How to perform a social media cleanup: A 9-step cybersecurity guide
Believe it or not, cybercriminals can learn a lot from your social media profiles. Follow this 9-step social media cleanup guide to protect your information online

From crafting a professional online presence for hiring managers to protecting your personal information from cybercriminals, a social media cleanup is something every digital citizen should consider routine.
But with so many social media platforms and settings to navigate, you might be curious about where to start with to clean up your social media profile?
That’s where our comprehensive guide comes in to walk you through essential steps of a social media cleanup to boost your cybersecurity, including:
Now, let’s get into it.

1. Find all of your social media accounts
Begin cleaning up your social media presence by collecting a list of past usernames and email addresses that could link back to you. Search your name on Google to uncover lost posts and forgotten social media accounts that are still associated with your identity.
Double-check if you have profiles on the following applications:
- YouTube
- TikTok
Profiles on popular platforms like these can store massive amounts of uploaded content. A thorough social media scrub will require you to dig deep as you sift through the digital archives and leave no profile or timeline unaccounted for. Every social media account has the potential to leak your personal information, so locating all of them is key.
2. Make your accounts private
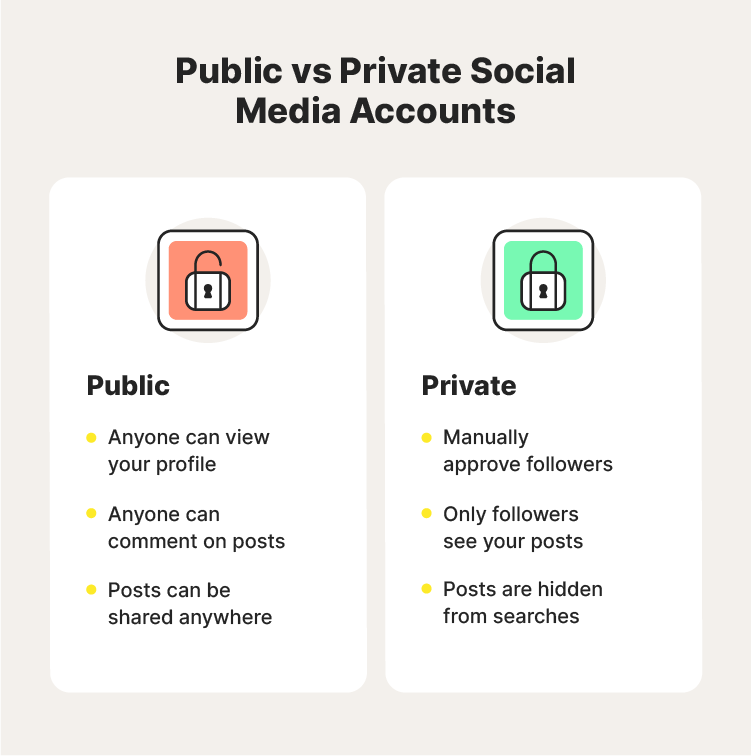
Keeping your account public allows you to interact with your followers and other users. Anyone can like, comment, and share your content with ease. This level of engagement, however, leaves your account information vulnerable.
Here are some visibility controls that private accounts help you navigate:
- Approve new followers
- Disable comments
- Block and report users
To make most accounts private, you can generally visit Settings and select “Privacy.” Here you will be able to block accounts and restrict user access. Switching your profiles from public to private is essential while you conduct your social media cleanup. It can help prevent more personal information from being shared while you scrub your accounts squeaky clean.
3. Delete any inappropriate posts or comments
Once your account is private, scan your profile for any inappropriate content. Consider how a hiring manager or family member would react to your posts. Delete anything that is unprofessional or offensive.
Posts that contain profanity, excessive alcohol, drug use, or illegal activity should be deleted immediately. Be mindful of the comments section under each post as well. Delete any inappropriate comments written by you or other users.
Take your social media cleanup to the next level by filtering through your tagged photos on Facebook and Instagram. Untag yourself from inappropriate photos and report users who tag you in offensive posts.
4. Deactivate any unused accounts
The more social media accounts you have, the harder it will be to keep all of them clean. Deactivate the accounts you no longer use. If you forgot your password for these accounts, check your browser’s settings for saved login information.
If your passwords are nowhere to be found, then click “forgot my password” to begin the account retrieval process. A “reset my password” link will be sent to the email address associated with the account.
Avoid the hassle of lost passwords altogether by installing a password manager directly into your web browser. Here you can store all of your login information and receive reminders to update old passwords.
5. Clean up your followers and friends list
No social media cleanse is complete without a close examination of your followers and friends list. Users that interact with your content reflect your interests, so pay close attention to their posts and comments.
Keep an eye out for these warning signs:
- Strange usernames
- Spam accounts
- Inappropriate bios
- Explicit profile pictures
Treat your friends list as an extension of your own profile. Stay connected with people who share similar goals and values, and unfollow any user who you would not like to be associated with. You can also block users who you do not want engaging with your content.
6. Unfollow any inappropriate accounts
Help foster a safe online environment by unsubscribing from profiles with posts that could be perceived as offensive in any way.
Take a look at the social media profiles of professionals that inspire you. Here are a few things you may see on their account:
- High-quality photos
- Family-friendly content
- Examples of their work
If you wouldn’t want your boss to see a specific post, then it should probably be deleted during your social media cleanup.
7. Use appropriate profile pictures
Your profile picture is one of the first things people will see when they search for your account, so take this opportunity to make a good first impression. Choose a profile photo that is appropriate to be viewed by all users.
Professional headshots are normally used on networking platforms like LinkedIn. A simple selfie, however, can be used as a profile photo on apps like TikTok. Consider the following when selecting a profile photo for your social media accounts:
- What’s in the background
- How you are dressed
- Your facial expression
- Other people in the photo
8. Think about your personal data
Remove any identifying information and personal data that you wouldn’t want cybercriminals or other users to have access to. This includes the following:
- Home address
- Phone number
- Email address
- Physical location
Always keep the amount of personal information you share on social media to a minimum. To accomplish this, adjust your online privacy settings so the app cannot access your current location.
If you would like to attach a physical location to a post, wait until you’ve left that location to do so. This will ensure that no one can track your location via your social media activity.
9. Routinely update your passwords
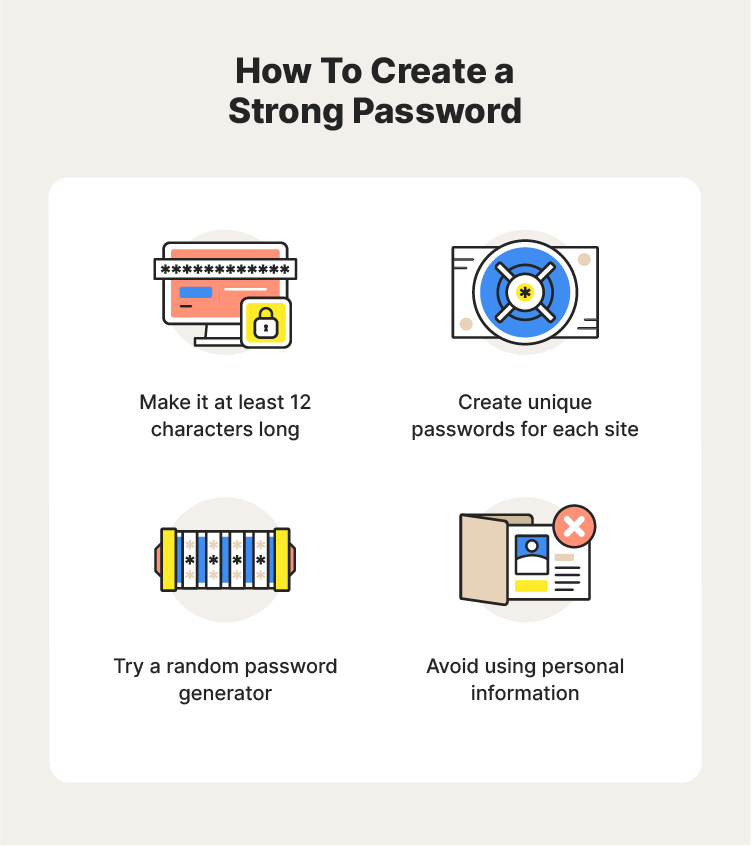
The last thing you need is for someone to hack into one of your profiles and post inappropriate content. Changing your passwords often makes it difficult for someone to break into your account
If someone were to gain access to one account’s login information, then they can access any account that shares the same username and password.
Create strong passwords that contain a combination of at least 12 unique letters, numbers, and symbols. Random password generators can also help you create strong passwords.
After you feel confident with your social media presence, keep it secure by sharing as little sensitive information as possible.
Keep inappropriate content at bay by curating your friends list carefully. Updating your passwords regularly and keeping your accounts private can also help you maintain a secure online presence.
There are a variety of tools that can help keep your information safe while posting online. Try private browsing next time you use social media to enhance the security of your accounts.
Happy scrolling!

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
- 1. Find all of your social media accounts
- 2. Make your accounts private
- 3. Delete any inappropriate posts or comments
- 4. Deactivate any unused accounts
- 5. Clean up your followers and friends list
- 6. Unfollow any inappropriate accounts
- 7. Use appropriate profile pictures
- 8. Think about your personal data
- 9. Routinely update your passwords





Want more?
Follow us for all the latest news, tips, and updates.