How to remove a hacker from my phone + tips to prevent hacking
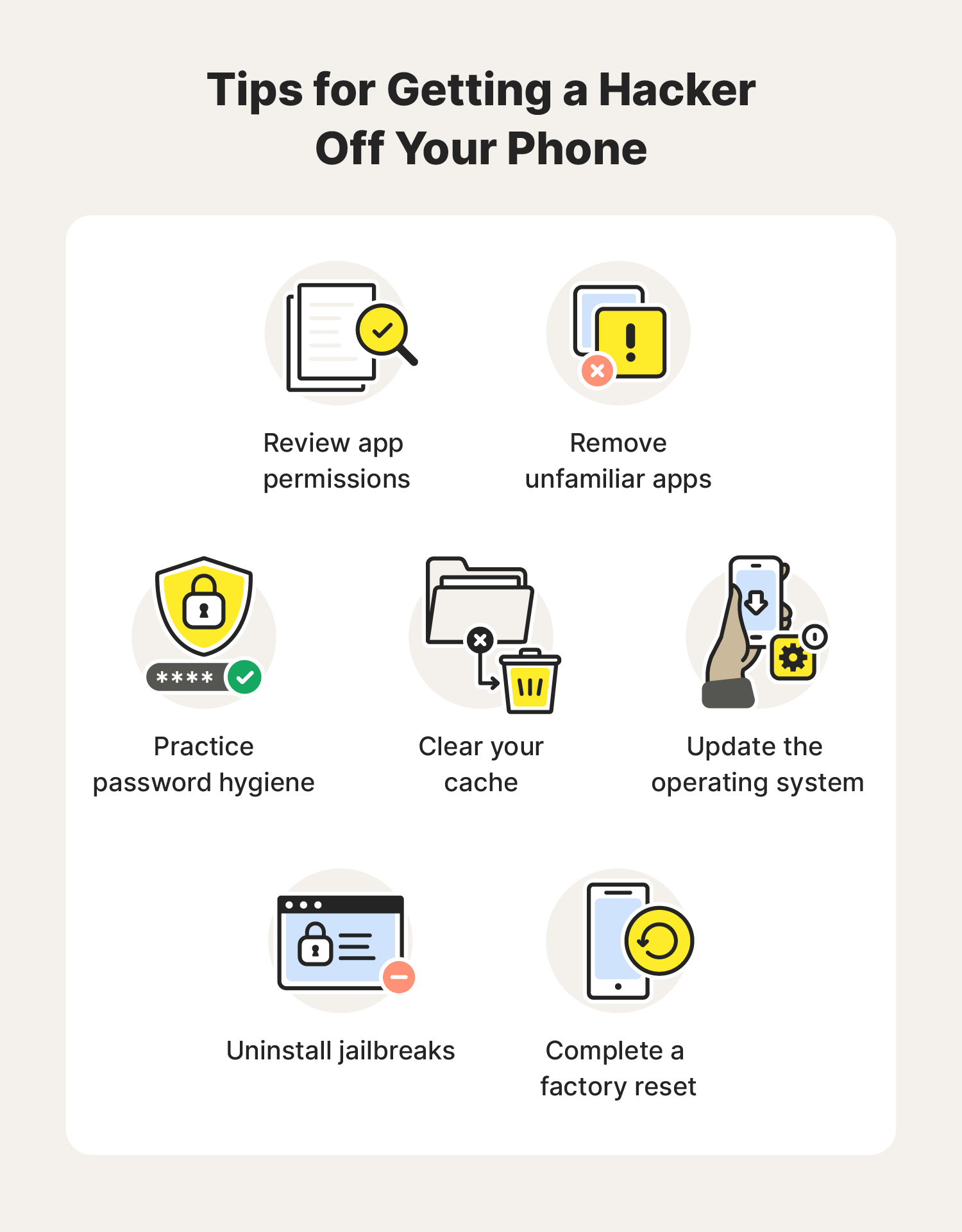
To remove a hacker from your phone, you should review app permissions, remove unfamiliar apps, update the operating system, clear cache, or do a factory reset.

Whether it’s sending emails, taking photos, or checking your bank account, mobile devices put your personal data right in the palm of your hand—and, if your phone gets hacked, right in the hands of others. Continue reading to learn how to remove a hacker from your phone, signs of a hacked phone, and how you can protect yourself with mobile security software like Norton 360 Deluxe.
How to get a hacker off your phone
Cybercriminals can hack your phone if you use unsecured networks, your information is leaked in a security breach, or if they steal your phone and use brute force attacks. In doing so, hackers may gain access to your:
- Social media
- Online banking
- Photos
- Text messages
- Home security system
- Smart appliances
If you suspect a hacker is messing with your device, the first thing you may ask Google is, “how to remove a hacker from my phone.”
Review app permissions
After downloading an app, you may be asked for permission to access various information, including your:
- Camera
- Microphone
- GPS location
- Contacts
- Photos
To ensure an app isn’t violating your privacy—and, in turn, hackers aren’t either—you can review or change app permissions in your settings.
On an iPhone, you can find out which apps can access your information by going to Settings, then Privacy.
To keep your Android secure, go to Settings, then Apps, and then Privacy.
Remove unfamiliar apps
As a rule of thumb, if you didn’t download the application yourself, then you should delete it. Unfamiliar apps could be malicious tools used by a hacker. Removing unwanted apps is also a great way to keep your phone clean.
Many phones have pre-installed bloatware, including weather, music, or messaging apps. Keep in mind that you may not be able to remove these apps from your device.
Practice password hygiene
These days, giving someone your password is like giving someone the keys to your house. With so much sensitive information stored on our phones and online, a password is often the final line of defense between a hacker and your valuable data.
Using strong passwords can stop hackers from taking over your digital life with password attacks. For extra security, be sure to change your passwords periodically, especially if you think your phone may be under attack.
Be sure to monitor your credit statements closely for the next year or two or even implement a credit freeze if you think your financial information was compromised.
Clear cache
To make your browsing experience quicker and more enjoyable, your phone temporarily stores data from the websites you visit. In case you’ve encountered any malware in your web browsing routine, clear your cookies and cache regularly.
Update the operating system
Updating your operating system (OS) is a great way to keep your device running smoothly. In addition to added features and bug fixes, these updates contain security patches to keep your phone secure. Just as you wouldn’t leave your door unlocked when you’re out of town, you shouldn’t leave your phone without proper security.
Uninstall jailbreaks
People have been jailbreaking their phones and other devices for years. It allows you to customize your phone's features—at a cost. A jailbroken phone may be more vulnerable to cyberattacks and prevent you from updating your operating system, which often includes security patches that prevent zero-day exploits.
Complete a factory reset
If all else fails, you can perform a factory reset on your device. Before doing so, back up your important files, as a factory reset will wipe all of your files and personal data from your phone’s internal storage. On the plus side, a factory reset will also remove any malicious files a hacker may have been using.
Norton 360 Deluxe makes safe browsing on your phone and mobile devices easier, taking the guesswork out of protecting your devices with a password manager, VPN, and even dark web monitoring to help keep you safe online.
Common signs of a hacked phone
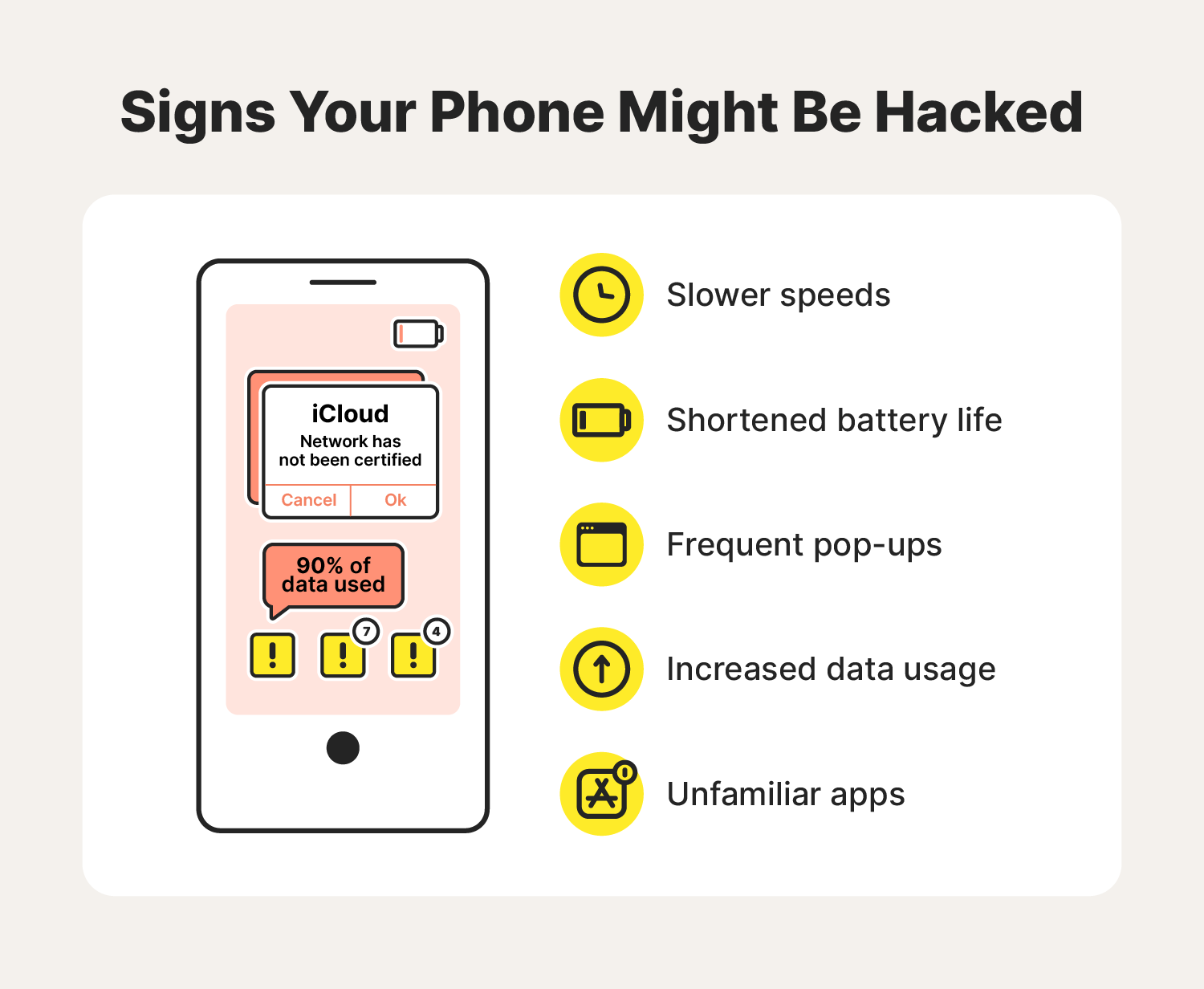
Are you unsure if your phone was hacked? Luckily, these warning signs may help you figure it out. Let’s take a look at some of the most common red flags of a hacked phone.
Slower speeds
Once your device is under the control of a phone hacker, malicious applications may use up a large amount of its computing power. While it’s common for phones to slow down with time, malware can cause a sudden decrease in speed.
Shortened battery life
Hackers often use malware in fraudulent apps when breaking into your phone. These methods will use up a lot of your phone’s battery power, therefore shortening your battery life.
Frequent pop-ups
Combatting frequent pop-ups when browsing the web may be a sign your phone is under attack. Common examples of malicious pop-ups include:
- Notifications you’ve won a prize or contest
- Fake virus alerts
- Warnings that your personal information has been leaked
If you see any of these pop-ups, close your browser immediately, because clicking on anything in the window may further expose your phone to cyberattacks.
Suspicious increase in data usage
Malicious applications are also known for their high data usage. Because these apps will constantly run when you’re under attack, you may notice a higher data usage on your monthly bill.
Unfamiliar apps
If you notice any new apps you don’t remember installing, your phone could be compromised. Many smartphone hackers rely on malware disguised as phone applications to trick users into giving up personal information.
9 phone hacker protection tips
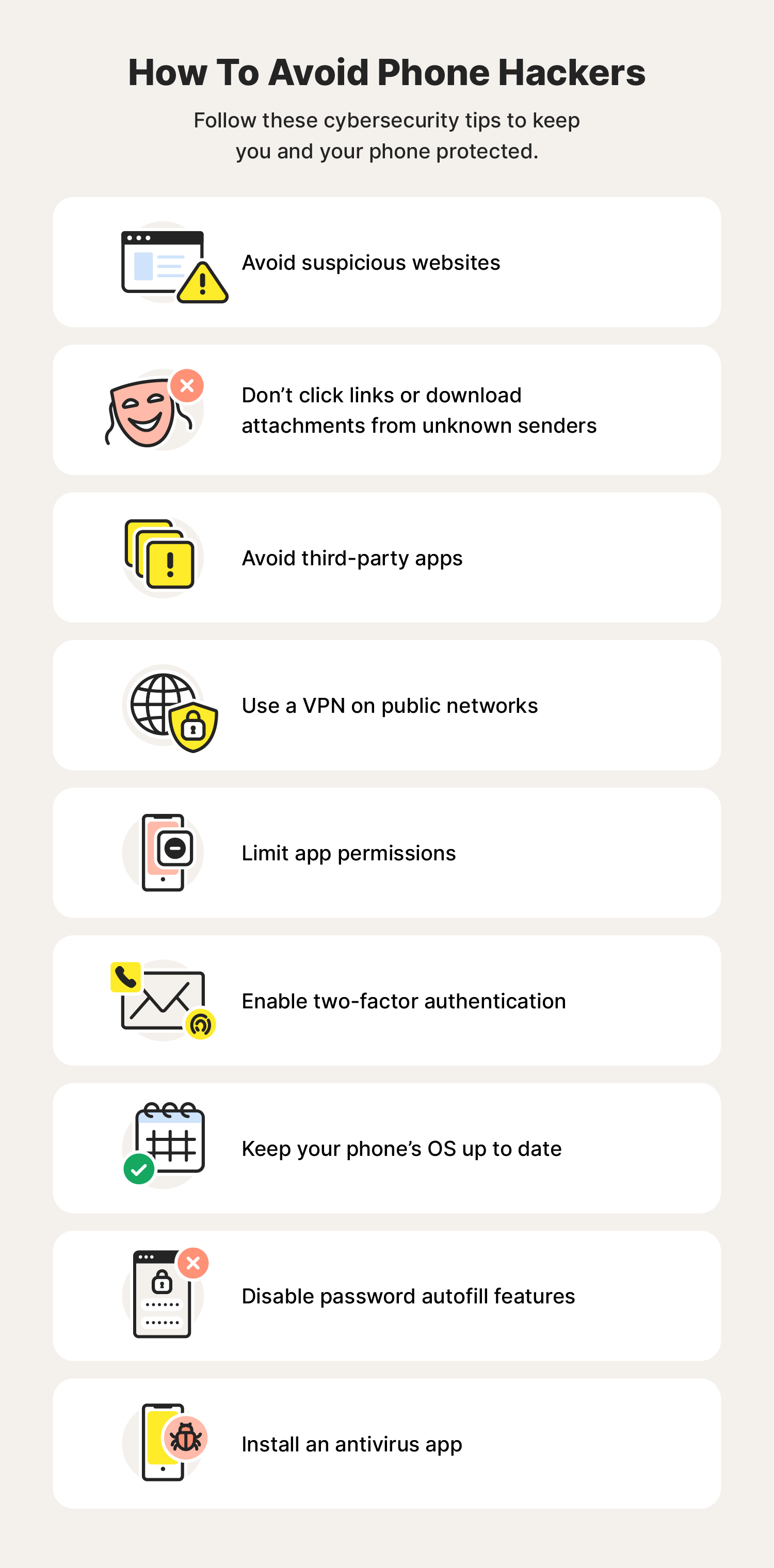
Now that you know how to get rid of hackers, it's time to ensure they’ll never come back. Follow these tips to keep your phone safe from mobile hacking:
- Install an antivirus app: Using an antivirus app can protect your phone from hackers.
- Never visit any suspicious websites: In many cases, suspicious website URLs include numbers, symbols, or hyphens.
- Avoid clicking links and attachments from unknown senders: Proper email security practices are key to protecting your data. By clicking a strange link, you could accidentally install malware on your phone.
- Use a VPN on public networks: Using a VPN can help keep your web connection secure and encrypted.
- Disable password autofill features: Disabling autofill can prevent a hacker from easily logging into your accounts.
- Avoid third-party apps: Unlike an app from your phone’s native app store, third-party applications could be malware in disguise.
- Enable two-factor authentication (2FA): Enabling 2FA adds an extra layer of security between a hacker and your personal information.
- Limit app permissions: By limiting app permissions in your settings, you can control what information your apps have access to.
- Keep your phone’s operating system up to date: Installing the latest OS ensures your phone has the most up-to-date security patches.
Whether you’ve dealt with a phone hacker before or are just now learning about it, following these tips can help keep you and your device safe from mobile security threats.
Help keep you and your phone safe
Norton 360 Deluxe helps protect you from hackers by constantly scanning your devices and blocking viruses, malware, ransomware, and hackers. It also includes a password manager and VPN to help you create better password habits and keep your searches private.
FAQs about how to remove a hacker from your phone
Do you have some lingering questions about phone hacking? We have answers.
Can someone hack your phone from your number?
Yes, hackers often commit SIM swap fraud by tricking cell phone carriers into rerouting a stolen number to a new phone. However, many service providers require security questions, PINs, and passwords before completing that kind of request.
Is there a way to tell if your phone has a virus?
You may be able to tell if your phone has a virus if you begin to notice a change in your phone’s performance. Examples include:
- Slow speeds
- Frequent pop-ups
- Shortened battery life
These symptoms can stem from any malicious applications that are running on your device.
Will resetting your phone remove hackers?
Yes, resetting your phone should remove malware that hackers use to control your phone.
Is there a way to scan your phone for hackers?
Antivirus created for your phone can scan your device to determine if it’s been hacked or compromised. Norton Mobile Security for Android and iOS devices scans your system for vulnerabilities so you can take action and protect your device.
Can hackers see through your phone camera?
If a hacker gains access to your device, they may be able to control and use your phone’s camera. To avoid this, always take the proper steps to protect yourself online and block hackers from accessing your device.
What happens when a hacker tracks your phone?
If a hacker gains access to your phone they could monitor your browsing, which apps you use, your location, and even anything you type into your phone. Anything you do or store on your device could potentially be compromised.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.





Want more?
Follow us for all the latest news, tips, and updates.