What is email spoofing? A complete guide
Does something seem off about an email you received? Someone could be using email spoofing to mask their true identity and trick you into compromising your security. Discover what email spoofing is, how it works, and how to spot a spoofed email. Then get Norton 360 Deluxe to help protect against malicious email attachments and links.

Email spoofing definition
Email spoofing is a deceptive technique used to make an email appear as if it’s from a trusted source, like a friend or legitimate organization. Scammers commonly use spoofed email addresses in phishing attacks to trick recipients into sharing sensitive personal information or clicking dangerous links.
Email spoofing vs. phishing
Email spoofing is the act of altering an email sender’s address; the purpose is to make recipients believe an email is from a trusted source. Email phishing is a type of social engineering attack that may use a spoofed email address to dupe recipients into sharing sensitive information, clicking malicious links, or downloading a file containing malware.
How does email spoofing work?
Email spoofing works by creating a fake email address designed to mimic that of a real person or a trusted institution. The attacker then alters email header metadata like the sender’s address and subject line, crafts their message, and sends the spoofed email to their target.
Here’s a breakdown of how email spoofing works:
- Fake email created: A cybercriminal creates a bogus email address that closely resembles that of the person or organization they’re impersonating.
- Email headers forged: The attacker then modifies the email's header information—such as the "From," "Reply-To," and "Sender" fields—to make it look like the email came from a trusted source.
- Email content created: A bogus message is crafted to dupe the recipient into believing the email is legitimate and engaging with the scam.
- Spoofed email sent: The spoofed email is sent—if it’s convincing enough, the target may be tricked into clicking a malicious link or providing their personal details.
Reasons for email spoofing
Scammers use email spoofing to deceive recipients into believing a message is from a trusted source, which makes it easier for them to steal sensitive information, spread malware, or perpetrate a scam for financial gain.
Here’s a closer look at the most common reasons for email spoofing:
- Phishing: By impersonating trusted individuals or organizations, attackers can manipulate victims into revealing sensitive information like login credentials, sending money or gift cards, or downloading malware.
- Spreading disinformation: A bad actor could spoof an email to spread disinformation and fake news. This could lead to the impersonated organization or individual’s reputation being damaged.
- Bypassing email filters: By imitating trusted email structures and domains, spoofed emails can sometimes evade email spam filters.
- Staying anonymous: Email spoofing lets scammers carry out attacks while concealing their true identity. When combined with sophisticated technologies like a VPN, spoofing can be difficult to trace.
How to spot a spoofed email
The most effective ways to identify a spoofed email involve looking for email address irregularities, identifying mismatches between a sender’s display name and their email address, finding unnecessary urgency in the message, and spotting failures in security protocol checks.
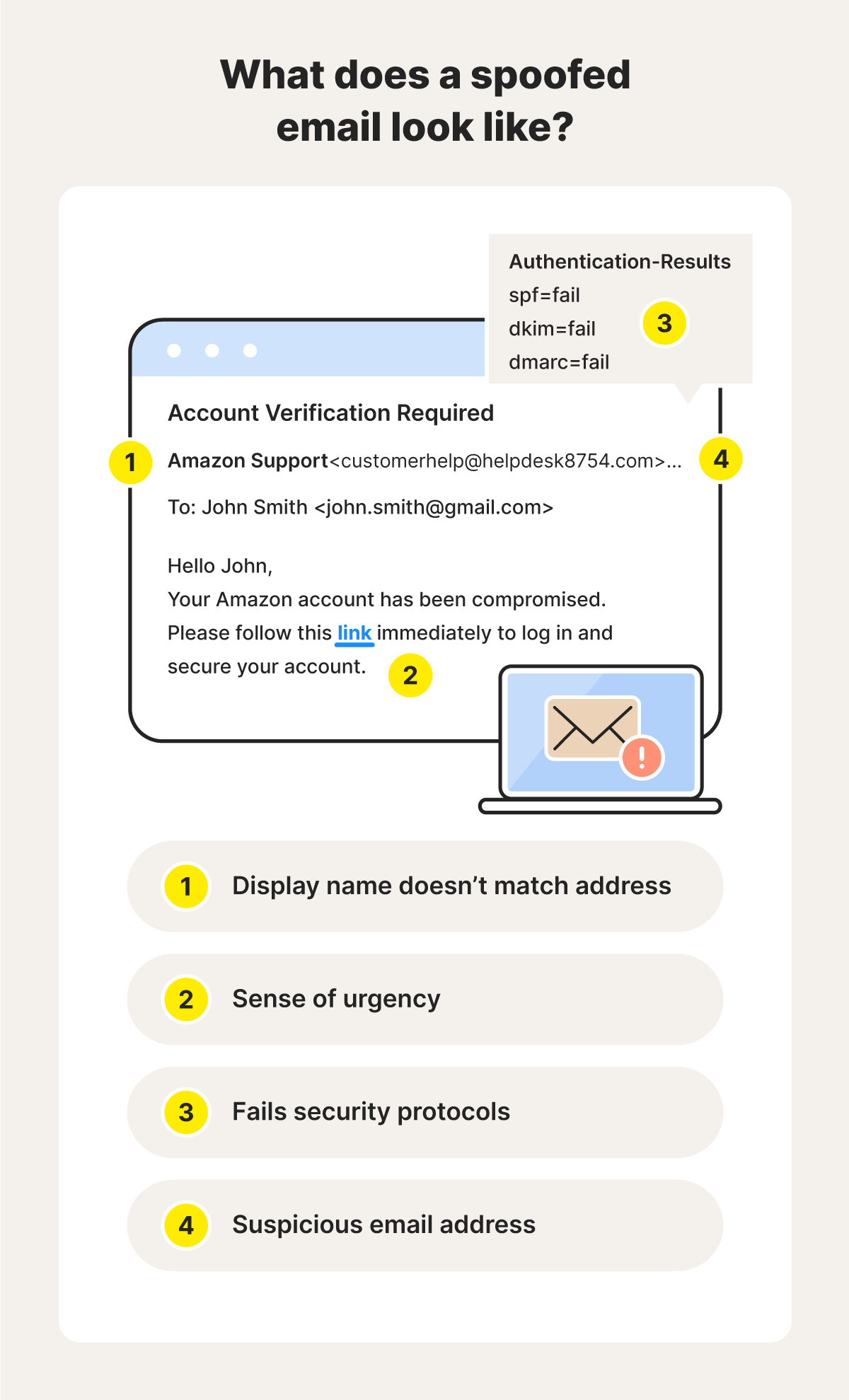

Suspicious email addresses
Email addresses that contain errors, deviate from the standard format, and don’t match the display name can indicate spoofing. For example, if the sender’s display name is Quick Orders but the email address is support@quick0rders.com, this is suspicious since the domain has the number “0” instead of the letter “o” in “orders.”
Display name and email address mismatch
Another hint of a spoofed email message is if the display name differs from the sender’s email address. Businesses, schools, and other organizations typically stick to consistent email formats.
In the example above, the display name is Amazon Support and you would expect the word “Amazon” to feature in the email address, too. Large organizations also typically use their domain name in their email address—meaning that in the example above, the email would end with @amazon.com.
Sense of urgency
Email spoofers often create a sense of urgency to pressure recipients into making hasty decisions. They might make claims about data leaks, limited-time offers, or scare you into thinking your device is at risk of malware. The idea is usually to scare you or excite you into acting without thinking.
Security protocol failure
Most popular email providers have security frameworks in place like the Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC) to help detect spoofed emails. You can check these authentication results to check if a message is from a legitimate sender.
Here’s how to check SPF, DKIM, and DMARC status from a phone or computer through a web browser:
On Gmail
- Open the email and click the three-dot icon in the top right corner.
- Select Show original.
- Check whether the email is marked pass or fail for each section.
On Outlook
- Open the email and click the three-dot icon in the top-right corner.
- Hover over View and then select View message details.
- Scroll through the details and view Authentication-Results to see if the email is marked pass or fail for each section.
On Yahoo Mail
- Open the email and click the three-dot icon in the top right corner.
- Select View raw message.
- Scroll through the details and view Authentication-Results to see if the email is marked pass or fail for each section.
Bear in mind that not all emails have these security protocols. So, if these protocols are missing, it doesn’t necessarily mean the email is spoofed, but be extra cautious and look further into the sender before replying.
How to help protect against email spoofing
Knowing how to spot spoofed emails is the first step in protecting yourself from the dangers they pose. But there may be times when a fake email is so sophisticated that there aren’t any obvious red flags. Here are some additional tips to help you stay safe:
- Don’t rush: If you’re unsure whether an email is legitimate, take some time to review it, and don’t feel pressured by urgent and threatening language.
- Don’t click: Avoid clicking any links or attachments when you’re unsure, as spoofed emails may contain links that can take you to malicious websites or expose you to malware.
- Don’t respond: Email spoofing doesn’t always involve malware. Some might be tech support scams or other online scams targeting your information or money, so don’t respond or call any numbers provided.
- Verify through another channel: If you know the purported sender and something seems off, text or call them to confirm whether they emailed you—or contact the company directly via the contact info on their website.
- Use antivirus software: The best antivirus software can help protect you from dangers spawning from email spoofing, like phishing, malware, and subsequent identity theft.
Detect suspicious emails with Norton
No matter how careful you are, spoofed emails and other malicious messages can still land in your inbox. Norton 360 Deluxe provides a rock-solid layer of defense against advanced spoofing attacks, with automatic unsafe link detection and a heuristic threat-detection engine to help stop malware attacks before they do damage.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.








Want more?
Follow us for all the latest news, tips, and updates.