What is the pig butchering scam?
Pig butchering scams are a type of investment fraud where cybercriminals use social engineering tricks to manipulate their victims into making fraudulent cryptocurrency payments. Learn how pig butchering scams work and the red flags to look out for. Then, get Norton 360 with its built-in AI-powered scam detection engine for robust protection against advanced scams.

Fraudsters seem to be lurking around every corner of the digital world. In 2024, Meta removed more than two million social media accounts to combat pig butchering scams. And technology like AI and deepfakes can make spotting long cons like pig butchering scams harder than ever.
Keep reading to learn the ins and outs of pig butchering scams, including how they work, real-life examples, and how to avoid falling victim.
Pig butchering scam meaning
Pig butchering refers to a scam where cybercriminals build fake relationships — often romantic — to exploit a victim financially through cryptocurrency investment fraud or urgent requests for large sums of money for travel or fabricated emergencies. These financially ruinous scams often unfold over months, sometimes employing AI and deepfakes to seem more convincing.
This scam’s name comes from the Chinese phrase sha zhu pan, which translates to “butchering a pig.” Scammers “fatten up” their victims by gaining their trust through fake friendships or online romances before leading them into fraudulent investments.
How pig butchering scams work
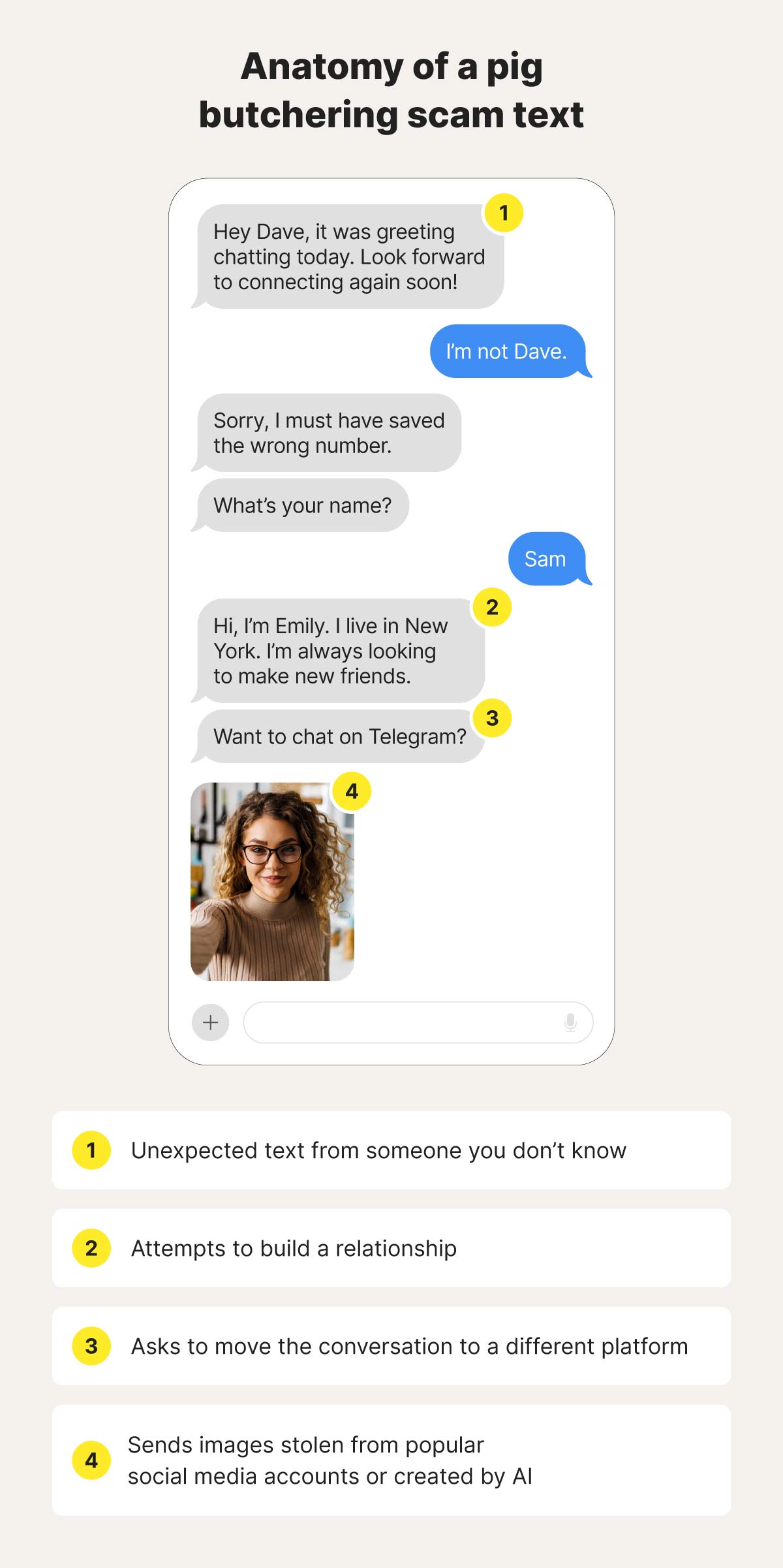
The pig butchering crypto scam starts when someone unexpectedly contacts you and works to gain your trust by building a relationship. Then, they lure you into making fake cryptocurrency investments or other payments before ultimately stealing your money.
Here’s a closer look at the steps involved.
Step 1: The scammer initiates contact
Pig butchering scams often begin with a smishing (SMS phishing) attempt, or an unsolicited message via social media or dating apps. Scammers typically target individuals they assume have substantial savings or those nearing retirement. They often consider such groups more lucrative and vulnerable to manipulation.
Scammers may pretend to have a wrong number before casually striking up a conversation. In other cases, if your data has been leaked online or exposed by data brokers, they may already know your name and where you live. Matching on Tinder is another preferred pretext.
To make their approach more convincing, scammers are increasingly turning to generative AI to craft highly personalized messages, making their communication appear natural, authentic, and fluent. Some even leverage deepfake technology to create realistic images or videos of fake personas.
Step 2: They slowly build trust
If you respond to the message, scammers use social engineering tactics to gain your trust and cultivate a relationship. They gather personal details to use later while fabricating similarities to make themselves seem relatable.
Over time, this false connection makes you more likely to believe their investment scheme.
They often attempt to move the conversation to Telegram, WhatsApp, or other minimally moderated platforms, reducing the risk of detection. Patient pig butchers may spend weeks or even months chatting and flirting with their victims, before moving on to the next step of the fraud scheme.
Step 3: They introduce investment opportunities
Once the scammer has established trust, they shift the conversation toward money — often a so-called lucrative investment, usually in cryptocurrency. They may share fake screenshots of impressive returns to make their investment seem credible and claim to have personally profited.
Step 4: They collect the funds
After convincing you to invest, the scammer directs you to transfer funds using cryptocurrency or digital payment platforms, which make transactions difficult to trace or reverse. They may send you to a fake investment platform or custom app designed to show inflated returns.
You will see what appears to be rapid growth on your initial investment, reinforcing trust and encouraging larger deposits. In some cases, they will display real market data to create the illusion of legitimacy, but the actual investment and account balances are fabricated.
Step 5: They disappear forever
Once the scammer has taken as much as possible or senses you’re getting suspicious, they vanish without a trace. The investment platform suddenly stops working, the website goes offline, and their phone number is disconnected. If they’ve also stolen your banking details, they may drain any remaining funds before disappearing.
Since you technically invested in cryptocurrency willingly, recovery is unlikely. Banks and government agencies usually can’t help, leaving you with financial loss and the emotional distress of being deceived by someone you trusted.
A real-life pig butchering scam story
Even successful, intelligent people can fall for pig butchering scams. Shan Hanes, a former CEO of Heartland Tri-State Bank in Kansas, embezzled $47 million from his bank after falling victim to a pig butchering scam. Over the course of eight weeks, he funneled the stolen funds into cryptocurrency wallets controlled by scammers who promised massive returns.
Desperate to recover his “investments,” Hanes drained a church fund, an investment club, and his daughter’s college savings before the scam wiped out everything.
The bank collapsed, leading to an FDIC takeover. Hanes’ actions devastated his small community, leaving shareholders bankrupt and some residents unable to retire or afford medical care.
Who’s behind pig butchering scams?
Pig butchering scams are typically orchestrated by highly organized criminal gangs operating on a large scale. Many of these groups are based in Southeast Asia and rely on trafficked victims, forced into carrying out the fraud against their will.
The victims of trafficking are often young, college-educated individuals from neighboring countries, lured by fake job offers. Upon arrival, traffickers take their passports, leaving them unable to escape.
Workers must meet scam quotas or face violent punishments. They work long shifts in squalid conditions under strict control. These operations fuel a global fraud network that exploits both scam victims and the trafficked workers behind them.
How to spot the pig butchering scam
Knowing how to spot the pig butchering scam can help you avoid falling for this scheme. Watch out for the following signs you’re talking to a scammer:
- You receive texts or social media messages from unfamiliar numbers or strangers.
- You match with someone on a dating app who seems too good to be true.
- Conversations turn personal, even though you are strangers.
- You are nudged to move to another platform, like Telegram, which has less robust moderation.
- They persistently message you, even if you don’t respond.
- They refuse calls, avoiding any direct voice or video communication.
- They pressure you to invest in cryptocurrency or send money via bank transfer.

How to protect yourself from the pig butchering scam
Taking the right precautions can help protect you from pig butchering scams. Use the following best practices to stay safe.
- Use scam detection tools: Fraudsters are getting harder to spot. AI-powered scam detection tools like those included in Norton 360 Standard can help you identify deepfake videos, and tell you whether a message is legit or from a scammer.
- Ignore messages from strangers: Scammers often initiate contact through random texts or social media messages. If you don’t recognize the sender, don’t engage.
- Never blindly follow investment advice: Before investing, conduct your own research. If you still have questions about the investment, consult a finance professional.
- Verify a platform’s legitimacy: Scammers can create convincing fake websites and apps. Check for licensing, read reviews, and confirm platforms’ legitimacy through neutral sources.
How to report a pig butchering scam
If you suspect you’ve encountered a pig butchering scam, report it to the Federal Trade Commission (FTC) at ReportFraud.ftc.gov and inform law enforcement. Providing details like messages, transaction records, and scammer contact information can help the authorities investigate and prevent further fraud.
Keep yourself off the chopping block with Norton 360
Scammers are getting more sophisticated, more patient, and harder to detect. You may spend months chatting online with a fraudster from Tinder without ever suspecting you’re being conned. Fortunately, anti-scam technology is evolving just as quickly.
Norton 360 Standard, with its cutting-edge, AI scam-detection features, can help you make the call when you’re in doubt about a message’s authenticity. Just upload a screenshot of a suspicious email, text message, or social media conversation, and you’ll know in seconds if you’re dealing with a scammer. And, thanks to award-winning malware, ransomware, and hacking protection, you’ll be safer from more traditional cyberthreats, too.
FAQs
What should you do if you fall for a pig butchering scam?
If you fall for a pig butchering scam, immediately stop all communication with the scammer, report the incident to your bank or payment provider, and file a report with authorities such as the FTC and local law enforcement. You should also consider changing your passwords and monitoring your financial accounts for suspicious activity.
Is cryptocurrency a scam?
Cryptocurrency itself isn’t a scam, but the relatively unregulated space it operates in can create conditions conducive to cryptocurrency scams. And crypto’s anonymity makes it popular with fraudsters.
Can I get my money back if I fell for the pig butchering scam?
Getting your money back from a pig butchering scam is nearly impossible, since cryptocurrency transactions are hard to trace or reverse. But it’s still a good idea to report the scam to the authorities and your bank.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.








Want more?
Follow us for all the latest news, tips, and updates.