What is a rootkit? Detection + prevention tips
Computer viruses and malware are serious threats, but rootkits might be the most dangerous, both in the damage they can cause and the difficulty in finding and removing them. Read on to learn how to tell if a rootkit has infected your device and the steps to remove it. Better yet, install Norton 360 Deluxe to help protect yourself against rootkits and other types of malware.

What is a rootkit?
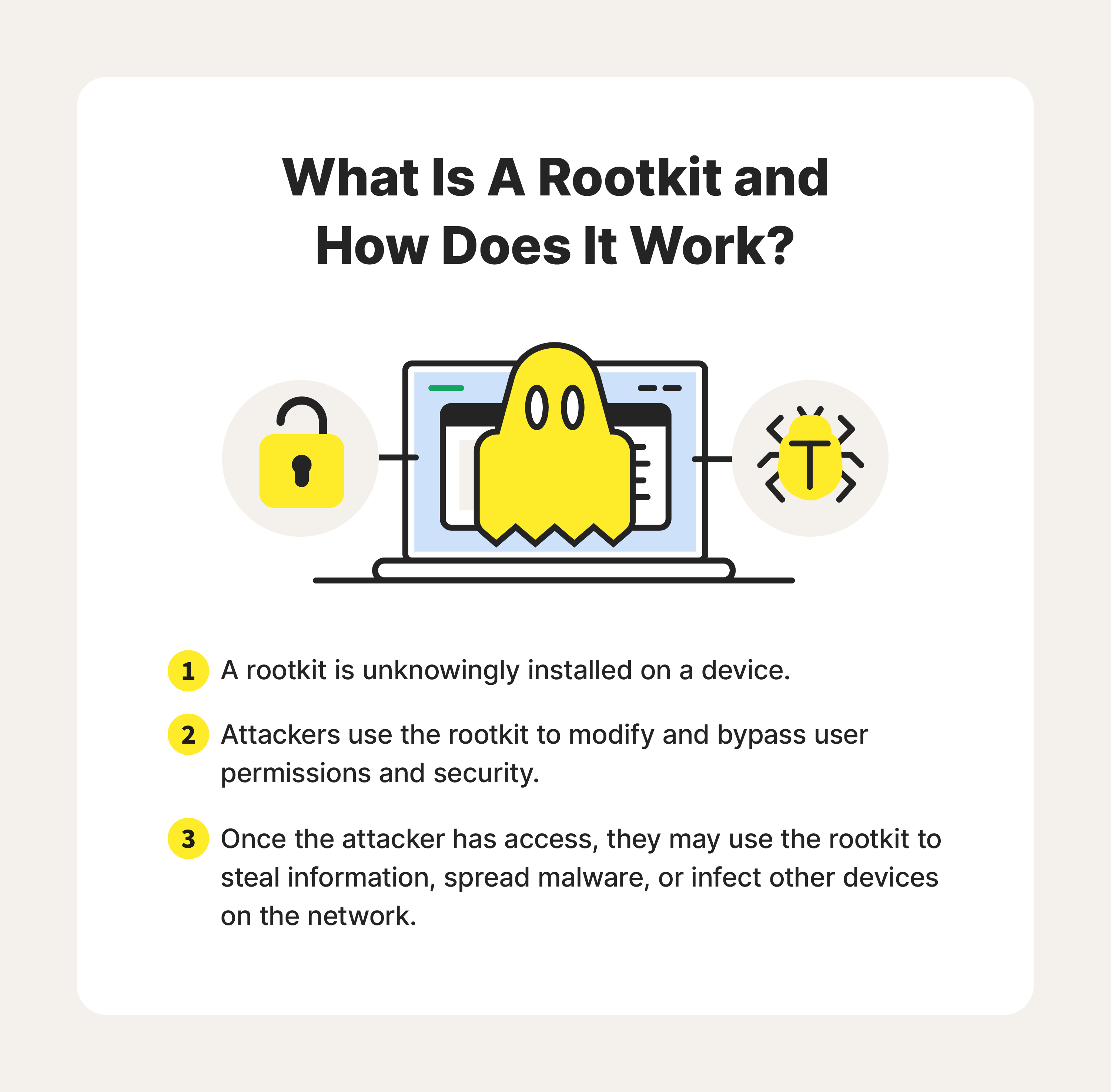
Rootkits are malware designed to let malicious code hide within your device. While they may not be doing obvious damage to your system, rootkits give cybercriminals the ability to remotely control your operating system without detection, putting your network and personal information at risk.
Here are a few examples of how rootkits can affect your operating system:
- Hidden malware: Rootkits can install and conceal other types of malware within your network, making detecting and removing them difficult.
- Remote access: Cybercriminals use rootkits to gain unauthorized remote access to a system, so they can steal or modify information without detection.
- Backdoor creation: Hackers can use a rootkit to open a “backdoor” into your operating system, allowing them to access a network that bypasses the system’s security mechanisms.
- Microphone/camera access: Cybercriminals can use rootkits to hack your device's webcam and microphone to eavesdrop on your conversations.
Cybercriminals take advantage of system and user vulnerabilities when infecting devices with rootkit malware. Rootkits can be installed on a device through various methods, including:
- Exploiting vulnerabilities: Rootkits can exploit system security vulnerabilities that have not been patched or fixed by the user or the software developer.
- Drive-by downloads: When you visit compromised or malicious websites, cybercriminals can exploit vulnerabilities in your browser or its plugins to silently download and install a rootkit on your computer without your knowledge or consent.
- Email attachments: Rootkits can be distributed through malicious email attachments. These attachments may appear harmless, but once opened, they exploit vulnerabilities in software (such as document readers) to install the rootkit.
- Social engineering: Attackers may use social engineering techniques to trick users into installing rootkits unknowingly. They can do this through deceptive pop-up windows, fake software updates, or enticing downloads that, when executed, install the rootkit.
- Infected software installers: Attackers can compromise legitimate software installers and bundle them with a rootkit. When users download and install these infected programs, the rootkit is installed alongside it.
- Physical access: If an attacker gains physical access to your computer, they can directly install a rootkit through various means, such as booting from an external device or modifying the system firmware.
Types of rootkits
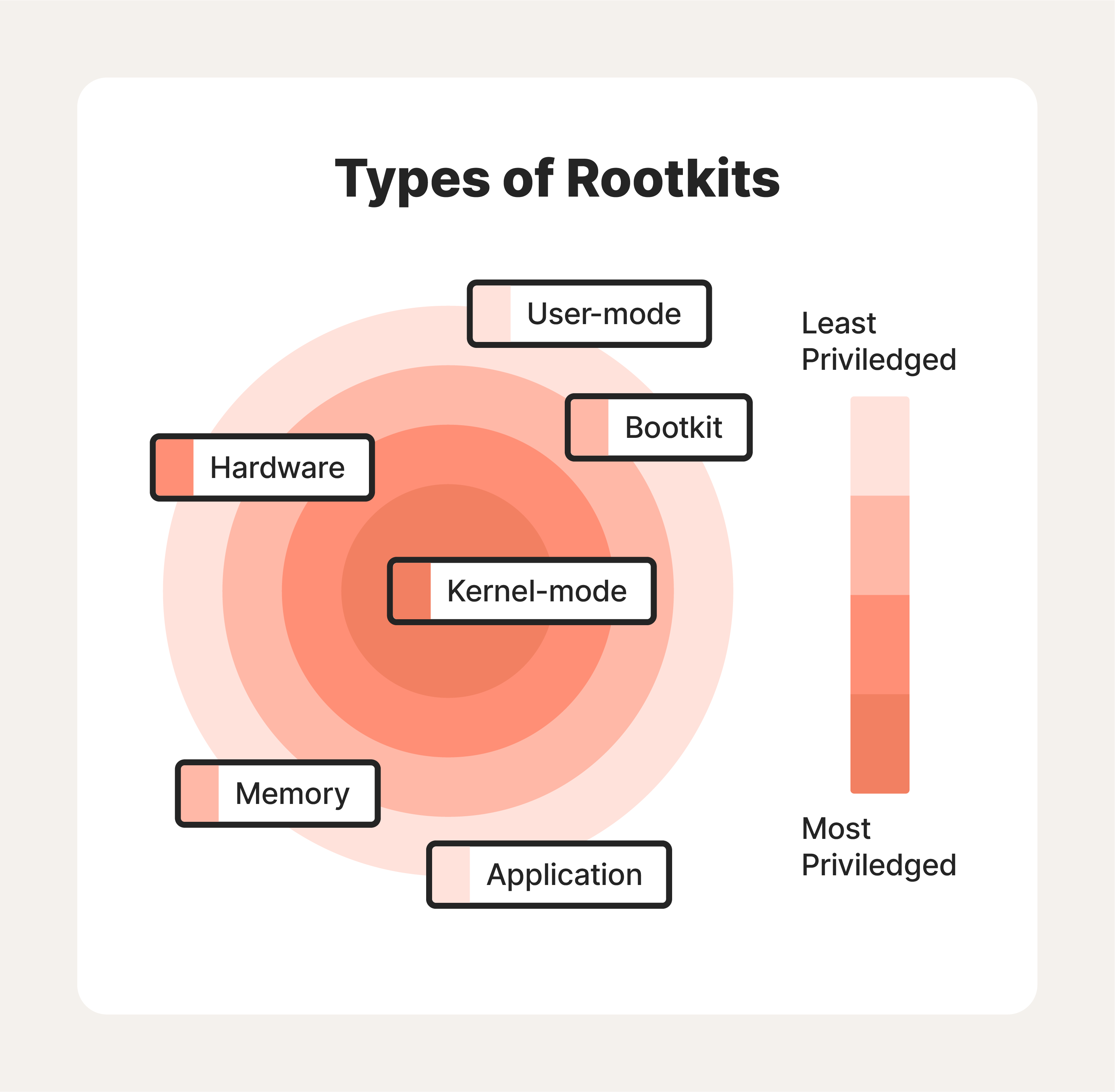
Types of rootkits vary by the system components they infect and the level of access they grant an attacker. To that end, there are six common types of rootkits you should be aware of—and avoid:
1. User-mode rootkits
A user-mode rootkit operates at the user level of an operating system. Unlike kernel-mode rootkits that target the operating system's core components, user-mode rootkits focus on manipulating or undermining specific applications or processes running on the system.
2. Application rootkit
Application rootkits target programs at the application layer of a computer system, giving hackers access to your computer every time you use a compromised app. They replace standard files in your computer with rootkit files that may slightly change how infected applications work. The challenge here is that the infected programs will still largely run normally, making it difficult for users to detect the rootkit.
3. Bootloader rootkit or bootkit
Your computer’s bootloader is an important tool required to load your computer’s operating system when you turn the machine on. A bootloader rootkit attacks this system, replacing your computer’s legitimate bootloader with a hacked one. This means that the bootkit gets activated even before your computer’s operating system turns on, allowing hackers to control the system from the earliest stages of startup. Bootkits are challenging to detect and remove as they execute before the antivirus and security software.
4. Memory rootkit
Memory rootkits hide in your computer’s Random Access Memory (RAM) and can modify running processes, intercept system calls, and manipulate data to hide their presence and evade detection. The good news? These rootkits have a short lifespan. They only live in your computer’s RAM and will disappear once you reboot your system—though sometimes further work is required to get rid of them.
5. Hardware or firmware rootkit
As the name suggests, this type of rootkit targets the firmware or hardware components of a system or the system’s BIOS (basic input/output system). This software gets installed on a small memory chip in your computer’s motherboard. It can even infect your router. Hackers use these rootkits to intercept data written on the disk. Because they grant control over the system at a very low level, hardware rootkits are incredibly difficult to detect and remove.
6. Kernel mode rootkits
These rootkits target the core—also known as the kernel—of your computer’s operating system, giving the attacker unauthorized privileged access and control over the system. Cybercriminals can use these kernel mode rootkits to manipulate the entire system, allowing them to override security systems and avoid detection while harvesting sensitive information.
Possible signs of a rootkit attack
Detecting a rootkit attack can be challenging since rootkits are specifically designed to stay hidden. However, several signs may indicate that a rootkit infected your system:
- Performance issues: Rootkits can consume system resources, causing a noticeable decrease in performance. Sluggishness, slow startup and shutdown times, and unresponsiveness may indicate a rootkit infection.
- Unexpected system behavior: If your system starts behaving strangely, such as frequent crashes, unexpected error messages, or unusual system restarts, it could be a sign of a rootkit attack. Rootkits may interfere with system processes, leading to unstable behavior.
- Unusual network traffic: Rootkits may establish unauthorized network connections or manipulate network traffic. If you notice excessive network activity when your system is idle or unexplained outgoing connections, it could indicate a rootkit.
- Disabled or malfunctioning security software: Rootkits often attempt to disable or bypass a system’s security measures. If your antivirus software, firewall, or other security tools stop working or behave abnormally without any obvious reason, it might be due to a rootkit.
- Hidden files or processes: Rootkits employ techniques to conceal their presence. Look for hidden files, directories, or processes that are not normally visible or suspiciously named files you don't recognize. Unusual system files or processes may be the result of a rootkit attack.
- Unexpected system modifications: Rootkits can alter system files, configurations, or registry entries to maintain persistence or hide their activities. Keep an eye out for unauthorized changes in system settings, unusual entries in the registry, or modified system files.
- Antivirus alerts or inability to update: Some antivirus software may detect rootkit activity and raise alerts. If your antivirus repeatedly detects and removes the same rootkit-related files or if you are unable to update your antivirus software, it could indicate a persistent rootkit infection.
How to remove a rootkit
If you suspect a rootkit attack, it is important to take immediate action. Here are a few general steps to take to remove a rootkit and start repairing any damage done to your system:
- Update your security software: Ensure that your antivirus software and other security tools are current. This will increase the chances of detecting and removing the rootkit.
- Boot into Safe Mode: Restart your computer and enter Safe Mode. This helps prevent the rootkit from loading during startup, making it easier to remove. To access Safe Mode, you’ll need to press a specific key (such as F8 or Shift) during the boot process.
- Perform a full system scan: Run a comprehensive scan using your antivirus software or specialized anti-rootkit tools. These tools are specifically designed to detect and remove rootkits. Try Norton Power Eraser for free to easily and quickly detect and remove malware and infected files from your system.
- Use offline scanners: If the rootkit is particularly stubborn or your regular antivirus software fails to detect it, you can try offline scanners. These antivirus tools run from a bootable USB or CD/DVD, allowing them to scan your system without the rootkit being active.
- Remove identified threats: If your security software identifies any rootkit-related files or processes, follow the instructions provided to remove or quarantine them. Be cautious and double-check that you are removing the correct files, as deleting critical system files can cause further issues.
- Repair system files: Rootkits can modify system files or configurations. Use system repair tools such as Windows’ System File Checker (SFC) or Deployment Image Servicing and Management (DISM) to scan and repair any corrupted or modified system files.
- Monitor system behavior: After removing the rootkit, closely monitor your system for any unusual activities, performance issues, or signs of reinfection. Run regular scans with updated security software to ensure your system remains clean.
Sometimes, you may need to seek help from a cybersecurity professional to fully remove the malware and restore your system. And that's where Norton Power Eraser comes in, a dedicated anti-malware tool that can help remove malware from your device.
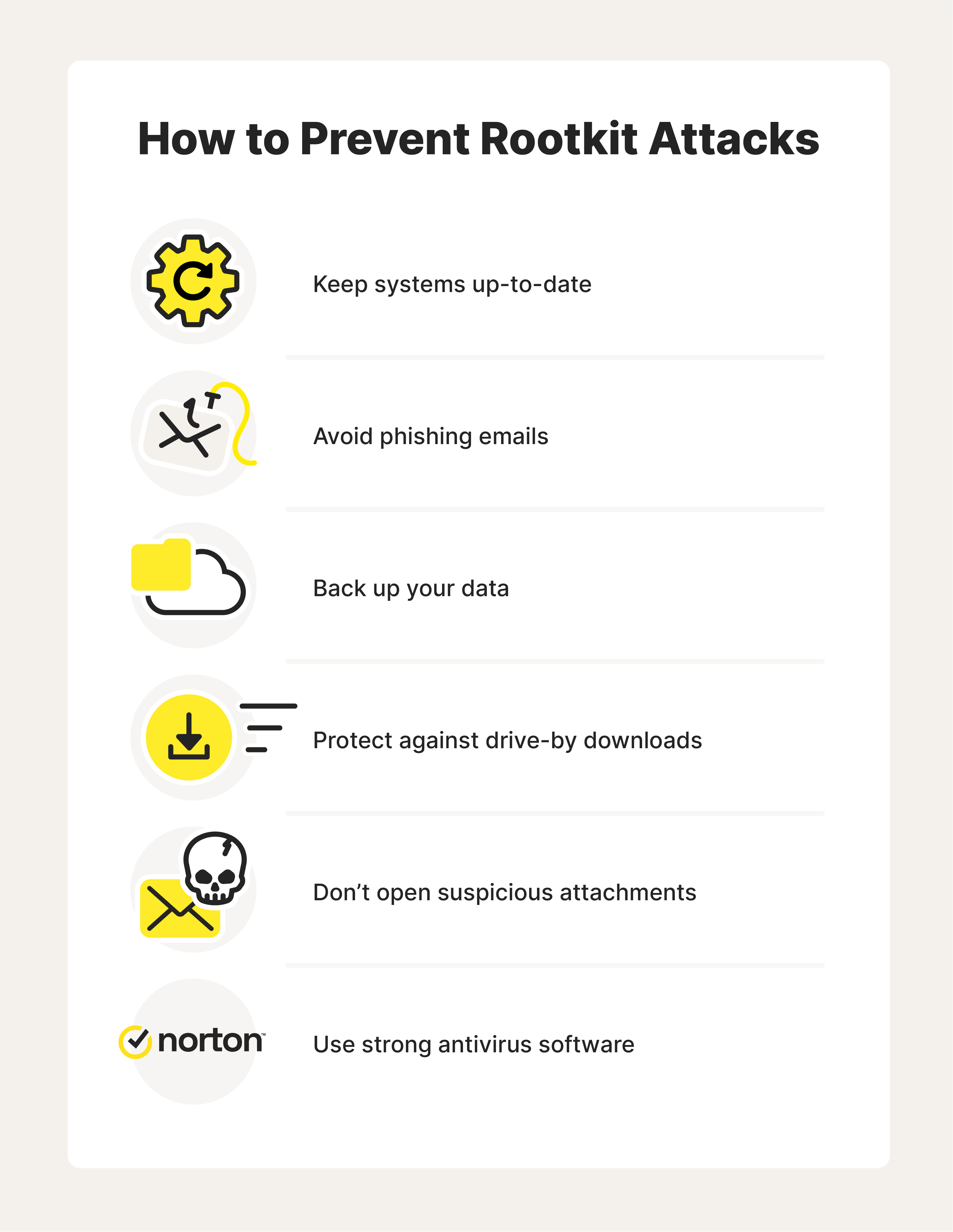
6 ways to prevent rootkits
As we mentioned before, the best defense against rootkits is consistent prevention processes. Because rootkits are dangerous and incredibly difficult to detect, it’s essential to exercise caution when surfing the internet or downloading programs.
Fortunately, you can increase your odds of avoiding these attacks by following the same cybersecurity strategies you’d take to help avoid any other malicious malware attack.
1. Keep your system and applications up-to-date
Updates to your computer’s applications and operating system can be annoying, especially when it seems like there’s a new update for you to approve every time you turn on your machine. But don't ignore these updates. Keeping your operating systems, antivirus software, and other applications updated is the best way to protect yourself from rootkits.
2. Know how to recognize phishing emails
Phishing emails are sent by scammers who want to trick you into providing them with your financial information or downloading malicious software, such as rootkits, onto your computer.
Never click on any links supposedly sent from a financial services company. If the message was sent from a company you’re unfamiliar with, delete it. If the message comes from a company you have an account with, log into your online account or call the company. If there’s a problem, it should appear on your online account or a customer service representative will confirm it.
3. Regularly back up your data
Implement a regular data backup strategy to ensure you have copies of your important files. In the event of a rootkit infection or any other security incident, having backups can help you restore your system to a clean state without losing essential documents.
4. Be wary of drive-by downloads
Drive-by downloads are especially difficult to detect. These happen when you visit a website, and malware gets automatically installed on your computer. You don’t have to click on or download anything from the site for this to happen.
The best way to help protect yourself from drive-by downloads is to approve computer software updates quickly. Set your operating system, browsers, and all applications to automatically install updates so your computer systems will always have the most up-to-date protections.
5. Don’t download files sent by people you don’t know
Be careful when opening attachments, and avoid opening an attachment from someone you don’t know. Attackers spread rootkits using viruses and Trojans tied to attachments or downloads. Only download files from trusted sources.
If you receive a suspicious email attachment, avoid opening it until your antivirus software scans it.
6. Use advanced antivirus software
Install and maintain a reliable antivirus/anti-malware program that offers real-time scanning and malware detection capabilities. Norton AntiVirus Plus is powered by AI and machine learning technology to help identify and block even the latest threats.
Rootkit examples
Whether designed by cybercriminals or large government agencies, rootkits have been one of the most dominant cybersecurity threats since the late 90s. Here are a few of the most notorious examples of rootkits:
- Rustock: Rustock is a well-known rootkit that targets Windows operating systems. It primarily focuses on infecting the Master Boot Record (MBR)—the area on a hard drive that stores the information required to start the device—and uses cover techniques to hide its presence from the operating system and security software.
- Zeus: Zeus, also known as a Zbot rootkit, primarily targets banking information. It infects systems through drive-by downloads or malicious email attachments and aims to steal sensitive financial data, such as login credentials and credit card information.
- Necurs: Necurs is a well-known rootkit primarily serving as a botnet controller. It infects systems through malicious email attachments or drive-by downloads and establishes a connection with a command and control server. Necurs has distributed various types of malware, including spam email campaigns, ransomware, and banking Trojans.
- ZeroAccess/Sirefef: ZeroAccess, also known as Sirefef, primarily targets Windows systems and is often distributed through infected websites or malicious downloads. ZeroAccess is commonly associated with click fraud activities, where it generates revenue for attackers by manipulating online advertising clicks.
- Mebroot: Mebroot infects the MBR on Windows systems. Hackers often distribute it through drive-by downloads or malicious websites. Mebroot is known for its ability to modify the MBR in a way that allows it to load before the operating system, making it difficult to detect and remove.
- Machiavelli: Machiavelli was the first rootkit to target Mac OS X operating systems in 2009. This rootkit creates hidden system calls and kernel threads, which are both used to trigger an action from the system’s core.
- Flame: Flame is another type of rootkit that attacks Windows systems. Considered one of the most complex malware ever created, flame rootkits can record audio, screenshots, keyboard strokes, and network activity. It can also spread to other systems over a local network.
Guard against rootkits with Norton 360
Good cyber hygiene can protect you against most types of malware. However, cyberthreats are evolving, and even the most cautious online users can run into traps. Rootkits are a sophisticated cyberattack, but Norton™ 360 with LifeLock™ security software tackles the challenge with real-time malware protection, website scans, and secure browsing features to help keep you and your information protected.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.






Want more?
Follow us for all the latest news, tips, and updates.