What is spoofing? 12 examples of different spoofing attacks
Spoofing may be a silly word, but its impact is serious — scammers can use it to steal your money and identity. Learn more about spoofing techniques and read about 12 different attack types. Then get Norton 360 Deluxe to help protect against email and website spoofing in real time.

In 2023, the Internet Crime Complaint Center (IC3) received more than 880,000 complaints, with estimated losses surpassing $12 billion — and phishing and spoofing scams were the most frequently reported.
Cybercriminals use spoofing to impersonate individuals or entities you recognize, like family, friends, or businesses. This tactic preys on your trust, making it harder to distinguish deception from reality and leaving you vulnerable to scams.
What is spoofing?
Spoofing is a deceptive practice where someone falsifies information such as an email sender address or phone number to appear as a trusted entity. It’s often used by cybercriminals in scams, phishing, or cyberattacks to steal data or money, or gain unauthorized access to systems.
You can think of spoofing as a short-term form of identity theft. Scammers typically keep their impersonations brief, manipulating an email, text message, phone call, or website to pretend to be a friend, company, government entity, or other reputable source.
While typically malicious, spoofing does also have legitimate uses, such as in cybersecurity testing, or as a form of privacy protection where individuals want to mask their identity or activity.
How does spoofing work?
Most spoofing schemes rely on impersonating a person or entity to trick a target into doing something that benefits the spoofer. While the specific technical means vary depending on the type of spoofing, the fundamental principles remain the same.
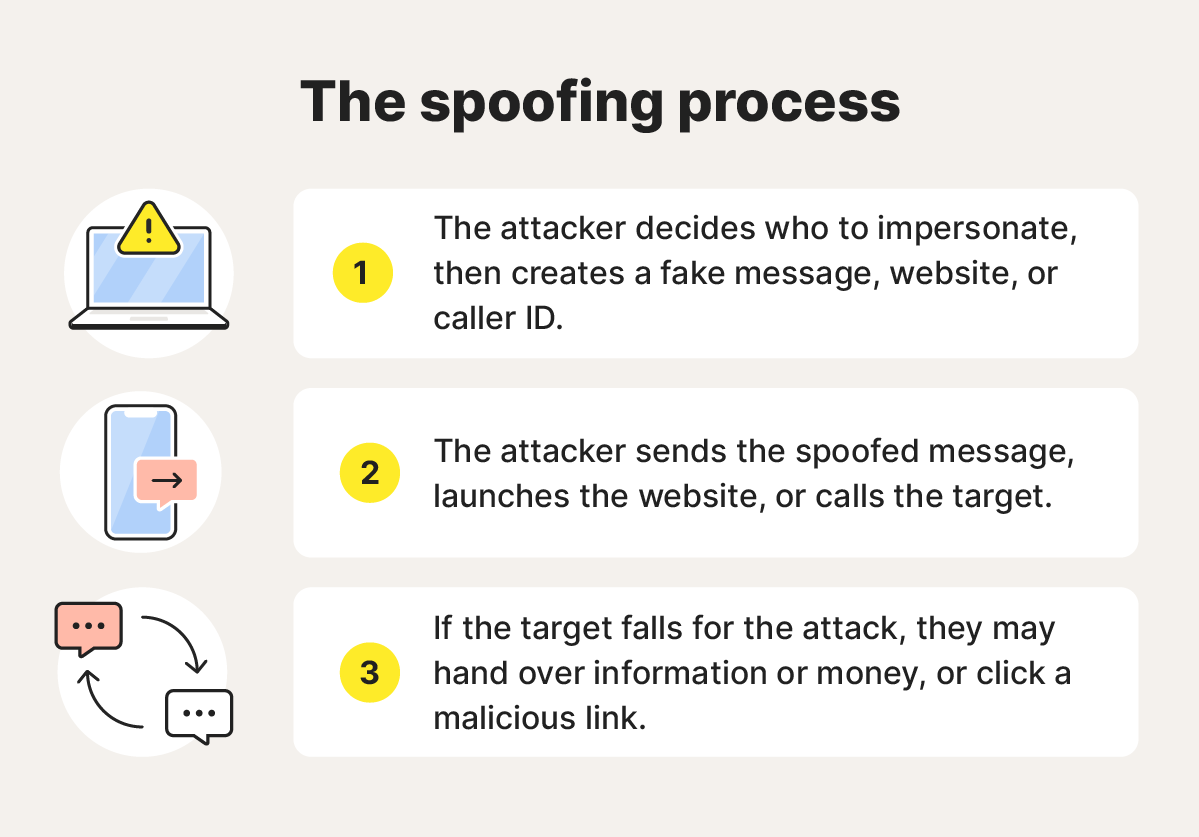
A spoofing attack that targets individuals often follows a similar process:
- Forging information: The spoofer decides who to impersonate, then creates fake information, often copying a website, email, or caller ID so that it’s the same or nearly identical.
- Using the identity: The spoofer contacts their target by email, text, phone call, pop-up ad, or another medium, and asks the target to click a link, give money, share personal information, or visit a website.
- The target responds: If the target believes the spoofer, they respond by doing whatever the objective of the attacker is. This usually results in financial loss, risk of identity theft, or malware landing on their device.

It’s a sneaky ploy — and, all too often, it works. But knowing about the different kinds of spoofing attacks out there can help you spot spoofed communications, allowing you to short-circuit this process before your security is compromised.
12 different types of spoofing, with real-life examples
From fake emails to forged websites, cybercriminals use a variety of spoofing methods to manipulate trust and steal information. In this section, we’ll explore 12 common types of spoofing, complete with real-life examples to help you recognize and avoid these threats.
1. Email spoofing
Email spoofing is when cybercriminals send bogus emails to deceive recipients using email addresses that appear nearly identical to trusted organizations or contacts. Other elements of the email are often also crafted to mimic the entity’s branding, including logos and messaging.
Email spoofing uses social engineering tactics and is often realized as a phishing attack, aimed at stealing personal details, money, or tricking victims into clicking malicious links.
Detection tips:
- Sender anomalies: Scammers will either register a fake domain or a sender’s name that’s similar to the legitimate entity. They’ll often swap letters or numbers in the address (like “amaz0n” instead of “amazon”).
- Suspicious links: Be wary of links in emails. Always hover over the link and look at the URL in the bottom left corner to see if it matches an address you’d expect to see. When in doubt, don’t click. Be wary of attachments, too, since they can carry malware.
- Sense of urgency: Language or a deadline in the email aiming to pressure you into acting quickly without thinking is a sign the sender is likely not legitimate.
2. Text spoofing
Text spoofing tricks you into believing a message is from someone you trust by faking the caller ID. Like email spoofing, these phishing scams rely on clever impersonation and exploiting systems. Virtual phone number services make this easier, allowing overseas criminals to send messages from local numbers.
Fraudsters use text spoofing to steal personal information or money through smishing (SMS phishing). Much like email phishing, the idea is to get you to tap a malicious link, download malware, or provide personal information.
Detection tips:
- Urgent tone: Scammers frequently exploit fear and urgency, like fake bank messages claiming your account will be locked unless you share your PIN.
- Unclickable sender fields: Tap the sender field in a text to see details like name and number. If unclickable, the sender may be hiding their identity.
- Links or attachments: Fraudulent texts often hide malware in links or attachments. Verify URLs carefully and use antivirus software to detect malicious content.
3. Caller ID spoofing
Caller ID spoofing is displaying a familiar name or number to trick you into answering a call. Similar to text spoofing, these scams impersonate people or companies.
Like email and text spoofing, the goal of Caller ID spoofing is to steal your money or information through a process called vishing (voice phishing). For example, a scammer might impersonate Apple tech support, saying they need to connect to your device to fix an issue.
Detection tips:
- High-pressure calls: Scammers create urgency to pressure you to provide personal information or make payments immediately.
- Number doesn’t match: If the name displayed on your phone is familiar but the number doesn’t match, it’s probably spoofed.
- Robocalls: Pre-recorded messages are used to scam many victims quickly and often just ask you to type a number, say your name, or answer a yes-no question.
4. Website spoofing
Website spoofing occurs when a scammer imitates a website to steal your information. The website looks safe or close enough to the real thing for people to insert their username, password, or other information.
Criminals can also use fake websites to get you to download malware. For example, ransomware is a specific type of malware that locks your computer or files. To get these files back, criminals will ask you to pay a ransom.
Detection tips:
- Misspelled URLs: Scammers create web addresses with small spelling changes, such as “g0ogle.com” instead of “google.com.”
- Unusual design choices: While fraudsters will try and make the fake website look similar to the legitimate site, it may have an odd layout or poor grammar.
- Unexpected requests for information: The site may ask for unnecessary and unexpected sensitive information.
5. DNS spoofing
DNS spoofing, or DNS cache poisoning, tricks servers into sending users to fraudulent websites. This technique is more technically advanced than typical website spoofing, targeting the infrastructure that directs internet traffic.
These attacks aim to steal personal information or install malware by tricking users into interacting with fake sites. Just like website spoofing, DNS spoofing can also be used to distribute malware. These attacks can also facilitate man-in-the-middle attacks, which allow hackers to steal information in transit.
Detection tips:
- Unexpected redirects: You enter a legitimate URL into your browser and are redirected to an unexpected or suspicious website.
- Unusual slowdowns: Redirects through malicious DNS servers can lead to unusually slow internet speeds.
- Security warnings: If you see a security warning in your browser, like an SSL site certificate error, you might be being directed to a malicious site.
6. IP spoofing
IP spoofing involves modifying the source IP address in the headers of data packets to impersonate another device or network. This may allow hackers to bypass online security measures, disguise their identity and location, and carry out malicious activities undetected.
IP spoofing serves multiple malicious purposes, including launching DDoS attacks to overwhelm networks, gaining unauthorized access to steal data, and masking identities to evade detection during illegal activities.
Detection tips:
- Unusual network activity: There are sudden, unexplained spikes in network traffic or connections originating from unexpected or unfamiliar locations.
- Inconsistent packet headers: There are discrepancies in packet headers, such as mismatches between the source IP address and the expected address.
- Loss of connection: A network experiences frequent disconnections or difficulty accessing certain resources.
7. Identity spoofing
Identity spoofing refers to the act of impersonating someone else through various communication channels like text, email, phone, or social media. The aim is to deceive the target into believing the imposter is trustworthy, often mimicking personal or professional identities for the spoofer's gain, whether for financial, reputational, or malicious purposes.
Detection tips:
- Unusual requests: If someone you know suddenly asks for money or makes an unusual request, it could be a scammer spoofing their identity through a SIM swap scheme.
- Unknown number: If you receive a call or text from an unknown number claiming to be someone you know, verify their identity by contacting them directly through another communication method you typically use.
8. Facial spoofing
Facial spoofing is a type of identity spoofing that tries to bypass facial recognition software using stolen images. Scammers may collect publicly available photos from social media or other sources to trick systems into believing they are the person in the photo.
To help prevent cybercriminals from using your selfies and other photos, check your social media settings and set your accounts to private.
Leyla Bilge, Director of Scam Research Labs at Gen Digital, shared her thoughts on the acute risk posed by facial spoofing in a recent interview:
Leyla Bilge, Director, Scam Research Labs, Gen
“Facial recognition apps are very advanced right now, so you don't need to have a super clear picture to be able to authenticate.”
9. Filename extension spoofing
Filename extension spoofing occurs when a malicious file is disguised by using a misleading or altered extension. For example, a file with a ".jpg" extension may actually be an executable file like ".exe." This trick aims to deceive users into opening harmful files, often leading to malware infections or data breaches.
Filename extension spoofing is effective because many users focus on visible extensions, neglecting the actual file type. This exploit can also bypass basic security checks, as some operating systems or email clients may not flag the discrepancy.
Detection tips:
- Visible extensions: Extensions are normally hidden, so look out for file names ending with an extension like .exe or a double extension like .doc.exe.
- Unusual icons: Pay attention to file icons that don't match their claimed type — e.g., a Word doc displaying a different icon.
- Unexpected file sizes: If you see a file that’s unusually small (or large) for what you’d expect the content to be, it might be a compression error — or, the size could signal something more dangerous.
10. GPS spoofing
GPS spoofing involves manipulating GPS-enabled location services to trick systems into thinking a device is somewhere else. Spoofers can use it for both nefarious and relatively harmless purposes.
While spoofing your location to get in-game rewards could be considered innocent fun, some apps will suspend accounts that engage in this activity. But cybercriminals can also use GPS spoofing for nefarious purposes, such as mimicking trusted locations to commit fraud and other crimes.
Detection tips:
- Inconsistent location data: If a device suddenly appears miles away from where it was or should be, the unexplained location changes might be a sign of GPS spoofing.
- Unexpected GPS behavior: Spoofing GPS data can lead to routes that are improbable based on geography — e.g., a mobile device appearing to cross a large body of water without a bridge.
11. MAC spoofing
MAC spoofing involves faking a device’s MAC (Media Access Control) address to impersonate another device on the same network. MAC spoofing is less common these days because MAC addresses are now randomized on all major platforms. However, hackers can still target older devices or specific hardware.
Detection tips:
- Unexpected devices: Look for unexpected devices listed in your network monitoring app or router logs.
- Suspicious network activity: Watch out for strange activity like duplicated IP addresses or devices with suspicious names.
12. ARP spoofing
Address Resolution Protocol (ARP) Spoofing, also called ARP poisoning, is a network attack where hackers send fake ARP messages to a local network. This tricks devices into associating the attacker’s device with a legitimate IP address. ARP attacks are often used to intercept, modify, or disrupt data in transit.
Detection tips:
- Unexpected traffic issues: ARP spoofing can cause delays in network communication or missing data during file transfers.
- Unusual ARP table entries: If your device’s ARP table has duplicate or suspicious MAC addresses mapped to the same IP address, that could be a sign of spoofing.
How do you prevent spoofing attacks?
It’s impossible to prevent people from targeting you with spoofed communications. But you can help reduce your exposure and reduce the risk of falling victim to malicious spoofing by taking precautions and educating yourself on how to spot a spoofing attack.
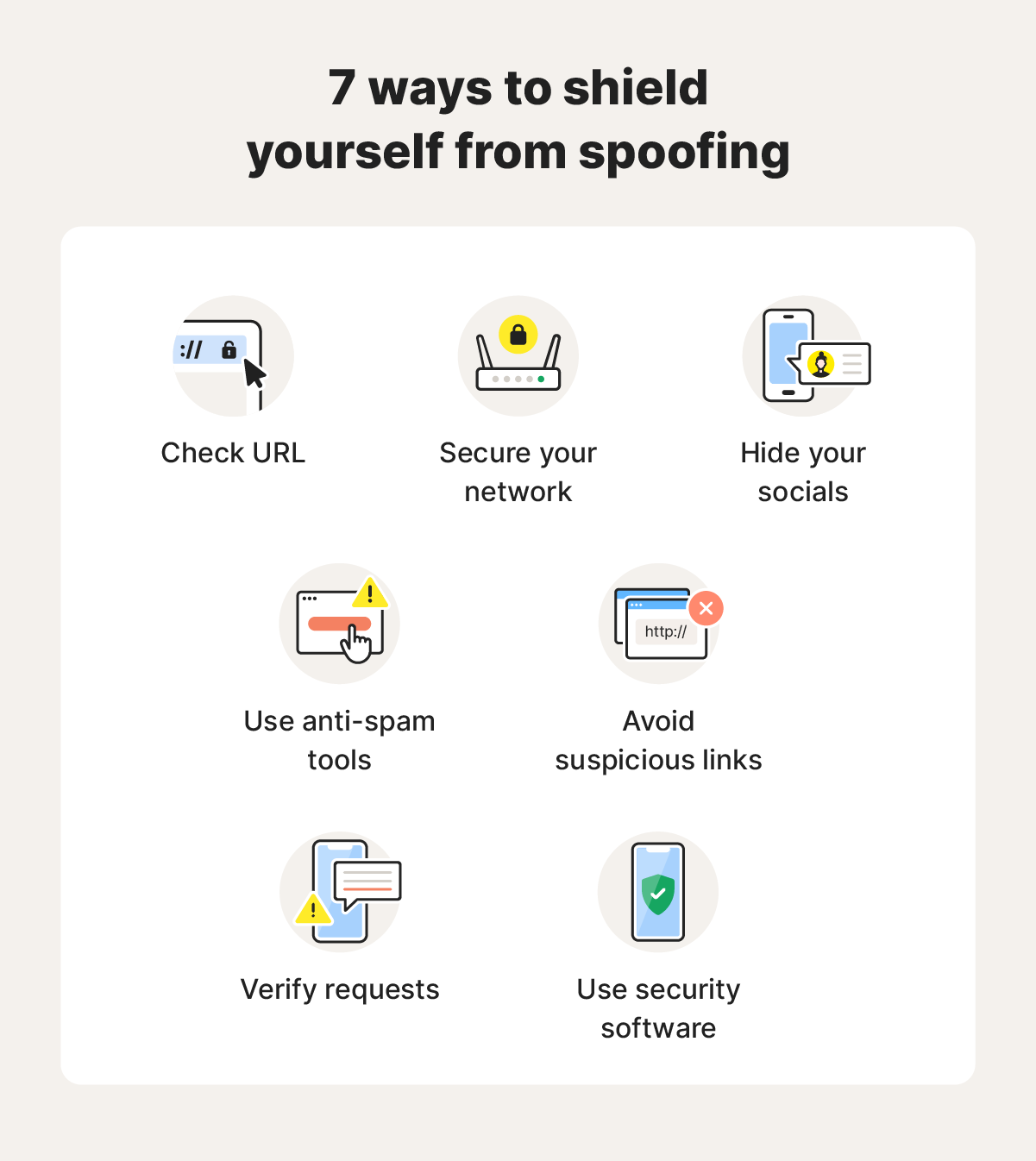
Here are some cybersecurity best practices to help keep you safe from spoofing:
- Verify the website: Check the browser address bar for HTTPS, and check the URLs for typos or slight variations. You can use a secure browser to help detect spoofed websites.
- Secure your network: Use strong passwords on your router, enable firewalls to block packets with forged IP headers, and monitor network activity to block unauthorized access.
- Hide your socials: Ensure your social media profiles are private to prevent attackers from easily stealing your information and photos.
- Use anti-spam tools: Use built-in anti-spam features or third-party tools to help keep spam and potentially spoofed calls or emails away from your devices.
- Avoid suspicious links: Don’t click suspicious links or download unknown attachments in emails or text messages, because they could lead to a phishing site or malware.
- Verify requests: If you receive an unusual or suspicious request for sensitive information, confirm the request via an official channel before providing any info.
- Use security software: Use strong security software like Norton 360 Deluxe to help protect against malicious links, spoofed websites, and other online scams.

Help protect against spoofing
Protecting against spoofing attacks — and their repercussions — requires comprehensive security that goes beyond basic measures.
Norton 360 Deluxe provides a powerful defense against advanced online attacks, with a heuristic threat-detection engine that helps stop malware attacks before they do damage. Get ironclad protection against malicious links, hackers, and scams, as well as a built-in VPN to encrypt your connection and keep your activity private.
FAQs
What are the differences between spoofing and phishing?
Spoofing is a technique used to falsify data, such as email addresses or phone numbers, to impersonate trusted sources. Phishing is a specific type of attack that can use spoofing to trick individuals into revealing sensitive information, often through fraudulent emails or messages designed to steal credentials or financial data.
What happens when you are spoofed?
If your details are spoofed, attackers may impersonate you to deceive others, potentially leading to fraudulent activities carried out under your name. This form of identity theft is very hard to prevent but can result in long-term legal and reputational damage.
Is spoofing illegal?
Not all forms of spoofing are illegal; it depends on the intent and context. Legal spoofing could include faking your location to view another streaming library, or arranging a holiday meet-up ahead of time via a dating app. However, these actions may violate platforms’ terms of service and could result in account suspension or termination.
How do you tell if your phone number is spoofed?
If your phone number is spoofed, you may notice strange calls from unknown numbers claiming to be you, or people reporting missed calls from your number without your involvement. Additionally, if your number appears in scam reports or call-blocking apps, it’s a sign your number may be misused in spoofing.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.