What is facial recognition and how does it work?
Once the stuff of spy films, facial recognition is now part of everyday life — used to identify you in seconds by your unique features. In this guide, I'll teach you how it works, where it’s being used, and the risks it poses. Then get a comprehensive security tool to help protect you from deepfakes, social engineering, and other scams that exploit your facial data.

Facial recognition seems almost ubiquitous nowadays, from Apple’s Face ID to airport security, workplace access systems, and even public transportation. While it offers convenience and security benefits, it also raises serious privacy concerns.
As the technology spreads, privacy laws are struggling to keep pace. Some cities are even moving to expand its use, framing it as a crime‑fighting tool despite well‑documented issues like racial bias and potential misuse. In New Orleans, for example, officials have pushed to roll back bans on using facial recognition as a surveillance tool to track criminal activity, sparking concerns about privacy and misuse.
I'll give you a closer look at how facial recognition is used, its benefits, and its drawbacks. Then, I’ll walk you through a personal example of when I’ve encountered this technology in my everyday life.
How does facial recognition work?
Facial recognition is a type of biometric technology that works by capturing an image of a person’s face, detecting key features, and converting them into a unique digital template. The system then compares this template to stored biometric data to find a match and verify identity.
Take a closer look at the steps involved in facial recognition below:
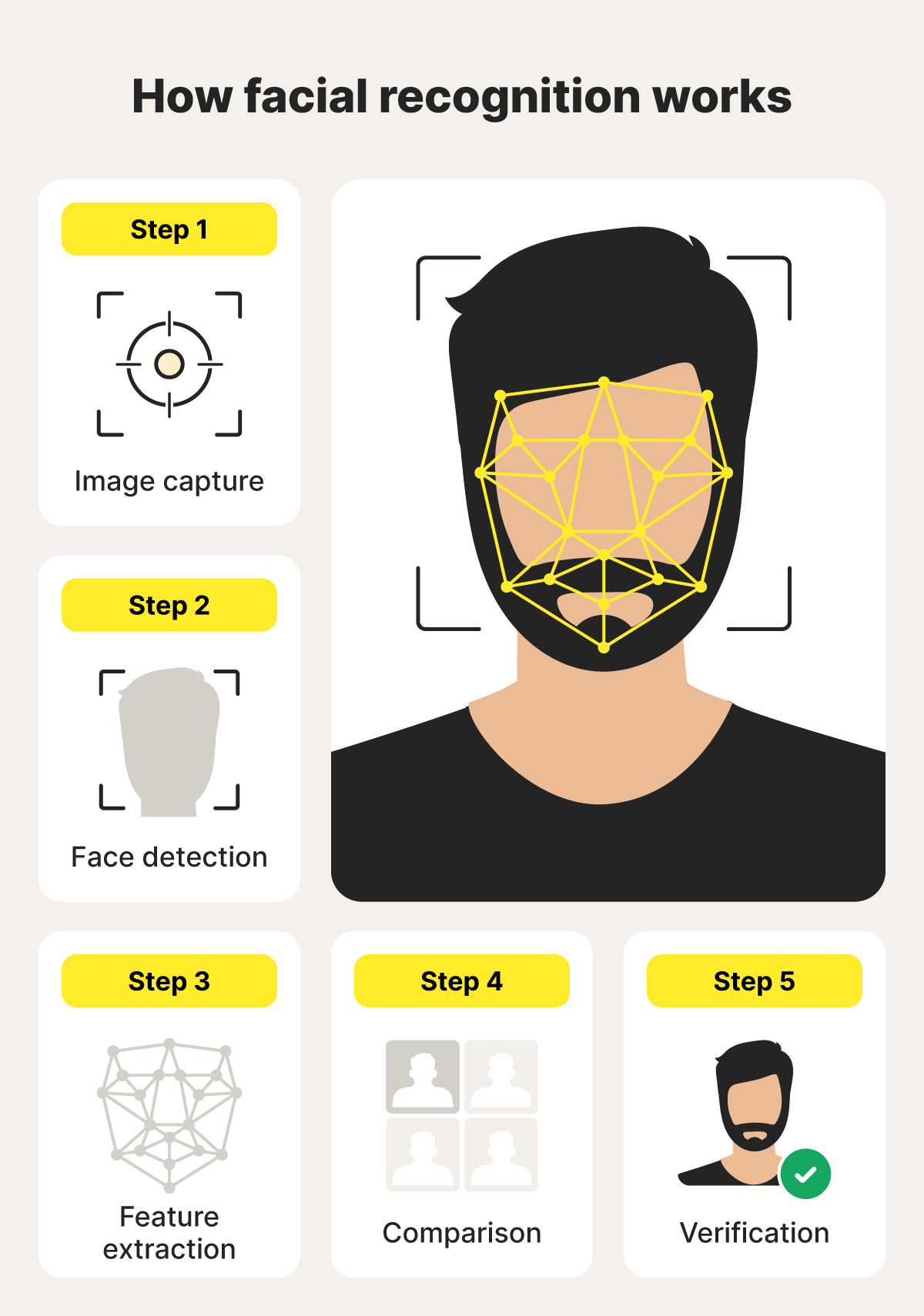

1. Image capture
Image capture involves taking a photo or video of a person’s face. The image can come from various sources, like security cameras, smartphone cameras, or even social media photos. The clearer and more front-facing the image, the easier it is for the system to analyze.
2. Face detection
Next, the facial recognition system scans the captured image to locate a face within it. It separates the face from the background and other objects, focusing only on the relevant area.
3. Feature extraction
Feature extraction involves analyzing the detected face to identify unique features, like the distance between the eyes, the shape of the nose, and the contour of the jaw. These details are converted into a biometric template representing the face’s distinct characteristics.
4. Comparison
Next, facial recognition technology matches the digital biometric template from the captured face against a database of stored templates. It looks for similarities to find potential matches, helping determine if the person is known or unknown based on the level of similarity.
5. Verification
Finally, the system assesses how closely the captured template matches the claimed identity, using a predefined similarity score. If the score is high enough, the person’s identity is confirmed.
Where is facial recognition used?
Facial recognition is embedded in a wide range of technology and security systems. It’s used to unlock phones, verify identities, screen passengers at airports, assist law enforcement, control access to secure buildings, and even monitor casinos for banned individuals or suspicious behavior.
Here are a few common places you may encounter facial recognition:
- Device unlocking: Facial ID enables users to unlock phones, tablets, and laptops without requiring a password.
- Multi-factor authentication: Facial recognition is a form of multi-factor authentication, adding an extra layer of security by verifying your face and a password or PIN.
- Airport security: Airports use facial recognition to verify passenger identities and speed up boarding and customs. For a real-life example of how this works, check out my experience with facial recognition below.
- Law enforcement surveillance: Police use facial recognition to identify suspects, find missing persons, and monitor public spaces.
- Access control: Businesses and secure buildings use facial recognition to grant entry only to approved individuals.
- Casino surveillance: Casinos use facial recognition to spot banned players, detect cheating, and flag suspicious behavior.
Real examples of facial recognition technology
Major companies, governments, and industries worldwide use facial recognition for everything from security to convenience. Below are real-world examples that show how facial recognition shapes travel, home security, casinos, and public services.
- Apple Face ID: Apple uses facial recognition to unlock devices, approve payments, and secure apps, offering a password-free experience for millions of users.
- Amazon Ring and Google Nest cameras: These smart home devices use facial recognition to identify familiar faces, send tailored alerts, and improve home security. However, apps like Ring also collect user data such as email addresses, phone numbers, device IDs, and even audio recordings. Without strong safeguards, this data could be exploited by criminals to access sensitive information.
- Delta and American Airlines biometric boarding: These airlines use facial recognition to verify passengers at boarding gates, helping speed up the process and reduce the need for physical IDs.
- Harrah’s Casino: Harrah’s Casino used facial recognition to identify suspected cheaters and banned patrons, prompting a lawsuit under Illinois’s Biometric Information Privacy Act (BIPA). Two rewards‑program members claim the casino collected and stored their facial scans without consent or a public retention policy—both required under BIPA’s strict biometric data rules.
- Government schools in Karnataka, India: Schools in Karnataka, India, are rolling out facial recognition to track student attendance, aiming to improve administrative efficiency. However, privacy advocates worry this invasive use collects sensitive biometric data on minors without clear consent and could be vulnerable to misuse, hacking, or biased misidentification.
- Public transportation fare in Moscow: Moscow’s transit system lets riders pay fares using facial recognition, removing the need for cards or tickets. It’s one of the largest public transit deployments of the technology in the world, but it has also sparked concerns over privacy, data security, and the potential for expanded government surveillance.
My real-life facial recognition experience
- Image capture: I recently flew into Chicago O’Hare airport from Europe, and my picture was taken at the Customs and Border Protection (CBP) checkpoint.
- Face detection: As I approached the Customs counter, they instructed me to take off my glasses and look directly into the camera. This is so the facial recognition technology could detect my full face, unobstructed.
- Feature extraction: The facial recognition technology used the Customs photograph to analyze specific traits on my face, like the shape of my eyes and a scar on my right cheek, creating a biometric template unique to me.
- Comparison: The template created through my facial feature analysis was compared to my travel documents to ensure I was who I claimed to be.
- Verification: My biometric template matched the photo stored in the CBP database with a high confidence score. My identity was confirmed, and I proceeded quickly through the border.
Facial recognition benefits
Biometric facial recognition offers both stronger security and added convenience in daily life. Here's a closer look at the benefits of facial recognition:
- Enhanced airport security: Facial recognition helps verify passenger identities, reduce fraud, and speed up boarding, making air travel safer and more efficient.
- Criminal identification: Law enforcement can use facial recognition to match suspects to criminal databases and assist in investigations.
- Locating missing persons: The technology can scan public spaces to help find missing children, vulnerable adults, or victims of human trafficking.
- Securing personal devices: Facial recognition helps protect phones, tablets, and laptops by allowing only authorized users to unlock them. Apple’s Face ID, for example, has a false acceptance rate of less than 1 in 1,000,000.
Facial recognition concerns
Facial recognition raises concerns about privacy, accuracy, and security because of how it collects, stores, and processes personal biometric data, often without consent. It can misidentify people, struggle with age and race differences, and expose sensitive biometric data to theft.
Here's a closer look at facial recognition concerns:
- Mistaken identity: Facial recognition can misidentify people, especially in crowded or poor-quality images, leading to false matches and potentially serious consequences. For example, in 2020, Robert Williams was wrongfully arrested after being misidentified by facial recognition software.
- Age inaccuracies: Systems often struggle with aging faces as feature patterns shift over time, reducing accuracy for older individuals. Similarly, features like Face ID may not be as secure for individuals under 13 years old due to their distinct facial features not being fully developed yet.
- Racial bias: Algorithms perform worse on people of color, leading to higher error rates and unfair outcomes. A University of Michigan study found that using facial recognition in schools could exacerbate racism by disproportionately misidentifying students of color, reinforcing discriminatory practices, and creating a hostile learning environment.
- Potential violation of privacy: Using facial recognition in schools or public transit without consent means people are tracked without knowing it.
- Security risks: If somebody steals biometric data like facial scans, it creates lasting risks because you can’t change your face like a password. Hackers could use stolen data to impersonate you, bypass security systems, or commit identity theft. This makes breaches of biometric databases especially dangerous and hard to fix.
- Preemptive arrests: Facial recognition technology can flag individuals as suspicious before any crime occurs, leading to wrongful detentions or increased surveillance based on flawed or biased data.
Can facial recognition be exploited for identity theft?
Yes, criminals can exploit facial recognition to commit identity theft by posing as someone else. This can give them access to private accounts or personal information without permission.
Hackers use spoofing attacks, where photos, videos, or masks fool the system into thinking they’re someone else. Another tactic is deepfakes, in which a hacker — usually with the help of AI — creates highly realistic fake videos that can trick facial recognition technology. These attacks make it easier for criminals to bypass security and commit identity theft.
Even low-tech methods can work. Researchers have shown that subtle cosmetic changes — such as specific makeup patterns around the lips, jawline, and nose bridge — can confuse facial recognition systems by interfering with how they map a face.
Cybersecurity tips for facial recognition
Taking a few proactive steps can help safeguard your biometric data from misuse. Here are some ways to stay safer when using devices or services with facial recognition features:
- Opt out of facial recognition systems: Some apps, devices, or services offer facial recognition features you can disable. Turning them off helps limit how often your face is scanned, stored, or shared, reducing the risk of data misuse.
- Secure your router: A secure home network helps protect connected devices, like smart cameras or phones, from hackers who may try to access facial recognition data.
- Be cautious about camera permissions: Only grant camera permissions to trusted apps. Malicious apps can capture images or videos that criminals can use to steal your biometric data.
- Use facial recognition blocking glasses: These specially designed glasses reflect infrared light or distort key facial features, making it harder for facial recognition cameras to scan your face accurately.
Protect against scammers after your data
While facial recognition can improve security, it also raises privacy concerns, especially if your biometric data falls into the wrong hands.
Norton 360 Deluxe adds an extra layer of protection by helping safeguard your device against hackers and scammers, including those who might try to exploit facial recognition data. You’ll also get access to our cutting-edge Deepfake Protection feature, which can help you identify online videos that use faked or breached facial data.
FAQs
Can facial recognition work with a mask?
Facial recognition accuracy drops with masks, since key features like the nose and mouth are covered. For example, Apple now lets you enable a mask mode, which forces Face ID to focus on the eyes and upper face, but results vary. It’s generally less reliable than full-face recognition without a mask.
What are some examples of biometric technology?
Examples of biometric technology include fingerprint scanners, voice recognition, iris and retina scans, palm vein recognition, and, of course, facial recognition. These tools use unique biological traits to verify identity and are common in smartphones, airports, banking, and security systems.
Can facial recognition be fooled with a photo?
Yes, somebody can fool basic facial recognition systems with a photo, especially older or less secure versions. However, modern systems use anti-spoofing technology, like depth detection and liveness checks, to tell the difference between a real face and a flat image.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.