RFID blocking: What it is, how it works, and why you may need it
RFID blocking protects against unauthorized scanning of contactless cards. But what exactly is RFID blocking, and how does it work? Keep reading to learn about RFID protection, and discover how Norton 360 with LifeLock can help secure your data and protect your finances if your card details or other sensitive information are stolen.

RFID stands for radio-frequency identification — a wireless technology used to verify contactless payment cards, passports, and key fobs via embedded tags and readers.
While convenient, RFID is also susceptible to exploitation by cybercriminals who can use unauthorized RFID readers to secretly scan and capture data from RFID-enabled cards.
That’s why many people choose to use RFID-blocking wallets and other products to help prevent skimmers from remotely hacking their credit cards to make fraudulent payments or commit identity theft.
What is RFID blocking?
RFID blocking is the use of materials such as metal or specialized fabrics in wallets, bags, or other products, to disrupt radio waves used by RFID readers, preventing them from accessing the embedded chips in credit cards, passports, or key fobs.
By shielding RFID-enabled items in this manner, you can help protect yourself against RFID skimming — a form of electronic pickpocketing used by thieves to make bogus charges to your card, “clone” your key fob, or steal sensitive data, simply by walking close by with a hidden RFID scanner.

How does RFID blocking work?
RFID blocking works by using materials that interfere with electromagnetic fields to cover your contactless card, tag, or passport. This prevents radio waves transmitted by RFID scanners from reaching them — and vice versa — helping to thwart RFID skimming attempts.
The RFID chips in contactless cards, passports, ID cards, or key fobs are programmed to transmit data automatically in response to RFID “pings” by interrogating devices such as card readers or security systems. By shielding them from unauthorized scanners, RFID blocking prevents criminals from secretly capturing sensitive information.
For a closer look at this low-tech solution to a high-tech form of data theft, here’s a breakdown of how RFID blocking works:
- RFID signals transmitted: RFID readers emit radio waves to communicate with RFID-enabled items and trigger the RFID chip to send stored data wirelessly.
- RFID signals disrupted: A metal or conductive fabric covering acts as an electromagnetic barrier, preventing the radio waves from reaching the RFID chip.
- Unauthorized access prevented: Because the RFID chip cannot receive or transmit signals through the blocking material, unauthorized scanners are unable to access sensitive data stored on the chip.
Because RFID blocking passively redirects electrical charges to neutralize radio signals, it doesn’t require batteries or any form of activation, making it a simple, efficient solution for protecting RFID-enabled items from skimming threats.
What is an RFID-blocking material?
RFID-blocking materials are conductive substances — usually metals or specialized fabrics such as aluminum and carbon fiber — that can disrupt the radio waves used by RFID technology.
Here’s a closer look at some RFID-blocking material examples and their effectiveness:
- Carbon fiber: A material made of mostly plastic powder and woven metal, it’s said to be effective against blocking electromagnetic frequencies. However, it might not be as effective against high-powered RFID readers.
- Leather: While leather may shield some electromagnetic signals, it isn’t seen as an effective blocker. Leather is often combined with other blocking materials to increase its effectiveness.
- Aluminum foil: It’s possible to block electromagnetic radiation with aluminum foil, but it isn’t ideal for RFID applications due to its susceptibility to wear and tear.
- Copper: Theoretically an effective RFID blocker because it’s highly conductive, copper can create a barrier that absorbs radio waves. But real-life effectiveness varies from product to product.
- Mu-metal: Used in many RFID blockers, mu-metal alloys are shown to be effective in redirecting electromagnetic signals, but durability is an issue since bending can cause it to lose some effectiveness.
Does RFID blocking work?
RFID-blocking wallets and sleeves work if they’re well-made, and use high-quality, RFID-blocking materials that completely cover the contents. The thicker and denser the shielding material is, the more likely it is to prevent attempted skimming attacks.
But it’s important to understand that the effectiveness of RFID blocking also depends on several factors including the strength and frequency of the RFID signal, and the distance between the RFID reader and the chip.
For example, active RFID tags have internal batteries that extend their range, allowing them to automate toll payments at distances of up to 300 feet. While these are unlikely to be blocked by most RFID-blocking products at short distances, the passive chips in contactless cards are much weaker and can be blocked by RFID-blocking materials — even at close range.
To test if an RFID blocker works, place a contactless card inside the product and hover it over a payment reader when checking out at a store. If it scans, the product isn’t effectively blocking the signal.
Is RFID blocking necessary, and do you actually need it?
Using RFID-blocking products offers simple and effective protection against unauthorized scanning, making them a worthwhile option for anyone concerned about fraud or identity theft relating to their contactless payment cards and passports.
While the risk of RFID skimming is relatively low — phishing attacks and data breaches are far more common — card skimming attacks are a real threat, despite the robust security protocols built into contactless payment systems.
It’s important to note that RFID attacks come in other forms too, and can even pose a physical security risk if criminals use scanners to perform digital tailgating attacks to steal information from security tags or key fobs. By capturing access credentials wirelessly, they can clone the RFID device, spoof security systems, and gain unauthorized entry to secure locations or systems.
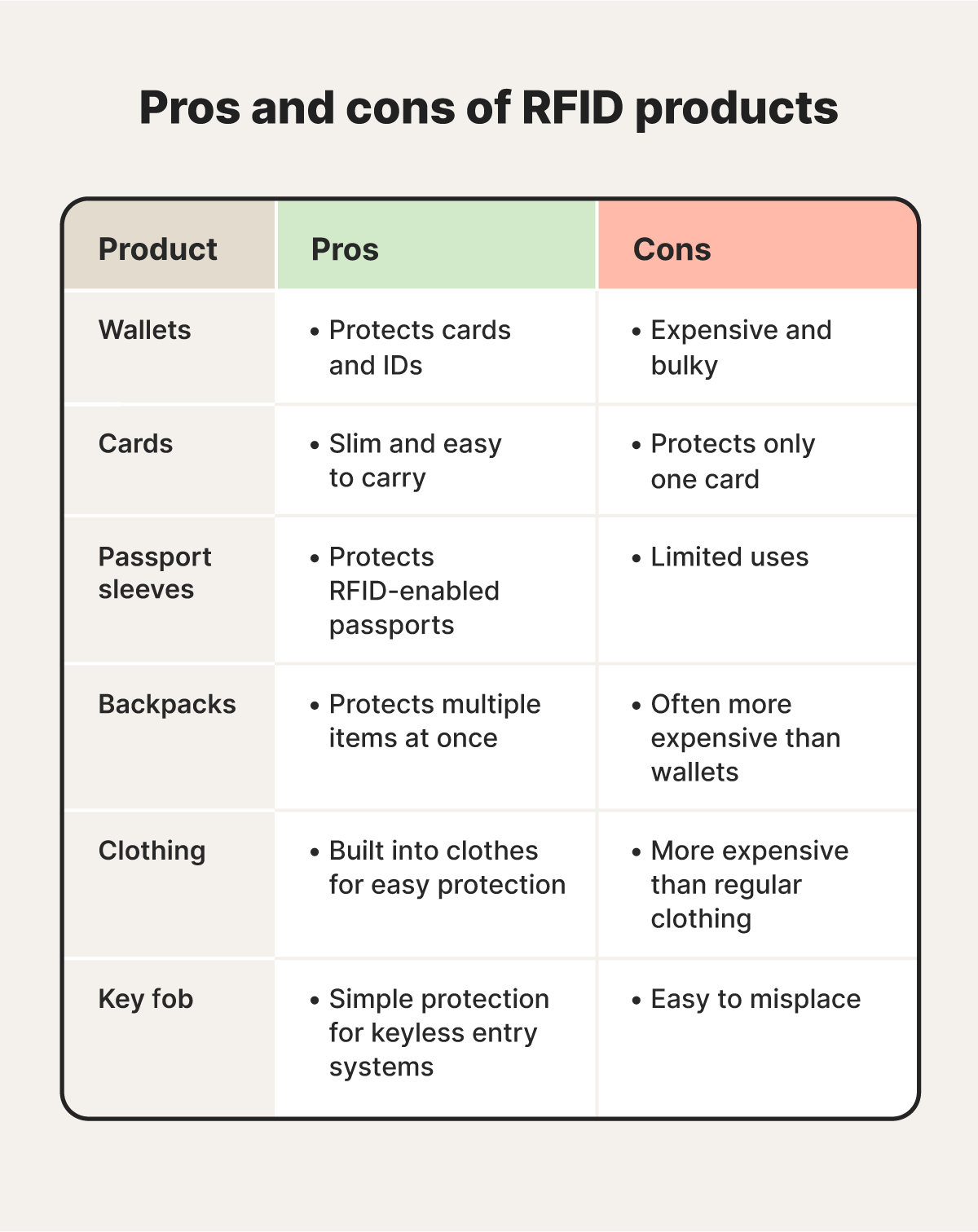
RFID blocking example products
The most common RFID-blocking products are wallets, cards, and passport sleeves, but it’s also possible to buy backpacks and clothes with RFID-blocking materials woven into them.
Here are a few RFID product examples:
- Wallets: RFID-blocking wallets use aluminum or copper woven into wallet fibers to block radio waves. This prevents skimmers from using devices to scan your cards.
- Cards: RFID-blocking cards are often made of metal, like copper or mu-metal, to jam radio signals unless they’re extremely close.
- Passport sleeves: RFID-blocking passport sleeves use materials woven into the sleeve covering to prevent skimmers from stealing sensitive personal data.
- Backpacks: RFID-blocking backpacks weave materials throughout the bag to prevent radio waves from escaping RFID-enabled devices inside.
- Clothing: RFID-blocking pants, jackets, and shirts weave radio-blocking materials into clothing fabrics, helping to secure payment cards or key fobs in your pockets.
- Key fob protectors: RFID-blocking key fob protectors are designed to stop skimmers from cloning your key fob and remotely opening your RFID-enabled garage or car door.

Beware that counterfeit and other bogus products often claim to have RFID-blocking features to boost sales, even if they offer minimal or no protection. To verify products before you buy, check reviews on third-party sites like Reddit to see if others have shared their experiences.
What to do if your RFID protection fails
If your RFID protection fails, and you’ve been fraudulently charged or believe your card details have been skimmed, report the issue to the local authorities, your bank, and the FTC. You should also set up bank alerts and monitor your accounts closely.
Here are some steps to take if your RFID protection fails:
- Call your bank: If you suspect your card information was compromised, contact your bank immediately. Request that they disable your card and issue a replacement to prevent further fraudulent transactions.
- Report compromised access cards or fobs: If you believe your RFID-enabled access card or key fob has been compromised, contact the issuer immediately to deactivate and replace it to prevent unauthorized access.
- Contact local law enforcement: Report RFID skimming to your police department. This helps document the crime, support potential investigations, and may assist in reclaiming lost funds.
- Monitor your accounts: Continue to monitor your accounts for any further fraudulent activity. If you notice an unrecognized transaction, report it to your bank immediately and secure your accounts.
- Set up bank alerts: Set up bank alerts via your bank’s mobile app or text to receive notifications for transactions or suspicious activity, reducing the need for manual monitoring.
- File a report with the FTC: Report any instances of fraud to the Federal Trade Commission (FTC). This helps them monitor broader trends and take necessary regulatory action.
- Replace your RFID-blocking product: If your wallet, sleeve, or bag isn’t blocking signals, invest in a higher-quality RFID-blocking product with proven shielding materials like copper or mu-metal.
- Invest in identity theft protection: If you suspect your passport or ID card’s RFID chip was scanned maliciously, enrolling in an identity theft protection service can help monitor for fraudulent activity and potentially avoid identity theft.
Protect against RFID skimming identity fraud
While RFID blocking can help safeguard your contactless cards and identity documents, it’s not something you want to rely on.
Norton 360 with LifeLock Select Plus offers comprehensive security and powerful identity theft protection, including Stolen Wallet Protection to help you cancel and replace lost or stolen cards, and Stolen Funds Reimbursement,† which can help cover financial losses due to identity fraud. Invest in peace of mind today.
FAQs
Does aluminum foil block RFID tags?
Aluminum foil has mixed results in blocking RFID tags. While it can deflect the electromagnetic signals used by RFID, it’s easy to tear or damage, which will severely impact its effectiveness. Although using multiple layers could help, it's not a reliable long-term solution for blocking RFID signals.
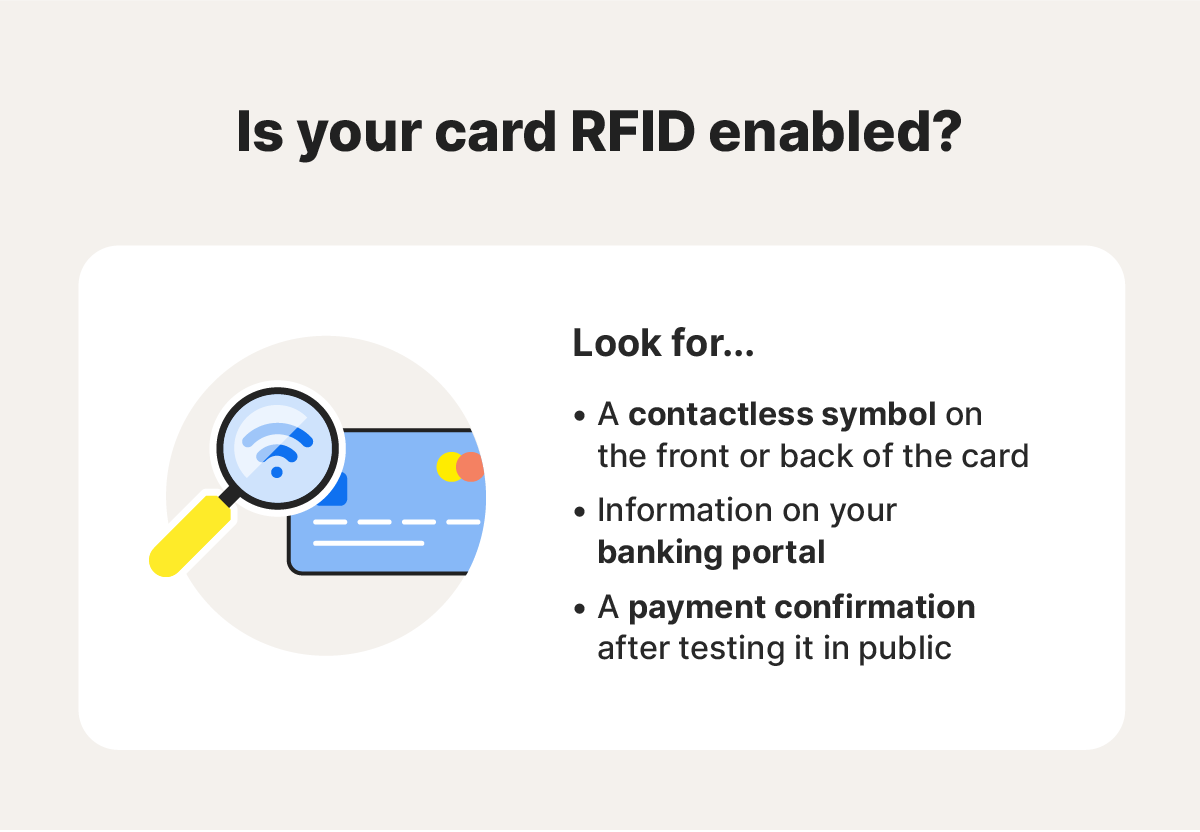
Does my credit card have RFID?
You’ll know your credit card has RFID when you see a contactless symbol resembling a Wi-Fi symbol on the front or back of the card. You’ll also find references to contactless or tap-based payments featured in your card’s documentation.
How important is RFID blocking when traveling?
Cases of RFID skimming are very rare, but RFID blocking can be important for your peace of mind when traveling through crowded airports or tourist attractions where your contactless cards and identity documents are more likely to be targeted by bad actors.
Do RFID wallets ruin credit cards?
No, RFID-blocking wallets do not ruin credit cards. The materials used, such as copper or aluminum, block emitted RFID radio signals, but they don't affect the integrity of the card itself.
Does RFID blocking prevent identity theft?
RFID blocking can help prevent certain instances of identity theft by blocking unauthorized scans of cards, passports, or ID cards embedded with contactless chips. By using materials that disrupt or absorb radio waves, RFID-blocking products create a protective barrier, making it much harder for criminals to steal sensitive personal and financial information through wireless skimming.
† Up to $1 million for coverage for Lawyers and Experts, collectively, if needed, for all plans. Reimbursement and expense compensation varies according to plan—up to $1 million for Ultimate Plus, up to $100,000 for Advantage, and up to $25,000 for Standard. Benefits under the Master Policy are issued and covered by third-party insurance companies.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.









Want more?
Follow us for all the latest news, tips, and updates.