Cryptography Definition, Algorithm Types, and Attacks
Cryptography uses algorithms to encrypt private information on apps and hardware like phones, only showing details to people with a valid decryption key. In this article, we’ll tell you more about how cryptography relates to cybersecurity, share examples of how it works, and explore the most common types. Install cybersecurity software with a built-in VPN on your devices, like the one included in Norton 360 Deluxe, to help keep your browsing private no matter which network you connect to.

Today, many people (if not most) are chronically online. So, it’s safe to say there is a never-before-seen amount of private data and messages floating around. Hackers who access that information can use it to steal identities, dox their targets, or blackmail them. The good news is that as hackers advance, cybersecurity technology and tools do, too—one example is cryptography.
What is cryptography in cybersecurity?
Cryptography in cybersecurity is a technique that uses mathematical algorithms to secure information, communications, and data behind a nonsensical wall of random code. This prevents unauthorized users from accessing and tampering with confidential information.
What is the difference between cryptology vs. cryptography?
Cryptography is a category that falls under cryptology:
- Cryptology is a broad field that encompasses both cryptography (encrypting information) and cryptanalysis (decrypting information).
- Cryptography is a branch of cryptology that focuses on creating secure messaging by converting plaintext (readable text) to ciphertext (unreadable text). It involves creating codes and ciphers, encryption, and other techniques to secure data.
What is the history of cryptography?
There is evidence of cryptography in ancient Egypt. However, modern cryptography began in World War ll when the Axis powers created the Enigma machine (a cryptography tool designed to encrypt messages), and the Allied powers invested in cryptanalysis to decrypt outgoing communications.
Then, in the 1970s, IBM developed public key cryptography, which eventually became the standard for modern cryptography. Then, modern cryptography innovations started to advance rapidly in the late 20th century when quantum computers were invented.
How is cryptography used today?
Today, cryptography helps to secure digital communication and protect sensitive data. Here are a few ways you might already be using cryptography:
- Online banking: Cryptography can encrypt sensitive financial data like account numbers and transaction details.
- Email encryption: Cryptography can scramble emails so that only the intended recipient can open and read the message.
- Blockchain security: Cryptography can secure transactions, verify the authenticity of data, and prevent double-spending.
- End-to-end encryption (E2EE): Cryptography ensures that messages are encoded so that only the sender and intended recipient can decipher them.
- Multifactor authentication (MFA): Cryptography can verify a user’s identity and authenticate a session using one-time codes.
- Electronic signatures: Cryptography allows users to create unique digital signatures and ensures they are authentic.
- IoT security: Cryptography in IoT security can protect the data sent using devices on a network from data breaches.
- Website encryption: Cryptography in website encryption can safeguard user login and credit card details using technologies like Secure Sockets Layers (SSL) and Transport Layer Security (TLS) to encrypt data as it travels between a user’s web browser and a website’s server.
Key tenets of cryptography
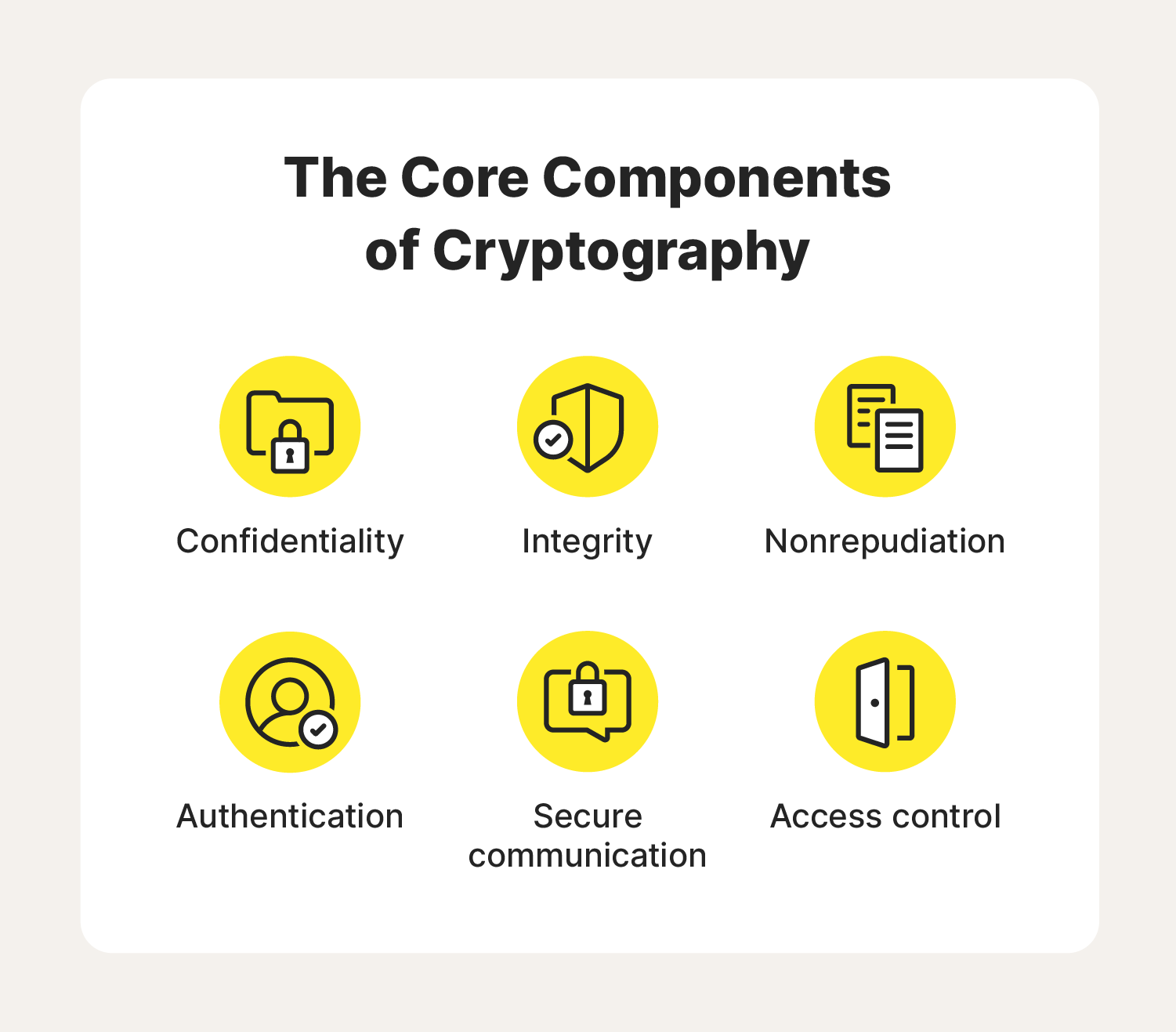
Cryptography plays an important role in modern cybersecurity because it’s built on six key tenets. They include:
- Confidentiality: Encryption keeps sensitive information safe from prying eyes.
- Integrity: Cryptography catches data tampering and unauthorized changes, guaranteeing that the message the recipient receives arrives in its original form.
- Nonrepudiation: Cryptography provides evidence that a message was sent and received, ensuring that everyone is accountable for their involvement.
- Authentication: Cryptography verifies the identities of the sender and recipient to stop unauthorized users from accessing private messages.
- Access control: Cryptography uses keys to ensure only the intended recipient can open a message.
- Secure communication: Cryptography prevents eavesdropping and interception from third parties while a message travels from the sender to the recipient.
What are the 3 main types of cryptography algorithms?
Algorithms are an essential part of cryptography. They are responsible for making plaintext unreadable to anyone without a valid decryption key. There are three primary types:
1. Symmetric key cryptography
This method requires the sender to encrypt the message and the receiver to decrypt it using a shared private key. Generally considered fast and efficient, it’s a strong option for encrypting large batches of data.
2. Asymmetric key cryptography
This approach uses two separate keys. First, the sender uses a public key to encode their plaintext message. Then, the recipient uses a private key to decode the ciphertext. It’s good to use this algorithm to secure confidential messages.
Hash function
This method validates data using hash values, usually to store passwords or verify user identities. In simple terms, hash functions use a mathematical hashing algorithm that “hashes” the plaintext, turning it into unreadable code.
How does cryptography work?
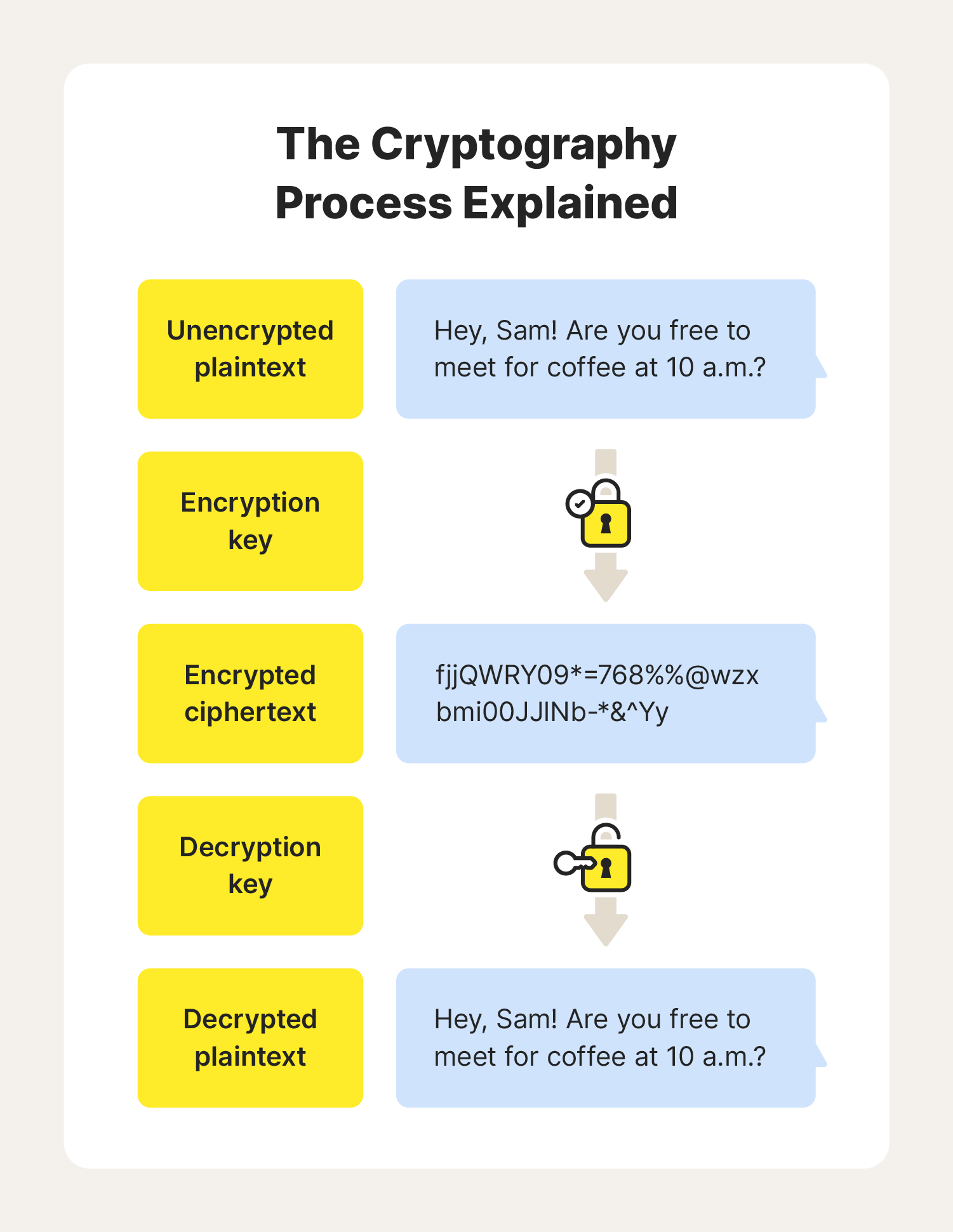
Cryptography uses algorithms to transform plaintext data into ciphertext, making a typical message unreadable. Here's how cryptography algorithms function:
- Encryption: Cryptography algorithms turn data into ciphertext. The ciphertext appears as a jumbled, random, and unreadable message to anyone without a decryption key.
- Secure communication: Cryptography encrypts data so no one can snoop on or manipulate communications in transit.
- Decryption: Only the person with the correct key can open the message to see its true contents.
Can cryptography be broken? (6 types of attacks)
Cryptography algorithms are extremely difficult to break. However, they aren’t invincible since security depends on the strength of the algorithm and keys.
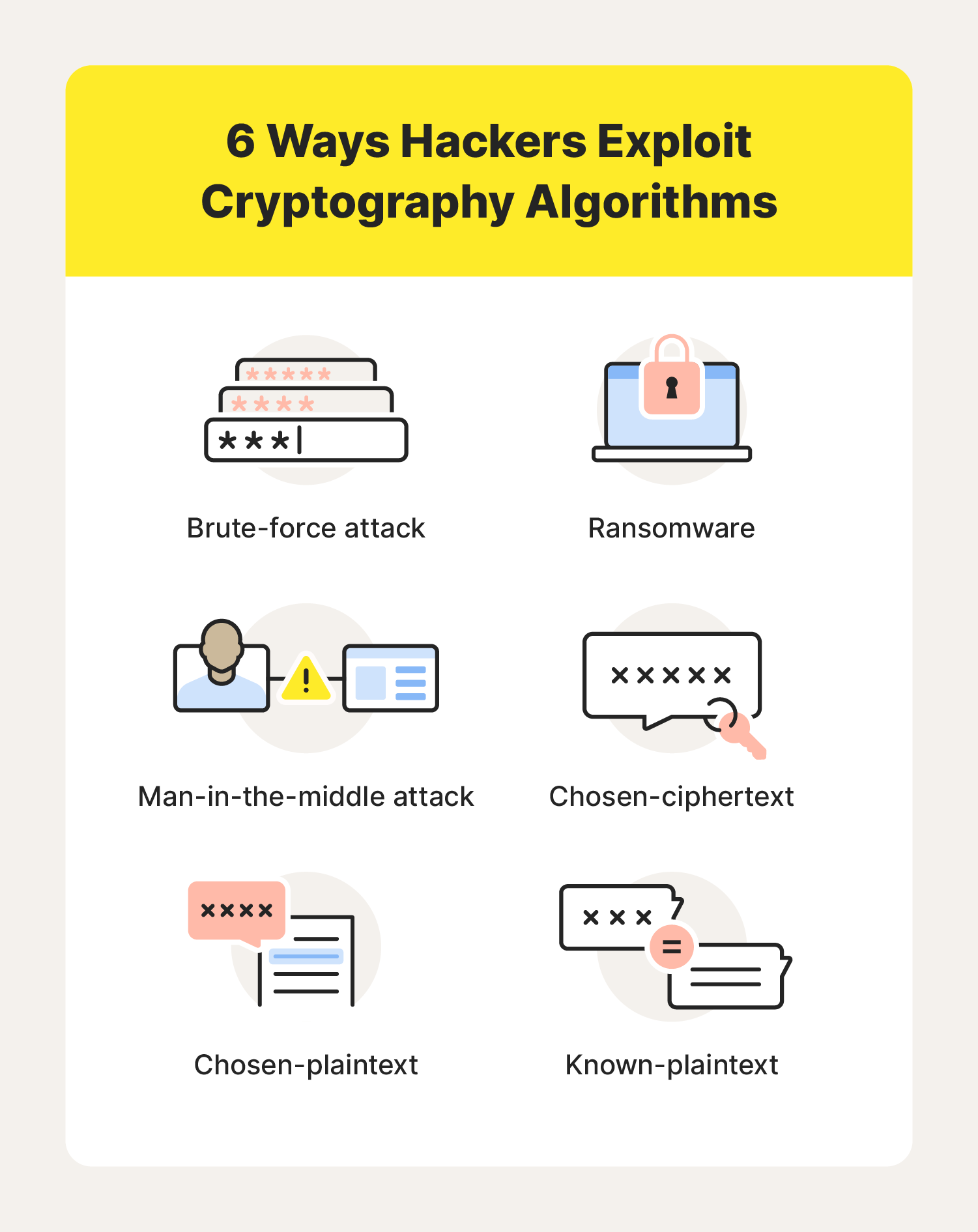
Here are a few tactics hackers can use to exploit cryptographic vulnerabilities:
- Brute-force attack: Sometimes, hackers can successfully break through cryptographic defenses by trying every possible key until they stumble onto the correct one. To keep them guessing correctly, use long and complex keys.
- Ransomware: Ransomware isn’t a direct threat to cryptographic security. However, hackers can use this malware to target user data and hold it for ransom until the person with the key surrenders it.
- Man-in-the-middle attack (MitM): A hacker intercepts data while it’s being sent, sometimes altering the contents of the message. Often, the sender and recipient are unaware when this type of attack occurs.
- Chosen-ciphertext: An attacker manipulates ciphertexts and observes the corresponding decrypted plaintexts to search for cryptographic weaknesses.
- Chosen-plaintext: Chosen plaintext attacks involve a hacker selecting specific plaintexts and analyzing their corresponding ciphertexts to find cryptographic vulnerabilities.
- Known-plaintext: Known plaintext attacks leverage the knowledge of both plaintext and ciphertext pairs to guess encryption keys or break cryptographic systems.
How to stop cryptography attacks
Cryptography is a powerful tool for preventing data breaches. However, it’s only as strong as you make it. Here are some key steps to enhance your cryptographic system:
- Use strong algorithms: Begin with a robust encryption algorithm that's trusted and time-tested. For example, algorithms like AES 256-bit encryption have never been cracked and hold up against brute-force attacks.
- Create lengthy encryption keys: Longer keys add complexity and resilience to your encryption. This tactic also deters brute-force attacks.
- Protect cryptographic keys: Safeguard your encryption keys to prevent unauthorized users from gaining access. You should also avoid storing keys in plaintext format to decrease security risks.
- Install software updates regularly: Keeping your software up-to-date is crucial for fixing security vulnerabilities. Often, software updates patch up known weaknesses that hackers may otherwise exploit.
- Use strong passwords: Ensure that your passwords are intricate, unique, and difficult to crack. This is another proven tactic to safeguard against brute-force attacks.
- Identify phishing attacks early: Be aware of possible phishing attempts to prevent unauthorized access—never click on suspicious links, files, or videos.
- Invest in malware and antivirus software: These tools can help detect and thwart malicious software attempting to compromise your encryption.
Protect your data and device from cyberattacks
Even the most secure apps, devices, and programs can have vulnerabilities that enable hackers to steal your private information. That’s why it’s important to add another layer of defense to enhance device security. Installing cybersecurity software with a built-in VPN like Norton 360 Deluxe can help keep your browsing sessions private whether you connect to a private or public network.
FAQs about cryptography
Still have questions about cryptography? Here are some answers to some commonly asked questions.
What is the difference between cryptography and encryption?
Cryptography encompasses a variety of techniques and methods for securing information. Encryption is a specific cryptographic technique that involves converting plaintext into a coded ciphertext form to protect it from unauthorized access.
What is post-quantum cryptography?
Post-quantum cryptography is a branch of cryptography focused on developing encryption methods that can safeguard against attacks by quantum computers. It often relies on approaches like lattice-based cryptography and hash-based cryptography.
What is the purpose of post-quantum cryptography?
Post-quantum cryptography is an alternative to traditional cryptography because it enables encryption algorithms that can combat cyber attacks from quantum computers. This is important because quantum computers are powerful and can easily break traditional encryption algorithms.
What is cryptography in Bitcoin and other cryptocurrency?
Typically, cryptography can secure and verify cryptocurrency transactions for blockchain-based currency like Bitcoin. Cryptography can also be used to “mine” cryptocurrency or to secure blockchain networks.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.







Want more?
Follow us for all the latest news, tips, and updates.