What is a pharming attack? An overview + prevention tips
Don’t let a pharming attack threaten your cybersecurity. Continue to learn the basics of pharming scams as well as tips to help keep devices protected.

Pharming is a form of online fraud involving malicious code and fraudulent websites. Cybercriminals install malicious code on your computer or server. The code automatically directs you to bogus websites without your knowledge or consent.
The goal is to get you to provide personal information, like payment card data or passwords, on the false websites. Cybercriminals could then use your personal information to commit financial fraud or identity theft.
So, how can you help protect yourself against pharming? Here’s some information and tips that can help.
How does pharming work?
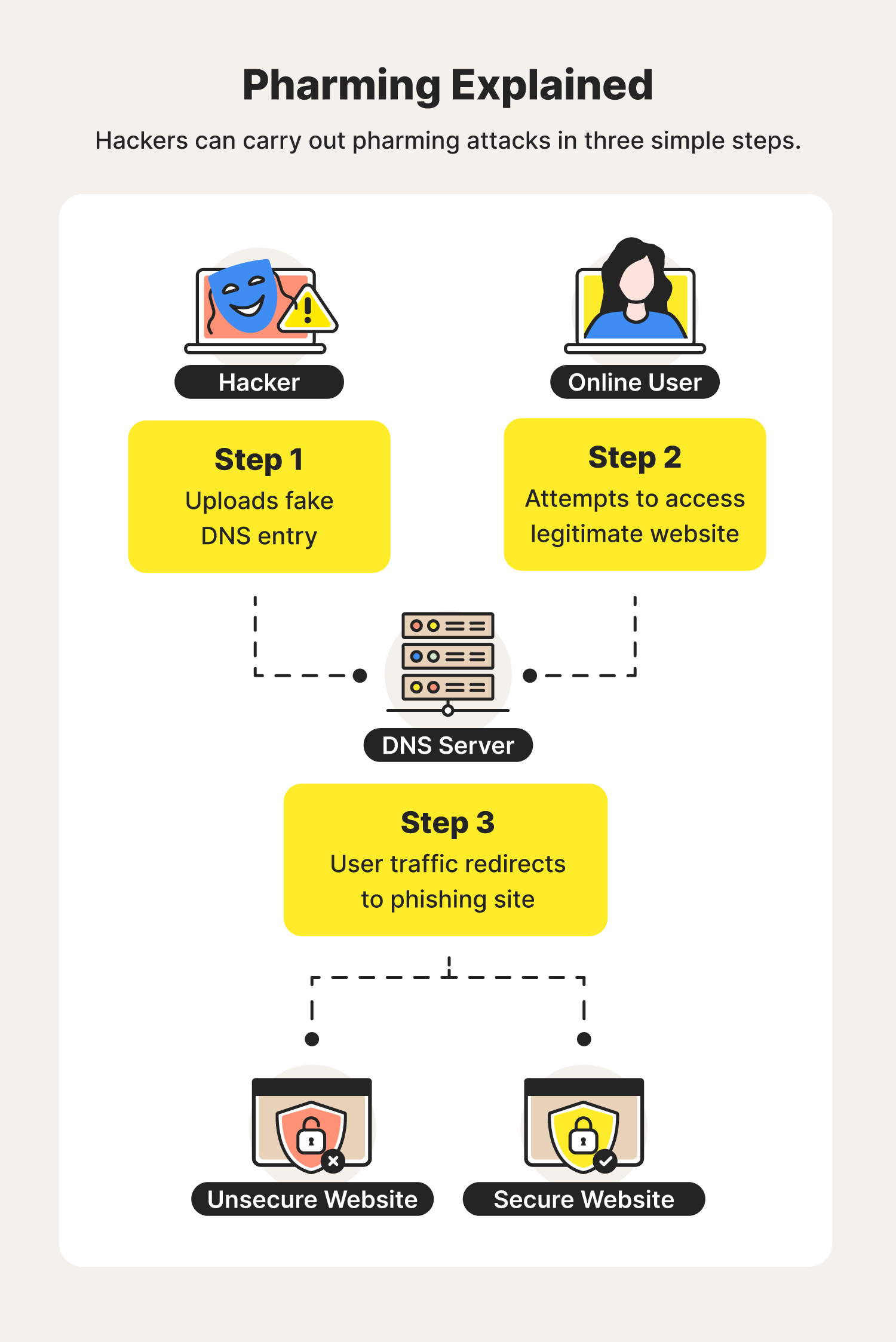
Hackers use pharming to force online users onto unsecure sites capable of tricking them into revealing personal and sensitive data.
To fully understand how pharming works, it’s important to understand how Domain Name System (DNS) servers work.
DNS servers translate domain names into IP addresses. While websites use domain names for their addresses, an IP address denotes their actual location. Your web browser then connects to the server with this IP address.
Once you visit a certain website, a DNS cache forms so you don’t have to visit the server each time you return to the site. Both the DNS cache and the DNS server can be corrupted by pharming. This can result in two types of pharming — malware-based pharming and DNS pharming.
Pharming vs. phishing
Pharming and phishing are two types of cyberattacks that are easily confused. They’re similar because they both work to trick online users into revealing personal information or steal money.
However, phishing is a hacking method that uses emails to deliver infected links that lead people to social engineering sites. Pharming, on the other hand, requires hackers to do more coding and background work to intercept online traffic and redirect targets to their malicious sites.
To help you understand the differences between the two, let’s check out the signs of each attack.
Signs of a pharming attack:
- Hard to spot
- Targets multiple people at a time
- Malicious code installed on computer
- Uses automatic redirects to lead users to malicious sites
Signs of a phishing attack:
- Easy to spot
- Targets one person at a time
- Delivers malicious emails
- Requires a manual click to trigger cyberattack
Now that you know the differences between pharming and phishing, let’s take a deeper look at the types of pharming attacks you may encounter.
Types of pharming
Here are a couple types of pharming you may run into while browsing online.
Malware-based pharming
In this case, you may pick up a Trojan or virus via a malicious email or download. The malware then covertly reroutes you to a fake site created and controlled by fraudsters when you type in your intended website address.
This type of pharming software uses malicious code sent in an email to change your computer’s local host files. These corrupted host files can then direct your computer to fraudulent sites regardless of the internet address you type.
DNS pharming
Domain Name Systems are computers on the internet that direct your website request to the right IP address. A rogue, corrupted DNS server, however, can direct network traffic to an alternate, fake IP address.
This pharming scam doesn’t rely on corrupting individual files, but rather occurs at the DNS server level by exploiting a vulnerability. The DNS table is essentially poisoned, so you’re being redirected to fraudulent websites without your knowledge.
If a large DNS server is corrupted, cybercriminals could target and scam an even larger group of victims.
Pharming attack warning signs
Pharming attacks may be stealthy, but they have signs like most other cyberattacks. Here are two signals of pharming.
- An unsecure connection. If your site address says “http” instead of “https” in the address line, the website may be corrupted.
- A website doesn’t seem right. If the site you’re on has spelling errors, unfamiliar fonts or colors, or otherwise just doesn’t seem legitimate, it may not be.
Examples of pharming attacks
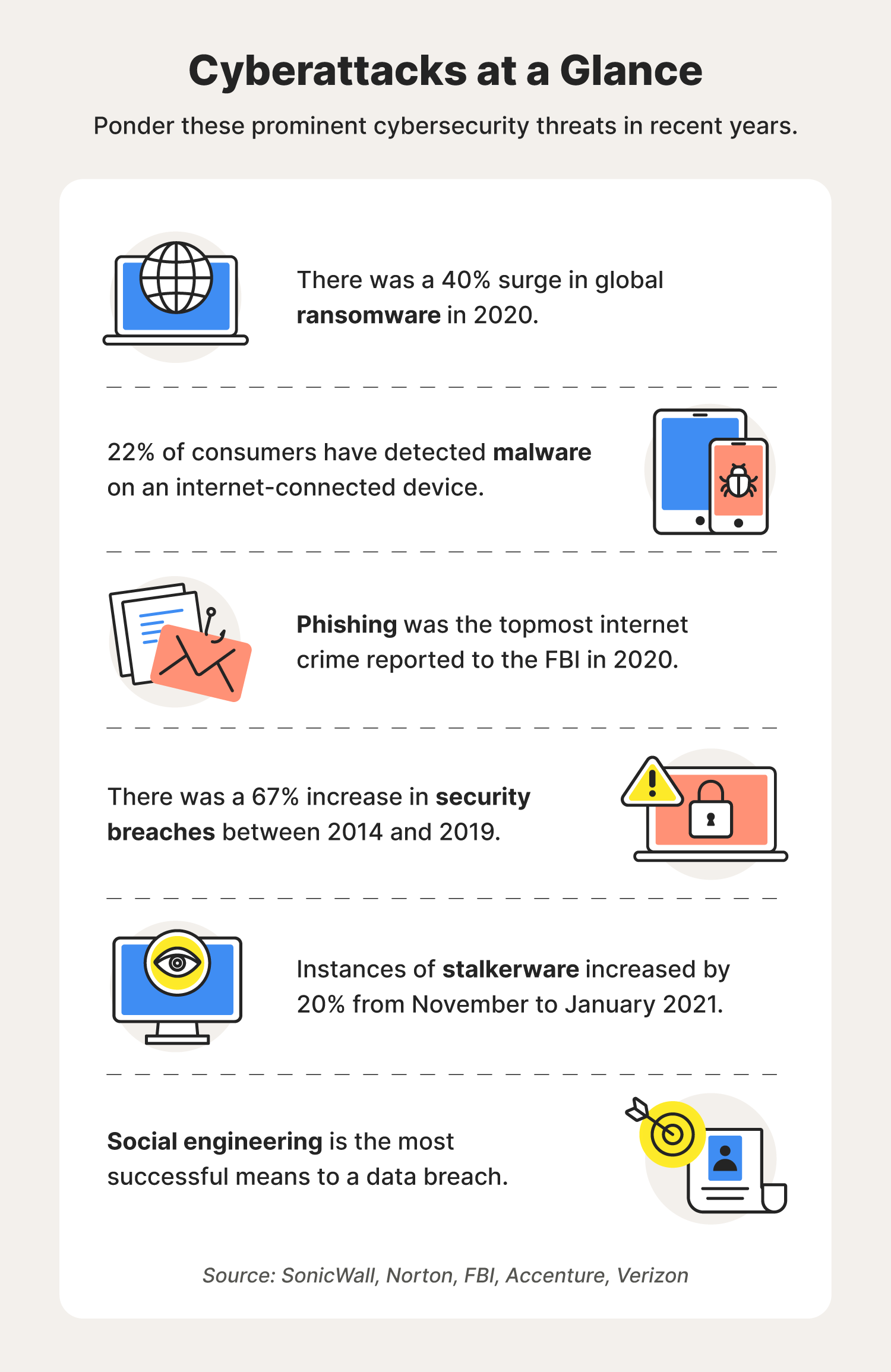
Pharming cost victims more than $50 million in 2021. Here are a couple noteworthy attacks that helped pharming get to where it is today.
- Microsoft (2007): 50 financial institutions found themselves to be the recipients of a pharming attack that exploited a Microsoft vulnerability, creating fraudulent websites that mimicked the targeted bank sites.
- Brazil (2015): A pharming attack targeting Brazilian internet users exposed security flaws in home routers to gain access to administrative network settings.
Just because hackers have a couple wins under their belt doesn’t mean you’re an easy target. There are several ways you can help keep yourself protected from pharming scams.
Pharming attack protection tips
Not all antivirus and spyware removal software can protect against pharming, so additional anti-pharming measures may be needed.
Here are some anti-pharming safeguards.
- Avoid unsecure websites (double-check URLs for typos)
- Be cautious when opening links or attachments that you weren’t expecting or that are from an unfamiliar sender
- Enable two-factor authentication on sites that offer it
- Use a reputable internet service provider whenever possible
- Use a VPN service that has reputable DNS servers
- Change the default password on routers and wireless access points
- Download reliable antivirus software
If you suspect you’re already a victim of pharming, you can try resetting your computer to reset your DNS entries. You can also turn your network on and off if using a DNS for gaming.
As these cyberattacks show, pharming could be a major threat for people using e-commerce and online banking websites.
That’s why it’s important to know about pharming and learn what you can do to help protect against it.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.