Android vs iPhone security: which is safer?
The Android vs iPhone security debate is not easy to resolve. The answer can depend on the model and settings of your device, how you use your phone, and the type of threat you may face. Below, we examine how Android and iPhone stack up in terms of device, operating system, and app store security. And regardless of what kind of phone you have, get a mobile security app to help protect against malware, hackers, and other online threats.

With so many of us shopping and banking on our phones these days, mobile devices and their operating systems—namely, Apple’s iOS and Google’s Android—appear to be a more attractive target for malware attacks.
If safety is a priority for you, and you want to keep your Android, iPhone, or iPad free of viruses and other malware, you may be wondering if Android or Apple security is better. While Apple may have a reputation as the more secure option, the answer isn't so simple. Read on for a thorough breakdown of Android security vs iOS security.
Android vs Apple device security overview
A key difference between Android and Apple devices is that the Android operating system is used by different mobile phone manufacturers, all of whom have slightly different security practices. Meanwhile, Apple operates in a closed system, with standardized security measures across all its devices. That difference leads to certain advantages and disadvantages for both device types.

iPhones and Androids come with certain security measures.
Another crucial factor to consider is the age of your device. Some sources suggest that iPhones “stay current for longer than Android phones” because Apple supports older devices for many years. If that’s the case, then using an older Android device may be riskier than using an older iPhone as software updates are critical to security.
However, both Androids and iPhones are vulnerable to hacking, spyware, and other threats, especially if you don’t use good digital hygiene. For example, regardless of how often you update your phone, according to research from the NSA you should turn it completely off and back on again at least once a week.
Android device security
Since Android devices are made by a wide range of manufacturers, standardizing security measures across the platform is extremely difficult. But some manufacturers provide strong security features to strength Android’s built-in protections. For example, the Samsung Knox security platform, which has been certified by multiple government agencies, comes pre-installed on most Samsung devices to help protect user data and the devices that house it.
Another example of an Android device with strong security is the Google Pixel, which comes with a Titan M2 security chip that underpins different security sensitive functions to help strengthen the Android operating system’s built-in security measures.
But Android’s diversity of manufacturers also introduces potential weaknesses, as some brands may not prioritize security the way that Samsung and Google do. If you choose an Android, do your research and buy from a high-quality manufacturer with a good reputation for security.
Apple device security
Because so much of Apple’s device and app ecosystem is closed—its walled garden of proprietary services and features and the requirement that Apple vet any new app on its App Store—security vulnerabilities are perceived to be more difficult for cybercriminals to find.
Apple devices also come with the built-in Secure Enclave, a special subsystem separate from the main processor that stores sensitive data like biometrics for Touch ID and Face ID. Secure Enclave has its own set of security rules, so that even if the main part of your iPhone is compromised, the Enclave stays locked up.
However, Apple devices are not immune to security threats. That’s especially true if you jailbreak your phone. Jailbreaking opens new capabilities on the device—such as changing digital assistant Siri’s voice or offering a different selection of apps to download. But unless (and even if) you know what you’re doing, jailbreaking your device is dangerous because built-in security may get compromised, leaving your device more vulnerable.
No matter what phone and operating system you have, mobile security is essential. Norton 360 for Mobile provides powerful protection to help combat the variety and sophistication of today’s online threats. With an award-winning, real-time malware detection engine and a built-in VPN, Norton 360 for mobile will help keep your phone safer and running smoothly.
Android vs. iOS operating system security
Apple’s iOS is known for its tight security since Apple doesn’t share its source code with developers or allow users to easily modify their device code. That can make it more difficult for hackers to find vulnerabilities in iOS devices.
By contrast, Android devices rely on open-source code, providing both users and manufacturers more flexibility to customize devices. This flexibility can be an advantage, but too much tinkering with an Android device can also lead to security issues.
Android operating system
Android prides itself on its open-source operating system, reflected in the tagline “Android is for everyone,” shared on the company’s website. The company reports that there are currently nearly 1,300 brands producing Android devices and that devices in some markets sell for as little as $50.
Here’s a closer look at some of Android’s main strengths and weaknesses as an operating system:
- Open-source code: Android users can modify the source code of their devices. While this flexibility allows for customization, it can also introduce potential vulnerabilities that could be exploited by malicious actors.
- Multiple manufacturers: The Android operating system can run on mobile devices produced by a wide range of manufacturers, which means more consumer choice and lower-cost options. But some manufacturers prioritize security less than others, and this could lead to weaknesses in devices or their programming.
- Varied update frequency: Android updates vary in frequency across devices, which could pose a security risk for some users. While the updates originate with Google, it is up to the individual manufacturers to adapt and apply those updates to their specific hardware or software, and some manufacturers react faster than others.
| Android OS | |
| Pros | Cons |
| Open-source code allows for customization and innovation. | Increased customization can introduce security vulnerabilities. |
| Diversity of manufacturers provides a range of devices and prices. | Manufacturers have different security standards. |
| Regular updates address vulnerabilities and add new features. | Some manufacturers may be slow to roll out security updates. |
| Global popularity caters to different preferences and budgets. | Widespread adoption can make an appealing target for cyberattacks. |
iOS operating system
Apple’s iOS, which powers iPhones, iPads, and iPod Touches, is a closed-source operating system tightly controlled by Apple. Since iOS doesn’t work on phones from different brands, Apple can more easily ensure that its software and hardware work together.
Here’s a look at a few of iOS’s strengths and weaknesses:
- Closed ecosystem: Apple controls its whole ecosystem, helping create a consistently secure user experience. However, it may limit user customization and third-party app availability.
- Apple-made devices: Being exclusive to Apple is good for device security because it reduces the risk of vulnerabilities stemming from diverse hardware. But with a more limited range of Apple-only products, customers are left with fewer options.
- Update frequency: iOS gets updated frequently, which is great for security. Plus, security patches are usually available to all compatible devices, even older ones.
| iOS | |
| Pros | Cons |
| A closed ecosystem helps tighten security controls. | Less customization and limited availability of third-party apps. |
| Reduced risk of security issues stemming from diverse device manufacturers. | Limits consumer choice to Apple devices. |
| Frequent operating system updates covering many devices. | Fewer device options means Apple devices are more expensive. |
Android vs iPhone app store security
Since the Android operating system is hugely popular worldwide, controlling more than 70% of mobile operating system market share, developers are constantly building new apps to run on the system. That means a lot of choice, but also more risk. Apple’s App Store, on the other hand, offers a meticulously curated selection that may tighten security, but it also results in less variety for users.
Android app store security
Google Play is the official app store for Android devices. It has a rigorous app review process, but no process is perfect—it's still possible for fake Android apps to sneak into Google Play.
One of the main issues with Android app security is that users can navigate to Android settings and install third-party apps—software from sources outside the official Google Play Store. These apps can bypass the Google Play Store review process, potentially posing security risks.
Apple App Store security
Apple also has tight entry requirements for the Apple App Store. This makes it challenging for developers to have their apps accepted and reduces the likelihood of malicious apps infiltrating the store. However, it also means a more limited selection for Apple users, with Android boasting more than twice the number of apps compared to Apple.
Historically, third-party app stores weren’t allowed on iOS. But that changed in March 2024 thanks to the European Union’s Digital Markets Act, which forces Apple to permit the installation of alternative app stores on iOS devices for users in the EU.
Tips for better phone security on iPhone and Android
Android and iOS users alike need to be aware of possible risks that come from downloading third-party apps. Additionally, users on both platforms can be vulnerable to social engineering attacks, where cybercriminals attempt to trick users into giving up sensitive data.
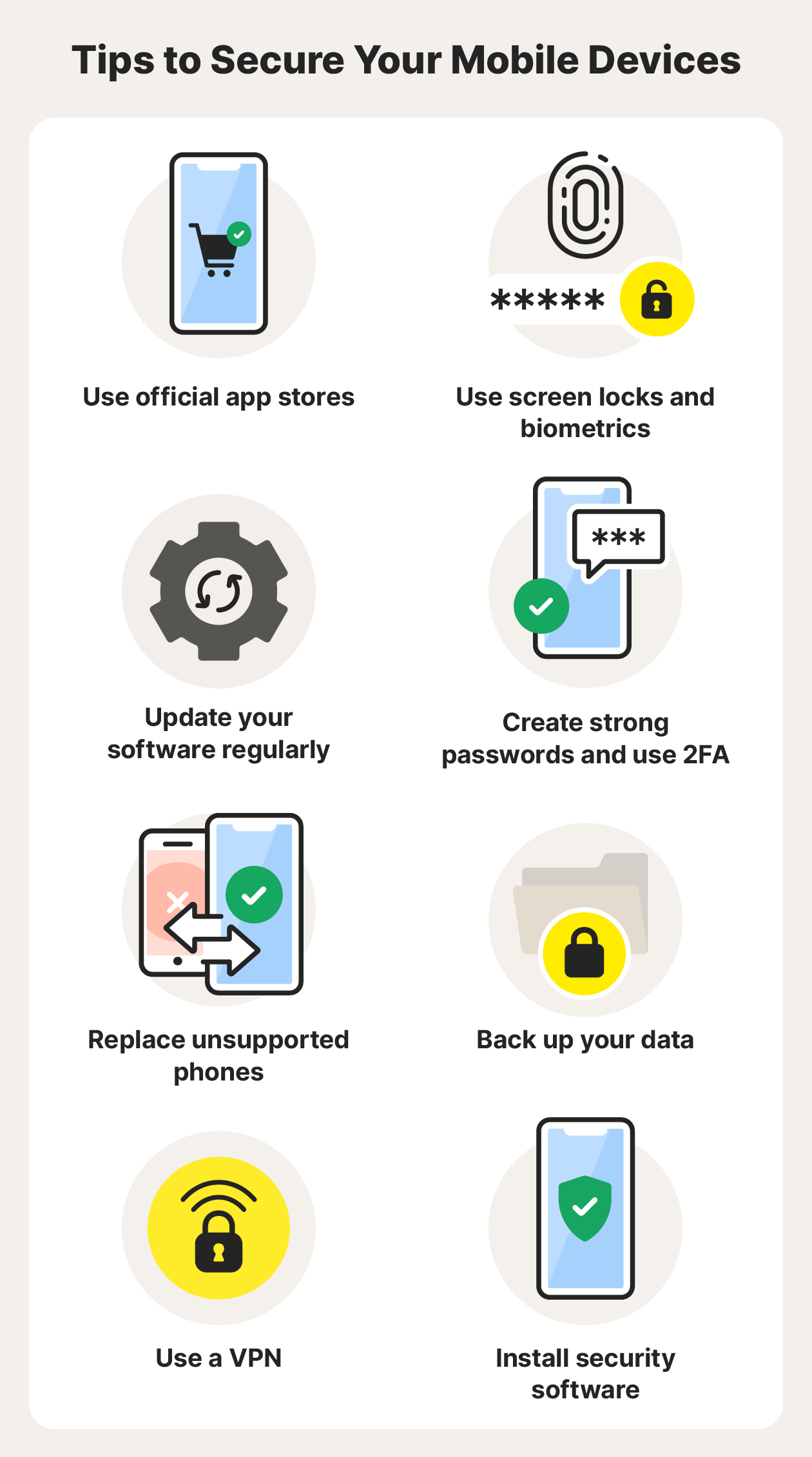
Follow these security tips for Android and iOS devices:
- Use official app stores: Stick to trusted sources when downloading apps to minimize the risk of malicious software ending up on your device.
- Use screen locks and biometrics: Take advantage of built-in security features to help protect your device against unauthorized access.
- Update your software regularly: Keep your device secure by promptly installing software updates, which often include crucial security patches.
- Create strong passwords and use 2FA: Use strong and unique passwords and two-factor authentication for your online accounts; and store your passwords in a password manager.
- Replace unsupported phones: When your phone is no longer supported, upgrade to a newer model to get continued protection against potential vulnerabilities.
- Back up your data: Protect your sensitive data by creating encrypted backups and enabling remote data wiping in case of phone loss or theft.
- Use a VPN: Encrypt the data you send and receive online and help protect your privacy on public networks by using a virtual private network (VPN).
- Install security software: Use reputable security software to help protect your mobile device against cyber threats.
Stay safer while using your phone
As you can see, there’s a lot you can do to stay safer on your phone. But with so many invisible online threats, using cybersecurity software like Norton 360 for Mobile should be high on your list.
Norton 360 for Mobile packs powerful security and antivirus features to help protect your mobile device against malware, hacking, and other threats. Plus, it comes with a built-in VPN to encrypt the data you send and receive online.
FAQs about Android vs iPhone security
We’ve covered the essentials, but here are some more questions and answers in the Android vs iOS security debate.
Can iPhones get viruses?
iPhone viruses are rare, but yes, Apple devices can get viruses and other types of malware. A malware infection is more likely if you jailbreak your device, which removes key layers of built-in security.
Is it easier to hack an iPhone or Android?
All devices are susceptible to cyberattacks, regardless of model or operating system. Because of open-source code and the ability to easily download third-party apps, Android devices are often perceived to be more susceptible to hacking. But that doesn’t mean iPhones are immune to cyber threats.
Is iOS or Android more popular?
Globally, Android is more popular than Apple, with more than 70% of the market. But in North America, the race is much tighter, with Apple holding about 54% of the market share.
What is the most hacked phone?
It’s difficult to definitively state which specific phone is the “most hacked.” Android’s global popularity, open-source code, and use on many low-cost devices are reasons why Android devices are often considered more vulnerable to hacking than iOS devices.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.







Want more?
Follow us for all the latest news, tips, and updates.