What is quishing? Learn to spot QR code phishing and stay safer online
Cybercriminals have weaponized the convenience of QR codes, giving rise to a stealthy new threat: quishing attacks. Keep reading to learn the definition of quishing and how to spot QR code scams. Then get Norton 360 Deluxe to help protect against dangerous links hidden within QR code scams.

QR codes provide a quick and convenient way to access websites, log into accounts, or pay for a meal in a restaurant. But as QR codes grow more ubiquitous, the risk of QR code scams rises.
What is quishing?
Quishing is a cyberattack in which cybercriminals use QR codes to spread malware, steal personal information, or defraud people. The term is a combination of “QR code” and “phishing.”
In quishing attacks, scammers place malicious QR codes in public or disseminate them on the internet. Scanning them prompts users to download harmful files or navigate to dangerous websites that can harvest sensitive information. Quishing attacks can result in malware infections, stolen funds, or even identity theft.
How does quishing work?
Quishing works by using QR codes to hide links to malicious websites, dangerous files, or spoofed payment portals. Then, if someone scans the malicious code, they could end up on a dangerous website or their device could get infected with malware.
Unlike traditional phishing links, which spam filters can often detect, QR codes obscure a link’s destination, making it potentially more difficult for spam filters to detect them. Accordingly, malicious QR codes have quickly risen in popularity within email phishing campaigns, accounting for almost 11% of phishing attacks in 2024, compared to less than 1% in 2021.
Here’s a step-by-step breakdown of how quishing works:
1. Scammers disseminate QR codes
Scammers can use free, widely available tools to generate QR codes leading to spoofed websites. The only difference between a regular QR code and a quishing code is the nature of the link or file embedded within it. Then, the scammer places these QR codes in locations where people are likely to scan them, such as:
- Flyers and posters: Fake promotional offers or event ads in public spaces.
- Emails and text messages: Embedded in traditional phishing messages instead of a link.
- Public transport locations: On schedules, ticketing systems, or around stations.
- Pop-up ads: Served via pop-ups, notifications, or malvertisements.
- Menus: On restaurant or cafe menus for fake payment systems.
- Parking meters and ATMs: Overlaid on legitimate payment QR codes.
- Social media feeds: Shared as DMs, part of fake contests or campaigns, or Ticketmaster scams.
2. People land on malicious sites
The quishing attack begins in earnest when you scan the QR code and follow the link. Just like clicking a link in a phishing email or smishing text, quishing links can lead to shady websites or automatically infect your device with various types of malware like viruses, ransomware, or spyware.
Many scam QR codes lead to malicious websites that mimic real ones — similar to clone phishing attacks. These sites may contain fake payment portals or login pages that allow fraudsters to steal your payment information, login credentials, or other sensitive information.
3. Victims reveal personal information
Falling for a quishing scam can result in stolen funds, identity theft, or other nasty consequences. When you enter your credit card information into a fake payment portal, you reveal sensitive financial information to cybercriminals, allowing them to make fraudulent purchases and potentially drain your accounts.
Similarly, a QR code that leads to a fake login page can trick you into revealing your email address, passwords, or other personal information. This opens the door to account hacks — especially if you don’t have a password manager and use the same password everywhere. Hackers may then sell the information they harvest on the dark web.
If scammers collect enough information, they may even be able to steal your identity to open bank accounts, take out loans, or pay for costly medical treatments in your name.
Real-life quishing example
A recent Gen Threat Report details how the hacker group CryptoCore used quishing to scam victims out of more than one million dollars in cryptocurrency in 2024.
Scammers mimicked well-known brands and personalities like Elon Musk, Donald Trump, and Apple using deepfake videos disseminated via compromised social media accounts, some of which had millions of followers.
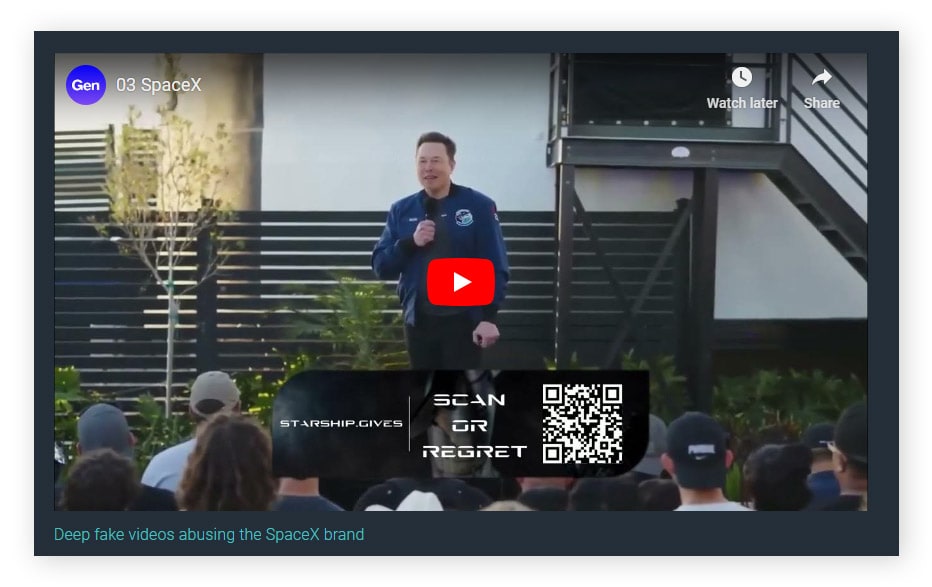

The videos, which contained QR code links to fraudulent websites, promised lucrative cryptocurrency giveaways. Instead of getting free crypto, however, victims were tricked into sending their own cryptocurrencies to scammers’ wallets.
How to spot a quishing attack
While fake QR codes look no different from real ones, there are ways you can suss out a likely quishing attack. Most important, always preview a QR code link before clicking it. On most phones, when you scan a QR code with your camera app, the URL will appear in a preview box.
Suspicious links may have misspelled domain names or contain unusual characters. Remember that it’s best to avoid following any links that come from senders you don’t know. If the link looks suspicious in any way, don’t click it.
If you still have doubts, try Norton Genie — a free AI-powered scam detector that can help you determine in seconds whether a link is dangerous.
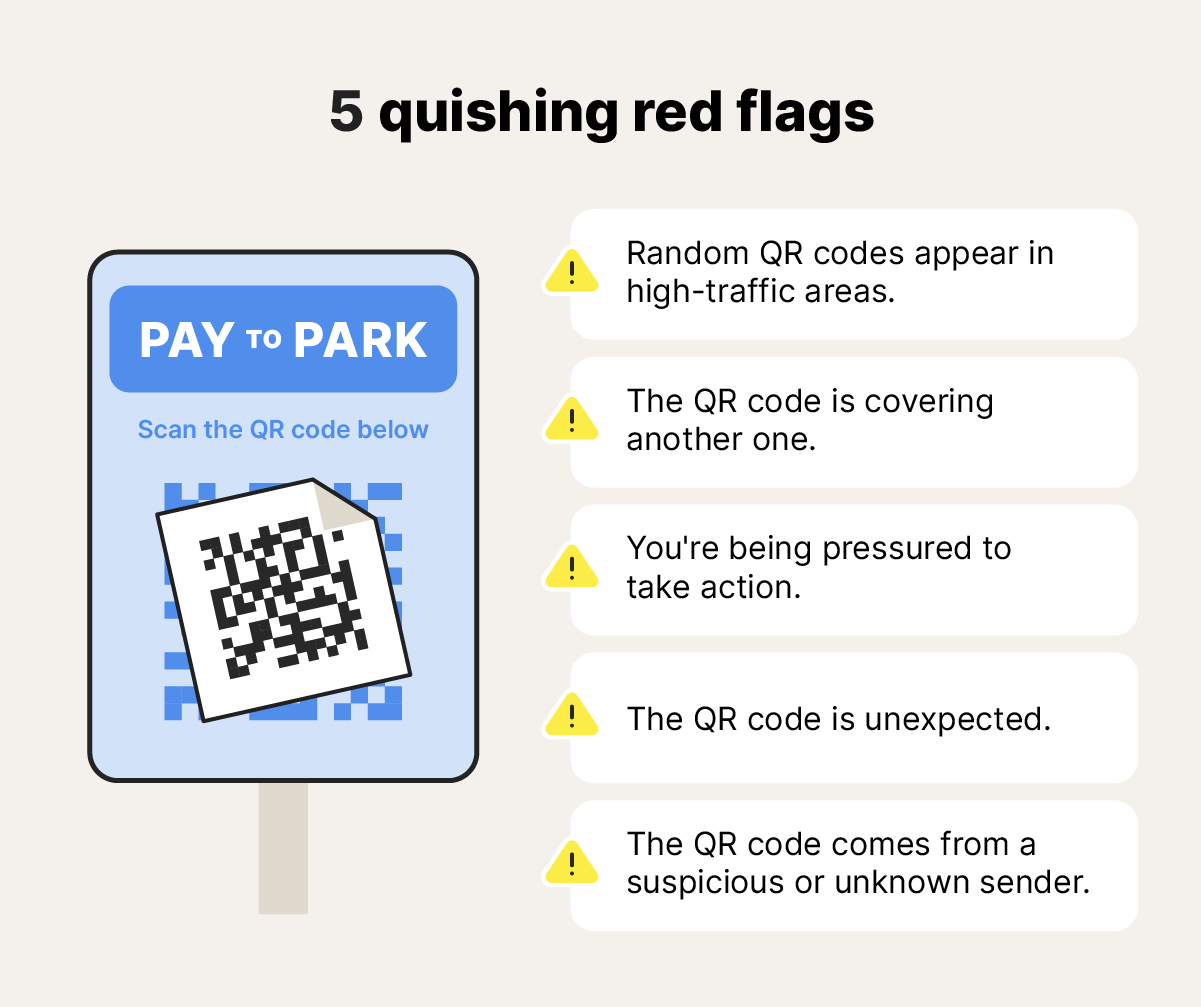
Finally, remember that a QR code may be part of a quishing attack if it:
- Appears in a high-traffic area: Random QR codes found in public near high-traffic areas might be scams.
- Seems to be covering something: QR codes that have been stuck on top of something else, like a poster or official sign, might be scammers trying to trick you.
- Lacks context: Unexpected QR codes sent via text or email with little contextual information could be dangerous. Cybercrooks may hope you’ll scan them out of curiosity.
- Is accompanied by pressure tactics: Be wary of urgent language that instills panic, mentions too-good-to-be-true, time-sensitive deals, or threatens you if you don’t click the link in the QR code.
- Comes from a suspicious sender: QR codes sent via email or text that come from unknown senders are prime candidates for quishing attacks.

What to do if you scanned a malicious QR code
If you scanned a malicious QR code, quick action can minimize potential damage. Disconnect from the internet immediately to block data extraction or malware installation, and then follow the steps below according to your situation:
- If you downloaded a file: Run an antivirus scan with a reputable antivirus like Norton 360 Deluxe to help find, block, and remove malware that’s infected your device.
- If you opened a malicious page: Avoid clicking anything or entering personal information. Simply close the tab and clear your browser’s cache to help remove any potential trackers or cached malware.
- If you revealed your username and password: Change your passwords immediately, enable two-factor authentication (2FA), and monitor your accounts for unusual activity.
- If you exposed personal or financial information: Alert your bank, update your account security settings, block your card, freeze your credit, and monitor your credit.
If you have fallen victim to a QR code scam, file a report with your local police department and notify your bank. Also report the quishing attack to the Federal Trade Commission (FTC), which could help others avoid similar attacks in the future.
To help protect your identity in the aftermath of a quishing attack, consider using Dark Web Monitoring with Norton 360 Deluxe to check if your personal information has been sold or shared in shady corners of the web.
How to prevent quishing attacks
The simplest way to prevent a quishing attack is to avoid interacting with suspicious QR codes altogether. Here are some additional tips to help you prevent quishing attacks:
- Think before you type: Never input sensitive information unless you’re positive the site is legitimate. Free AI tools like Norton Genie can help you make the call if you’re unsure.
- Get mobile security: Advanced security software, like Norton 360 Deluxe, can help detect deepfake videos used to spread quishing scams, and block unsafe websites if you accidentally scan a malicious QR code.
- Update your devices: Regularly update your phone and apps to patch any security vulnerabilities.
- Report suspicious QR codes: Report suspicious QR codes and phishing sites to the FTC to help prevent attacks on others.
- Avoid public QR codes: Only scan QR codes from trusted sources. Whenever possible, go directly to a website by entering its URL.
- Inspect QR codes carefully: If you must scan a public QR code, inspect it to make sure it hasn’t been tampered with. Remember that QR codes on stickers are riskier than codes covered by glass.
- Only scan QR codes with your camera app: Some third-party scanning apps offer extra features, but the companies behind these apps may violate your privacy. Such apps may also contain dangerous ads.
Following these tips and understanding how to protect yourself from phishing can greatly reduce your risk of falling victim to a quishing attack.
Help protect against quishing
The rise of QR code scams illustrates how fast cybercrime evolves. Fortunately, you can count on the good guys to keep pace with emerging threats.
Get Norton 360 Deluxe and unlock a powerful cybersecurity suite packed with state-of-the-art protection to help prevent account takeovers, detect deepfake videos, block malware and hackers, and safeguard your device in the event of a quishing attack.
FAQs
What is a QR code?
A QR code, or quick-response code, is a scannable barcode that looks like a random combination of squares inside a larger square and is usually black and white. QR codes can store information like links, text, files, or login portals, which viewers can access using a smartphone camera, QR code reader, or other scanning device.
How does quishing differ from phishing?
Quishing is a type of phishing, but whereas traditional phishing methods usually involve clicking a link, quishing involves scanning a QR code. In both types of cyberattacks, hackers impersonate legitimate entities to trick people into revealing sensitive information like passwords, credit card numbers, or personal data.
What is QRLjacking?
QRLjacking is a type of quishing that takes advantage of sites that allow you to log in via a QR code. Instead of logging you in, QRLjacking lets cybercriminals hijack your session and take over your account.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.