WEP, WPA, WPA2, and WPA3: Definitions and comparison
The conversation about wireless security is no longer a matter of WEP vs WPA. With a range of wireless security protocols to choose from, find out what they are exactly, how they compare, and which type of Wi-Fi security you should be using. Then get Norton VPN to help secure your home network with bank-grade encryption.

WEP, WPA, WPA2, and WPA3 are all wireless security protocols — sets of rules used to protect information transmitted over Wi-Fi networks, ensuring data confidentiality, integrity, and authentication. While they’re all designed to prevent unauthorized data access or tampering, each protocol uses different rules for securing data over a network.
Wi-Fi networks need security protocols such as WEP, WPA, WPA2, or WPA3 because they broadcast signals to nearby devices. Without protection, anyone within range of those signals could potentially intercept the communications sent across a broadcast network.
Read on to learn more about Wi-Fi security protocols, how each compares, and which protocol you should choose to keep your home network more secure.
How Wi-Fi security protocols work
Wi-Fi security protocols work by enforcing a series of processes that encrypt and verify data transmitted over wireless networks to prevent unauthorized access. When a device connects to a Wi-Fi network, the protocol establishes a secure communication channel using encryption keys that ensure data being sent and received is unreadable to hackers or other third parties.
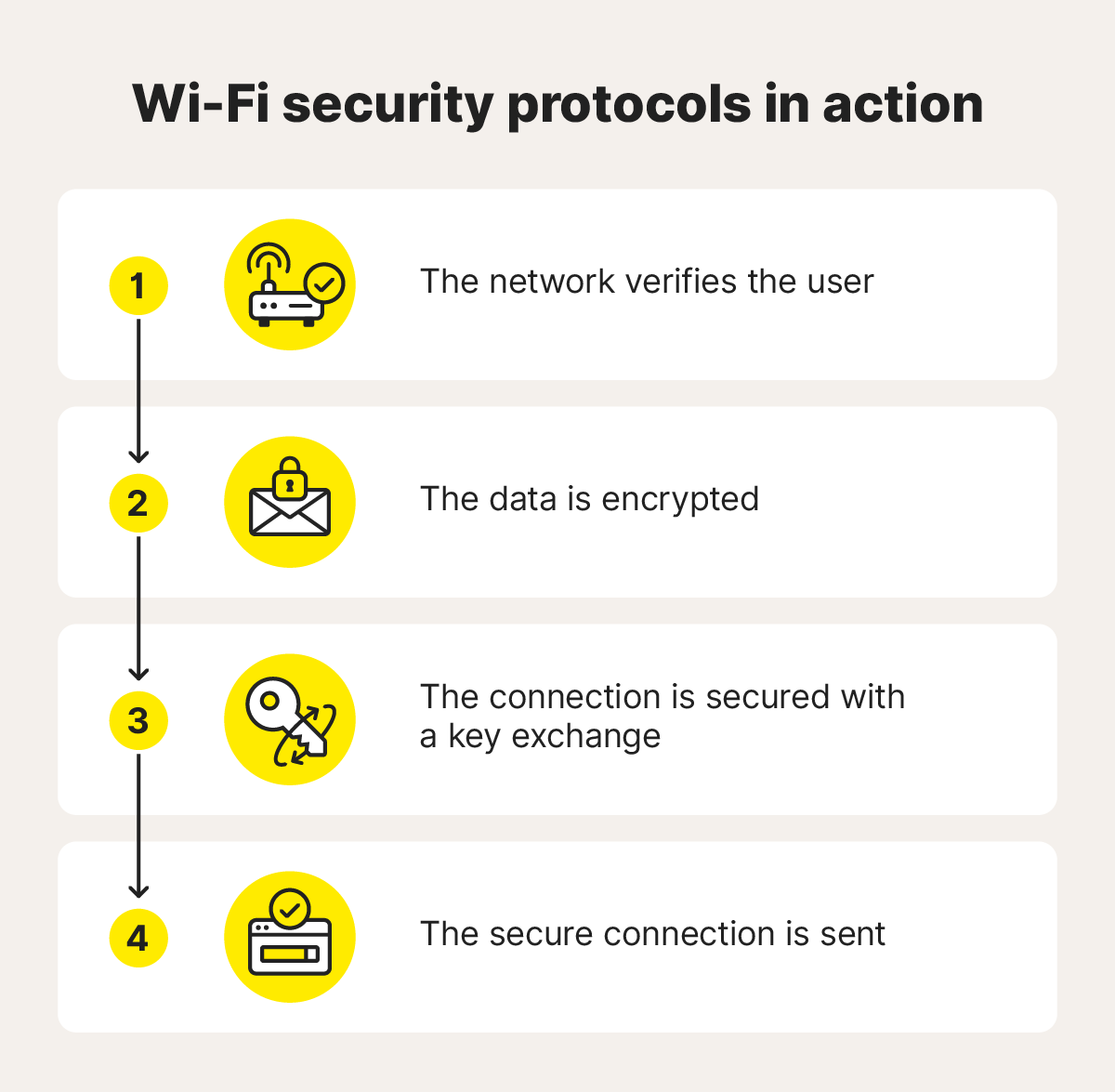
Although each protocol works slightly differently, they all follow the same basic procedure:
1. Network verification
The device scans for available Wi-Fi networks and requests to connect to a selected one. The router then prompts for authentication credentials (password or certificate). If the device provides the correct network security key, the router grants access, confirming the device's identity before allowing the connection.
2. Data encryption
After authentication, the device and router agree on an encryption method, such as AES, to scramble the data. This ensures the information remains unreadable to unauthorized parties, protecting it from interception during communication.
3. Key exchange
The router and device securely exchange encryption keys during authentication. Using methods like a pre-shared key ensures both parties have the correct keys to protect data and establish a secure communication channel.
4. Data transmission
Once encryption keys are established, the device and router transmit data over the encrypted channel, ensuring confidentiality. The data is encrypted before transmission and decrypted upon receipt, with periodic key updates to prevent interception and packet sniffing attacks.

What is Wired Equivalent Privacy (WEP)?
Wired equivalent privacy (WEP), released in 1997, was one of the earliest Wi-Fi security protocols. It was designed to offer the same level of protection as a wired connection — hence the name “equivalent” — but it quickly became outdated due to design flaws.
In 1999, WEP was retired as a secure standard. In 2004, it was replaced completely by a next-generation protocol.
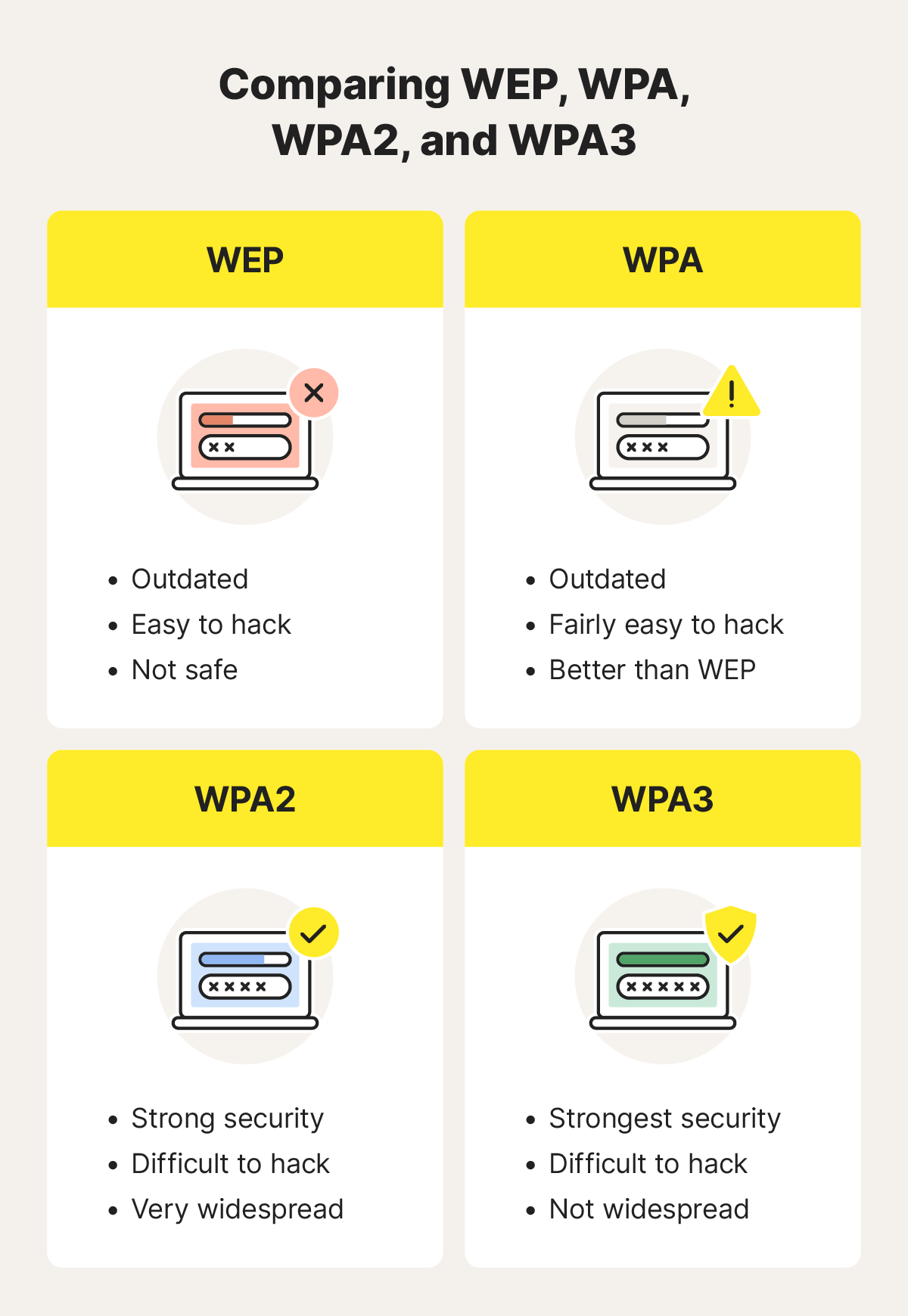
| Pros of WEP | Cons of WEP |
| Lightweight and easy to set up | Obsolete and no longer supported by most devices |
| Wide compatibility across legacy hardware | Multiple security vulnerabilities |
What is Wi-Fi Protected Access (WPA)?
Wi-Fi Protected Access (WPA) was introduced in 2003 as a more secure alternative to WEP.
WPA improved on previously existing Wi-Fi security by introducing a Temporal Key Integrity Protocol (TKIP) system to generate new network security keys for each connection. WEP, meanwhile, relied on fixed keys for each communication, meaning it had the same easily guessed keys for each session.
But, just as WEP was sunset, WPA vulnerabilities became increasingly apparent, and the framework was eventually retired in 2015 in favor of newer, more secure protocols.
| Pros of WPA | Cons of WPA |
| Stronger encryption than WEP | Outdated and no longer supported by most modern routers |
| TKIP generates new keys for every session | Known vulnerabilities |
What is WPA2?
WPA2, introduced in 2003, was the next generation of Wi-Fi security. The protocol replaced TKIP with the Advanced Encryption Standard (AES), a powerful encryption method also used by the U.S. government to protect classified data.
AES is better than TKIP because it creates more than one key. WPA2-AES goes through 10 rounds of key generation while TKIP only goes through one, making AES resistant to brute force attacks, which try to guess your key through repeated attempts.
WPA2, while more secure, is vulnerable to KRACK attacks (Key Reinstallation Attacks). And many WPA2 routers still support outdated protocols like WEP and WPA, which pose security risks. Disabling these protocols or replacing such routers is advised to enhance online privacy and security.
| Pros of WPA2 | Cons of WPA2 |
| More secure than WPA with fewer vulnerabilities | Vulnerable to KRACK attacks |
| Uses a trusted encryption standard (AES) for protecting information | Some WPA2 routers still support WEP |
What is WPA3?
WPA3, introduced in 2018, represents the latest evolution in Wi-Fi security. The protocol is an upgrade over WPA2, with more powerful, 192-bit encryption, and a more secure authentication process called Simultaneous Authentication of Equals (SAE).
WPA3 also offers enhancements for public Wi-Fi through Opportunistic Wireless Encryption (OWE), which provides individualized data encryption to users on open networks. This helps protect data transmitted over public networks such as those in cafes and hotels, reducing the risk of eavesdropping.
Despite these advancements, WPA3 adoption remains slow. The protocol can face compatibility issues with older devices and is known to occasionally cause system slowdowns. Early security flaws, such as those enabling password leaks, also raised concerns, though future updates are expected to address these problems.
| Pros of WPA3 | Cons of WPA3 |
| Stronger encryption than WPA2 | Slower than other protocols |
| SAE helps eliminate authentication vulnerabilities | Not compatible with older hardware |
| OWE increases protection on public networks | Vulnerabilities have been discovered |
WEP vs. WPA vs. WPA2 vs. WPA3
Among WEP, WPA, WPA2, and WPA3, WPA3 is the best security protocol due to the sophistication of its encryption algorithms and other enhanced security features that offer more robust protection against modern threats than legacy WPA and WEP options. But you may not be able to use WPA3 if your hardware doesn’t support it.
What devices are compatible with WPA3?
- Windows 10 Version 1903 or later
- Windows 11
- macOS 10.15 (Catalina) or later
- iOS and iPadOS version 13 or later
- Android 10 or later (varies based on device)
For older devices that lack WPA3 compatibility, WPA2 remains a credible alternative, although you should use it alongside a reliable VPN to ensure your connection is protected by powerful encryption — especially when doing online banking, shopping, or sharing sensitive information.
However, the heavily outdated WEP and WPA protocols should be avoided due to their significant vulnerabilities that can make your network an easy target for hackers. If you’re still relying on old WEP or WPA hardware, it’s time to upgrade for the sake of your privacy and security.

How do I find out my Wi-Fi security type?
You can check your Wi-Fi security type through your computer or phone, or via your router’s admin portal. Here’s how to find out your wireless security type on Windows, macOS, Android, or router devices:
Windows 11
- Click the taskbar in the bottom-right corner.
- Select the arrow next to Wi-Fi and the “i” icon beside your connection.
- You’ll find the network security type on the details screen.
macOS
- Click the Wi-Fi icon in the top-right corner and select Wi-Fi Settings.
- Scroll down and click Advanced.
- A list of known networks and their security types will be displayed.
Android
- Open Settings and tap Network & Internet.
- Select Internet, and choose your Wi-Fi network.
- You’ll see the security type under the Security heading.
Routers
- Find your router’s IP address on the side or bottom of the device, or in the owner’s manual.
- Enter the IP address in your browser’s address bar to reach the router’s admin page.
- Log into the router’s admin page credentials (the default login is in the owner’s manual).
- Locate your security type under the Wireless Security menu.
While you’re in your router’s admin portal, consider updating your router’s password for added security. If you have trouble accessing your router, contact your internet service provider (ISP) for help.
Pro Tip: iOS devices (iPhones and iPads) do not allow you to see your network security type from their Wi-Fi menu.
Which Wi-Fi security setting should you choose?
You should select WPA3 as your Wi-Fi security setting if you have compatible home network devices. This allows you to benefit from its stronger levels of encryption and enhanced security features. Otherwise, you should use WPA2 to secure your home network — unlike the legacy WEP and WPA protocols, it’s still considered a viable security standard.
Secure your local network
Wi-Fi security is a vital first line of defense against network attacks, but neither WEP, WPA, WPA2, or even WPA3 offer the same level of encryption as a top-quality VPN.
With Norton VPN you can fortify any connection with bank-grade AES-256 encryption, helping you keep all your internet data private and secure — even once it’s left your home network. And thanks to features such as split tunneling, a range of cutting-edge protocols, and ultra-fast data transfer speeds, you can keep hackers at bay without sacrificing performance.
FAQs
How do I keep my Wi-Fi network secure?
To secure your Wi-Fi network, use WPA3 or WPA2 encryption and set a strong, unique password. You should also disable WPS on your router, regularly update its firmware, and change the default admin credentials. Enable a firewall, hide your network SSID if possible, and consider using a trusted VPN for additional protection.
How are unsecured Wi-Fi networks a risk?
Unsecured Wi-Fi networks are risky because they allow unauthorized users to intercept your data, exposing sensitive information like passwords and financial details. Hackers can exploit these networks for malicious activities, such as installing malware or launching attacks. Without encryption, your online activity and personal information may be exposed and vulnerable to eavesdropping.
What is WPS?
Wi-Fi Protected Setup (WPS) is a feature designed to simplify the process of connecting devices to a Wi-Fi network. It allows users to connect by pressing a button on the router or entering a PIN. However, WPS is vulnerable to brute-force attacks. For better security, WPS should be disabled on routers that support it.
What cyberattacks can affect my home network?
Cyberattacks of practically every kind pose a risk to your home network. Hackers can exploit vulnerabilities to target your personal devices, steal sensitive data, or plant malware.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.