15 infamous hacker groups to look for [1981 to 2024]
Hacking groups can be a major threat to your business and are widely active on the web today. Learn about the top 15 hacker groups to watch for in this guide.

A hacker group is a team of decentralized and skilled cybercriminals who work to infiltrate and exploit networks to make a profit, make a statement, or just cause mayhem. Some even aim to do good by exposing security flaws and teaching others how to fix them. These hacker groups can be categorized into different types of hackers, such as:
- Black hat: These are stereotypical cybercriminals who work to break into personal networks and devices to steal sensitive data for profit.
- White hat: These hackers break into systems to detect security flaws so that entities like businesses and governments can address them.
- Gray hat: These individuals belong to groups whose main purpose is to hack for fun or entertainment.
Throughout the years, several hacker groups have managed to compromise the security of some of the biggest companies and brands, such as Microsoft, Apple, and even whole governments and healthcare systems, with devastating effects.
Read more to learn about the most famous hacker groups organized by origin date, their objectives, and notable attacks, as well as tips to protect yourself from cybercrime.
1. Chaos Computer Club
Type of hacker: White hat
- Stated objective: Provide education surrounding data privacy, freedom of information, hacktivism, surveillance, and technical and societal issues
- Alleged region of origin: Germany
- Perceived years active: 1981 to present
- Notable attack(s): German Bildschirmtext (BTX)
Originating in Europe in 1981, the Chaos Computer Club (CCC) is one of the oldest and largest hacking groups in the world with over 7,000 members. It’s a group of white hat hackers that focuses on exposing governmental security flaws and spreading education about computer network security. They also advocate for government transparency, the human right to communication, and freedom of information.
The group made headlines when its members hacked the German Bildschirmtext (BTX) in 1984. The BTX was an online videotex system that was launched in 1983. During the hack, members of the CCC were able to transfer 134,000 German Marks into their bank accounts. After catching the attention of the press, the hackers returned the funds. This attack was carried out as a statement to prove that the system was at risk for potentially more threatening hackers.
2. Legion of Doom
Type of hacker: White hat
- Stated objective: Spreading knowledge about hacking
- Alleged region of origin: United States
- Perceived years active: 1984 to early 2000s
- Notable attack(s): The war with the Masters of Deception hacker group
The Legion of Doom was an American white hat hacker group credited for publishing its hacking knowledge in several pieces of content, the most notable being the Hacker Manifesto. This essay highlighted the goals and ethics of hackers from all over the world.
This group was the most active between 1984 and the early 2000s and is also noted for its conflict with another hacker group, Masters of Deception. Known as the Great Hacker War, these two groups worked to attack each other’s networks. The conflict ultimately led to the temporary shutdown of AT&T and the disbanding of both groups.
3. Lazarus Group
- Type of hacker: Black hat
- Stated objective: Conduct cyber operations including cyber-enabled finance crime and espionage
- Alleged region of origin: North Korea
- Perceived years active: 1998 to present
- Notable attack(s): Sony Pictures, the WannaCry ransomware attack
Lazarus Group is a famous hacker group that was created in North Korea in 1998 and is still active today. The group considers itself a cyber warfare agency that’s part of the Reconnaissance General Bureau within North Korea’s military. Lazarus Group’s main goal is to conduct cyber operations, with its main targets being South Korea and the United States.
The actions of Lazarus Group came to the surface after they hacked Sony Pictures following the release of the film “The Interview” in 2014. The attack leaked personal emails and information, which cost Sony $15 million to repair. However, the group’s most famous attack was the WannaCry ransomware attack, which infected over 200,000 computers operating Microsoft Windows and resulted in $4 billion in damage.
4. Tailored Access Operations (TAO)
- Type of hacker: Black hat
- Stated objective: Gather intelligence by computer network exploitation from foreign entities
- Alleged region of origin: United States
- Perceived years active: 1998 to present
- Notable attack(s): Snowden leak
Tailored Access Operations, also known as TAO, is a cyber warfare unit of the United States National Security Agency (NSA) known for having its files leaked by Edward Snowden, a former NSA contractor. TAO hacker group’s main purpose is to gather intelligence on foreign entities by exploiting software and hardware.
According to the leaked files from Snowden, the hacker group uses software templates to break into popular hardware, such as switches, firewalls, and routers from product vendor lines.
5. Dragonfly
- Type of hacker: Black hat
- Stated objective: Infiltrate third-party organizations
- Alleged region of origin: Russia
- Perceived years active: 2010 to present
- Notable attack(s): Ukraine power companies
Dragonfly is a cyber espionage group that is attributed to Russia’s Federal Security Service (FSB). They’re also known as Crouching Yeti, Iron Liberty, and Berserk Bear. Since 2010, this group has been known to hack infrastructure entities in North America and Europe and target aviation and defense companies. It carries out attacks through spear phishing and drive-by compromise attacks on third-party organizations that have lower levels of network security.
Although they’re known for carrying out these types of attacks, authorities have been unable to officially trace a specific attack back to the group. Allegedly, the group is responsible for conducting a DDoS attack by infecting multiple power companies in Ukraine with the BlackEnergy trojan, resulting in a blackout for thousands of citizens.
6. LulzSec
- Type of hacker: Gray hat
- Stated objective: Expose security flaws of high-profile companies for entertainment purposes
- Alleged region of origin: United States
- Perceived years active: 2011
- Notable attack(s): The hacking of Fox News, PlayStation Network, and the U.S. Senate
LulzSec, also called Lulz Security, is a gray hat group that hacks the day-to-day operations of high-profile companies and organizations. According to the group, its mottos are: “The world’s leaders in high-quality entertainment at your expense” and “Laughing at your security since 2011.”
The group gained attention after they hacked the websites of Fox News, Sony Pictures, PlayStation, and the CIA. All the hacks were carried out through DDoS attacks. These malicious activities even caught the attention of law enforcement — Hector Monsegur, one of the group's members, helped the authorities catch some of the other members.
7. Morpho
- Type of hacker: Black hat
- Stated objective: Gain access to high-level corporate data
- Alleged region of origin: Unknown
- Perceived years active: 2011 to present
- Notable attack(s): The Microsoft, Apple, Twitter, and Facebook breaches in 2013
Morpho is a hacker group focused on cyber espionage, and is also called Wild Neutron, Sphinx Moth, and Butterfly. This group usually performs financially motivated attacks, and has affected and stolen confidential information from high-profile companies such as Twitter, Apple, Facebook, and Microsoft. To hack these organizations, the group utilized zero-day vulnerabilities.
Although its motivations are clear, the group’s origins remain unknown and they’ve made themselves nearly impossible to track. However, it’s said that they may be of English-speaking origin because the code is entirely composed of English and their encryption keys are named after memes in American pop culture.
9. Lizard Squad
- Type of hacker: Black hat
- Stated objective: Target entertainment and video game servers via DDoS attacks
- Alleged region of origin: North Korea
- Perceived years active: 2014 to 2015
- Notable attack(s): PlayStation, Xbox, Malaysia Airlines, Facebook
Lizard Squad is a North Korean hacker group that carries out DDoS attacks. They’re known for hacking Facebook and Malaysia Airlines, as well as gaming giants such as PlayStation Networks and Xbox Live. They also take credit for shutting down the internet in North Korea in 2014.
It’s also alleged that Lizard Squad imposed bomb threats against Sony Pictures’ CEO and leaked explicit photos of celebrities. Fortunately, their attacks only lasted from 2014 to 2015 after key members of the group were arrested by authorities.
10. Conti
Type of hacker: Black hat
Stated objective: Gain access to the victim’s network and encrypt important services or files
Alleged region of origin: Russia
Perceived years active: 2018 to 2022
Notable attack(s): Irish health care system, the Costa Rican government
Conti, also known as Ryuk, is a ransomware as a service (RaaS) black hat hacker group that originated in Russia in 2018. This group sought to target institutions ranging from financial services, education, technology, and health care. Over the years, Conti has affected over 400 targets across France, the United Kingdom, and the U.S.
One of their most infamous attacks was the hack on Ireland’s Health Service Executive (HSE) in 2021, causing the HSE’s IT systems to shut down, which resulted in limited access to important diagnostic and medical records. Conti asked for a ransom of nearly $20 million.
11. LockBit
- Type of hacker: Black hat
- Stated objective: Block user access to computer systems in exchange for a ransom payment
- Alleged region of origin: Russia
- Perceived years active: 2019 to present
- Notable attack(s): The Center Hospitalier Sud Francilien attack
LockBit is an RaaS hacker group from Russia that blocks user access to computer systems in exchange for payment. Since 2019, LockBit has averaged around 70 victims a month and has been responsible for 46% of all RaaS breaches in the first quarter of 2022. The group has also been tied to over 40 attacks in June 2022 alone.
An example of LockBit’s attacks includes the $10 million ransom they demanded from Paris’ Center Hospitalier Sud Francilien after they infiltrated the hospital’s business software. As a result of the attack, the hospital was unable to use several medical systems.
12. REvil
- Type of hacker: Black hat
- Stated objective: Gain access to high-level organizations and encrypt their files
- Alleged region of origin: Russia
- Perceived years active: 2019 to present
- Notable attack(s): The Kaseya attack
REvil is another famous black hat hacker group in the RaaS playing field. Originating in Russia in 2019, this group encrypts files and information and hacks into systems, demanding a ransom payment in exchange for information. REvil’s most active year was 2021 — it accounted for 37% of ransomware attacks in 2021 according to IBM Security.
However, its most notable attack was the attack on Kaseya, an IT service provider. This attack was an automatic software update with REvil’s ransomware that affected over a million customers of Kaseya’s managed service providers (MSPs). The attack had a $70 million ransom to fix affected systems.
Other REvil attacks include stealing Apple’s schematics for upcoming products, leaking 2.4 GB of data from Lady Gaga, and publishing HX5 documents related to the U.S. Air Force, Navy, and Army.
13. DarkSide
- Type of hacker: Black hat
- Stated objective: Target victims via ransomware and extortion
- Alleged region of origin: Eastern Europe
- Perceived years active: 2020 to present
- Notable attack(s): Colonial Pipeline attack of 2021
DarkSide is a newer Eastern European RaaS hacker that is perceived as one of the world’s most dangerous hacking groups. This group is known for targeting high-profile corporations worldwide with stolen credentials and manual jacking with testing tools.
DarkSide became a major player in cybersecurity attacks with the Colonial Pipeline attack in 2021. The attack was responsible for the partial shutdown of the network that supplies 45% of the gasoline for the U.S. East Coast. This resulted in widespread panic-purchasing in the gasoline industry and a 75 million Bitcoin (about $5 million) ransom paid by the Colonial Pipeline Company.
14. Hafnium
- Type of hacker: Black hat
- Stated objective: Exploit vulnerabilities in American internet-facing servers
- Alleged region of origin: China
- Perceived years active: 2021 to present
- Notable attack(s): The Microsoft Exchange Server data breach
Hafnium is a cyber espionage hacker group that originated in 2021 allegedly from the Chinese government. This group is known to mainly target American internet-facing servers across a variety of industries, including higher education, defense contractors, infectious disease researchers, and law firms.
Hafnium’s most notable attack (although denied by Hafnium) is the data breach of the Microsoft Exchange Server in 2021. This attack utilized a zero-day exploit that affected the email servers of over 60,000 organizations, including the European Banking Authority.
15. Lapsus$
- Type of hacker: Black hat
- Stated objective: Pursue extortion against government agencies and companies via social engineering tactics
- Alleged region of origin: England
- Perceived years active: 2021 to present
- Notable attack(s): The attack of the Brazilian Ministry of Health, Cisco, Samsung, Microsoft, Okta, and Nvidia
Lapsus$ is another famous hacker group that is data extortion-focused, pursuing attacks against companies and government agencies with social engineering tactics by gaining access to sensitive information and employee credentials.
Lapsus$ is unique because they use Telegram, a messaging app, to recruit additional group members from the public, and will use the channel to post stolen information. They first made headlines after their attack on the Brazilian Ministry of Health, which compromised the COVID-19 vaccination data of millions of people. Since then, the group has targeted additional victims, such as Microsoft, Samsung, Uber, Rockstar Games, Cisco, and Nvidia.
How to protect yourself from hacker groups: 9 tips
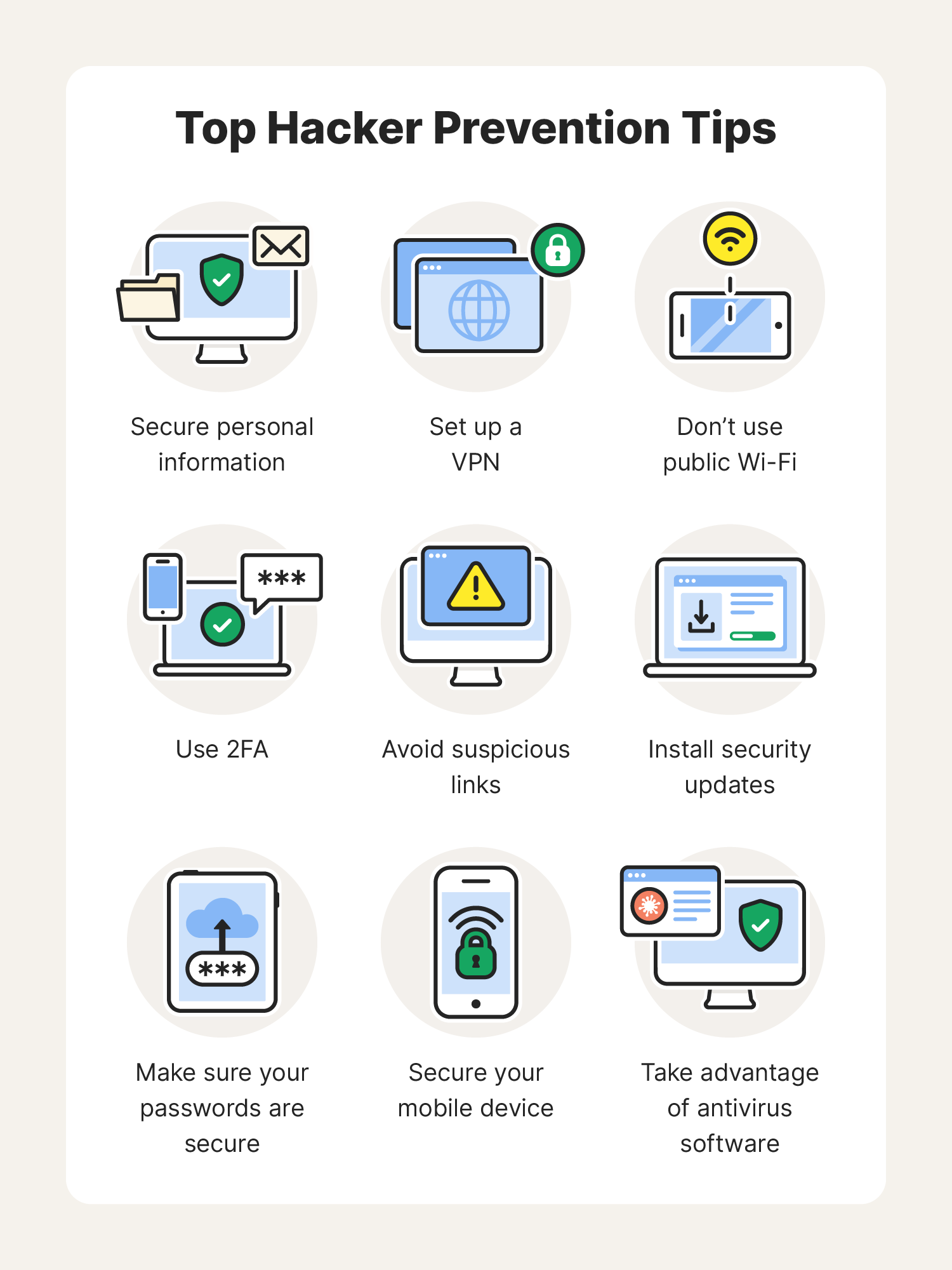
After learning about these famous hacker groups, it’s safe to say you may feel like your own security can be improved or that you’re in need of some ways to protect your personal information and devices. Here are nine tips to help protect you and your organization from hacker groups:
- Secure your personal information: Avoid including personal information such as phone numbers and addresses on online platforms. If you have to send sensitive information, make sure you know who is on the receiving end.
- Set up a VPN: A VPN can keep your online activity encrypted, which ensures your sensitive information is harder to access.
- Don’t use public Wi-Fi: Some hackers use unprotected and public Wi-Fi to spread malware, so make it a habit to use secure or private internet connections.
- Use two-factor authentication: Two-factor authentication (2FA) creates another layer of protection around your passwords. This technology usually includes features such as facial and fingerprint recognition.
- Avoid suspicious links: Be wary of links that look suspicious — hackers can spread malware through them, especially via email. Avoid downloadable files or attachments from unknown senders.
- Install security updates: Make sure your devices are up to date with the latest security updates to ensure further protection.
- Make sure your passwords are secure: Create strong passwords by using a combination of letters, symbols, and numbers, or take advantage of password managers that can create secure passwords.
- Secure your mobile device: Make your mobile devices secure by setting security PINs, only downloading apps from official app stores, and updating your operating system.
- Take advantage of antivirus software: Antivirus software can provide 24/7 protection against emerging threats and hackers.
Although there are many dangerous hacker groups to watch out for, businesses and organizations have learned many valuable lessons from their attacks. Threats can come at any time, and it’s important that your organization is prepared. To ensure your data is protected, consider investing in strong cybersecurity and antivirus software like Norton AntiVirus Plus to help keep your mind at ease.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.