What is wardriving and how can you protect your network?
Imagine someone prowling your neighborhood, not checking for unlocked cars, but hunting for unsecured Wi-Fi networks. This practice, known as wardriving, can allow hackers to infiltrate your home network and connected devices, putting you at risk of malware, identity theft, and worse. Learn how to protect yourself and how a VPN can help secure your connection.

Failing to secure your home network is like leaving your door unlocked at night. And research indicates that up to 70% of Wi-Fi passwords are easy prey for wardrivers, leaving sensitive data and devices vulnerable to unauthorized access. Read on to discover what wardriving is, how it works, and, most importantly, how to protect your network.
Wardriving meaning
Wardriving is the practice of actively searching for and mapping Wi-Fi networks while traveling through neighborhoods or public areas using a GPS-enabled device and wireless scanning tools. Wardrivers often use laptops, smartphones, or specially equipped vehicles to detect and log Wi-Fi signals.
While some wardrivers engage in wardriving for legitimate reasons, like research or mapping, others are aiming to find unsecured networks they can exploit to steal sensitive data, compromise connected devices, or launch cyberattacks.
How does wardriving work?
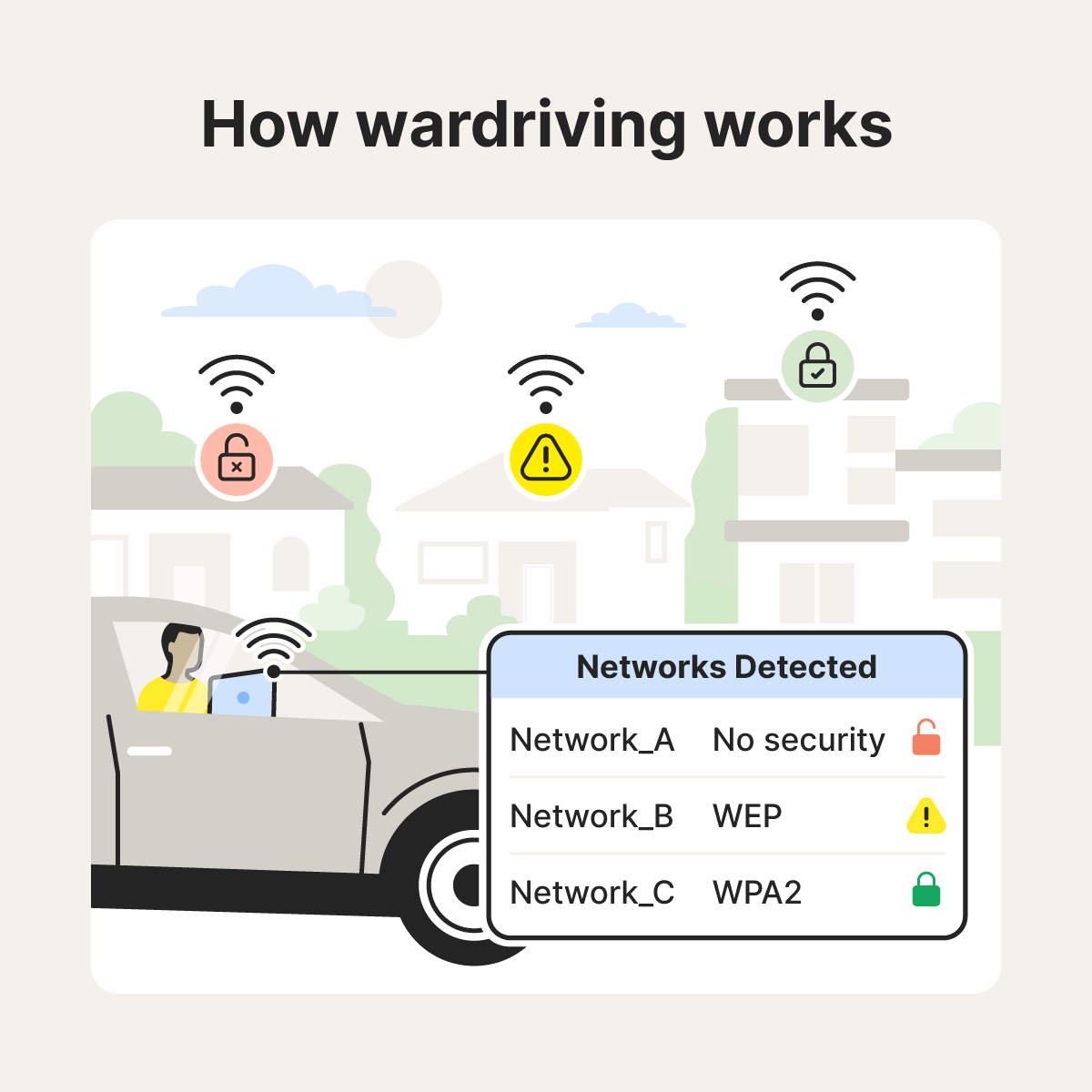
Wardriving involves using specialized software, wireless scanners, and GPS-enabled devices to find and log unsecured or poorly secured Wi-Fi networks. Once vulnerable networks are identified, attackers can exploit them to gain unauthorized access, infiltrate connected devices, and steal sensitive data.
Here’s a closer look at how this process works:
1. Wardrivers acquire equipment
Wardrivers rely on a range of equipment to scan and map Wi-Fi networks. A software suite, including traffic analyzers, packet sniffers, and signal-strength testers, helps them identify and catalog nearby networks. Specialized antennas improve their ability to detect Wi-Fi signals, typically operating on the common 2.4 GHz and 5 GHz frequencies.
For mapping vulnerable networks, they often use GPS-enabled devices, sometimes integrating tools like a Raspberry Pi with GPS modules to track and log the exact location of Wi-Fi signals.
2. Wardrivers scan for Wi-Fi
Wardrivers cruise through neighborhoods and business districts, running hardware and software tools to actively scan for Wi-Fi signals. Their tools capture network names, signal strength, and wireless security protocols, flagging vulnerable connections. This process helps them pinpoint unsecured or poorly protected routers that criminals can exploit to access a network.
3. Wardrivers collect and map data
Using a connected GPS device, wardrivers track their location in real-time as they scan for networks. This allows them to map out exactly where each network is located, helping them record areas with unsecured or weakly protected Wi-Fi connections that could be exploited.
4. Wardrivers exploit networks
Not all wardrivers use their findings for harmful purposes, but some take the next step and attempt to access open or weakly protected networks. If they’re able to get access, these malicious wardrivers may intercept unencrypted data, install malware, or hijack devices connected to the network. Networks using outdated protocols like WEP are especially vulnerable.

Is wardriving illegal?
Wardriving itself isn’t illegal — simply driving around and scanning for Wi-Fi networks doesn’t break the law. However, it becomes illegal when wardrivers exploit network vulnerabilities to access private networks without authorization, intercept personal data, or distribute malware. Such actions violate laws against unauthorized access, wiretapping, and data theft.
Here are some of the legal and illegal reasons someone may engage in wardriving:
- Ethical hacking: Security researchers may use wardriving techniques to identify network vulnerabilities with permission, helping businesses or individuals strengthen their cybersecurity. This is a form of ethical hacking.
- Mapping wireless networks: Some wardrivers map wireless networks for research or educational purposes, compiling data on signal strength, coverage areas, and encryption types.
- Homebrew applications and games: Tech enthusiasts or developers sometimes use wardriving setups to test location-based features in apps or games they’ve created, particularly those that rely on Wi-Fi signal detection.
- Cyberattacks: Malicious actors may wardrive to locate unprotected networks they can illegally exploit to steal data, install malware, or launch further attacks.
Consequences of a wardriving attack
A wardriving attack can expose your home network to hackers, who may steal sensitive data, install malware, or gain control of your connected devices. This can lead to privacy breaches, financial losses, and identity theft.
Here's a closer look at the consequences of a wardriving attack:
- Network manipulation: Infiltrators could tamper with your network’s settings, opening further vulnerabilities or redirecting your traffic to malicious sites.
- Malware infections: Once a wardriver accesses your network, they might inject malware into your devices. This can lead to data loss, system corruption, and ongoing network vulnerabilities.
- Data interception: Wardrivers can monitor your network traffic, capturing sensitive information such as login credentials, emails, and financial details if data isn’t properly encrypted in transit.
- Identity theft: With access to your personal information, wardrivers may be able to steal your identity to open credit lines or commit other types of fraud in your name.
- Bandwidth theft: Attackers may hijack your network, using your internet connection for their activities. This can slow your internet, use up your data allowance, and potentially result in unexpected charges on your account.
- Legal liability: If a hacker uses your unsecured network to commit illegal acts, you could be held responsible or investigated for activity that wasn’t yours.
How to protect your network against a wardriving attack
Although there’s no way to prevent wardrivers from prowling your neighborhood, you can upgrade your wireless security to limit your vulnerability. Key steps include using the highest level of encryption available on your router, choosing a strong network password, and getting a VPN to help protect your internet data.
Use these strategies to help secure your home network and reduce the risk of malicious wardrivers gaining access:
- Turn off your wireless router when away: This prevents unwelcome outsiders, including wardrivers, from discovering and exploiting your network.
- Use the highest level of encryption: Choose a router that supports WPA2 or WPA3 encryption, and make sure access is restricted by strong, unique passwords.
- Change the default admin login: Update the default administrative username and password on your router. Default credentials are easy for hackers to find online.
- Review your network settings: Regularly update your router’s firmware with the latest security patches to close vulnerabilities that hackers could exploit.
- Use a VPN: A VPN encrypts your internet traffic, making it much harder for wardrivers to intercept your data, even if they manage to access your network.
- Configure a smart firewall: A firewall provides an extra layer of protection by monitoring network communications and blocking unauthorized users from getting in.
Protect your data from malicious wardrivers
Wardriving poses serious risks to your network, connected devices, and personal data. To protect yourself from Wi-Fi hackers and other online snoops, secure your network and use Norton VPN. With ultra-secure AES-256 encryption and advanced IP masking, Norton VPN makes it nearly impossible for anyone to intercept or monitor your online activity. Take the next step to strengthen your privacy and security today.
FAQs
What is an example of wardriving?
In 2025, two Cedar Rapids high school seniors went wardriving out of curiosity, using a desktop, high-powered antenna, and Wi-Fi scanning software. In 10 minutes, they found over 20 wireless networks, showing how easily unsecured networks can be discovered.
What is the purpose of wardriving?
The purpose of wardriving is to detect and map wireless networks to identify unsecured or poorly secured ones. Criminals can exploit these vulnerabilities, like weak passwords or no encryption, to access data, commit fraud, or launch attacks. By targeting these security gaps, they stay hidden and out of reach of the network owner while causing significant harm.
What tools are commonly used in wardriving?
Common tools used in wardriving include GPS devices, wireless network scanners (like NetStumbler or Kismet), packet sniffers, signal-strength analyzers, and hardware like laptops, smartphones, or Raspberry Pi with external antennas.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.