Can someone track my phone? A guide to detection and prevention
Phone tracking is easier than you might think. From spyware to tracking links, cyber snoops have various ways to compromise your privacy. Learn how to spot, prevent, and remove tracking threats, and discover how Norton 360 for Mobile can help safeguard your device from spies.

Smartphones make life easier, but they also store a wealth of personal and sensitive information. Unfortunately, their convenience comes with risks — including the possibility of someone tracking your device without your knowledge.
This can occur through various methods, such as spyware attacks, unauthorized phone access, or phishing. In the wrong hands, helpful features like location tracking can be misused. Knowing the warning signs of unauthorized tracking is the first step to protecting your privacy.
How can someone track your phone?
Someone can track your phone using spyware, phishing attacks, SIM card cloning, or by exploiting public Wi-Fi networks. Below, we’ll break down common methods in more detail and explain how to recognize and prevent them.
Tracking apps
Hackers (or any creep with physical access to your phone) can install spyware or tracking apps that run in the background, monitoring your calls, messages, location, and online activity. These apps are often disguised as harmless programs, making them difficult to detect.
Tracking apps can be installed remotely: advanced threats like Pegasus spyware can infiltrate a device using zero-click exploits, meaning the user doesn’t need to click a link or take any action for their phone to be compromised. Originally designed for government surveillance, Pegasus can track calls, messages, and locations without the victim’s knowledge.
Pegasus has historically been used in intelligence operations and to target journalists, executives, and government officials, but recent studies suggest that its prevalence is growing: one investigation uncovered 2.5 infected devices per 1,000 scans — although the study’s sample, drawn from users of cybersecurity software, may not be representative of the wider population. Other illicit software with phone tracking capabilities include FinSpy, DarkComet, AndroRAT, and SpyNote.
Phishing attacks
In a process known as phishing, cybercriminals use deceptive emails, text messages, or fake websites to trick you into downloading malicious software. Depending on the type of malware installed, it may have different tracking capabilities.
Spyware can monitor your location, log keystrokes, and access private data, while stalkerware is designed to track calls, messages, and GPS locations. More advanced malware, like remote access Trojans (RATs), can even take control of your microphone and camera, turning your device into a surveillance tool without your knowledge.
Public Wi-Fi
Unsecured public networks, like those found in coffee shops, hotels, or airports, can expose your data to potential threats because they often lack encryption and allow multiple users to connect without authentication. This open nature makes it easier for attackers to intercept communications or manipulate network traffic.
Hackers can exploit these vulnerabilities in several ways. They may deploy packet sniffers to intercept unencrypted data, browser hijackers that redirect you to malicious sites, or man-in-the-middle (MITM) attacks that secretly position themselves between you and a legitimate website to alter communications in real time.
While public Wi-Fi isn’t inherently dangerous, it’s best to avoid accessing sensitive accounts, making financial transactions, or entering personal information, unless you’re using a trusted VPN, such as Norton VPN to encrypt your connection.
Social engineering
Attackers may attempt to manipulate or deceive you into providing access to your phone by posing as a trusted individual or convincing you to install malicious apps. These tricks are known as social engineering.
Cybercriminals often combine social engineering with phishing to trick victims into revealing sensitive information.
SIM cloning
SIM cloning is another phone tracking attack vector. Hackers use specialized hardware to create a duplicate SIM that connects to the same network as the victim’s, allowing them to intercept calls, SMS messages, and location data from cell tower connections, effectively tracking the victim’s movements in real time.
Since this method doesn’t require installing spyware, it’s a particularly stealthy way to track someone.
How to know if someone is tracking your phone
Unusual device behavior — like rapid battery drain, strange noises during calls, or unexpected icons appearing on your screen — can indicate unwanted tracking. If someone is actively tracking your phone, you might not notice it immediately.
Modern tracking methods can be subtle, running in the background without obvious signs. In fact, some of the most sophisticated tracking apps, like Pegasus, may be almost impossible to detect without advanced cybersecurity software.
Both iPhones and Android devices offer ways to check if apps are accessing your location, microphone, or camera without your knowledge. In this section, we’ll cover key indicators that your phone might be tracked.
Tracking icons
Most smartphones have built-in indicators that show when location services, the microphone, or the camera are in use. These icons typically appear when you’re using apps that require these permissions — such as maps, rideshare apps, or video calls.
However, if you notice these icons appearing unexpectedly, especially when you’re not actively using an app that should trigger them, it could be a red flag.
How to check for tracking icons on iPhone
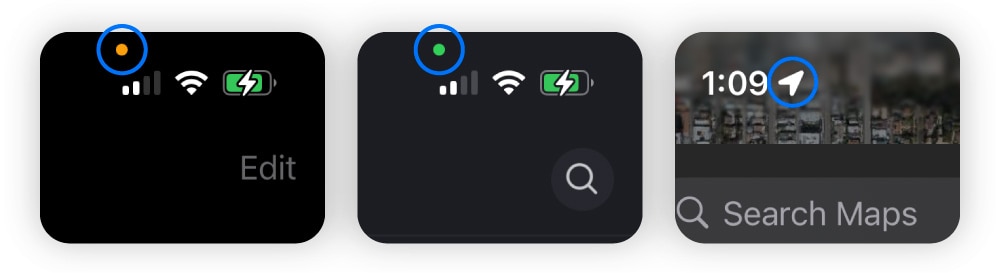

On an iPhone, a small colored dot or an indicator banner can reveal if your microphone, camera, or location are in use:
- Microphone: An orange dot appears in the top-right corner of the screen.
- Camera: A green dot appears in the same location.
- Location: A small arrow icon appears in the status bar.
To check which apps have recently accessed these services:
- Swipe down from the top-right corner to open the Control Center.
- Look for a privacy banner above the battery and signal indicators at the top.
- Tap the banner to see a list of apps that recently accessed your camera, microphone, or location.
How to check for tracking icons on Android


Android also displays real-time indicators when an app accesses sensitive phone features:
- Microphone or camera: A green dot or icon appears in the top-right corner when either is in use.
- Location tracking: A small location arrow appears in the status bar when an app actively uses your location.
To see which apps recently accessed your location:
- Open Settings.
- Select Location.
- Under Recent access, you’ll find a list of apps that have used your location.
Note that tracking icons may differ depending on your Android manufacturer, but the icons should still pop up in the same place in the status bar.
Poor device performance
If your phone has been behaving sluggishly, overheating, or its battery has been draining unusually fast, it could be more than just normal wear and tear. Spyware and tracking apps often run silently in the background, consuming processing power and battery life while transmitting data without your knowledge. These hidden processes can also cause spikes in data usage, which is another red flag.

Signs of tracking-related performance issues
- Unusual battery drain: If your phone’s battery depletes much faster than usual, it could be due to tracking software constantly running in the background. Learn more about why batteries drain quickly.
- Overheating: Phones naturally warm up when charging or running demanding apps, but if yours feels hot even when idle, it may be due to spyware overworking the device. Read more about why your phone gets hot.
- Spikes in data usage: Tracking software often transmits collected data to external servers, leading to sudden increases in mobile data usage. If your data consumption seems unusually high, it’s worth investigating.
How to check data usage on iPhone
- Open Settings.
- Tap Cellular (or Mobile Data in some regions).
- Scroll down to see a list of apps and their data consumption. Apps using excessive data without your knowledge could indicate spyware.
How to check data usage on Android
- Open Settings.
- Tap Connections > Data usage.
- Select App data usage to see which apps have used the most data recently.
Unfamiliar apps
Finding apps on your phone that you don’t remember downloading could be a warning sign of tracking software. While your device manufacturer or system updates may install unfamiliar apps, spyware is often disguised as harmless tools like weather apps, calculators, or system utilities to avoid detection. If you see an app you don’t recognize, it’s important to verify its legitimacy.
Malicious tracking apps can secretly monitor your location, record your calls, and collect personal data. If you find an app that seems suspicious, search for its name online to check its credibility. If it’s unverified or has mostly negative reviews in the App Store or Google Play, uninstall it.
How to check for unfamiliar apps on iPhone
- Open Settings.
- Scroll down to see a list of installed apps.
- If you find an app you don’t recognize, search for it online. If it’s suspicious, press and hold the app icon, tap Remove App, and select Delete App to uninstall it.
How to check for unfamiliar apps on Android
- Open Settings.
- Tap Apps or Apps & notifications.
- Scroll through the list and look for any unknown apps.
- If you find a suspicious app, tap it, then select Uninstall.
Strange texts or calls
Unexpected texts or calls can indicate that someone is tracking your phone. Spyware and malware sometimes use SMS messages to send and receive data, which means you might notice strange outgoing messages that you didn’t send or incoming texts with random characters or symbols. These coded messages can be commands sent to a spyware app running on your device.
Unusual calls can also indicate tracking. Hearing frequent background noises — such as clicking, beeping, or echoes — during phone calls could mean your phone is being monitored. While occasional sound distortion can result from network issues, persistent strange noises may suggest that spyware is secretly listening in.
What to do if you receive strange messages or calls
- Delete suspicious texts without clicking on links.
- Block unknown numbers sending spam texts.
- Avoid answering unknown numbers or robocalls.
- Check your messaging and call logs for any unknown activity.
- Run a security scan to detect spyware that may be using your phone’s communication channels.
If you consistently receive strange messages or experience unusual call interference, it’s worth investigating further to ensure your device isn’t being tracked.
What to do if your phone is being tracked
If you suspect that someone is tracking your phone, take immediate action. Here are a few ways:
Turn off location services
One of the easiest ways someone can track your phone is through location services. Apps, websites, and even hackers can use GPS data to monitor your movements in real time. Disabling location services limits their ability to do so, reducing the risk of unauthorized tracking.
However, note that turning this off may affect apps like Google Maps or ride-sharing services, so you may want to customize settings to allow access only when necessary.
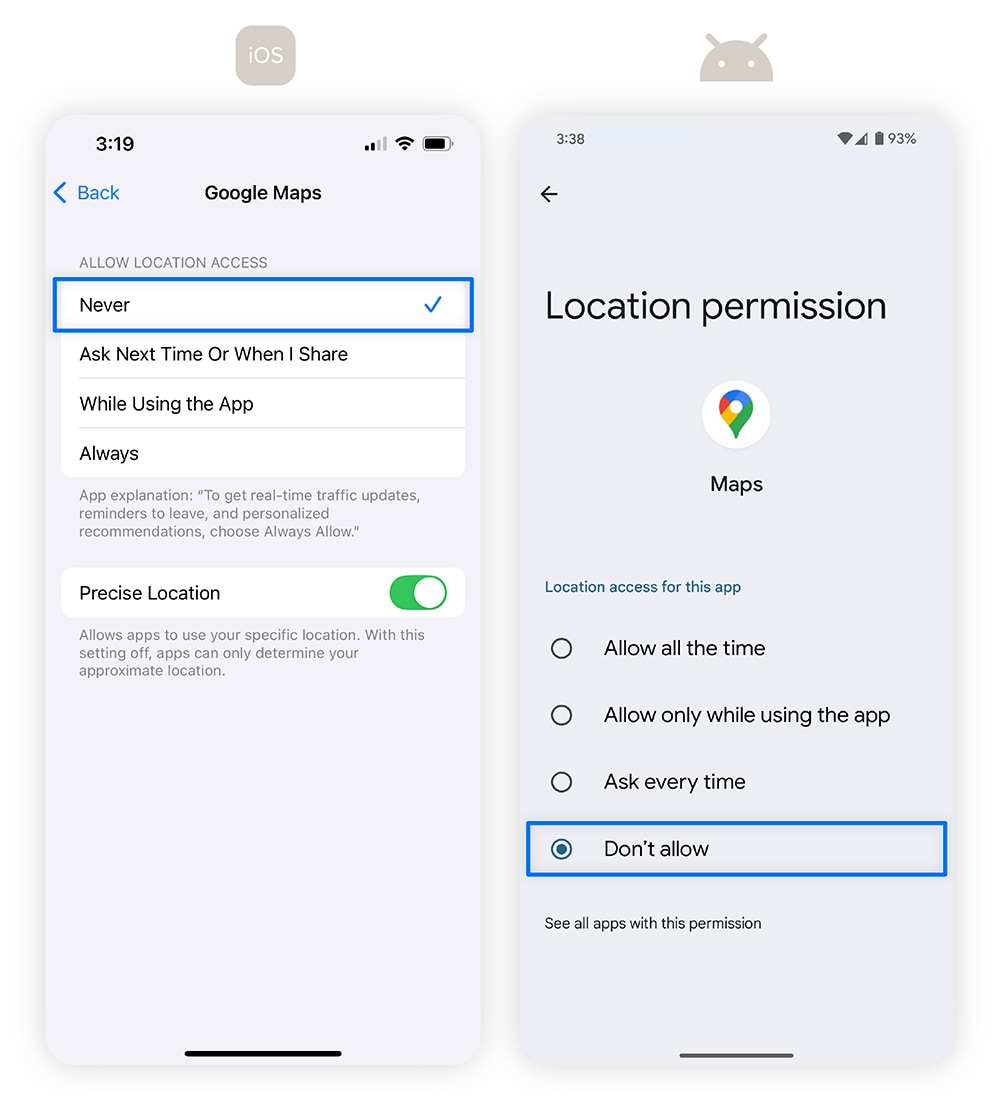

How to block location tracking on iOS:
- Open your iPhone’s Settings.
- Scroll down and tap Privacy & Security.
- Tap Location Services.
- Toggle the Location Services option off. Alternatively, you can customize the setting for individual apps by selecting the app and choosing Never, While Using the App, or Ask Next Time.
How to block location tracking on Android:
- Open the Settings app.
- Select Location.
- Toggle the Location setting off.
- You can also customize location access for specific apps by scrolling down and selecting the app you want to modify.
Change passwords
If someone is tracking your phone, they may have access to your accounts, including iCloud, Google, or other services that sync data across devices. Changing your passwords ensures you revoke all unauthorized access, preventing further tracking and data breaches.
Tips for a strong password:
- Create a secure password for all your accounts that’s at least 15 characters long, and includes randomized letters and numbers.
- Use a password manager to track and secure your login credentials and ensure you’re not reusing weak passwords across multiple sites.
Scan for malware
Spyware or tracking apps can run in the background without your knowledge, collecting data like your location, messages, and browsing activity. Running a malware scan helps detect and remove such threats before they cause serious privacy issues. If the scan finds any threats, follow the app’s instructions to remove them.
Contact the authorities
If you’ve confirmed someone is tracking your phone without your consent, reporting it to the authorities can help stop the activity and hold the responsible party accountable.
Law enforcement may guide you on legal actions, such as filing a report and obtaining an investigation. Keeping a record of suspicious activities, such as unknown logins, strange texts, or new apps, can help in their investigation.
Reboot in safe mode
Some tracking apps disguise themselves as legitimate software and operate in the background. Restarting your phone in safe mode temporarily disables third-party apps, helping you identify and remove any suspicious ones.
How to reboot in safe mode:
For Android:
- Hold the Power button.
- Tap and hold Power off until you see the Safe mode option.
- Tap the green Safe mode icon to reboot in Safe mode.
iOS does not have a “safe mode,” but you can restart your phone, avoid opening any apps, and monitor if your issue persists.
Clear cookies and cache
Websites and apps store cookies and cache data so they can load faster when you visit. Clearing cookies and cache can remove stored information that scammers may use to monitor your behavior, if they happen to get hold of it.
For iOS:
- Go to Settings > Safari.
- Tap Clear History and Website Data.
For Android:
Note that this process may be slightly different if you’re not using Chrome.
- Open Chrome and tap the three dots in the top-right corner.
- Go to History > Clear browsing data.
- Select the Time range and choose Cookies and site data, then tap Clear data.
Uninstall suspicious apps
If you find any apps you don’t recognize or don’t remember installing, they could be tracking your activity without your knowledge. Some apps disguise themselves as harmless tools, such as weather apps or games, but are actually spyware.
Here’s how to remove them.
For iOS:
- Press and hold the app icon until it shakes.
- Tap Delete App.
For Android:
- Go to Settings > Apps.
- Select the suspicious app, and tap Uninstall.
Factory reset your phone
If all else fails and you still believe your phone is being tracked, a factory reset is the most effective way to ensure that any malicious software is completely removed. A factory reset will erase all data on your phone, including apps, settings, and personal files. Be sure to back up any important data before performing this action, as it cannot be undone.
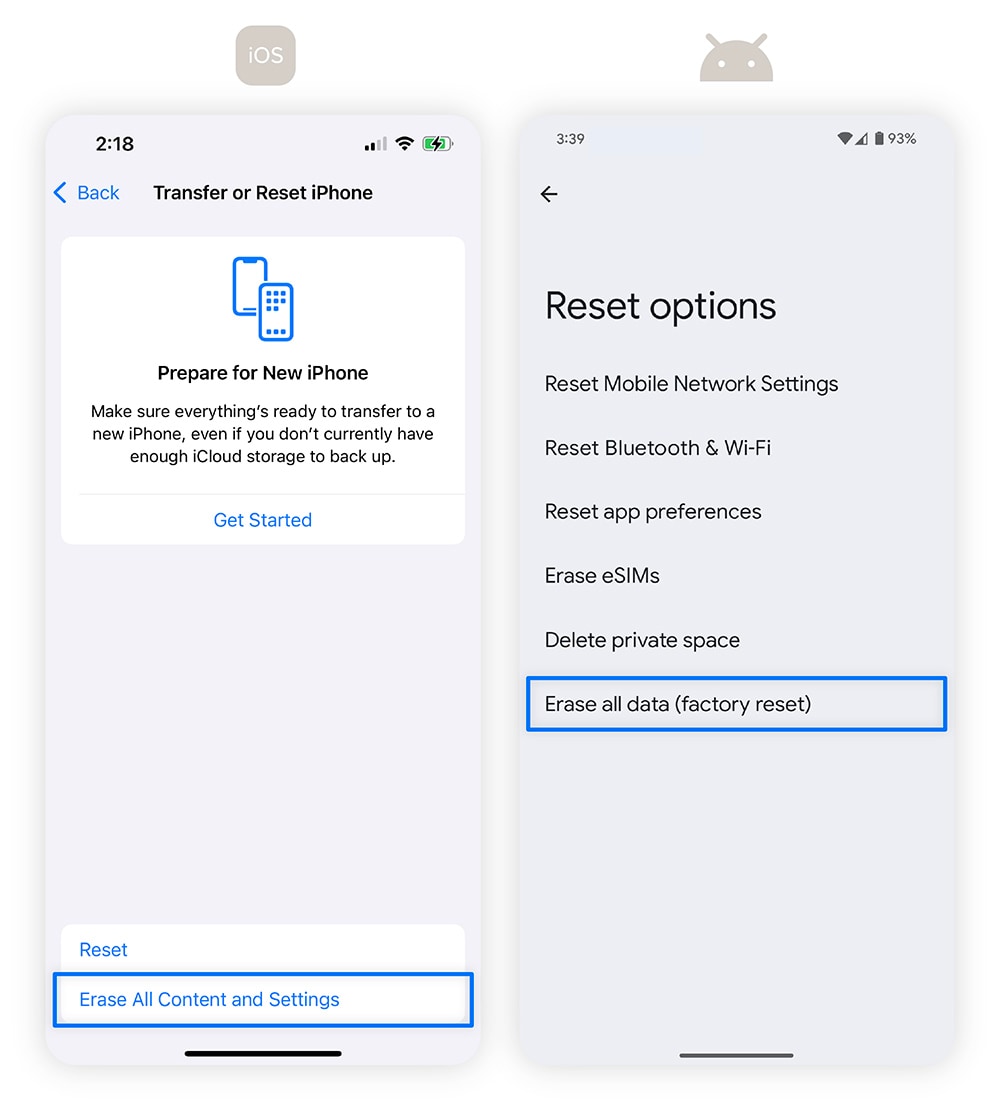

How to factory reset an iPhone:
- Go to Settings > General > Reset.
- Select Erase All Content and Settings.
How to factory reset an Android phone:
- Open Settings.
- Scroll down and tap General management or System.
- Select Reset > Factory data reset.
How to prevent someone from tracking your phone
Taking a few proactive steps can significantly reduce the risk of unauthorized tracking, helping you keep your data secure. Follow these essential measures to safeguard your privacy.
- Install routine updates: Regularly updating your phone’s operating system and apps is one of the best ways to patch security vulnerabilities and prevent tracking. Keeping your software updated ensures you have the latest security protections in place.
- Use a VPN: A virtual private network (VPN) encrypts your internet connection, making it challenging for someone to track your online activity. This is especially useful when browsing on public Wi-Fi, where unsecured networks can expose your data.
- Turn off location services: Many apps continuously track your location, even when they don’t need to. Disable location sharing for apps that don’t require it, or turn off location services entirely when privacy is a concern.
- Try a private browser: Regular browsers save cookies and history that criminals can use to track you. Switching to a secure browser with built-in privacy features can help keep your activity more private.
- Use secure messaging apps: Some communication apps may collect and share your data without your knowledge. Stick to reputable, encrypted messaging apps to protect your conversations and personal information.
- Download apps from trusted sources: Only install apps from official stores, like the App Store or Google Play. Be cautious of third-party sources, as they may contain spyware or malware designed to track your activity.
- Turn off Bluetooth: Cybercriminals can exploit Bluetooth connections to track your device or even inject malware. To prevent unauthorized access, keep Bluetooth disabled when not in use.
- Use airplane mode: If you suspect tracking, enabling airplane mode will instantly cut off all wireless connections, including cellular data, Wi-Fi, and Bluetooth, making it much harder for your phone to be tracked.
- Manage app permissions: Many apps request unnecessary access to your location, microphone, and camera. Update app permissions regularly to limit the data they can collect.
- Install security software: A good security app can detect spyware, block unauthorized tracking, and protect your personal data. Adding this extra layer of defense can help keep your information safer.
By implementing these steps, you can take control of your digital footprint and prevent unwanted tracking of your device.
Protect yourself from phone tracking today
Having your phone tracked isn’t just an invasion of privacy — it’s a real security risk. Norton 360 for Mobile offers powerful cybersecurity tools to help safeguard your mobile device against threats.
Features like Suspicious Network Detection and Wi-Fi Security help protect you from potentially unsafe networks that could lead to a spyware infection. Take control of your privacy today.
FAQs
Why would someone want to track my phone?
People may track phones for personal or malicious reasons. A jealous partner or family member might monitor your location, while cybercriminals might aim to steal data for fraud. Employers or governments may track devices for surveillance.
Can someone watch you through your phone camera?
Yes, hackers can access your phone’s camera using spyware or malware, capturing photos or videos without your knowledge. They often trick users into installing malicious apps. To protect yourself, check app permissions, cover your camera when not in use, and use security software.
Can someone track my phone if my location is off?
Even with location services off, tracking is possible via Wi-Fi, Bluetooth, or cell towers. Spyware can also reveal your location. Use a VPN, disable Bluetooth when not needed, and review app permissions.
Can people track your phone number?
Yes, using methods like carrier tracking, SIM cloning, tracking apps, or phishing scams. Protect yourself by keeping your number private, enabling two-factor authentication, and avoiding suspicious messages.
Is there a code to stop someone from tracking your phone?
You can dial ##002# to disable call forwarding and *#21# to check if calls and texts are forwarded. However, these don’t detect spyware or show who is tracking your phone. To fully secure your device, regularly update your phone, install security software, and be cautious when downloading apps or clicking suspicious links.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.








Want more?
Follow us for all the latest news, tips, and updates.