What is MD5 hash + how does it work?
MD5 hash is a cryptographic protocol that verifies the authenticity of files sent between devices—but is it a match for technology today? Learn how MD5 hashing works and how it impacts online security. Then, install a cybersecurity suite like Norton 360 Deluxe to get powerful protection for your devices and a built-in VPN with bank-grade encryption.

What is the MD5 hashing algorithm?
The MD5 (message-digest algorithm 5) hashing algorithm is a cryptographic protocol used to authenticate messages and digital signatures. The main purpose of MD5 is to verify that the receiver of a message or file is getting the exact same information that was sent.
Consider receiving a physical package in the mail. If you get a package that seems damaged or tampered with, you may not want to open it. When you go online, you constantly send messages and files. But in these cases, you can’t see if the files are corrupted. The MD5 hash algorithm can verify that for you.
MD5 and other cryptographic hash algorithms are one-way functions, meaning they aren’t used to encrypt files—it’s not possible to reverse the hashing process to recover the original data. When data is hashed, MD5 produces a fixed-size hash value. The hash value represents the original data. If the original hash value matches the hash generated from the received data, it signifies that the data is exactly the same and hasn’t been altered.
But MD5 was designed in 1991, and its powers are no match for today’s technology. While MD5 is still useful as an authenticator to verify data against unintentional corruption, it shouldn’t be used where security is a concern.
What’s the difference between MD4 and MD5 hash?
As MD5’s predecessor, MD4 is older and less secure, because its hash calculations aren’t as complex as those of MD5. But both MD4 and MD5 are considered obsolete today for cryptographic purposes due to their security vulnerabilities, and there are more modern alternatives available.
How does MD5 hash work exactly?
The MD5 hash algorithm authenticates messages by creating a unique identifier or “digital fingerprint” for a file. It then verifies this unique fingerprint when the message is received. This fingerprint is also known as a hash value or checksum.
When you send a message or file, MD5 passes it through a mathematical algorithm that generates a checksum (128-bit hash). Each hash contains a combination of 32 numbers and letters (4 bits per character).
The MD5 hashing algorithm generates the hash according to the contents of the file, then verifies the hash is the same once the data is received. Here’s an MD5 example: the word “hello” always translates to the MD5 hash value: 5d41402abc4b2a76b9719d911017c592.
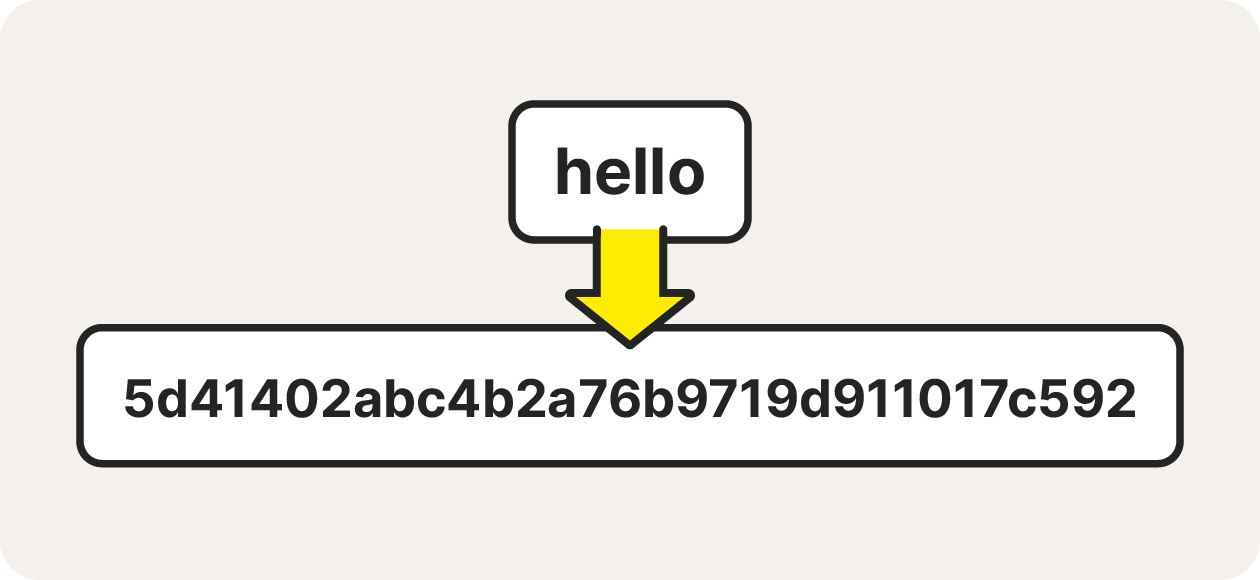
The MD5 hash value of the word "hello."
Any file sent is given an MD5 hash length of 32 characters, whether it’s 1 KB or 100 GB in size. When the message arrives, it is checked by the receiver’s device to ensure it matches the original checksum. If anything in the file has changed, the checksum will not match, and the receiver’s device will know the file is corrupted.
What is MD5 hash used for?
MD5 hashing is used to authenticate messages sent from one device to another. It ensures that you’re getting the files that were sent to you in their intended state. But it’s no longer used for password storage or in other applications where security is a concern.
When computers were less complex, MD5’s cryptographic signatures were effective at protecting files sent over the web against hackers. That’s not the case anymore. Some types of hackers can create inputs to produce identical hash values. When two competing messages have the same hash code, this is called a collision attack, though MD5 hash collisions can also happen accidentally.
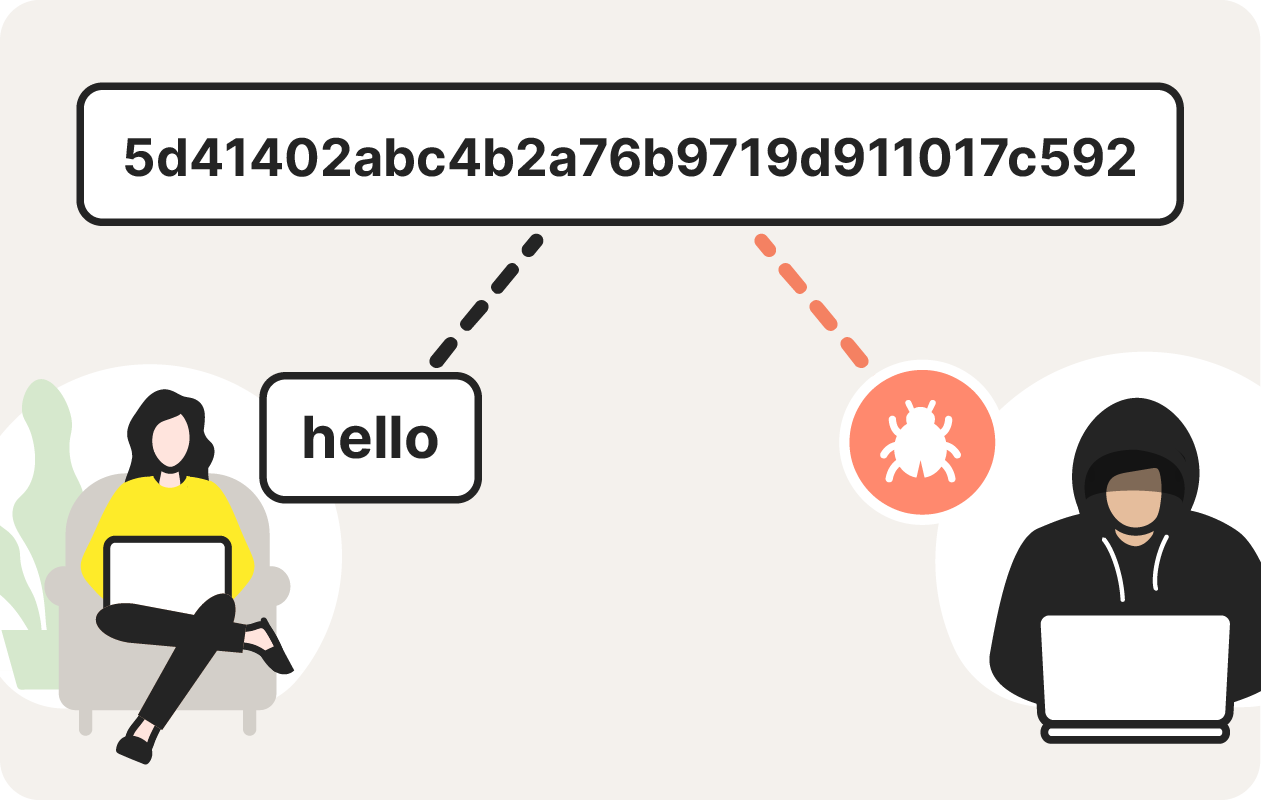
An MD5 collision attack occurs when a hacker sends a malicious file with the same hash as a clean file.
We’ll talk about the newer hashing algorithms next, which make it nearly impossible to create a collision attack on purpose—and every iteration is more secure. But if you’re worried about keeping your device safer, there are proactive steps you can take. For starters, always use a VPN on public Wi-Fi, because it will encrypt data that you send and receive online. And use a trusted antivirus on all your devices.
Norton 360 Deluxe includes a built-in VPN with bank-grade encryption protocols and multiple additional tools to help protect your device from hacking, viruses, and other malware. Install Norton 360 Deluxe today for multiple layers of device protection.
What are some alternatives to MD5 hash?
There are modern hashing algorithms that have better security properties than MD5. They create more complex hashes and have varying levels of security. Here are a few of the most common alternatives to MD5 hash:
- Secure Hash Algorithm 1 (SHA-1): The SHA-1 function works the same way as MD5, but it creates a 160-bit hash instead of MD5’s 128-bit hash. A longer hash length increases the complexity of each hash and decreases the likelihood of collisions. However, SHA-1 is also vulnerable to collision attacks.
- Secure Hash Algorithm 2 (SHA-2): SHA-2 is the successor of SHA-1. SHA-2 allows for hash lengths as long as 512 bits and offers significantly more complexity and protection than the MD5 hashing algorithm and SHA-1. Unlike these older functions, SHA-2 is still used for cryptographic purposes and is found in many practical applications like blockchain technology, digital signatures, and password security.
- Secure Hash Algorithm 3 (SHA-3): SHA-3 is the successor of SHA-2. Rather than producing fixed-length hash values, SHA-3 uses a different construction to produce hash values of variable length. While it provides stronger security guarantees, it isn’t as widely adopted as its predecessors because it’s more difficult to implement and existing systems require updates to introduce it.
- Cyclic redundancy check (CRC) codes: CRC codes are not hash functions, but they are similar to MD5 in that they use algorithms to check for errors and corrupted data. CRC codes are faster at authenticating than MD5, but they are less secure.
Keep your devices and online activity safer with Norton 360 Deluxe
MD5 hash is a useful way to authenticate files sent between devices. Thanks to MD5 hashing algorithms and its successors, your devices know when you’re getting the correct files.
But hashing algorithms alone can’t protect against the variety of today’s online threats. Norton 360 Deluxe provides comprehensive online security to help block suspicious links and keep hackers out. Plus, it features heuristic malware detection technology and a built-in VPN to enhance your security and private online.
FAQs about MD5 hash
Do you have more questions about MD5 hashing and other hash functions? Find the answers below.
Is MD5 hash secure?
No, MD5 hash is not secure. Why isn’t MD5 secure? The MD5 algorithm’s hash codes are not complex enough to prevent collision attacks. More modern hash functions, such as the SHA-2 and SHA-3 hash algorithms, are more secure than MD5.
How many bytes long is an MD5 hash?
An MD5 hash is 16 bytes long (or 128 bits). The length of an MD5 hash is always the same at 32 alphanumerical characters, no matter what the original file size is. An MD5 hash example is “5d41402abc4b2a76b9719d911017c592,” which is the hash value for the word “hello.”
Is MD5 hash better than SHA?
No, MD5 hash is an older hashing algorithm than the SHA algorithms. It produces less complex hash values and is less secure. The SHA-1 algorithm is more complex than MD5, but it is also not secure against collision attacks. The SHA-2 and SHA-3 algorithms are more secure.
What hashing algorithm is the best?
The best hashing algorithm depends on your needs. Certain cryptographic hash functions are used in password storage so that plain text passwords are hashed and kept safer in the event of a data breach. For password protection, Argon2 and Bcrypt are strong password hashing algorithms. Both provide reliable safety against brute force and pass the hash attacks. For authenticating files and certificates, SHA-2 is currently considered the best hashing algorithm that’s widely used.
The National Institute of Standards and Technology has established a Policy on Hash Functions that involves all U.S. government agencies and other stakeholders removing the SHA-1 hashing function and transitioning to SHA-2 or SHA-3.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.