What is blockchain security? An overview
Explore the ins and outs of blockchain security with this comprehensive guide covering different types of blockchain and best practices to follow.

Digital data storage can be a tedious business, especially when it comes to recording — and safeguarding — digital transactions or sensitive medical information.
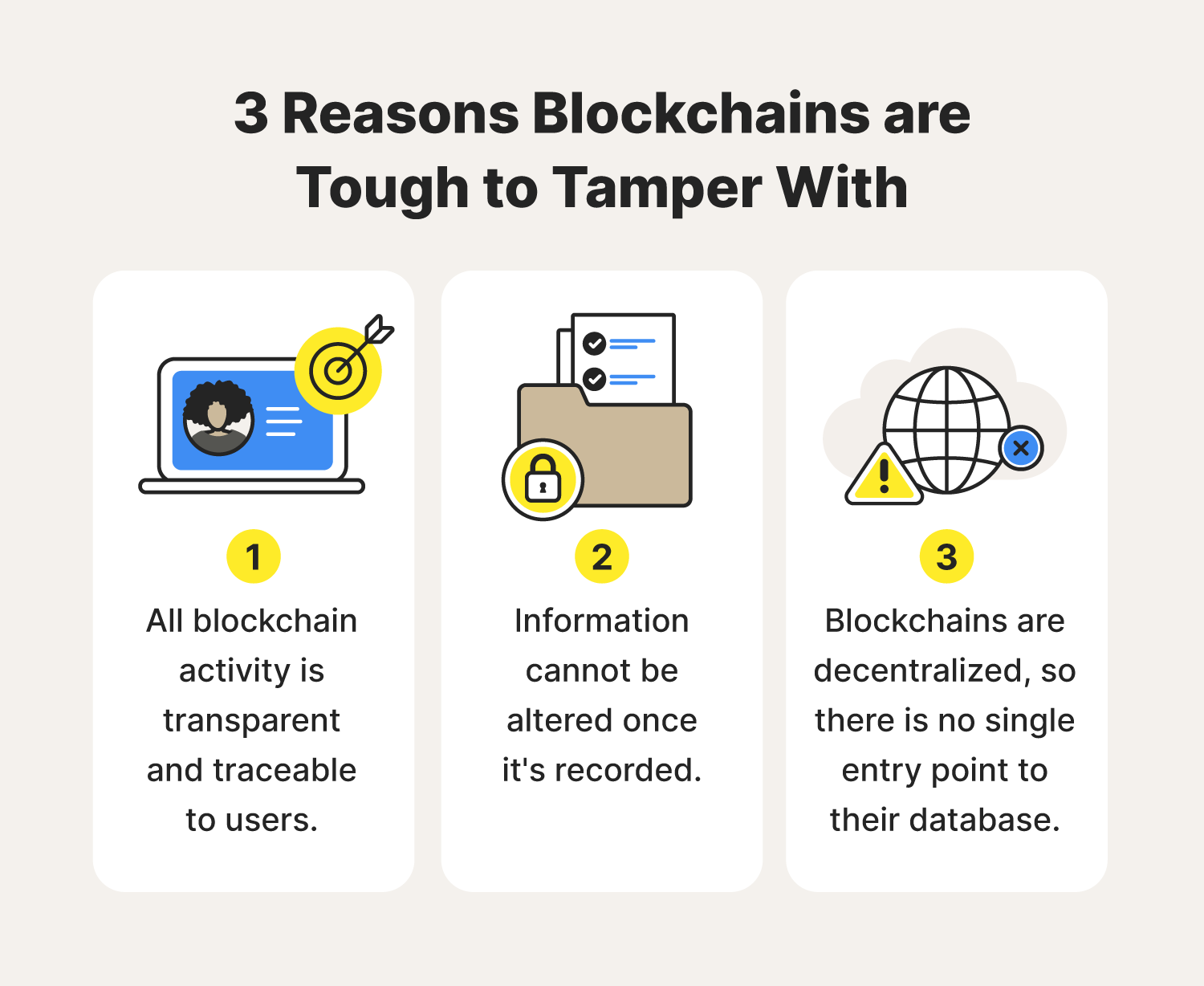
A database with an essentially impenetrable cybersecurity structure would be pretty handy, right? That’s the thought behind blockchain technology. You might compare the database to a house of playing cards where if you tamper with one card, the whole structure will tumble.
That just grazes the surface of blockchain security. Another facet of it is knowing the potential cyberthreats associated with blockchain technology and how to manage those threats. We’re overviewing just that, plus how blockchains are built to safeguard your confidential data and best practices for you to level up your blockchain security.
What is blockchain?
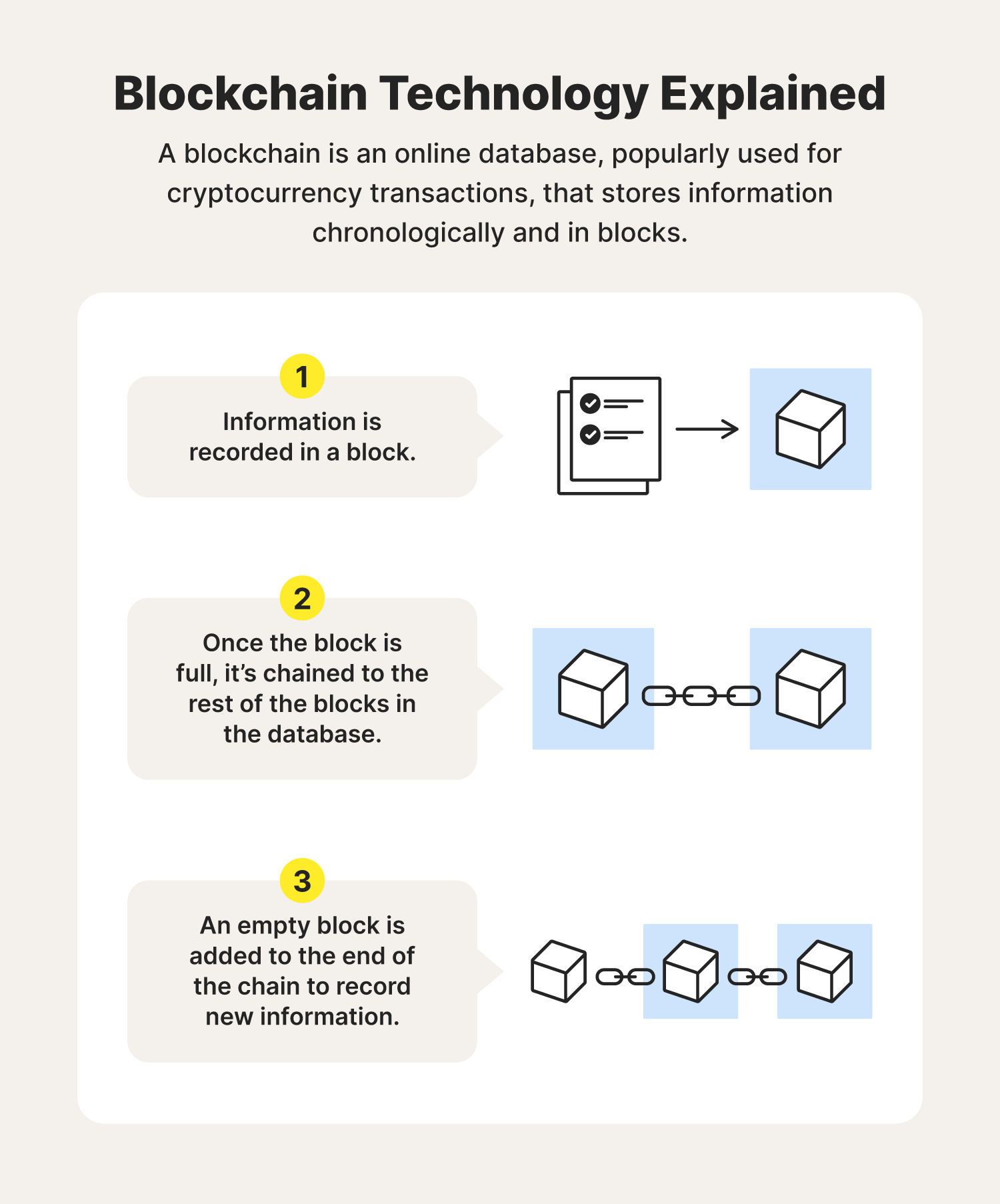
A blockchain, also known as distributed ledger technology, is an online database that’s popularly used for cryptocurrency transactions like Bitcoin. Hence the name, the database stores digital information in blocks and in chronological order. Once a block is full, it’s linked and locked to the rest of the full blocks in the database, creating a chain. An empty block is then added to the end of the chain to record new information.
In simpler terms, you might think of blockchain technology like a paper ledger book, which is used to record transactions. Once one page is full, you must flip to the next blank page to continue recording information, and so on. In the case of a blockchain, once a block is filled and locked into the chain, that block can no longer be changed. It’s a permanent recording — at least, that’s the thought.
Of course, blockchain technologies can differ, especially when it comes to who can access the data in each block. This means blockchain security approaches differ, too.
Different types of blockchains to know
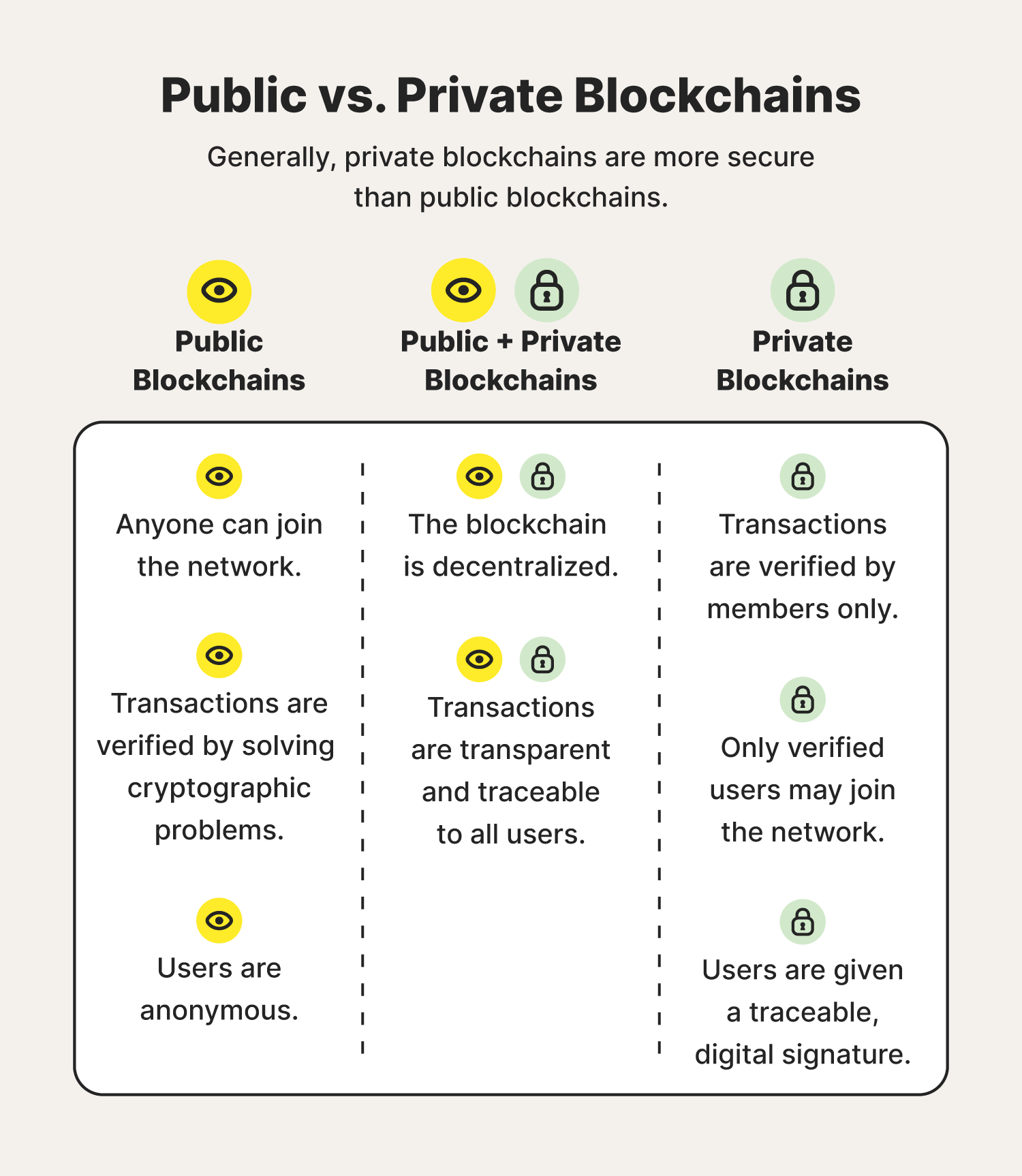
Blockchains tend to be categorized into two types: public or private. Private blockchains are generally considered more secure than public blockchains. And much of that is attributed to the ways users are permitted to verify information that’s recorded in a blockchain.
Public (and permissionless) blockchains
As the name indicates, public blockchains are public. They can be joined by anyone with an internet connection, meaning they’re permissionless, and all users are also anonymous. Each user is given a public key — think of it like an ID badge — associated with their name that can be traced back to their activity. Remember, blockchain activity is transparent to all users.
Blockchains also take a village to operate, as users must verify or validate any information that’s added to a block. In the instance of public blockchains, that’s through solving cryptographic problems.
For instance, you’ve perhaps heard the term “mining” when it comes to Bitcoin, which is among the most popular examples of blockchain technology. Bitcoin users essentially must work, or “mine,” to verify that their transaction is legitimate before it can be logged in a block. This can require a lot of data, power, and time.
Private (and permissioned) blockchains
Private blockchains, on the other hand, require less work to verify and record a piece of information in a block. That’s because only permitted users are allowed to access a private blockchain, meaning they’re permissioned blockchains.
Given users are pre-vetted, any permissioned users can verify and view personal information recorded in a private blockchain. Think of it as a members-only club. Most often used by businesses or organizations, private blockchains are considered more secure than public blockchains since they involve more access control, yet they too can be susceptible to cyber threats, especially from internal actors.
Blockchain risks to avoid
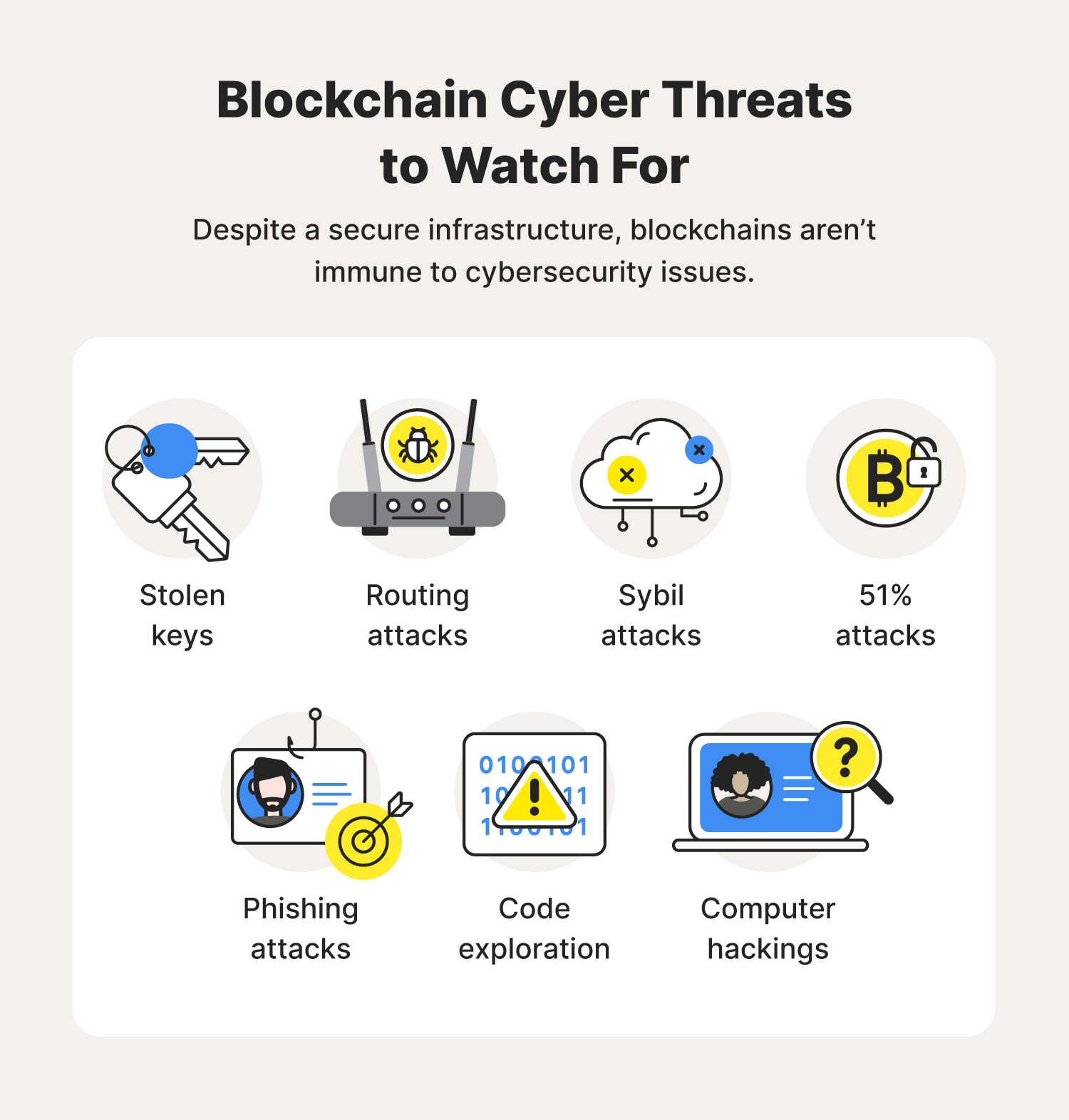
Blockchain technology is sometimes touted as being tamper-less. In reality, it’s susceptible to cyberthreats. Consider the following blockchain risks and security issues that can arise, including a few real-world examples of when blockchains were compromised.
Phishing attacks
One of the oldest hacking attempts in the book phishing is when a scammer tries to lure sensitive information or data from you by disguising themselves as a trustworthy source. They use platforms like text messages, emails, and even phone calls to do it.
These phishing messages might entice blockchain users to provide their unique ID associated with a blockchain account or encourage them to click a link that gains access to a blockchain network.
Code exploitation
Code exploitation is when a blockchain user — or cybercriminal acting as a blockchain user — identifies a weak spot in a blockchain’s software and exploits that weakness with malicious intent.
An example of this took place in 2016. A hacker swiped more than $50 million from a venture capital fund known as a decentralized autonomous organization by way of code exploitation.
Routing attacks
Routing attacks can come in a few forms, with the most common being denial of service attacks and man-in-the- middle attacks. In both instances, cybercriminals stealthily intercept data as it’s transferred across a network, usually a weak Wi-Fi network.
In the instance of blockchain of technology, cybercriminals essentially lurk on a weak network when a permissioned blockchain user is on. The permissioned user has no idea the information they’re adding to a blockchain or verifying in a blockchain is being monitored and potentially compromised.
Stolen keys
Remember how every blockchain user is granted a unique identifier — kind of like an ID badge — to enter a blockchain network? Those are also known as private keys and, yes, they can be stolen. When in the wrong hands, a cybercriminal can attempt to alter information in a blockchain under a permissioned user’s key.
An instance of this was seen in 2021 when $140 million worth of Bitcoin was stolen from crypto users. Authorities in charge of the investigation pointed to stolen keys as the source of the theft.
Sybil attacks
The “Sybil” in Sybil attack stems from a fictional book character with dissociative identity disorder. To that tune, Sybil attacks are when cybercriminals overwhelm a network with login attempts or false credentials and cause them to crash.
This can give cybercriminals free rein over a compromised blockchain network.
Computer hackings
Blockchain technology might seem advanced, but it’s no less vulnerable to good ’ole computer hacks — even in the form of a malicious individual sitting right in your computer chair and accessing a blockchain network you’ve been granted permission to.
In October 2021, $16 million was stolen from England-based cryptocurrency platform Indexed Finance, with an 18 year-old hacking prodigy as the main culprit.
51% Attacks
This blockchain security threat is mostly applicable to Bitcoin, which is built on mining, or solving cryptographic problems to validate transactions added to a block. Bitcoin users can essentially commandeer a Bitcoin network if they’re able to control more than 50% of the computing power of a blockchain.
In other words, this would require a group of Bitcoin users to be mining at the same time and with the intent of excluding new transactions being added to the blockchain. It’s a very unlikely scenario.
How to improve your blockchain security
Given that blockchain security issues indeed exist, individuals and businesses alike should build up their blockchain security infrastructure from the inside out to protect their blockchain activity.
And that’s all about understanding the cyberthreats associated with blockchain technology — and how to manage them. Adhering to cybersecurity best practices can go a long way in protecting our data stored in blockchain networks, too.
To that end, consider putting the following measures in place to level up your individual blockchain security:
- Use a VPN to encrypt your internet activity and avoid routing attacks.
- Never share your keys with anyone to avoid being hacked.
- Don’t leave your devices unattended to prevent malicious actors from accessing them.
- Know how to spot phishing attempts by being wary of suspicious or unwarranted messages.
- Don’t alter data in blockchains so your user permissions aren’t revoked.
The ways we store our data are constantly evolving. Knowing how to keep yours secure isn’t only a best practice, but imperative. Embrace the ways technology can streamline and safeguard the important parts of our lives — but also be proactive about ensuring it stays that way.
Blockchain security FAQs
Have more questions about blockchain security and blockchains in general? We have answers.
Who invented blockchain?
Satoshi Nakamoto, an anonymous online persona, created Bitcoin and what we know as blockchain.
Is blockchain secure?
Blockchain is incredibly hard to corrupt because of the anonymity and security features embedded within the technology.
How does blockchain improve security?
A blockchain is secured by an advanced level of encryption to protect each transaction and exchange that takes place on the platform.
Why is blockchain security important?
Blockchain security works to protect the crypto assets and account information stored on your profile, which is highly sought after by today’s cybercriminals.
What is the most secure blockchain?
The bitcoin blockchain is known as one of the most secure blockchains.
How many blockchains are there?
There are currently over 1,000 different types of blockchains available.

Norton technology blocked 142 million threats a day.
Norton™ 360 brings real-time protection for your PCs, Macs, smartphones or tablets against ransomware, viruses, spyware, malware and other online threats.
Try Norton 360. Post, bank and shop from your device. We’ll keep it secure.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.