What is riskware and how to spot and avoid it
Riskware refers to legitimate software that can potentially threaten your cybersecurity. Read our guide to learn how to spot and avoid riskware.

Riskware definition
Riskware is legitimate software that has the potential to turn malicious and become a threat to your cybersecurity.
Has your device ever begun to overheat or perform slowly after downloading an app that appeared trustworthy? Even legitimate software, like riskware, has the potential to turn malicious and threaten your cybersecurity.
It’s possible to download riskware without realizing it is vulnerable to malware or violates the laws of your country.
Since riskware can take the form of trustworthy software, it can be difficult to know which programs to avoid. Read our guide to learn how to spot, remove, and prevent riskware threats.
How riskware works
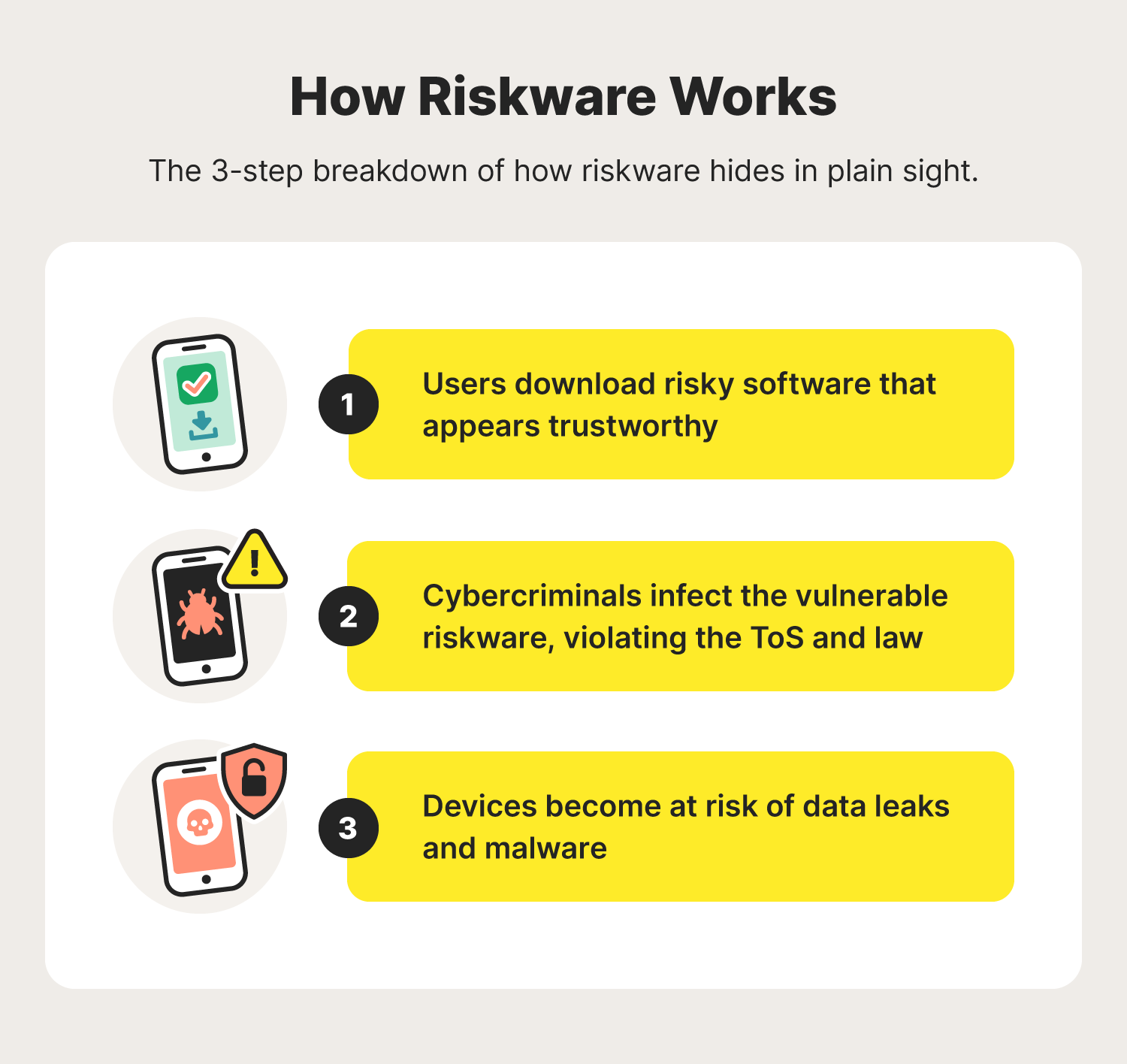
Unlike malware, riskware is not always created with malicious intent. It is sincerely legitimate software, but software that can pose a risk to devices and users, be it via tracking user activity or unknowingly abusing the privacy agreements.
For example, software at risk of violating service agreements or the law becomes identified as riskware because it can leak user data to cybercriminals. Here is a breakdown of how riskware turns malicious:
- Users download legitimate software: riskware that looks trustworthy yet features security vulnerabilities or violates privacy agreements can be downloaded at an app store and even bundled with other software.
- The software observes user activity: user data is recorded to help the software function and becomes prone to data breaches due to security vulnerabilities within the application. Cybercriminals take advantage of weak cybersecurity and can infect the user’s device and servers.
- Cybercriminals steal user data: sensitive information is now accessible to cybercriminals who can infect your device with a Trojan or virus that benefits the hacker. Your data can also be stolen and used in the form of identity theft.
Multiple types of riskware can leave your technology and sensitive information vulnerable to cyberattacks. Let’s learn how each type of riskware puts your user data at risk.
Types of riskware
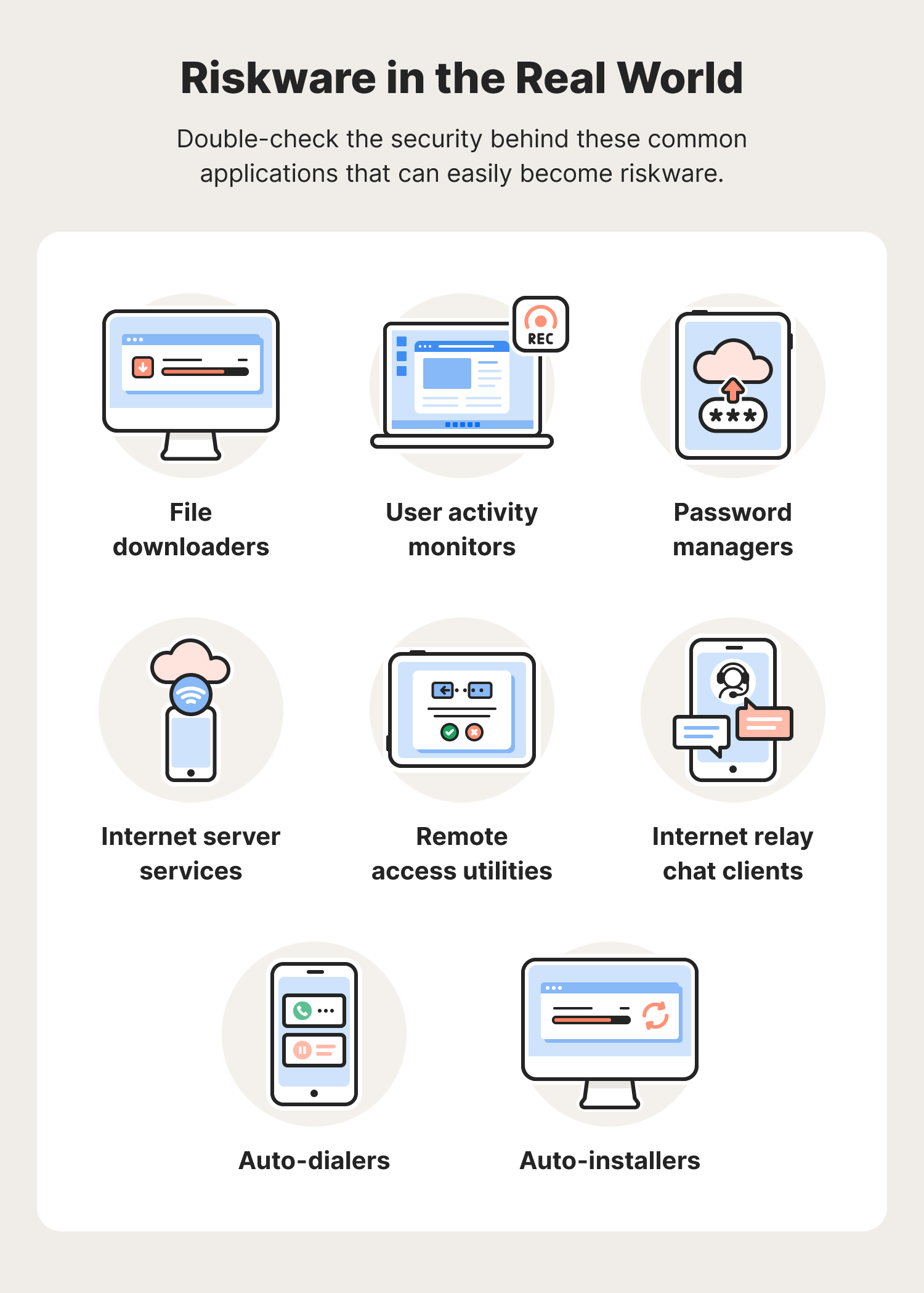
Riskware is all around us, and you have probably used at-risk software before without realizing it. There are five main types of riskware to be aware of:
- Vulnerable software
- Monitoring software
- Malware-accessible software
- ToS breaching software
- Law-violating software
Now, let’s dive into each type of riskware to understand how to spot, remove, and prevent it from threatening our cybersecurity.
Vulnerable software
Vulnerable software is an application with security loopholes or other privacy vulnerabilities that can make your data vulnerable to cybercriminals.
Shareware and other types of malware that are free to use are especially vulnerable to becoming riskware because user data and activity have the potential to be recorded and shared by an app that reaches a large user pool.
Password managers and software that connects your devices to a cloud server are examples of vulnerable software that have access to large amounts of your data, activity, and sensitive information.
Law-violating software
Law-violating software enables users to complete illegal activity on their devices. It is possible to accidentally download unlawful software so be mindful of your country’s cybersecurity laws before downloading your next app.
File downloaders, like piracy software, are examples of illegal riskware in the United States. Software that enables users to download media subjects users to criminal charges illegally.
Monitoring software
Monitoring software is any application that monitors user activity. Since more people are working from home, surveillance software that collects large amounts of user data and monitors user activity is an increasingly popular type of riskware.
An example of this type of riskware is the monitoring software that some employers use to track employee productivity. Riskware that tracks users' location online, like a map application, can also put the user’s security.
Malware-accessible software
Malware-accessible software is any software bundled with other applications that can require co-installation.
Carefully read the privacy agreements of bundled software to understand what user activity both applications will have access to. If the software begins functioning outside its privacy agreement, it might have a malware infection.
An example of malware-accessible software is an auto-installer that automatically downloads data, like stock prices, from the internet to provide real-time information.
ToS breaching software
ToS (Terms of Service) breaching is when any software attempts to ignore, change or override another application’s ToS. Doing so is also violating the law.
An example of this type of riskware is a remote access utility that allows users to access data or information they are not authorized to in their country.
How to spot riskware …

A Potentially Unwanted App (PUA) like malware-accessible riskware can be bundled with desirable applications and remain hidden during the installation process, making the risky software difficult to spot.
Be aware of these riskware warning signs:
- You didn’t download the software: This is an example of riskware that may have come bundled with other software without your permission while installing.
- Your device begins to perform slowly: Getting infected with a virus or Trojan soon after downloading an application potentially means the software has turned malicious.
- The software is accessing files it shouldn’t: If the software can access user data and activity outside of its functions, it might be riskware.
- The software is rarely updated: Application updates help keep software protected from the latest cybersecurity threats. Outdated software is at risk of becoming infected by malware.
- You're enabled to perform illegal activities: Software that allows users to engage in illegal activity is subjecting them to legal consequences.
- The software breaches the ToS: If not, you may receive notifications regarding your privacy settings or application incompatibility.
Answering these questions can help you identify riskware before downloading it and is the first step in removing current software that is putting your cybersecurity at risk.
How to remove riskware
If you suspect that riskware has turned malicious, proceed with caution. Follow this three-step strategy when removing riskware:
- Uninstall the software immediately: don’t allow the at-risk software to inflict any more damage or leave your data vulnerable to cybercrime.
- Run an effective antivirus program: enabling antivirus software can help you detect, remove and prevent riskware from threatening your cybersecurity. A trusted security software like Norton 360 Deluxe can help protect your devices and online privacy.
- Follow riskware prevention tips: take a proactive approach to combat riskware by having impeccable cyber hygiene.
Although riskware can be difficult to spot, users can quickly remove or potentially prevent it altogether.
How to prevent riskware
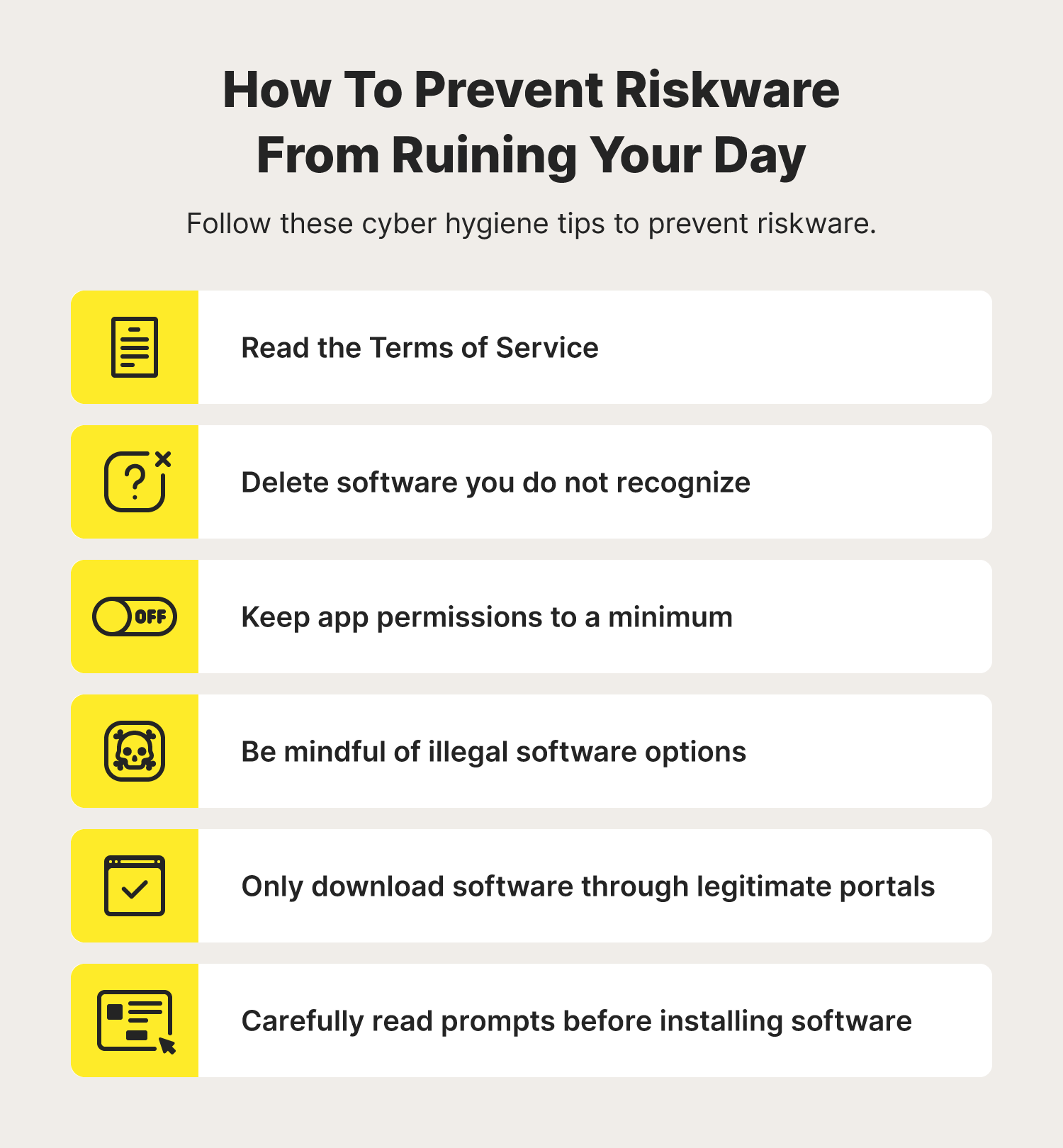
Preventing riskware requires users to follow the latest cybersecurity practices. Here are proactive prevention tips to prevent interactions with riskware:
- Read the Terms of Service
- Keep app permissions to a minimum
- Only download apps through official stores
- Be mindful of illegal software options
- Delete software you do not recognize
- Carefully read prompts before installing apps
Since malware is always taking new forms, having a firm grasp of cybercrime techniques like malvertising is also important.
Learn how to enhance your privacy online to take a stance toward malware, riskware, and cybercriminals who want access to your sensitive information.
Riskware FAQs
Still have riskware questions? We’ve got answers.
What does riskware do?
Riskware can make your device and servers vulnerable to malware infections.
What does riskware detected mean?
Riskware detected means that a risk assessment software has detected an application that threatens your cybersecurity.
What is adware and riskware?
Riskware that bombards your device with advertisements is known as adware. The advertisements can take the form of pop-ups or hidden windows.
How do I remove riskware from my Android?
To remove riskware from your Android device, uninstall the application and follow any instructions from the developer on how to successfully uninstall the app.
What is riskware generic?
Riskware generic and riskware injector generic are terms that describe potentially risky or unsafe risk management software.

Help protect your digital life on your devices.
Are you afraid of losing your personal information or all the precious things on your computer? Get comprehensive protection with Norton Security Deluxe across all your devices – up to 5 PCs, Macs, smartphones or tablets.
Create an account today and try it free for 30 days on up to 5 of your devices.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.




Want more?
Follow us for all the latest news, tips, and updates.