5 Types of phishing emails to watch out for
If you spot one of these in your email, it could be a scam. Keep an eye out for these red flags in your inbox.

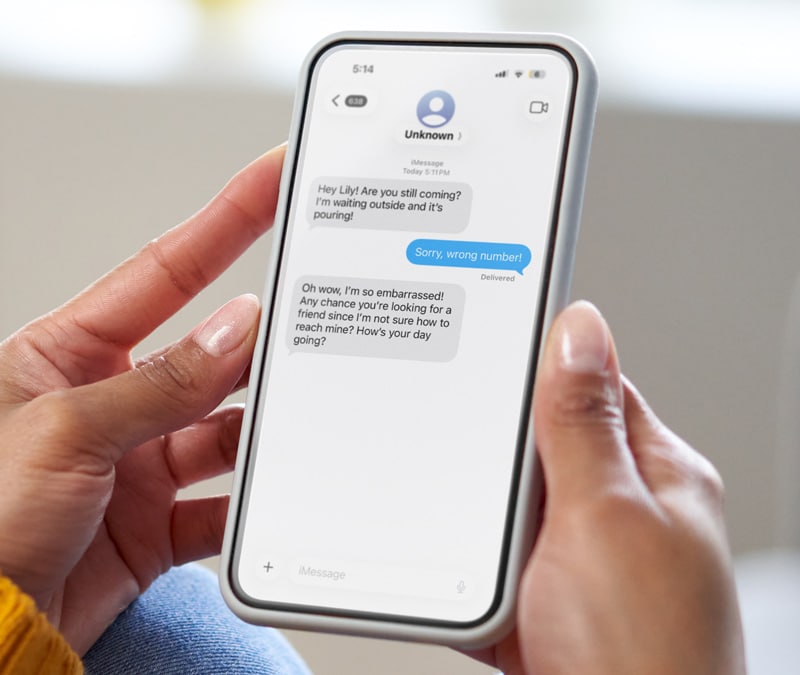
Maybe you’ve been here? You’re hanging out with friends on a Friday night. Or, relaxing on the couch, catching up with your shows. Maybe you’re right in the middle of a meeting at work, and it happens:
You get an email that makes you stop and wonder if it’s real ... or fake.
We’ve got some tips to help you spot when an email is true—and when it’s just playing you.
Offers you student loan forgiveness, but wants an application fee? 🚩
A rash of scam emails masquerading as part of the U.S. Student Loan Debt Relief program are making the rounds. These emails make promises like accelerated processing and a quick turnaround for getting your money back. Then, they lure you into responding with personal information or link to a fake website that prompts you to enter your Social Security number and other information. To add insult to injury, they ask you to pay a processing fee.
This is an easy one to spot, because any emails that you receive about the U.S. Student Loan program should lead you to https://studentaid.gov and nowhere else. If you are eligible for relief, there are no shortcuts, and applying for relief is free.
Claims they work for the IRS, but email you from their personal account? 🚩
In this phishing scam, you’ll get an email from the IRS, an online retailer, your bank, or any number of other businesses asking you to log in or respond with information. Sometimes they ask for sensitive information right away. Other times it might be the first step in setting you up for a longer scam. In any case, when you look at the return email address, you notice it’s an email address that has nothing to do with the company they’re representing.
If such an email is convincing enough to make you wonder, check the return address and avoid things like misspellings of websites, names that have an excess of numbers or gibberish, and email domains that are suspect. Most business emails ask you to visit their website, sent from email addresses that start with “no-reply@.” Also, the IRS does not initiate contact via email.
Has a package for you, but doesn’t know where you live? 🚩
In this ploy, you’ll get an email or a text that looks like it’s from a reputable shipping service. In fact, it’s from a hacker. The email may ask you to log in to a fake website or call them so they can collect your personal information. They might also pressure you to make an additional delivery payment, or they’ll send the item back. The scammer is hoping you’ll forget whether you ordered anything, and you’ll comply so that you’ll get your item … that you never ordered … and isn’t real.
If you get an email or a text message that doesn’t have detailed information about the shipping company and tracking information, it’s likely a scam. Any legitimate shipping message will give you information so that you can independently go to the shipper’s website (don’t use links provided in the email), enter the tracking information, and find out if you really have something coming.
Remotely detects that your computer has a virus, and wants remote access to fix it? 🚩
Bad actors often initiate this scam with a fake email subject like “Your machine has been hacked,” but it can also come from text messages, cold calls, and pop-ups on malicious websites. The message urges you to call a support line, which is actually a number that connects you to the scammer directly. They’ll then talk you through installing a remote-access program that lets them take control of your computer and gives them access to all of your personal data.
Operating systems like Microsoft, Apple, iOS, and Android do not email you if you have a virus. The best way to know if your device has been infected by a virus is to have antivirus software installed. You should never call a phone number from a vague email that simply says your computer is infected, and never allow anyone over the phone to talk you through installing remote-access software.
Says you owe them money, or they owe you money … wants you to open a PDF to know more? 🚩
Another method of infecting your device with malware the malicious PDF file download. Scammers will mask this threat by pretending to be a collector for a bank or business with whom you have an account. Or, they might tell you you’ve got a refund or a prize coming your way. All you have to do to fix things is to open the attached PDF file.
Never trust a PDF file that’s been emailed from someone you don’t know directly, and practice healthy skepticism if someone you know emails you with a PDF out of the blue (their account could be compromised).
Hackers, scammers, and threat actors use sophisticated and technical tools as well as psychological tactics to steal your personal information. The flags we list here should equip you with good information to differentiate between legitimate emails and phishing schemes. If you need a little help, check out Genie, one of the world’s first AI-powered scam detection tools that will scan and review text messages, emails, websites, and social posts. You’ll get instant advice on whether the message or site is potentially a scam.
But these tools are is only a step toward prevention—always report suspected scam emails to your email service or your IT administrator. Keep developing your healthy skepticism, and use antivirus software to help keep your digital devices safe. Stay informed, stay cautious, and continue to build up your defense against phishing attacks.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
- Offers you student loan forgiveness, but wants an application fee? 🚩
- Claims they work for the IRS, but email you from their personal account? 🚩
- Has a package for you, but doesn’t know where you live? 🚩
- Remotely detects that your computer has a virus, and wants remote access to fix it? 🚩
- Says you owe them money, or they owe you money … wants you to open a PDF to know more? 🚩




Want more?
Follow us for all the latest news, tips, and updates.