What is a computer worm? How they work and spread
If your computer is acting strangely or suddenly suffering from poor performance, it could be infected with a computer worm. Learn more about worms, the damage they can cause, and how you can detect them. Then, get Norton 360 for sophisticated built-in protection against computer worms and other forms of malware.

Despite the mild-sounding name, computer worms are a serious digital security threat. This type of malware originated as an experiment gone wrong but has since evolved into a dangerous tool in the arsenal of hackers and cybercriminals across the globe.
Read on to learn about the dangers of computer worms and how you can help keep your devices and data safe in the modern digital landscape.
Computer worm definition
A computer worm is a type of malware that can self-replicate, spreading copies of itself throughout a device or across a network without human interaction. They’re standalone programs, which means, unlike viruses, they don’t need to be attached to or hidden within another program or file to cause damage.
Computer worms can get access to devices through software backdoors, network vulnerabilities, email attachments, file transfers, or malicious links hidden in unwanted pop-up ads. Once installed on a device, they aim to propagate — infecting local programs and other devices on the network.
Worms consume system resources and network bandwidth in this process, often leading to computer errors and performance issues. They can also cause more serious damage, including modifying, deleting, or corrupting files and installing backdoors that allow hackers to steal sensitive data.
Computer worms vs viruses vs Trojans
Computer worms, viruses, and Trojan horses are all forms of malware that pose a risk to device and network security. However, they work slightly differently:
- Viruses are attached to “carrier” programs or files and remain inactive until a user interacts with them. They can only spread across a device or network if a human opens or shares the infected program or file.
- Computer worms function completely independently, with no need for a “carrier.” They can also self-replicate, spreading across local applications or other devices on a network without human activation.
- Trojan horses are disguised as legitimate programs or files, with cybercriminals using social engineering tactics to trick users into downloading or opening them. They don’t self-replicate but can steal data or create backdoors.
How do computer worms work and spread?
Computer worms install themselves on devices and automatically self-replicate to infect as many systems as possible, including the host device and other devices on the same network.
Worms are initially transmitted like any type of malware, including through email attachments, unsecured networks, and file download links on instant messaging apps or malicious websites. Once installed on a device, worms begin replicating, relying on network and system vulnerabilities to spread faster than users can react.
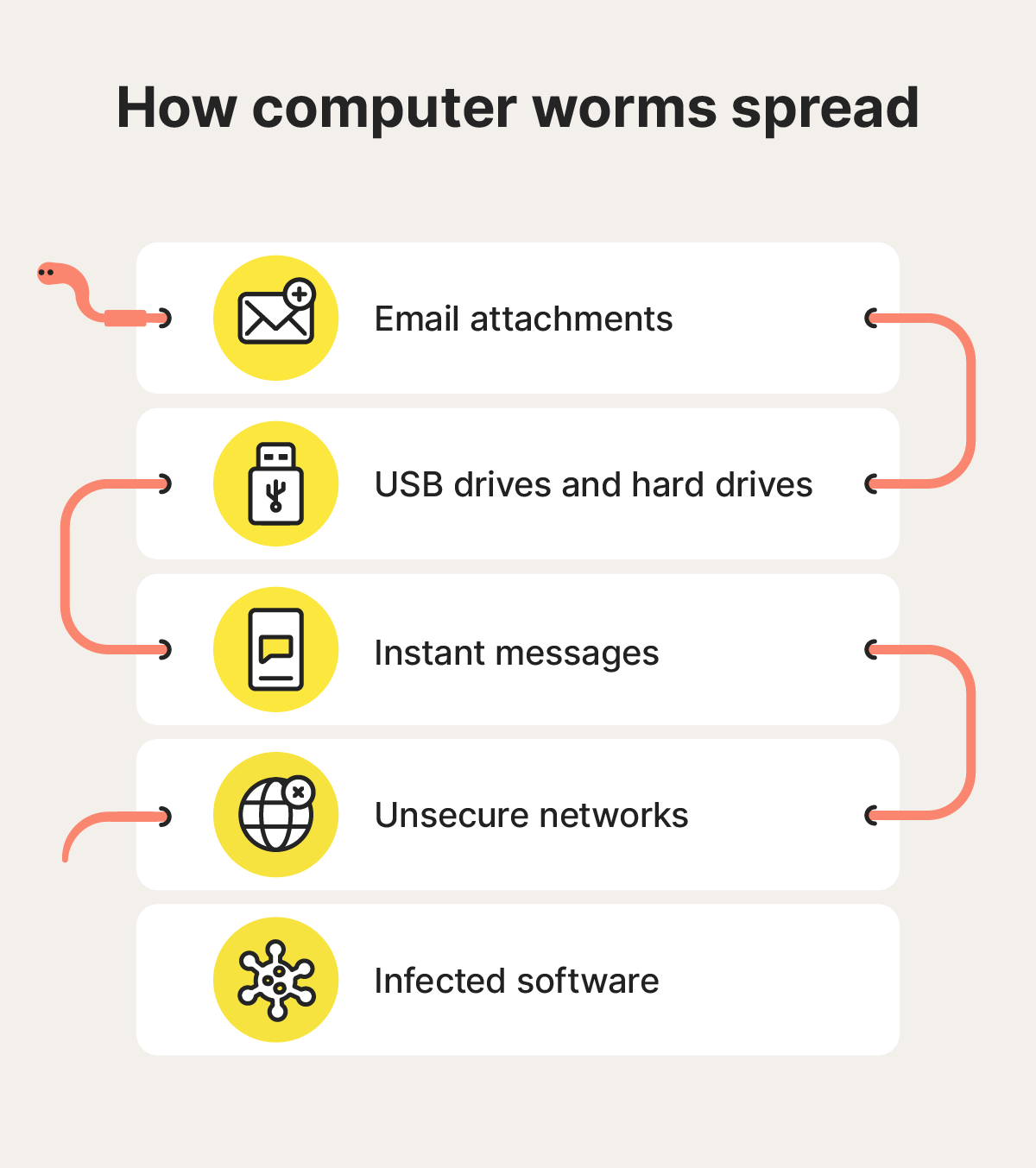
Here’s a more detailed breakdown of some of the most common ways computer worms can reach a device:
- Email attachments: Cybercriminals use phishing emails to spread worms, sending legitimate-looking messages that prompt recipients to click a malicious link or download an attachment.
- USB drives and hard drives: Compromised external storage devices can house computer worms that infect any device they connect to.
- Instant messages: Seemingly innocuous messages sent via SMS or instant messaging platforms can spread computer worms, through attachments or links.
- Unsecured networks: Worms can spread through unsecured networks or cloud storage servers, making anyone using them vulnerable to infection.
- Infected software: Computer worms can be installed on devices using compromised programs that contain backdoors or malicious hidden code, activating when a user downloads or opens the software.

Worms try to survive for as long as possible by spreading across local files and networked devices. As they continue to replicate, it gets increasingly difficult for users to stop the spread and protect their files or data.
During their spread, computer worms can cause all sorts of damage, including:
- Modifying and deleting files: Worms spread by infecting different files and programs on a computer. If they reach critical system files, they can cause performance issues, crashes, and system failures.
- Injecting malicious software: Some computer worms contain malicious code that can linger on infected devices, collecting personal information or granting hackers backdoor access that allows them to access devices remotely.
- Depleting system resources: A computer worm that’s left to replicate can quickly clog storage and slow down infected devices. It can also consume bandwidth as it transmits through a network, causing internet issues.
Computer worm examples
Over the years, several notorious computer worms have impacted devices worldwide. Understanding how these computer worms worked and what damage they caused can help you build your own defenses.
Some of the most famous examples of computer worms include:
- Morris Worm: Released in 1988, the Morris Worm was dubbed the “first major attack on the internet” by the FBI. It was created as an experiment by a Cornell University student but spiraled out of control, spreading to 6,000 computers in 24 hours.
- Code Red: Code Red was a computer worm that infected over 300,000 devices in 2001. It exploited computers running Microsoft IIS (Internet Information System) servers, overloading even the White House website with traffic from infected machines.
- Love Bug: This famously far-reaching computer worm from 2000 spread through emails with the subject line “ILOVEYOU.” It overwrote files on each computer it infected and then auto-sent itself to new victims via email, causing estimated damages of up to $10 billion.
- Conficker: First detected in 2008 but still infecting devices today, Conficker is one of the most widely spread computer worms in history. Also known as Downup, Downadup, and Kido, it exploits flaws in the Windows operating system.
How to tell if your computer has a worm
The key warning signs that your computer might be infected by a worm include your hard drive space being filled unexpectedly, your computer slowing down, or files randomly appearing or disappearing.
Here’s a more detailed explanation of how to tell if your computer has a worm:
- Less hard drive space: As worms self-replicate, they take up more storage space on your computer. If your hard drive is filling up unexpectedly, a computer worm could be the reason.
- Sluggish performance: Worms use up system resources as they spread, which can result in decreased device performance. You can check what processes are using resources, looking out for unusually high usage from an unrecognized program.
- Suspicious file changes: Worms can create malicious files and modify or delete existing files as they spread through your system. If you notice suspicious file changes that you don’t remember making, it could be a sign of a computer worm.
- Firewall warnings: Worms will often compromise or completely turn off your firewall to allow backdoors to work. Check your firewall settings for recently added ports or configuration changes that might be allowing hackers to access your device.
- Unusual computer behavior: The spread of a computer worm can cause your device to act strangely, including prompting programs to open or close themselves.
If you notice any of these signs, run a malware scan as soon as you can to check for a computer worm or other type of malware.
How to remove computer worms
To remove a computer worm from your device manually, you need to find and delete the malicious file. However, sophisticated malware can be hidden from view, making it difficult to track down.
Security software can help you detect and remove hidden malware, including computer worms. After you run a malware scan that identifies a malicious program or file, anti-malware software can delete it from your device, stopping it from spreading further.
Norton 360 Standard provides real-time, multi-layered malware protection for up to three Windows PCs, Macs, or mobile devices. Use it to get help identifying and eliminating existing computer worms and keep yourself better protected in the future.
How to protect against computer worms
Best practices for protecting your devices against computer worms include using strong security software, keeping your systems and programs updated, and taking cybersecurity precautions online.
Here are some details on how you can stay safer from the threat of computer worms:
- Use strong cybersecurity software: Anti-malware and security software like Norton 360 Standard can help detect and automatically remove computer worms, viruses, and Trojans, giving your device proactive protection.
- Keep your systems and applications updated: Software vulnerabilities are major infection vectors for computer worms. Downloading the latest version of your operating system and installing updates or patches for individual programs can keep you more secure.
- Be wary of unsolicited emails: Cybercriminals often use emails to spread attachments containing computer worms and other forms of malware. Be cautious when opening unexpected or suspicious emails and scan attachments for malware before downloading them.
- Refrain from clicking pop-up ads: Pop-up ads containing malicious links can prompt computer worm downloads. Refraining from clicking pop-up ads while browsing the web can help keep you safer from malware.
- Only download from trusted sites: Unsafe websites and file-sharing platforms can host malicious files. Before downloading software or files, make sure you trust the source. Searching “is X site legit” can help you get insights from other users.
Get Norton for computer worm protection
Norton 360 Standard can help you identify computer worms, spyware, viruses, and other malware. It helps you automatically detect and remove malicious programs and files and offers powerful security to protect against future infection.
Best of all, it works quickly and proactively, helping you stay one step ahead of computer worms to help prevent them from spreading out of control.
FAQs
Are computer worms still around?
Yes, computer worms still exist. Both old worms that are still active and new worms created to facilitate cyberattacks pose a risk to devices and networks worldwide.
Can computer worms be removed?
Computer worms can be removed manually or using dedicated anti-malware or cybersecurity software. If not detected quickly, worms can cause significant damage by overwriting files and clogging storage systems.
What are worm cybersecurity best practices?
The most important methods of protecting your device against computer worms include:
- Using strong cybersecurity software
- Keeping your operating systems and applications updated
- Being cautious with unsolicited emails or attachments
- Refraining from clicking pop-up ads
What is the most famous computer worm?
ILOVEYOU is one of the most famous computer worms due to its novel delivery method and the widespread havoc it caused, infecting millions of devices worldwide.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.









Want more?
Follow us for all the latest news, tips, and updates.