What is swatting? Examples and prevention tips
Imagine a SWAT team storming your home because someone made a false or malicious report. Terrifying, right? Aside from the trauma and possible reputational damage, this supposed prank can turn deadly fast. Discover more about swatting and ways to help protect yourself, including using Norton 360 with LifeLock to hide your IP address and help remove personal information from the web.

Swatting meaning
Swatting is a form of harassment where someone makes a false or malicious report to emergency services, leading to a police SWAT (special weapons and tactics) team or other law enforcement response at the victim's location. Common scenarios reported in swatting hoaxes include:
- Hostage situations
- Stabbings
- Active shooter threats
- Bomb threats
- Murders
- Imminent self-harm
- Hazardous material threats
Is swatting illegal?
Swatting is always illegal because it involves false emergency reporting—a misdemeanor in most states. Under some U.S. state and federal laws, swatting can also be prosecuted as a felony.
While some pranksters may consider swatting a “joke,” it can result in injury, trauma, or even death. Those found guilty of swatting can face stiff legal penalties, including fines or prison time.
How does swatting work?
Swatting occurs when a hoaxer gathers information about their intended target, calls 911, and makes a false, urgent report. If the caller sounds credible and describes a dangerous scenario, dispatch may send a SWAT team to the target’s location, leading to a potentially traumatic and dangerous interaction with the victim.
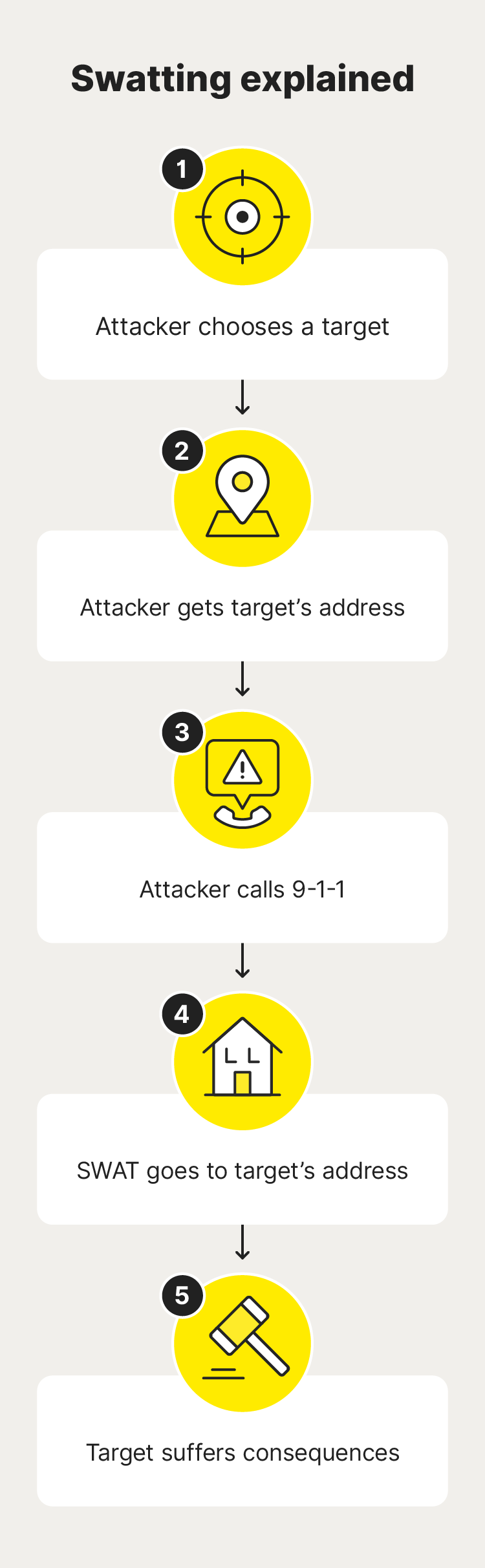

Here's a breakdown of how a swatting incident typically plays out:
- Target selection: The attacker chooses a target, often a public figure or someone they dislike, depending on their motivation.
- Information collection: The attacker gathers personal details about their target, like their address, often sourced from social media or public records.
- False report: The attacker calls the police, claiming there’s a serious threat at the target's location.
- SWAT response: The police dispatch a SWAT team, or other armed law enforcement units, to the scene.
- Fallout: Police or tactical units enter the target’s home to confront the alleged threat, and the situation can get out of control quickly.
How do swatters get your information?
Swatters can obtain victims’ information through social engineering, public records, people-search sites, data breaches, and other technical means. They may impersonate trusted sources to trick people into revealing personal details, find information leaked online, or piece together data from social media profiles.
Here’s a closer look at the main ways swatters gather information on their victims:
Location services
Location-sharing services like Life360, Find My, and Snapchat’s Snap Map provide real-time updates on your whereabouts. If you make this information public or share it with the wrong person, a swatter can track your movements and figure out where you live.
- Tip: Share your location only with trusted family and friends to reduce swatting risks.
Oversharing
Oversharing online can aid potential swatters and cybercriminals, as seemingly innocuous acts such as posting an event address, using check-in features, or even taking selfies near your home, can reveal personal details and help pinpoint your location.
- Tip: Use strict social media privacy settings, accept friend requests only from people you know, and avoid sharing photos that might reveal your location.
IP addresses
While it can’t give away your exact address, cyber snoops can narrow down your physical location if they know your IP address. When you connect to the internet, your device is assigned a unique IP address; geolocation databases link these IP addresses to approximate physical locations.
- Tip: Use a Norton VPN, which encrypts your internet connection and routes your data through a secure, remote server, to mask your IP address and help safeguard sensitive information.
Public records
Public records like tax and voter registration documentation can allow swatters to find personal information about their targets, including their legal name, home address, and phone number.
- Tip: Contact your local public records office to see if your address can be redacted; the availability of this option varies by county and state.
Online databases
Online databases and people search sites can contain extensive personal information including addresses, phone numbers, and family member details, making it easy for anyone with internet access to leverage this data for a swatting attack.
- Tip: Wherever possible, opt out of people-search sites to minimize how much of your personal information lives online.
Why do people swat others?
People typically swat others as a form of harassment, revenge, or intimidation. Motivated by grudges, online disputes, or attempts to gain notoriety, swatters intend to frighten their victim and cause maximum disruption to their home life.
Here are some of the most common reasons swatters call in fake threats:
- Revenge: Swatting can be a form of retaliation against someone the attacker dislikes or feels wronged by.
- Intimidation: The goal may be to scare or intimidate the target, causing them to feel unsafe or uncomfortable.
- Thrill-seeking: Some individuals may like the adrenaline rush that comes with causing chaos in someone’s life.
- Attention-seeking: Swatting can be a way to gain attention or notoriety, especially if the incident is widely reported in the media.
- Mental health issues: In some cases, the wrongdoer may have a mental health condition that contributes to their behavior.
People who’ve been Swatted
Celebrities, influencers, and politicians tend to have lots of personal details online, which can make them easier targets to swat. But swatting can happen to anyone. Some big names that have been swatted include:
- Chris Brown
- Lil Wayne
- Justin Bieber
- Miley Cyrus
- Nicki Minaj
- Rihanna
Here’s a closer look at some folks who were targeted in swatting attacks over the past year.
Mayor Michelle Wu
Status: Politician
Date swatted: 2023
Michelle Wu was the first woman and person of color to serve as Mayor of Boston. Since she was elected in 2021, she has been subject to multiple swatting calls.
Most recently, her home was swatted on Christmas after a man called 911 reporting that he had shot his wife at the address. This resulted in police and EMS showing up on her doorstep.
Jack Doherty
Status: Influencer
Date swatted: Multiple occasions
Jack Doherty is a YouTuber known for sharing footage of controversial stunts and interactions. And for getting swatted—a lot.
One incident in 2024 led to police responding to a swatting call about a shooting at the YouTuber’s home. And according to Doherty, that’s just the tip of the iceberg. One week, he claims he was swatted every day.
JoJo Siwa
Status: Celebrity
Date swatted: 2021 and 2024
JoJo Siwa—a dancer, singer, and reality TV star—was first swatted in 2021. The performer suggested that journalists may have made the call in hopes of smoking her out of her house for a photo op after she came out.
Three years later, she was swatted again after releasing her album “Karma.”
How to prevent swatting
Although there’s no surefire way to prevent a swatting attack, there are ways to reduce the risk by limiting the exposure of personal information that could be used to identify and locate you.
Following cybersecurity best practices—including limiting the sharing of private information online, using two-factor authentication, and securing your online connection with a VPN—can help minimize information exposure and protect against doxxing, making it more difficult for criminals to carry out swatting attacks.
Here’s how to proactively protect against swatting:
- Avoid posting details about your daily routine online.
- Turn off location services on your devices.
- Don’t use social media check-in features.
- Wait to review your accommodations until after you leave.
- Strengthen your device and app privacy settings wherever possible.
- Use a VPN to help mask your physical location.
- Use a dark web monitoring tool to help know if your personal info has been leaked.
If you’ve received specific threats, or suspect that you may be a potential swatting target, inform your local police department immediately and request that your address be flagged as a possible swatting target.
What to do if you get swatted
If you get swatted, try to stay calm, keep your hands visible, and avoid any sudden or unexpected movements. Follow police instructions carefully, and answer their questions clearly to help avoid escalation. After the situation has been defused, collect evidence and make a police report.
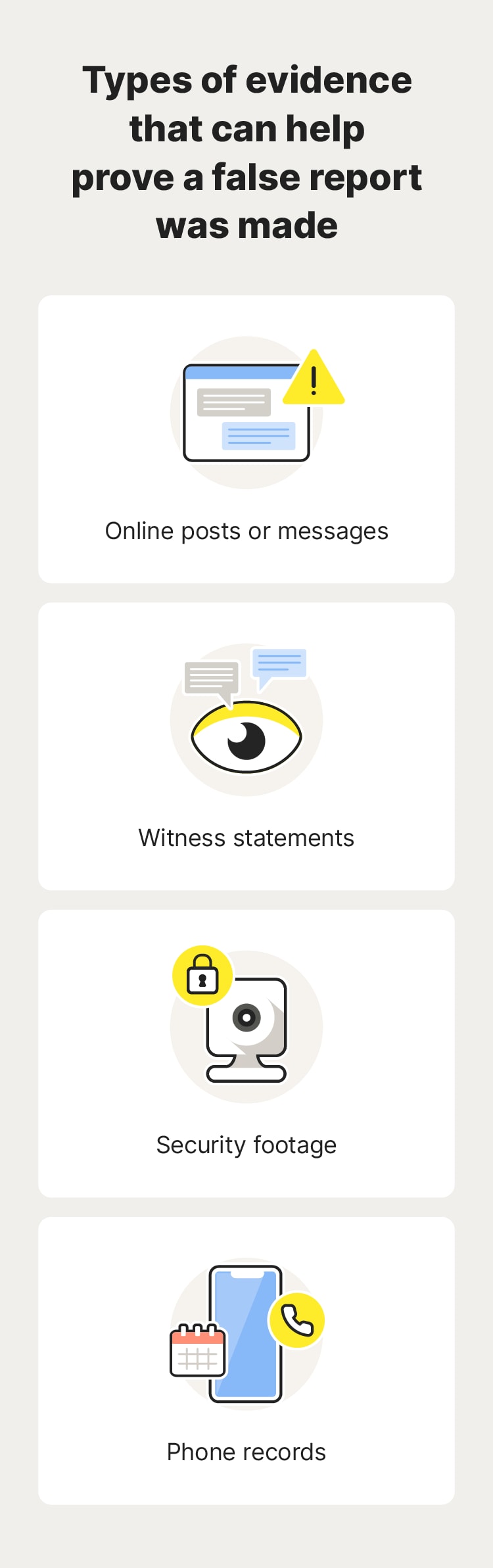

Here’s a more detailed look at what to do if you’re swatted:
- Stay calm and collected: Avoid reaching, running, and sudden movements. Follow police instructions to help establish that you’re not a threat.
- Verify the warrant: If the police have a warrant (they may not, due to the “exigent circumstances” exception) ask to see it to ensure it’s valid; look for the judge’s signature, the date issued, and the specific reason for the search.
- Collect evidence: Gather information that can help prove someone made a false report; this can include online posts and messages, witness statements, security footage, and phone records.
- Report the incident: After your home is cleared, file a police report at the station. Once you do this, the police can open an investigation and potentially find the person responsible.
Help prevent misuse of your personal information
To help protect your privacy and identity, and stay one step ahead of bad actors, you need a tool that combines device-specific security features with powerful identity-protection capabilities.
Norton™ 360 with LifeLock™ Select packs powerful tools to help protect against hackers, encrypt your online connection, and notify you of potential data breaches involving your personal information. And with the built-in Privacy Monitor will help you remove personal information from people-search sites. Plus, if your identity is ever stolen, expert U.S.-based restoration specialists are standing by to help you recover.
§Monitoring not available in all countries and varies based on region.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.