Man-in-the-middle attack: Definition + types
A man-in-the-middle attack involves a cybercriminal placing themselves in the middle of two parties communicating with each other online to intercept or alter sensitive data. Learn more about this invasive type of hacking and what you can do to avoid it. Then, get a powerful cybersecurity toolkit to help protect your data and devices.

What is a man-in-the-middle attack?
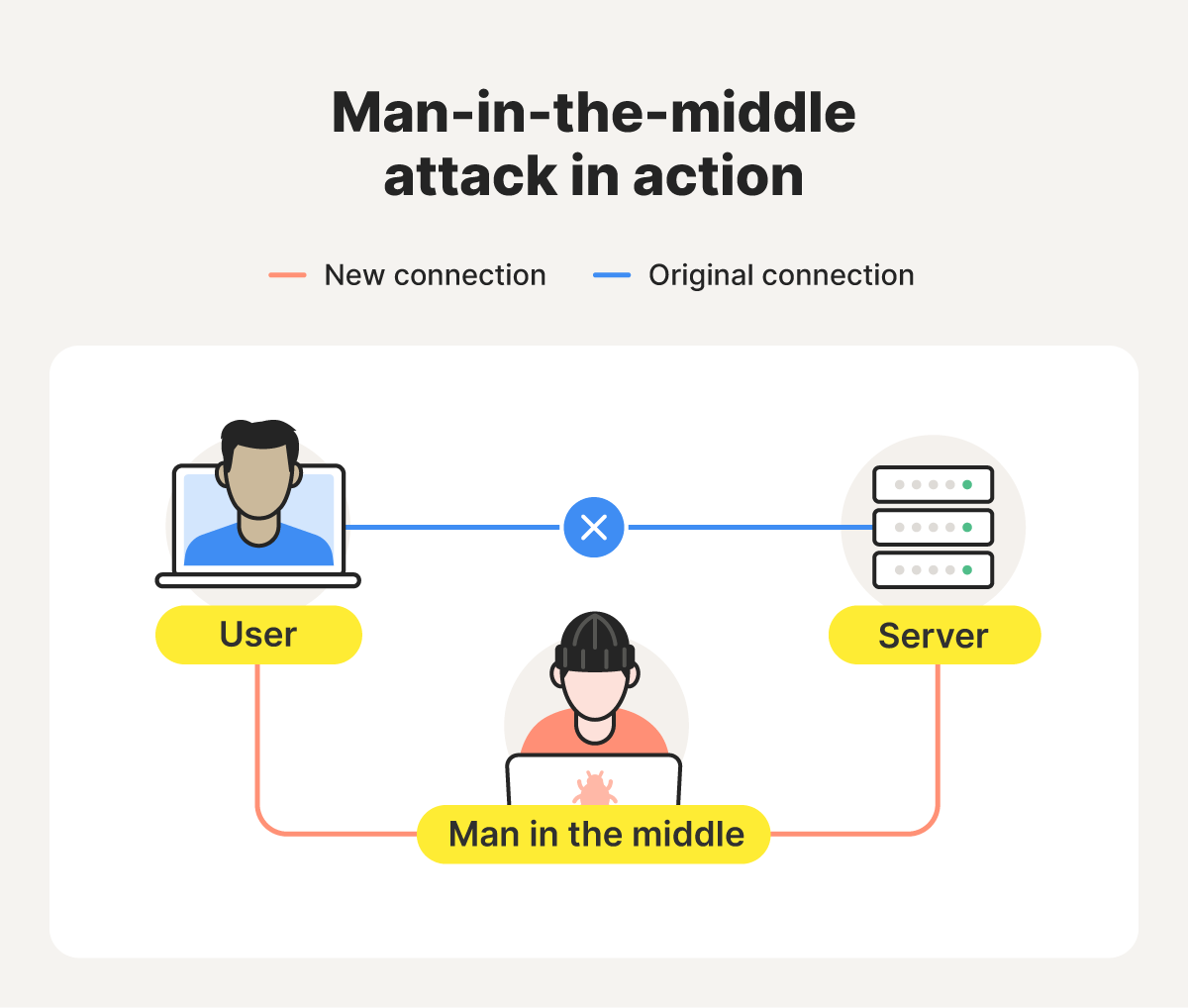
A man-in-the-middle (MITM) attack, also known as an on-path attack, is when a cybercriminal places themselves between two communicating parties — usually a client (like a user’s computer or phone) and a server. Once in position, the attacker can intercept data like passwords, credit card numbers, or messages while they’re in transit.
MITM attackers essentially re-route direct connections through a new path that includes themselves as a middle-man. This means they can not only see the data being transmitted, but might also be able to alter it, editing emails before they can reach their intended recipient, for example.
Attackers can use this hacking technique to capture sensitive data for use in fraud, as part of larger social engineering attacks, or to deliver malicious content, such as malware, to the victim.

If someone tries to intercept your data through a man-in-the-middle attack, you might notice signs like:
- Browser certificate warnings (such as “Your connection is not private”).
- Frequent and unexpected website connection errors (404 errors).
- Notifications about unauthorized logins to your online accounts.
- Automatic redirects to a different URL when you click a link.
- Strange pop-up windows, messages, or ads.
How do man-in-the-middle attacks work
Man-in-the-middle attacks typically unfold in two phases: interception and decryption. After these fundamental phases, attackers can use their access to eavesdrop or manipulate data. The process typically goes like this:
- Interception: Cybercriminals typically target unsecured or poorly secured public networks because it’s easier to steal unencrypted data. They use techniques such as ARP spoofing or DNS spoofing to gain access to the network and position themselves between the victim's device and the server.
- Decryption: Once positioned between two parties on a vulnerable network, attackers deploy tools to decrypt and read the victim’s transmitted data. If they’re targeting an encrypted connection (like HTTPS), attackers may use methods like SSL stripping to downgrade the connection to an unsecured HTTP connection.
- Eavesdropping and modification: If their attack is successful, attackers can view data that travels over the network, whether it’s login credentials, banking information, or other personal information. Then, they can exploit the information to commit identity theft or financial fraud or modify it as part of a social engineering attack. They may also be able to inject malware or redirect users to fake, malicious websites.
One specific form of man-in-the-middle attack, called an evil twin attack, involves cybercriminals creating fake Wi-Fi networks that emulate real ones, often in public spaces. A victim might then join the fake network by mistake, and any data they transmit during their session passes through the attacker’s device, potentially leaving them vulnerable to account-takeover attacks, financial fraud, or identity theft.
Types of man-in-the-middle attacks
All man-in-the-middle attacks aim to intercept and steal data as it travels, usually by exploiting a lack of encryption or removing it. What distinguishes different types is the way the attacker positions themselves and what network layers they target. Learn more about the main MITM attack variants and key warning signs for each type.
- HTTPS spoofing: If you’re on a URL that begins with “https,” it’s a sign that the website is secured with encryption, which means attackers can’t read the data you share. To get around this, HTTPS spoofers may create a malicious copy of the real website that instead uses the less secure HTTP protocol. They’ll then aim to get you to visit that website instead, perhaps by using a phishing attack with a fake link.
- SSL/TLS stripping: Even websites that are typically secured with HTTPS can be vulnerable to MITM attacks. Sophisticated attackers may be able to downgrade websites to an unsecured HTTP connection using SSL stripping techniques. The key warning sign to look out for is a missing SSL certificate, which you can spot if there’s no padlock in your browser’s address bar or the URL begins with "http”.
- IP spoofing: Attackers may modify the source IP address of data they retransmit during a MITM attack to make it look like it’s coming from a trusted source. This helps them trick you into thinking you’re interacting with a trusted website or person, so you’ll give them sensitive information.
- DNS spoofing: Domain Name Server (DNS) spoofing is a technique that forces a user to a fake website rather than the real one the user intends to visit. Like many other MITM attacks, you can generally tell this attack is underway if the SSL certificate is wrong or missing, or the website’s URL is slightly off.
- Email hijacking: Cybercriminals sometimes access company email accounts by intercepting login credentials. In a business email compromise (BEC) scam, attackers may intercept sensitive communications to alter financial instructions or send fake invoices. When this attack happens, you may get notifications about unusual account logins or unexpected requests for payment.
- Evil twin attacks: Cybercriminals can set up Wi-Fi hotspots with legitimate-sounding names, often copying an authentic public Wi-Fi network. Once a user connects to the “evil twin” network, the attacker can monitor their online activity and potentially intercept login credentials, payment card information, and more. Some common warning signs include sudden pop-ups and certificate errors.
- ARP spoofing: Attackers can manipulate Address Resolution Protocol (ARP) messages, which link IP addresses to MAC addresses (unique physical addresses assigned to each device on a network). This allows them to redirect traffic through their device by convincing the network that their MAC address is the legitimate gateway or destination server. Signs of ARP spoofing include unusual network slowdowns or frequent disconnections.
- Session hijacking: Criminals steal session cookies or authentication IDs to impersonate legitimate users and gain access to systems, sites, and applications. If your session is stolen, you might get logged out, receive an alert that there are too many active sessions, or find unusual account activity.
- Replay attacks: Attackers record valid login data or transaction messages and replay them later to impersonate users or repeat payments. Because the captured data is still valid for a short time, criminals can gain access or duplicate transactions even after the real user has already logged out. So, you might notice duplicate charges and transaction confirmations.
Tips to help avoid man-in-the-middle attacks
MITM attacks can expose you to financial loss and identity theft. But you can take some easy steps to help protect yourself, including only ever using websites secured with HTTPS, sticking to networks you know and trust, and learning to detect common scams. Here’s a more detailed summary of what you can do to stay safer against man-in-the-middle attacks:
- Avoid untrustworthy networks: Only use trusted Wi-Fi networks, ideally avoiding public Wi-Fi wherever possible. If you do have to use a public network, turn on a VPN and avoid logging in to sensitive accounts to help protect your data.
- Make sure websites are secure: If you’re suspicious about whether a website is secure, check whether the URL in your address bar starts with “https” (as opposed to “http”) before entering personal or financial information. This isn’t a foolproof way to dodge scams, but it is a good place to start.
- Use a virtual private network (VPN): A virtual private network encrypts your internet traffic, making it safer to browse on public Wi-Fi or other networks you don’t trust entirely. Use Norton VPN for better protection against MITM attacks and other threats to your data’s security.
- Set strong passwords: Use unique, complex passwords that are harder for hackers to guess or crack and use two-factor authentication (2FA) for a second layer of security (like a code sent to your phone). While this won’t help you avoid MITM attacks, it will mean your online accounts are harder for cybercriminals to access with stolen data.
- Don’t trust unsecured messaging apps: Avoid sharing sensitive personal or financial details on messaging apps unless you’re confident that they provide sufficient protection, like encrypting your communications.
- Try a scam detector: Use a scam detector to analyze suspicious emails and messages before you click any links or download any attachments they contain. Many MITM attacks begin with phishing messages in your inbox, and avoiding falling for them can help you getting lured to a fake site that steals your data.
- Get cybersecurity protection: Norton 360 Deluxe provides hacking protection, a password generator and manager, a scam detector, and a VPN. Combined, these features give you a complete toolkit to encrypt data you transmit, block unsafe connections, and spot scams or phishing attacks as they appear, helping you protect against man-in-the-middle attacks and other cyberthreats.
Man-in-the-middle attack examples
MITM attacks can be carried out by governments, companies, and individual hackers — all for varying reasons. Learn more about some notable man-in-the-middle attacks of the past and how they happened.
- The DigiNotar MITM attack: In 2011, the Dutch certificate authority DigiNotar was breached, allowing attackers to issue over 500 fraudulent SSL/TLS certificates for trusted websites. They used these fraudulent certificates to execute a man-in-the-middle attack, tricking web browsers into believing they were connecting to a legitimate site so attackers could intercept and decrypt sensitive data.
- NSA surveillance: In 2013, former NSA contractor Edward Snowden revealed that the U.S. National Security Agency (NSA) had been conducting extensive internet surveillance programs since the early 2000s. One of these programs involved tapping into the fiber-optic cables linking Google and Yahoo data centers to collect large amounts of user data, some of which may have been from U.S. users.
- The Lenovo Superfish adware attack: Starting in 2014, Lenovo began pre-installing the Superfish adware on its PCs. The software acted as a man-in-the-middle proxy, installing a malicious root certificate that allowed it to intercept, decrypt, and re-encrypt secure HTTPS connections. Armed with intercepted browsing data, the manufacturer intended to display targeted ads without user permission.
Protect yourself from MITM attacks
From securing your connections with a robust VPN to detecting phishing attempts before they can redirect you to malicious sites, Norton 360 Deluxe can help you keep your sensitive data more secure. Get it today to help protect your accounts, finances, credit, and reputation from the diverse cyberthreats you might be exposed to.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.









Want more?
Follow us for all the latest news, tips, and updates.