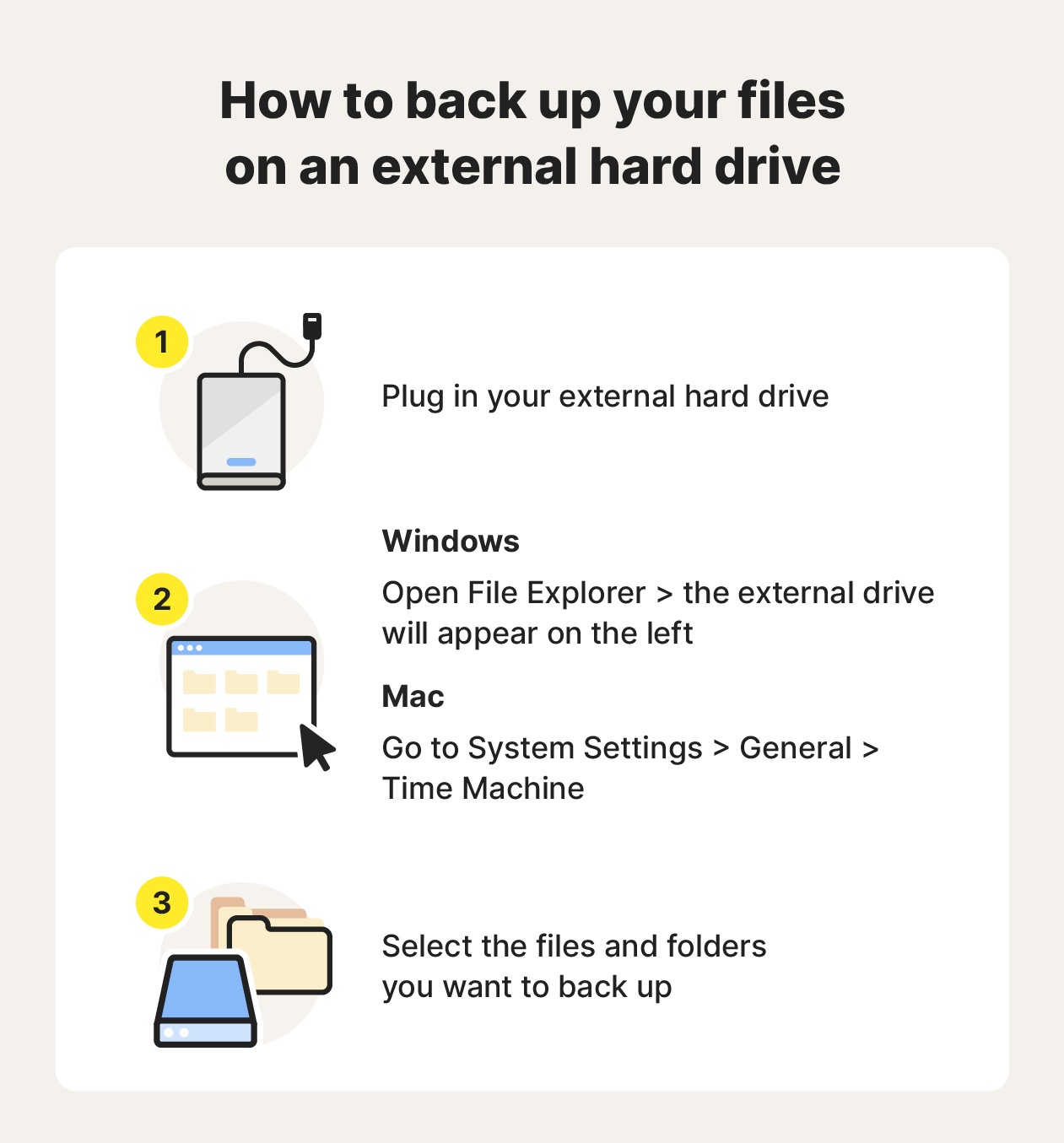
5. Perform backups regularly
Regular data backups are essential for minimizing the impact of ransomware. Since ransomware encrypts or locks your files, having backups helps you restore your data without paying a ransom or losing important files.
Ways to back up your data:
- Use the 3-2-1 backup strategy: This strategy suggests you keep three copies of your data: the original, one on a storage device at home, and another one stored elsewhere.
- Create offline backups: Use USB sticks or external hard drives and keep them disconnected from the internet when you aren’t using them.
- Automate backups: Use cloud services to sync folders automatically, ensuring your backups stay updated automatically.
- Activate file versioning: Check to see if your cloud service provider supports file versioning, which will automatically store older versions of your files.
Add passwords to physical devices to keep them safe in case of theft. If relying on cloud storage, use two-factor authentication to make it more difficult for cybercriminals to access your accounts. You should test your file backups at least once a year to be sure they’re still working. Test them more frequently if your data is important or high-risk.

6. Keep software and applications updated
Operating systems and applications need updates to improve functionality and patch security vulnerabilities. If your software is outdated, it’s an easier target for cyberattacks. Malware is known to take advantage of a program’s weaknesses.
In October 2024, Mozilla, the company behind the Firefox browser, announced a critical security vulnerability. Mozilla immediately released an update to patch the threat, protecting users from potential attacks as long as they updated to the new version that was released.
Considerations when keeping software secure:
- Enable automatic updates: You can save yourself from needing to check on updates by enabling automatic ones.
- Subscribe to security bulletins: Stay up to date by following the latest security updates of the software you use.
- Avoid dead software: Avoid using software that has reached its End of Life (EOL) status since it won’t receive security updates.
7. Practice good network management
Ransomware doesn’t just target individual devices — it can spread across an entire network, locking multiple computers or systems in the process. With good network management, you can limit the scope of potential infections, protecting critical segments of your network.
Network management tips:
- Limit administrative access: Limit the number of accounts with admin privileges to restrict the number of computers that can make network changes.
- Disable remote access: Remote access tools like Remote Desktop Protocol (RDP) can be exploited to install ransomware remotely. Disable unnecessary remote access services to reduce malware entry points.
- Check router settings: Use a strong, unique password instead of the default one and regularly update it.
- Segment your network: Segment your network into guest and private networks to help contain ransomware and prevent it from spreading across the entire network.
- Audit your network: Review your network regularly to see if you spot any unrecognized devices.
8. Safeguard your devices physically
When protecting your devices, you must consider both physical and digital threats. A stolen device can be compromised, infected with malware, or used to blackmail you into paying to prevent information from being leaked. How you protect your devices depends heavily on where you are.
Protecting your devices in different locations:
- Home: Storing your devices out of sight is smart. A thief who spots a laptop through a window could seize the opportunity. You should also secure your devices with strong passwords.
- Work: Lock computers with a PIN or password when you leave your desk. Secure portable devices in a lockable cabinet or drawer. If you have an office, lock the door before you step away.
- Public: Always keep devices with you or a trusted individual. If a device is lost or stolen, report the theft immediately to local authorities and try nearby lost-and-found locations.
Leaving a device in plain view attracts opportunistic thieves, whether you’re at home or in a public space. Unsecured devices provide easy access to your data. Good physical security practices are vital to help protect your personal information and devices from malware.
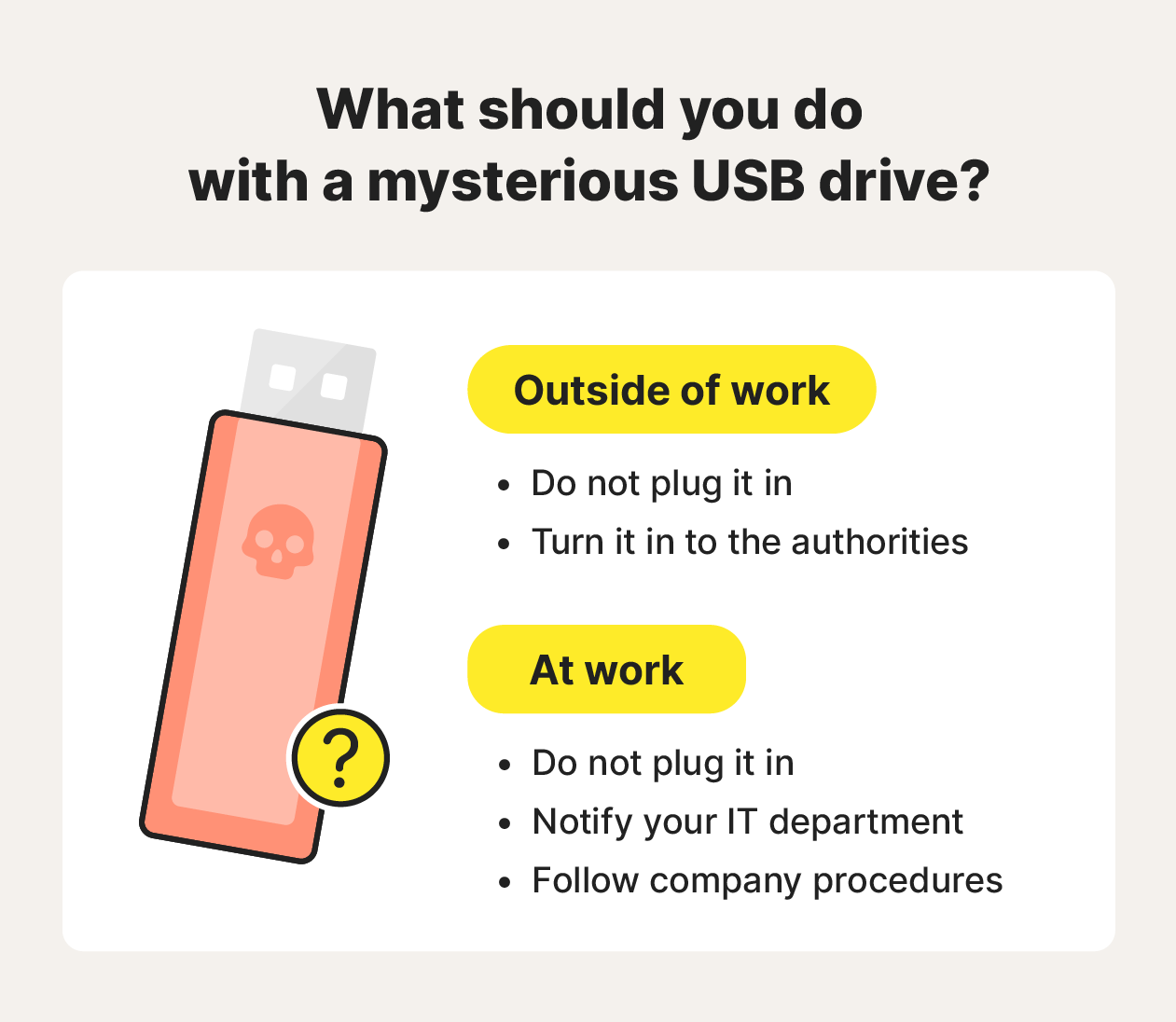
9. Don’t use unknown USB drives
Unknown USB drives, especially those found in workspaces or public spaces, should never be plugged into your devices. Rogue USB sticks are a known vector for ransomware and can potentially compromise your devices.
If you find an unknown USB at home or in public, don’t plug it in. The drive could contain sensitive information or malicious files that could harm your computer or lead to a data breach. If you find an unknown USB stick at work, don’t plug it in and give it to your IT department — and follow your company’s procedures.
Many companies prohibit the use of personal USBs on company devices. Rogue actors have been known to attempt drive-by plug-ins to compromise systems with ransomware. Companies and individuals concerned with this can rely on USB port-block software that limits USB port functionality to only authorized devices.

10. Use antivirus software
Using antivirus software helps keep your computer secure by regularly scanning your device to help detect ransomware before it can encrypt your files or steal sensitive data. However, not all antivirus tools include anti-ransomware features, so choosing software that meets your needs is important.
Norton 360 Deluxe not only comes with ransomware protection but also helps fight hackers, scams, and other malware — Norton technology blocks millions of cyber threats every day. With a plethora of privacy features, too, it’s your all-in-one digital bodyguard.
Educational resources on ransomware prevention
For a threat as widespread as ransomware, it’s important to couple cybersecurity tools with awareness. Here is some information on ransomware and emerging threats:
- Gen Q3/2024 Threat Report: Gen — Norton’s parent company — publishes regular reports on the most recent and prevalent threats to watch out for.
- CISA #StopRansomware Guide: The U.S. government’s cybersecurity agency has recommendations for how to protect your systems against ransomware.
- SANS Ransomware Resources: SANS, a leading cybersecurity education organization, keeps a list of helpful resources on how to spot and stop ransomware attacks.
- No More Ransom Project: The Netherlands’ National High Tech Crime Unit along with Europol’s European Cybercrime Centre cooperate to provide education about ransomware and prevention advice.
Staying up to date on the latest ransomware attacks can help you stay more secure. You can supplement the resources above by subscribing to cybersecurity news bulletins for real-time updates on the latest ransomware trends, using insights from a variety of sources to keep yourself informed.
Get powerful ransomware protection
A ransomware attack can cripple your device, costing you time and money to recover. Get Norton 360 Deluxe to help protect your devices from ransomware attacks and other malware. With a suite of security and privacy tools, you can rest easy knowing you’re safer from hackers, online scammers, and other bad actors who might come after your personal information and money.
FAQs
What should I do if I already paid the ransom?
If you’ve already paid the ransom, report the attack to local authorities, the IC3, and the FTC. If you can, provide them with a history of your communication with the hacker, as that might help the authorities track them.
Is it easy to get rid of ransomware?
The difficulty of removing ransomware largely depends on the specific variant and the scope of the infection. Certain types of ransomware can be eliminated fairly easily with trusted antivirus software, particularly if it hasn’t spread widely throughout a network.
Can resetting your PC remove ransomware?
Resetting your PC can help remove ransomware. A factory reset reinstalls the operating system, which may eliminate the ransomware — unless the recovery partition is compromised. However, a reset doesn’t guarantee complete removal, especially if the ransomware has deeply infiltrated the system or network.
Does a VPN protect you from ransomware?
No, a VPN doesn’t protect you from ransomware. A VPN's primary function is to secure your internet connection and maintain privacy by encrypting data transmitted between your device and the internet. While this can help protect against certain online threats, it doesn’t provide direct protection against ransomware attacks. Instead, you need antivirus software to help protect against malware like ransomware.
Are there free ransomware protection services?
There are some free ransomware protection tools out there, but they may come with limited features. Premium anti-ransomware services are often more comprehensive and might offer advanced detection capabilities, real-time monitoring, and other features.
How do I know I’m a ransomware target?
Some signs you’re the target of a ransomware attack include unexpected file encryption, a ransom message, unusual system behavior, missing files, or changes in file extensions.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.