What is a third-party app? Examples and potential risks
Third-party apps are any applications that aren’t created or supported by the maker of the device the app is installed on. While these apps are generally safe, especially if downloaded from an official app store, they could put your personal data at risk. Keep reading if you want to learn how to keep your devices clear of dangerous software and how mobile security software like Norton 360 Deluxe can offer even more protection.

First-party apps vs. third-party apps
Hardware manufacturers of smart devices create applications for their own devices. Those are first-party or “native” apps. A third-party app is a software application made by someone other than the manufacturer of the mobile device or its operating system. While manufacturers frequently create new apps to ship with their devices, most available applications are third-party apps.
Here’s an example: An email application that comes with your mobile device—likely with the manufacturer’s name on it—would be a native app. Uber is a third-party app because it wasn’t created by Apple or Google for use on their devices.
Types of third-party apps
While there are third-party applications for nearly everything you can think of, they fall into one of four main categories depending on where they’re downloaded, what they’re used for, and who they were designed to be used by.
Apps available on official app stores
These are the apps that people are most familiar with because they download and use them regularly. If you want to play a new game or find a way to track how much water you drink every day, you click on the app store icon on your phone, tablet, or computer and search among the apps listed there.
In order for one of these apps to be listed on official app stores, they are checked for malware, and they are supposed to meet certain criteria for privacy, data collection, and operating system compatibility.
While those measures aren’t always bulletproof, the apps you get from an official app store will usually be safe to use.
Apps from unofficial app stores or websites
There’s nothing inherently bad about unofficial app stores or websites where you can download applications. For specialized applications with limited user bases, it might not make sense for a developer to jump through all the hoops required by Google or Apple just to get an app listed. These unofficial app stores make it possible for them to distribute their application.
However, because those marketplaces are usually smaller, they may not have the resources to thoroughly check each program available for download. In other words, those apps can be more susceptible to infecting your mobile device with malicious codes like ransomware and adware. That’s because the ads or codes violating your privacy can be “injected” into popular apps you might buy through a third-party store.
The stores might sell popular apps for cheaper prices, which may sound appealing. But that bargain buy can put user privacy at risk.
Custom apps
Custom apps (also called in-house or enterprise apps) are designed and used by businesses. Many of these apps aren’t available on an app store because they’re only used internally. These apps can be developed to meet any need a business has—from inventory management to appointment scheduling to logistics. These apps are usually safe because they’re often installed on company devices and may have many other features disabled or limited to reduce the risk of problems.

Apps that enhance other apps or services
This type of app is different from the other apps mentioned because it may not even be downloaded directly to a device. Instead, it could be an application that is connected to another app and is authorized to use the data from that app to perform another function. For example, some of these apps use certain information accessed from a Facebook or Google account to enhance or add something to those profiles. Because these apps, like Zoom’s Google Calendar integration, connect directly to these accounts, they generally follow strict compliance requirements.
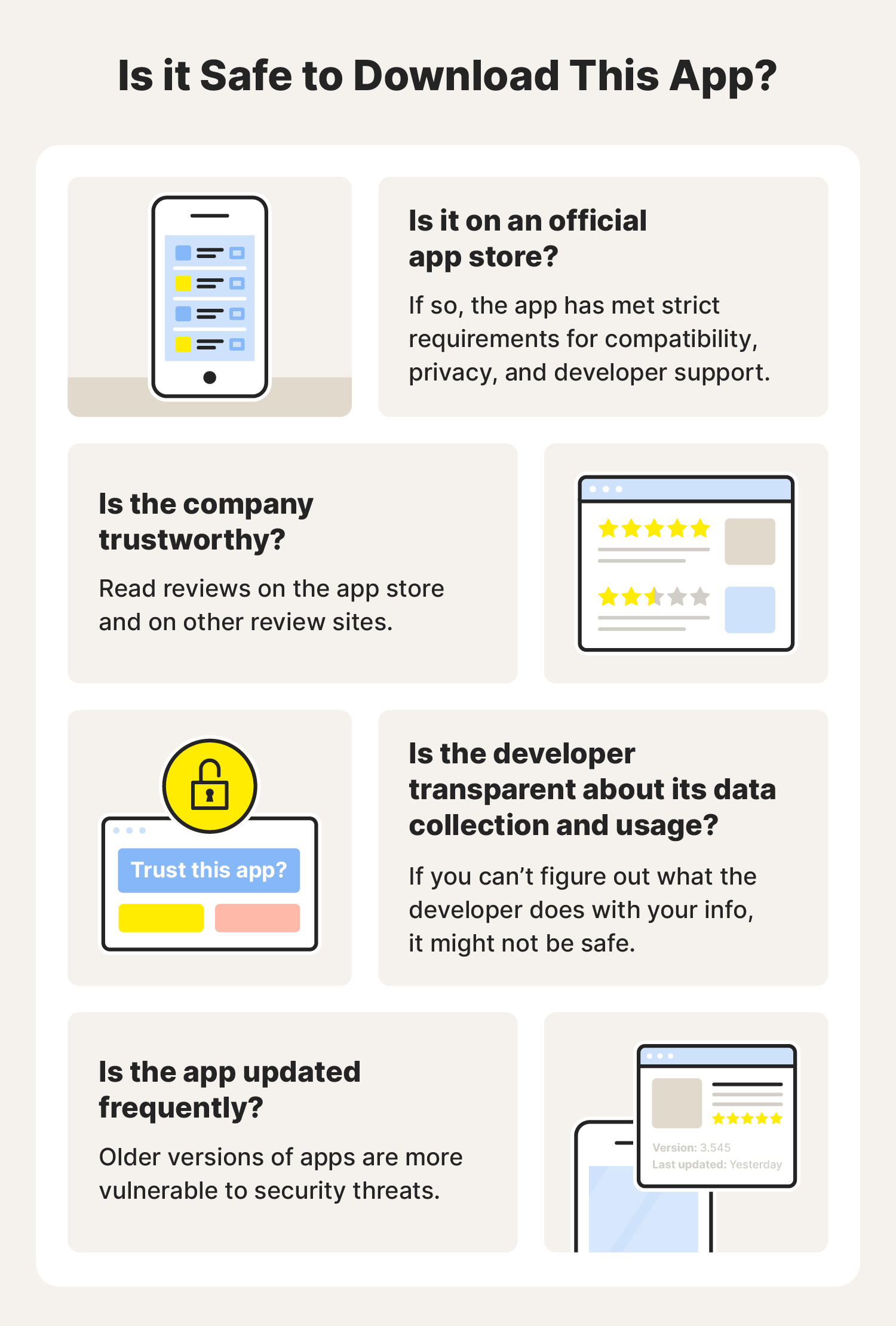
Risks of downloading and using third-party apps
Not all apps are what they appear to be. Some third-party software may look like other popular apps, but these scam apps can turn out to be a big headache when they damage your phone or compromise your privacy. Don’t be fooled into thinking that one kind of operating system is necessarily more secure than another: both Android and Apple devices are vulnerable.
Data exposure
Apps found in official app stores must adhere to strict data protection standards to be listed, while unofficial app stores (and the apps they list) may not have those same standards in place. Because your devices are filled with everything from your photographs to your financial information, having this information exposed could increase your risk of identity theft.
Here are a few examples of sensitive information third-party apps and app stores might extract:
- Phone numbers
- Device information
- Email addresses
Because of the potential security and privacy risks of having that information exposed, consider your security settings and where you download third-party apps from.
Security risks
In addition to exposing your personal information, some apps create or exploit existing vulnerabilities that can put the security of yourself, your business, or even the government at risk. The United States government banned TikTok from being installed on all government-issued devices after concerns about cybersecurity and privacy.
Malware and viruses
If you download an app from an untrustworthy store, site, or link , you could be downloading a program full of viruses or malware. These kinds of apps function properly, so you may not know anything bad is happening. Other apps might be part of a mobile ransomware scheme where your data is stolen, and you are forced to pay a criminal to get it back. Worse yet, once the app is installed, you may not be able to remove the malware or virus, even if you uninstall the application.
Stay safer when using third-party apps and app stores
One way to minimize danger from third-party apps and app stores is to avoid them. But, even if you do, it’s also possible to download an app from one of the official app stores and have your device subject to malware. So, how do you keep your device and your personal information safe? Signing up for Norton 360 Deluxe helps keep your devices safe by constantly monitoring your devices for malware, viruses, and other vulnerabilities.
FAQs about third-party apps
Have more questions about downloading apps? Read on to learn more.
Are third-party app stores all the same?
No. Not every third-party app store poses the same level of risk. Because Google Pay isn’t available in some countries, users in those countries may have to use third-party app stores to install their apps.
What are examples of third-party apps?
Every app not made by the company that makes your device’s operating system is a third-party app. This means that everything from the Facebook app to the New York Times app is a third-party application.
How do I delete third-party apps?
You delete them in the same way you would delete any other app. Some operating systems let you delete apps by pressing and holding on the icon, while others might have an applications manager where you can delete apps.
What do third-party apps have access to?
It depends on your settings. Many operating systems have default settings that limit access by third-party apps. You can change what information apps can access in the app or operating system settings. Many third-party applications will require you to give them permission to use certain features of your phone when you first install the app. This gives you more control over the parts of your device the app can access and change
Why are third-party apps banned?
It varies. Some businesses and governments have banned certain third-party apps because of security and privacy concerns. Other companies like X (formerly known as Twitter) have banned third-party apps because they violated X’s API terms of service.
Who uses third-party apps?
Almost everyone uses third-party apps. Unless an app is made by the hardware or operating system creator, it is a third-party app.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.







Want more?
Follow us for all the latest news, tips, and updates.