20 types of phishing attacks + examples and prevention tips
Have you ever received a suspicious email? If so, it may have been phishing. To ensure you’re prepared for all types of phishing scams, read this helpful guide.

Almost every time you set up an online account, it's likely you're providing some form of personal information.
Whether it’s your birthday, your Social Security number, or your mother’s maiden name, you probably have shared it online at one time or another without a second thought.
And because sharing personal information online is so mainstream, cybercriminals have taken advantage of it with phishing attacks, a cybercrime in which scammers try to get you to reveal sensitive information.
Not only are these attacks common, but there are many different types of phishing techniques to watch out for, including:
- Spear phishing
- HTTPS phishing
- Email phishing
- Social engineering
- Angler phishing
- Clone phishing
- Vishing
- Pharming
- Watering hole phishing
- Whaling
- Pop-up phishing
- Deceptive phishing
- Evil twin phishing
- Search engine phishing
- Image phishing
- Website spoofing
- Smishing
- Domain spoofing
- Man-in-the-middle (MITM) attacks
- Social media phishing
To ensure you’re prepared for even the most clever types of phishing scams, read through this helpful guide.
1. Spear phishing

Spear phishing is a targeted phishing method that cybercriminals use to steal your information by impersonating a trusted source. If they get the information they want, they may use it for malicious purposes such as identity theft. Unlike some other forms of phishing, spear phishing targets a specific individual.
An example of this would be a phishing email targeting an employee of a company by pretending to be their boss. In the email, the scammer may try to get the employee to give up private information that the scammer can later use to their advantage.
- Spear phishing prevention tip: Always double-check the sender's email address before responding.
2. HTTPS phishing
HTTPS phishing is when a cybercriminal tricks you into giving up your personal information using a malicious website. To get you onto these sites, the phisher will hide the malicious link within an email, often masquerading as a link to a legitimate site.
For example, an HTTPS phishing scam could be an email asking you to log into Instagram to secure your account. In the email, it would look like you’re talking to an Instagram support member when in fact it is all a hoax. When you click the link, you’ll instead be taken to a fake website designed to steal your login credentials.
- HTTPS phishing prevention tip: Always look closely at the URL of a site before logging in.
3. Email phishing
One of the most common phishing attacks is email phishing. Email phishing is when a cyberattacker sends you an email pretending to be someone else in hopes that you’ll reply with the information they requested. Once you’ve given the attacker what they want, they may use your information for criminal activities or even sell your information on the dark web.
One phishing email example is a cybercriminal emailing you while pretending to be your relative. In the email, they may try to get you to divulge personal information such as your address, birthday, login credentials, or more.
- Email phishing prevention tip: Don’t respond to an email unless you’re sure the sender is who they say they are.
4. Social engineering
Social engineering is a broad term that describes phishing tactics used to manipulate people into giving up private information. To make these scams more effective, scammers often research the person they are trying to scam and use that information to their advantage.
For example, a cybercriminal may contact you from a random number claiming to be one of your friends in desperate need of help. To get you to act quickly, the scammer will create an elaborate storyline designed to get to your emotions, asking you for money or sensitive information.
- Social engineering prevention tip: If you receive an urgent request, avoid panicking and take your time to assess the legitimacy of the situation. It may also help you to get a second opinion from a friend or family member.
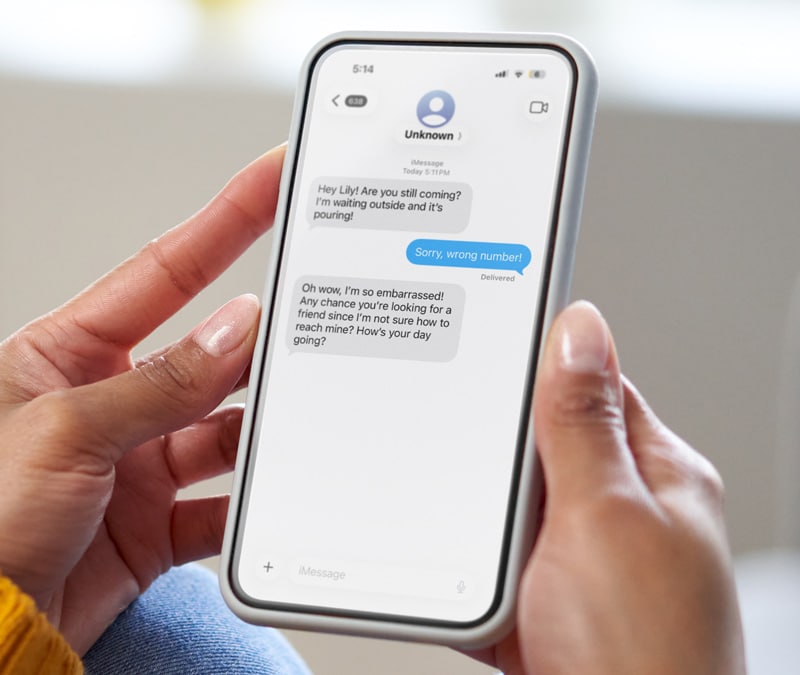
5. Angler phishing
Angler phishing is a type of phishing attack in which a cyberattacker pretends to be a customer service agent on social media. In addition to trying to steal your personal information, these cybercriminals may also try to infect your device with malware.
Some angler phishing examples may include a Twitter account pretending to be a customer service agent for a company like American Airlines. Unlike the official American Airlines support account, an angler phisher’s account will not be verified. In these scams, they may reply to a customer’s tweet that is directed to the official support account in hopes that the customer won’t notice.
- Angler phishing prevention tip: Always research the social media account before replying, following their instructions, or clicking any links.
6. Clone phishing
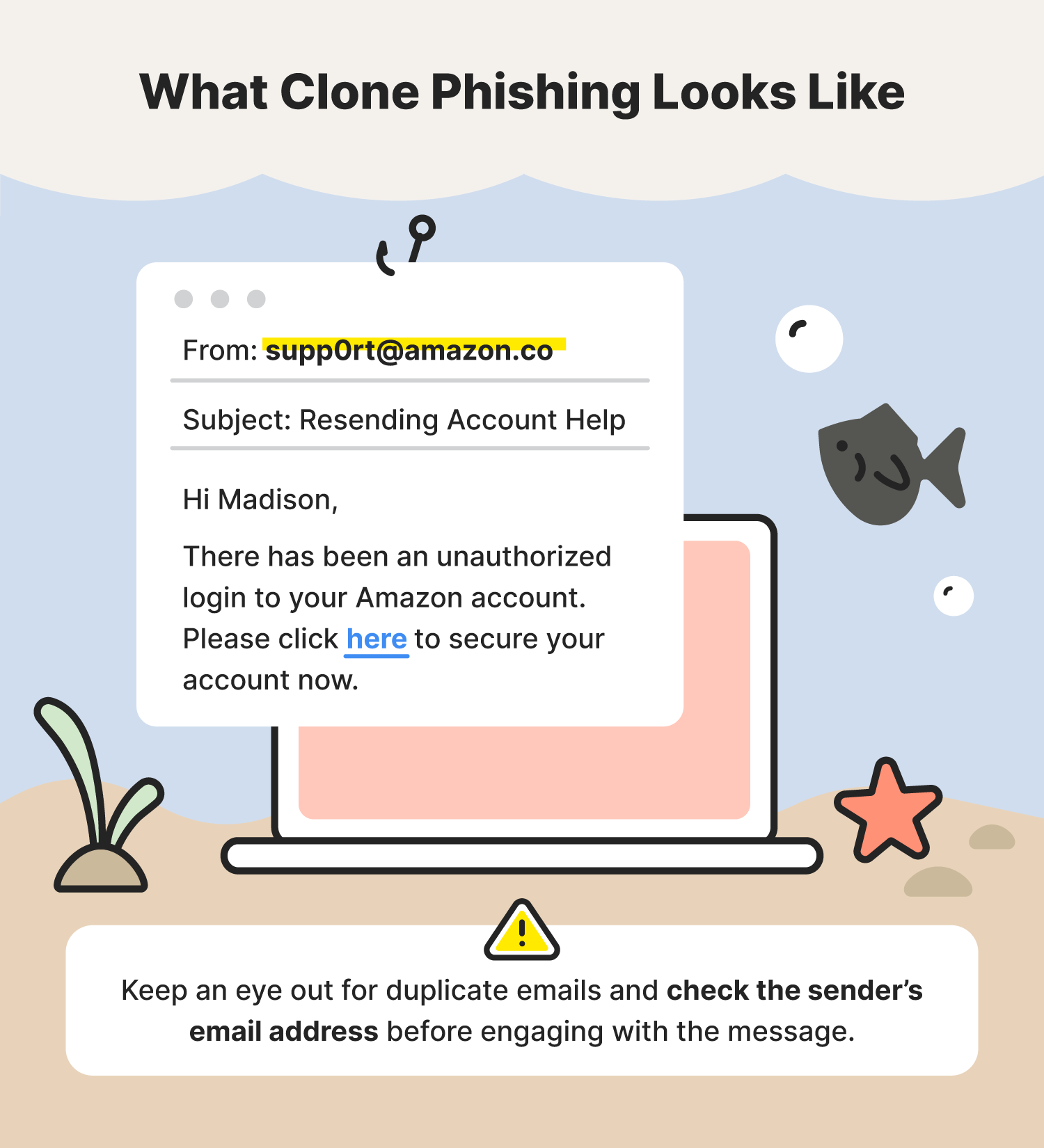
A clone phishing attack is when a scammer attempts to replicate a legitimate branded email you may have already received while sneaking in a malicious link or attachment. In some cases, the cloned email may contain something like “resending” or “sending this again” to make you think that it is from the original sender.
An example of clone phishing is receiving an email twice, but with one of them coming from a slightly different email address. For example, you receive two identical emails, one from “support@amazon.com” and the other from “supp0rt@amazon.co.”
- Clone phishing prevention tip: Keep an eye out for duplicate emails and check the sender’s email address before engaging with the message.
7. Vishing
Vishing is a type of phishing in which a scammer uses social engineering tactics to get you to give up valuable information over the phone. During these calls, the scammer may pretend to be a trusted source such as the Internal Revenue Service (IRS), your doctor, or your bank.
An example of this would be a random call from your credit card company claiming your account has been compromised. To secure your account, the scammer will ask you for your personal information.
- Vishing prevention tip: If you ever receive a suspicious call, hang up before giving away any information. To confirm the caller’s identity, you can search for the company’s official phone number and call it yourself.
8. Pharming
Pharming is a phishing method that utilizes malicious code and software to steal your information. Once the malicious code is in place, your web traffic may be directed to fake and malicious websites without your knowledge or approval, leading you to unknowingly expose private information to hackers.
An example of a pharming attack would be if your web traffic is being rerouted to unsecure websites with URLs that begin with “HTTP” rather than “HTTPS,” or you receive a “your connection is not private” error. Another example of pharming is if websites you've visited before begin to look suspicious, often with different fonts or spelling errors.
- Pharming prevention tip: Avoid visiting unsecure “HTTP” websites.
9. Watering hole phishing
Watering hole phishing is a targeted phishing attack in which a cybercriminal compromises a website that is used by a specific group of people. In these attacks, the hacker is trying to infect the targeted users’ devices with malware to gain access to private information.
For instance, a cybercriminal may seek out a security flaw in a website that a group of employees consistently use. Once the cybercriminal compromises the website, they can steal the information of anyone who visits the website, allowing them to sit and wait for users to fall into the trap.
- Watering hole phishing prevention tip: Install antivirus software to provide an added layer of security when browsing the web.
10. Whaling
A whaling attack is when a phisher impersonates a top executive at a company hoping to steal money or private information from another high-level executive at the same company. This is also known as “executive phishing.”
For example, a high-level executive at your company might reach out about a financial crisis that they need your help with. To solve this problem, the phisher may ask for login information or a wire transfer of funds. This is a common example of a whaling attack.
- Whaling prevention tip: If you receive a suspicious email from a coworker, reach out to them directly to confirm its legitimacy.
11. Pop-up phishing

Pop-up phishing is a type of attack that leverages adware and pop-up ads to trick users into downloading malware onto their devices. Common characteristics of these attacks include fake virus alerts and scare tactics to get you to click without thinking.
An example of pop-up phishing is if you’re browsing the web and are bombarded by a pop-up informing you that your device has been infected by a virus. The pop-up also states that you can remove the virus by inputting your information and downloading an antivirus program. While it might be tempting to follow the instructions, this is likely fake antivirus software designed to steal your information.
- Pop-up phishing prevention tip: Enable a pop-up blocker and avoid clicking on any pop-up windows you encounter online.
12. Deceptive phishing
Deceptive phishing is a type of phishing that uses deceptive technology such as email spoofing to send messages that appear to be from an address other than their own. Like other types of phishing emails, these messages may contain malicious links or attachments.
This can be a phishing email that appears to be coming from a trusted company. For example, you may receive an email from “support@apple.com,” claiming they need your login information to fix an issue with your account. Even though it may seem legitimate, it could still be a scam.
- Deceptive phishing prevention tip: Always think twice before clicking links and attachments, even if the sender appears to be legitimate. Instead, you can access the website directly using a trusted URL, rather than using the link in the email.
13. Evil twin phishing
Evil twin phishing is a cyberattack designed to steal your information using a fake Wi-Fi network. If you join a cybercriminal’s malicious network, they can monitor your web traffic and capture any login credentials you use while connected.
An example of this would be joining a fake Wi-Fi hotspot that is impersonating a public Wi-Fi connection. For example, you may think you’re joining a local coffee shop’s network when in reality you’re joining the network of a hacker. Once you’ve connected, the attacker can see everything you do using their router.
- Evil twin phishing prevention tip: Use extreme caution when connecting to any Wi-Fi connection other than your own. For increased security, use a VPN.
14. Search engine phishing
Search engine phishing attacks attract users using fake product pages. When a potential customer is searching for a product online, they may come across one of the hacker’s counterfeit pages using a search engine. The catch is that instead of being able to purchase the product, they’re handing over their payment information to a scammer.
For instance, a search engine phishing scam may be a fake website offering to sell designer sunglasses for a fraction of the cost. While the offer may seem too good to refuse, it’s best to avoid these sites, as they are usually scams.
- Search engine phishing prevention tip: Avoid giving your payment information to websites other than trusted and reputable online vendors.
15. Image phishing
Image phishing is an attack in which hackers disguise malicious code or different types of malware using image files. These images may be included in the body of an email or linked as an attachment. If you click on the image, you may accidentally be putting your cybersecurity at risk.
Image phishing emails include images and attachments that may be tempting to open. Once you click on the image, your computer will begin downloading the malicious code stored within the image.
- Image phishing prevention tip: Never click on or download an image from a suspicious email message.
16. Website spoofing
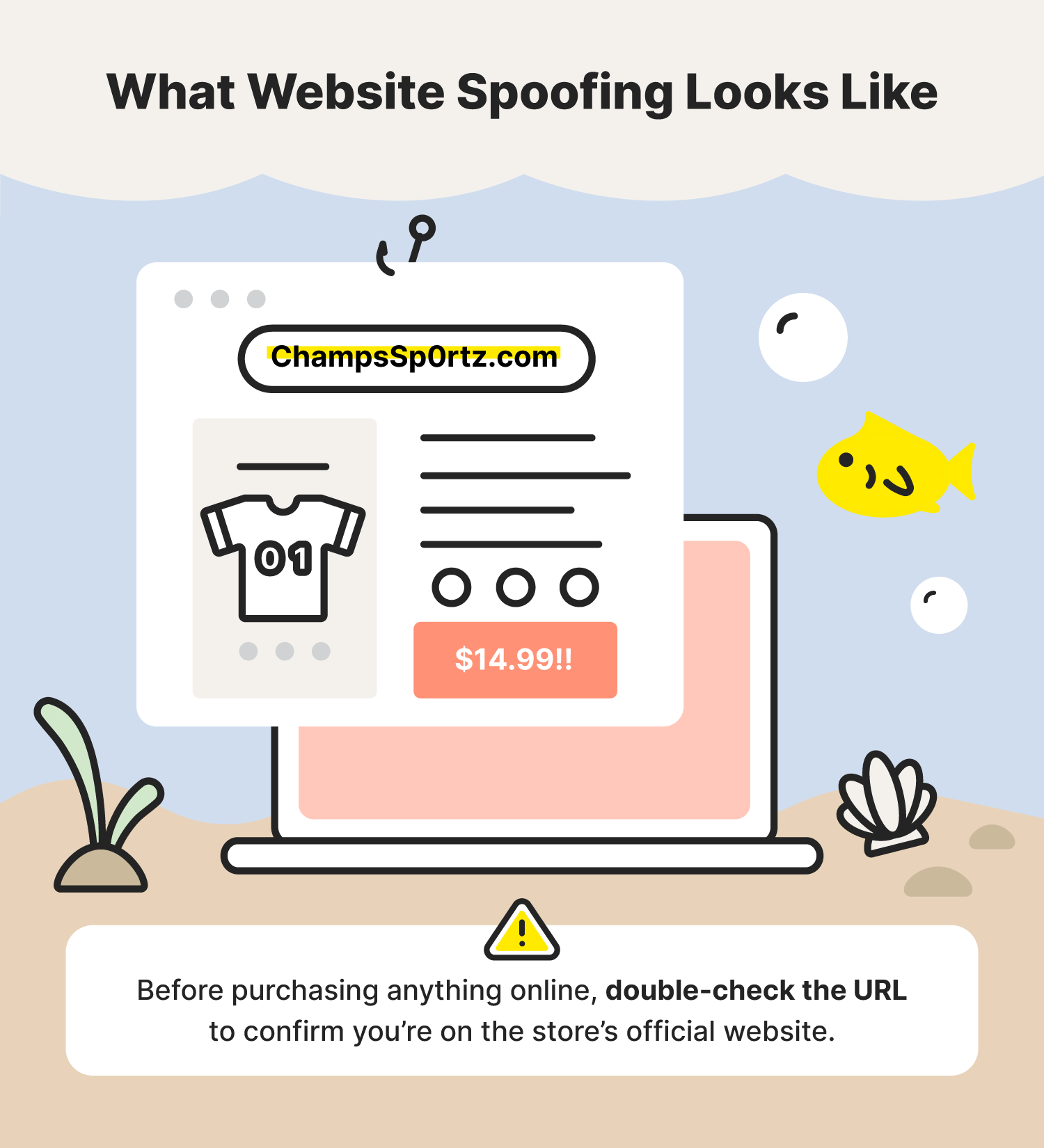
Most phishing attacks try to get you to share your private information, and website spoofing is no exception. Website spoofing is a type of cyberattack that relies on fraudulent websites. If you end up on one of these sites, you could lose your identity or damage your device.
Let’s say you’re looking to buy a basketball jersey online. After searching around, you finally find the one you want. While going through the checkout process, you notice that the website seems a little off. Even though it has the branding of a well-known store, you see some blurry images and grammatical errors. This is an example of a spoofed site.
- Website spoofing prevention tip: Before purchasing anything online, double-check the URL to confirm you’re on the store’s official website.
17. Smishing
Smishing is the word that describes phishing over short message services (SMS). Similar to phishing emails, these phishing text messages usually use social engineering tactics and contain malicious links.
An example of this is receiving a text message from a random number informing you that you’ve won a contest or gift card. In these smishing scams, a cybercriminal will send you a link you can click to “claim your prize.” While a free gift may sound enticing, this is only an attempt to get you onto their fraudulent site.
- Smishing prevention tip: Avoid opening links from unknown phone numbers.
18. Domain spoofing
Domain spoofing is a type of phishing attack in which the attacker impersonates a known person or company using a fake email domain. This phishing technique can be very effective, as the email will appear as if it is coming from a legitimate source.
For example, you may receive an email from “support@vvix.com.” At first glance, this email address seems like it is a trustworthy address. However, after inspecting further, you’ll notice the letter W is actually made up of two V’s.
- Domain spoofing prevention tip: Copy the sender’s email address and compare it to the official email address listed on the company’s site.
19. Man-in-the-middle (MITM) attacks
A man-in-the-middle (MITM) attack is an attack in which a hacker steals your information by getting in between you and a trusted party. If successful, the hacker may be able to gain access to your internet traffic and personal information.
Cookie theft is one example of a MITM attack. In this type of attack, a hacker will spy on users of unsecure public Wi-Fi networks. Then, the hacker will attempt to hijack your internet session and get access to your cookies. Once they have your cookies, they can access any account you’re currently logged into.
- MITM attack prevention tip: Always use a VPN when connecting to public Wi-Fi networks.
20. Social media phishing
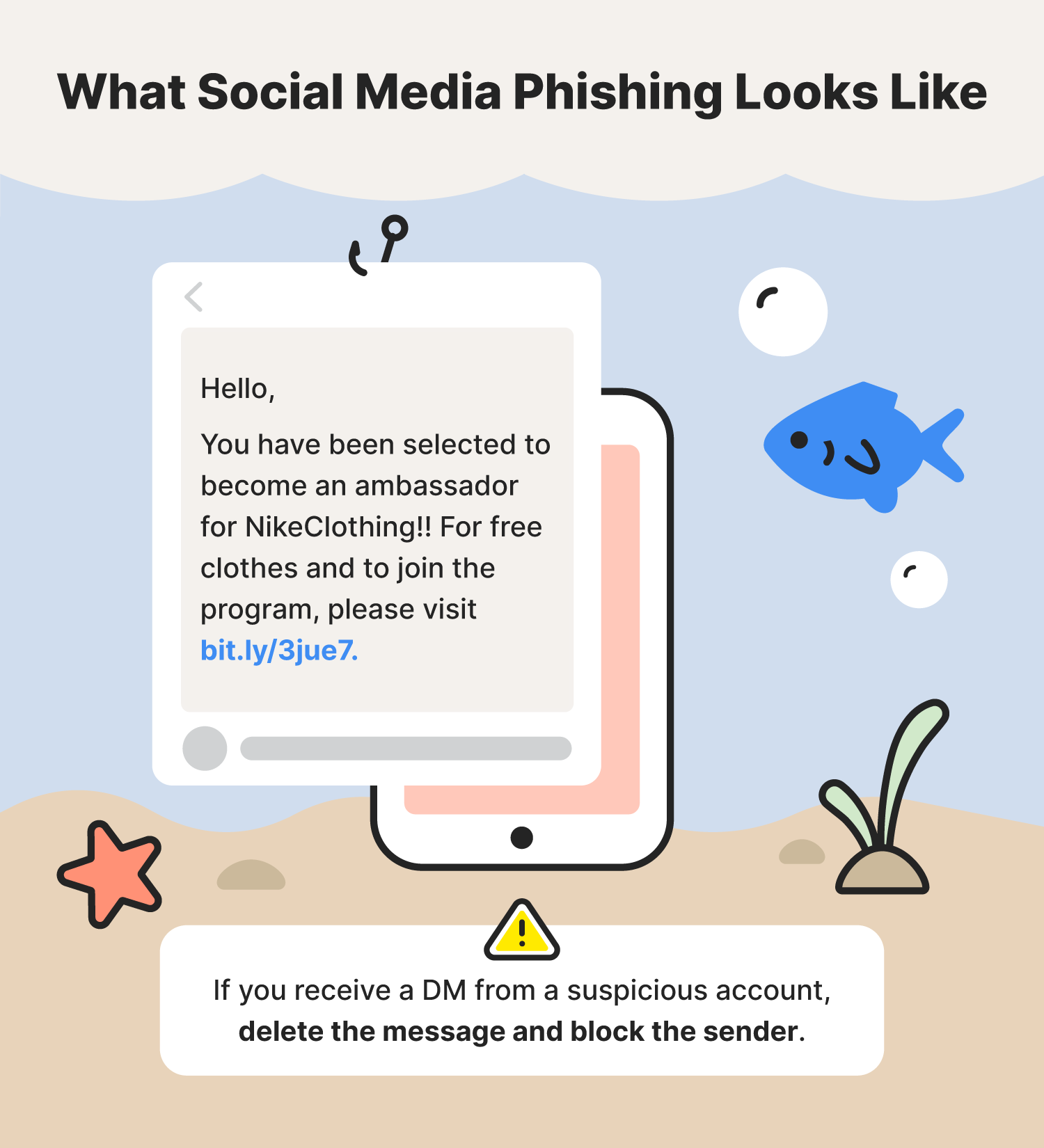
Social media phishing is a popular social media threat that takes place on platforms like Facebook, Instagram, Twitter, LinkedIn, and more. Similar to receiving a phishing email in your inbox, you may receive phishing messages in your direct messaging (DM) inbox.
Picture this: You're scrolling through Instagram and receive a DM from an account that appears to be one of your favorite clothing brands. In the DM, you're asked to be an ambassador for their brand in exchange for product discounts. To sign up, all you need to do is follow the link to their website. Upon further inspection, you notice that the message contains typos and the account isn’t verified. This is a classic example of a social media phishing scam.
- Social media phishing prevention tip: If you receive a DM from a suspicious account, delete the message and block the sender.
Pointers for how to prevent phishing attacks
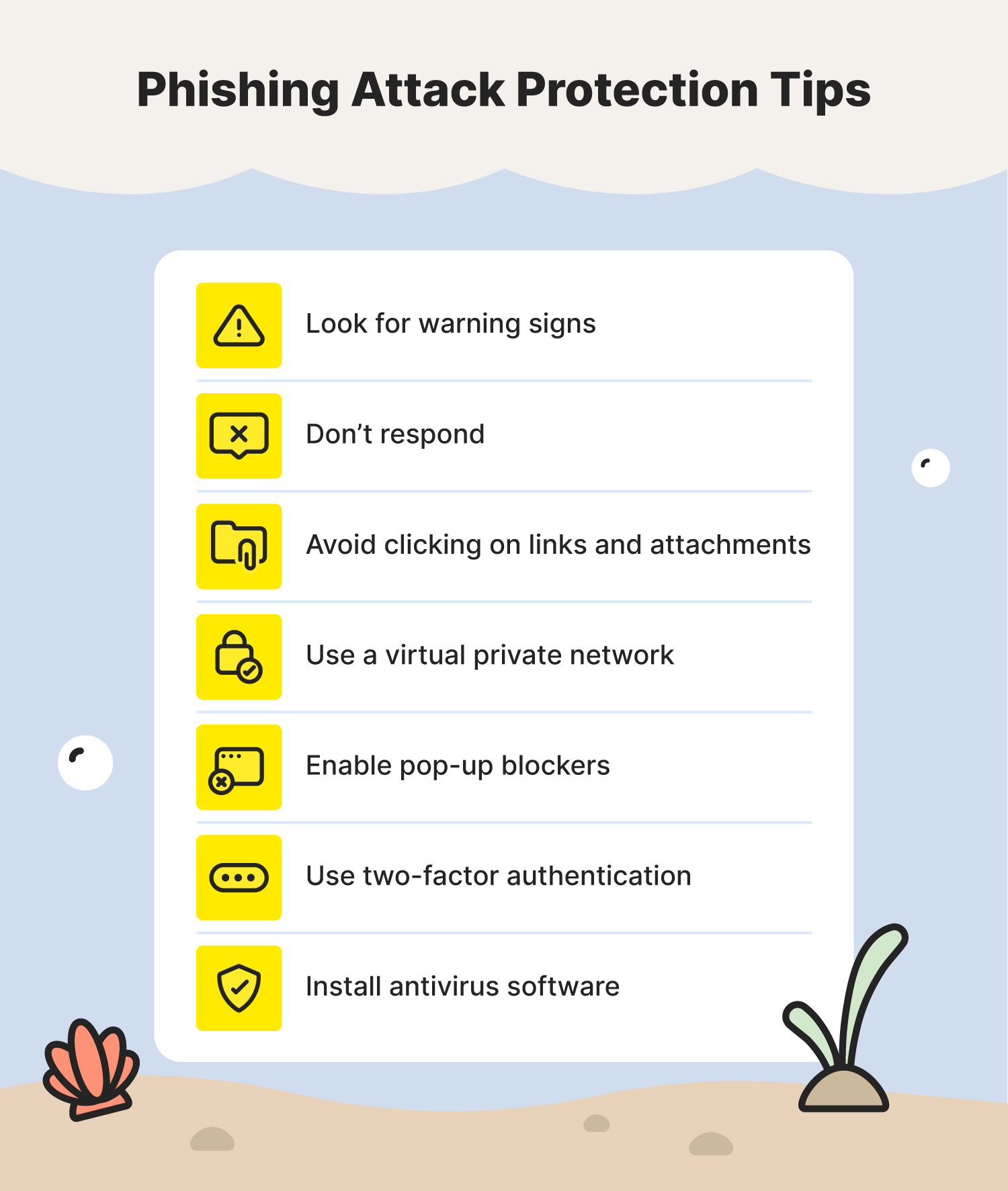
With a variety of different phishing examples to be aware of, you may be wondering if there is anything you can do to protect against phishing scams. While you might not be able to stop every phishing attempt, you can reduce the amount by following these steps.
- Look for warning signs: Common red flags of a phishing scam include unsolicited messages, spelling errors, a sense of urgency, requests for personal information, and suspicious links and attachments.
- Don’t respond: One of the safest responses to a phishing attack is no response at all. Even if you don’t give the scammer the information they want, responding will only let them know that they’ve found an active email address, encouraging them to try again in the future.
- Avoid clicking on links and attachments: When dealing with a message from an unknown sender, it’s best to avoid opening any links and attachments, because you could end up on an unsafe website or expose your device to malware.
- Use a virtual private network (VPN): Certain phishing attacks use unsecure public Wi-Fi networks to gain access to your private information. To help protect yourself, use a VPN.
- Enable pop-up blockers: Using pop-up blockers is a great way to protect yourself from accidentally clicking on something designed to steal your information.
- Use two-factor authentication (2FA): Enabling 2FA on your online accounts gives you a second layer of protection from phishing scams. That way, even if a phishing attack ends with your passwords exposed, scammers won’t be able to log into your account, giving you additional time to reset your passwords.
- Install antivirus software: As an additional precaution, installing trusted antivirus software can help protect your device from all sorts of cyberattacks, including phishing.
Now that you know about the different types of phishing, you can surf the web with confidence and avoid phishing campaigns with ease. To ensure you’re also protected from other cyberthreats, be sure to always use common sense and brush up on good password security.
FAQs about different types of phishing
Below you will find answers to some popular questions surrounding different types of phishing attacks.
What is group phishing?
Group phishing is a phishing attack that targets a specific group of people, such as a group of employees at a company.
What type of phishing attack targets particular individuals?
Spear phishing is a hyper-targeted form of phishing used to gain someone’s personal information by posing as a trusted acquaintance.
What type of phishing attack targets groups?
Watering hole phishing is a phishing tactic used to target a specific group of people that use the same website. In many cases, the phisher will try to compromise a trusted website and infect the users’ devices with malware.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
- 1. Spear phishing
- 2. HTTPS phishing
- 3. Email phishing
- 4. Social engineering
- 5. Angler phishing
- 6. Clone phishing
- 7. Vishing
- 8. Pharming
- 9. Watering hole phishing
- 10. Whaling
- 11. Pop-up phishing
- 12. Deceptive phishing
- 13. Evil twin phishing
- 14. Search engine phishing
- 15. Image phishing
- 16. Website spoofing
- 17. Smishing
- 18. Domain spoofing
- 19. Man-in-the-middle (MITM) attacks
- 20. Social media phishing
- Pointers for how to prevent phishing attacks
- FAQs about different types of phishing




Want more?
Follow us for all the latest news, tips, and updates.