What is a zero-day exploit? Definition and prevention tips
Zero-day exploits have been on the rise since 2023, exposing people to hacking risks like data breaches, identity theft, and financial loss. Stay safer against hacking attacks by learning how hackers exploit zero-day vulnerabilities. And get ironclad online security from Norton to help protect against hacking, scams, malware, and other advanced threats.

What is a zero-day exploit?
A zero-day exploit (or 0-day exploit) is an attack vector through which hackers discover a previously unknown software, firmware, or hardware flaw, then use it to access personal, corporate, or government data. In other cases, hackers may exploit zero-day vulnerabilities to plant malware, corrupt files, and commit other cybercrimes.
Zero-day glossary
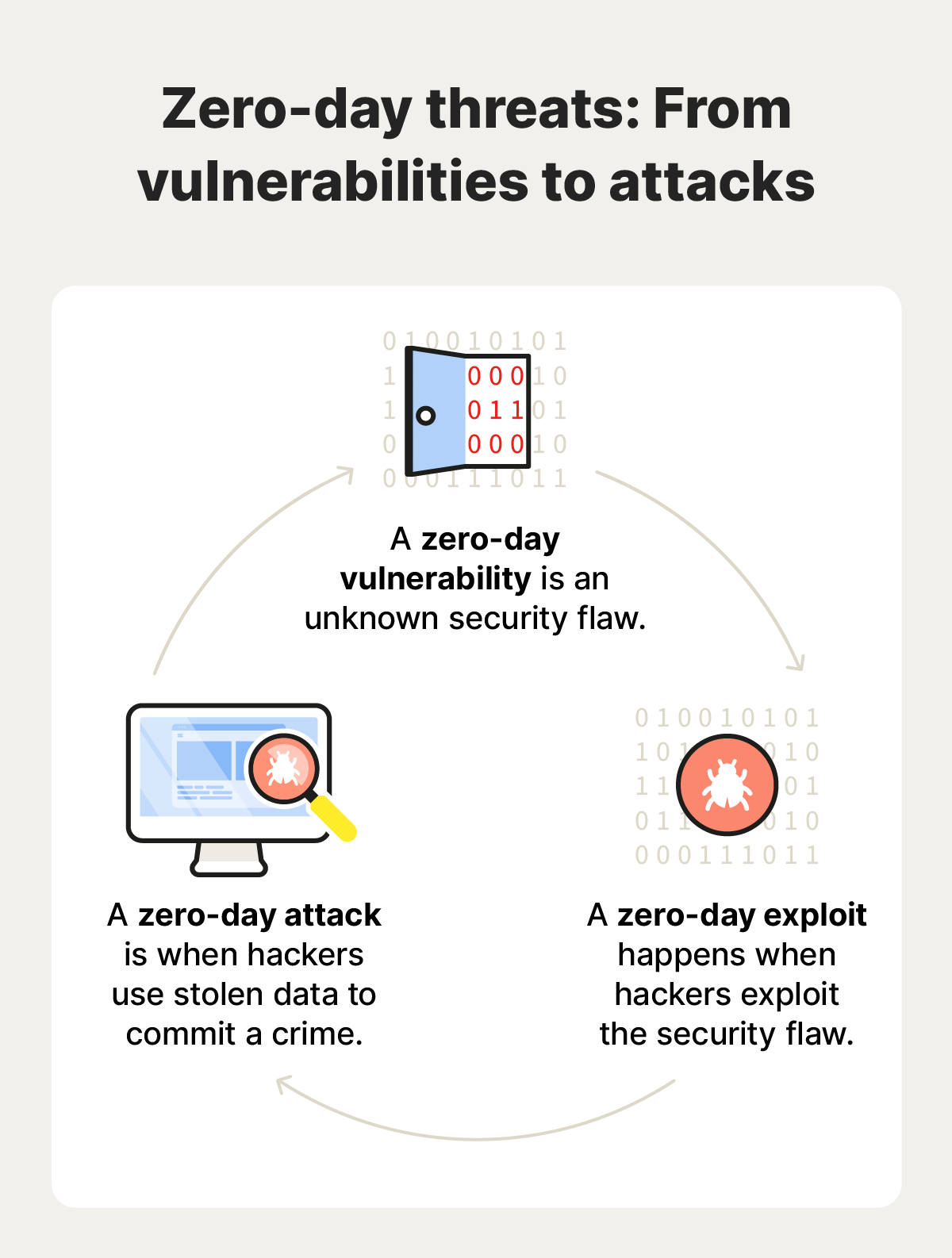
- Zero-day: developers have zero days to fix the newly discovered vulnerability.
- Zero-day vulnerability: when a hacker discovers a previously unknown security flaw.
- Zero-day exploit: the act of hackers gaining unauthorized access via the vulnerability.
- Zero-day attack: a data breach, malware attack, or other cybercrime enabled by the exploit.
The zero-day lifecycle
The lifecycle of a zero-day vulnerability, exploit, and attack begins when a hacker discovers a previously unknown software flaw. The vulnerability remains “alive” and poses a threat until a patch is released. Once a patch is available and widely applied, the vulnerability is considered “dead.”
Here's a breakdown of how a zero-day attack works:
- A developer unknowingly publishes a vulnerability: An app, device, or operating system is released with an unknown security vulnerability.
- A hacker discovers the vulnerability: The flaw is discovered by a bad actor, sometimes months or even years later.
- The hacker exploits the vulnerability: The cyberattacker develops a way to exploit the vulnerability and gain unauthorized access to a device, system, or network.
- A full attack is launched: The hacker begins the attack and proceeds to steal sensitive information or deliver malware, such as ransomware or spyware.
- More hackers attack: The zero-day hacker may sell exploit codes on the dark web for other scammers to purchase and use before developers can patch the vulnerability.
- A developer or security expert discovers the vulnerability: The zero-day hack is discovered through user reports of unusual network activity and unauthorized access attempts.
- The developer patches the vulnerability: The vendor creates a security patch and instructs users to update their systems to eliminate the vulnerability.

Who exploits zero-day vulnerabilities?
Many types of cyberattackers try to exploit vulnerabilities before they’re found and patched. Malicious hackers search for zero-days to find vulnerabilities they can use to enter and disrupt systems. Ethical hackers search for zero-day vulnerabilities to find security holes and help experts patch them to strengthen their systems and data.
The aims of malicious hackers include stealing sensitive information such as contact lists, intellectual property, or financial data. They also may want to install malware on a large scale, corrupt files, or gain remote access to users’ devices.
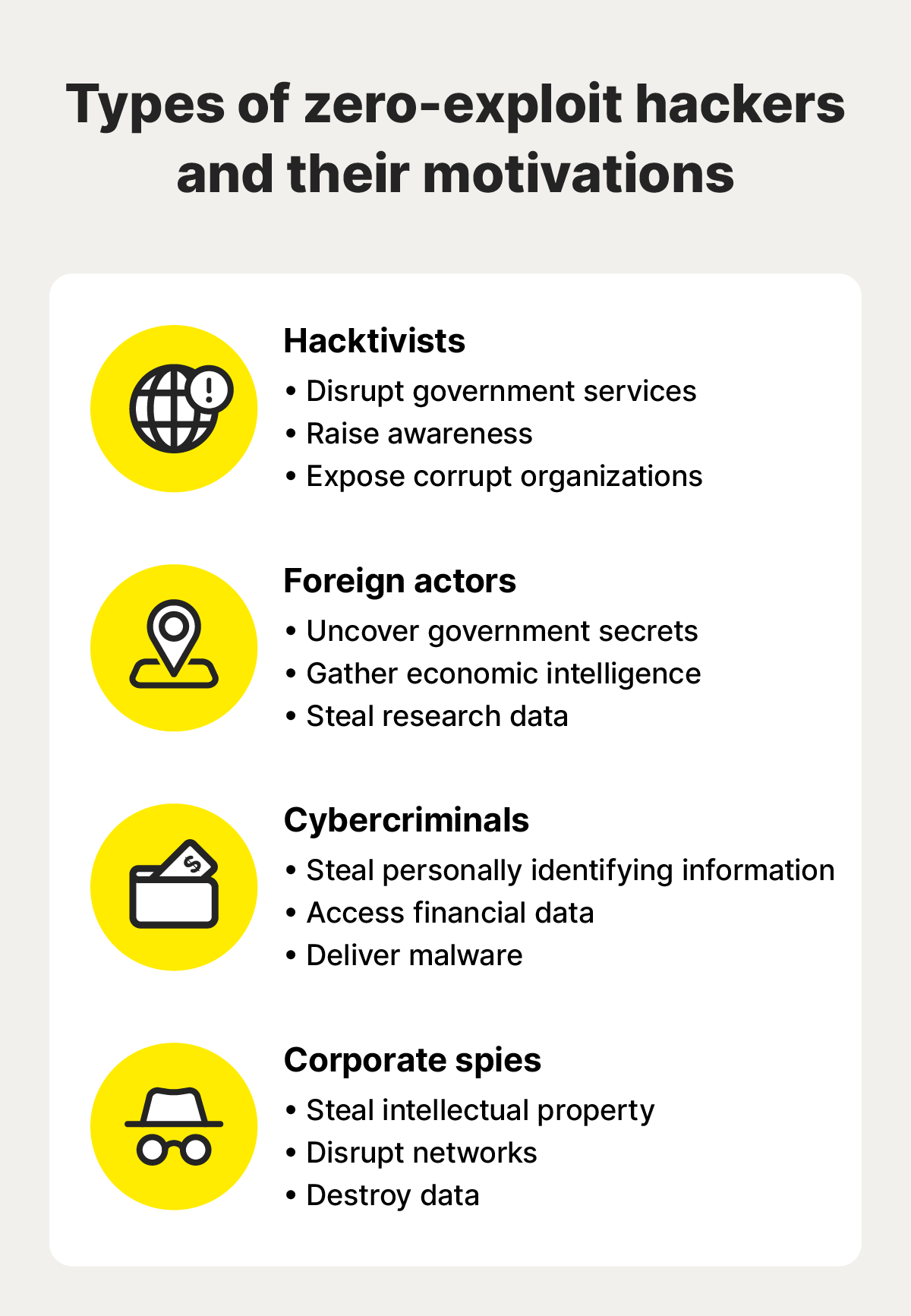
There are many types of zero-day cyberattackers, each with their own motivations—here are a few of the most common:
- Hacktivists (or hacker-activists) might use a zero-day exploit to disrupt government services, raise awareness about a political or social issue, or dig up dirt on a corrupt organization.
- Cybercriminals might use a zero-day exploit to commit digital crimes like stealing sensitive data or delivering malware.
- Foreign actors might use a zero-day exploit to establish advanced persistent threats to uncover another nation’s secrets or disrupt critical infrastructure.
- Corporate spies might use a zero-day exploit to steal trade secrets, intellectual property, or other sensitive business information from a competitor.

Common targets of zero-day exploits
Zero-day exploits may target widely used software such as web browsers, email clients, plugins, and mobile apps. Operating systems and devices are often targeted, too. Zero-day exploits can affect individual users as well as businesses, government agencies, and other large organizations.
However, the specific systems hackers choose to exploit generally depend on who or what they want to target, and why.
Here are some common zero-day attack vectors:
Individuals
- Mobile phones
- Computers
- IoT devices
- Gaming consoles
- Mobile apps
Businesses
- Mobile phones
- Computers
- IoT devices
- Gaming consoles
- Mobile apps
Government agencies
- Mobile phones
- Computers
- IoT devices
- Gaming consoles
- Mobile apps
Examples of zero-day attacks
There are plenty of examples of zero-day attacks—both old and new. One study by Google’s Threat Analysis Group (TAG) found that there were 97 zero-day exploits in 2023. And in recent months, Microsoft, LiteSpeed Cache, and Google have all had to deal with fresh vulnerabilities.
Here’s a rundown of some of the most infamous zero-day attacks:
Stuxnet
- Affected system: Microsoft Windows devices
- Culprit: The U.S. and Israel
- Motivation: To disrupt Iran's nuclear program
In 2010, a zero-day exploit was used to deploy a worm that apparently targeted high-value industrial control systems operating centrifuges used in Iran's nuclear program. The attack interrupted Iran’s weapons development and was one of the first real-world demonstrations of how digital weapons can take down critical infrastructure.
Sony
- Affected system: Sony Picture Entertainment's internal network
- Culprit: North Korea
- Motivation: To retaliate against Sony for producing the film “The Interview”
In 2014, North Korea exploited a vulnerability in Sony Pictures Entertainment's network. It’s generally believed that this was in response to Sony's production of the comedy film "The Interview," which satirized North Korean leader Kim Jong-un.
The hackers stole sensitive data, including employee emails, financial information, sensitive business plans, and unreleased movies. They also wiped data from Sony's computers and threatened to release Sony employees’ personal information.
LiteSpeed Cache
- Affected system: WordPress Websites
- Culprit: Unknown
- Motivation: To steal user data and take over websites
In 2024, the LiteSpeed Cache WordPress plugin opened up a critical zero-day vulnerability. This vulnerability, known as CVE-2024-47374, would have allowed attackers to inject malicious code into websites using the plugin. This could have led to serious consequences, such as data theft, website hijacking, and other malicious activities if it had been exploited before it was patched.
How to identify zero-day attacks
Identifying zero-day attacks can be challenging because they are—by definition—previously unencountered, and they may not display the same behavior as other known threats. However, there are some general warning signs you can look for to identify active attacks:
- Unusual network activity: Watch for unusual spikes in network traffic, unauthorized access attempts, or strange data transfers.
- Unexpected system behavior: If you notice unexpected crashes, slowdowns, or error messages, it could be a sign of an attack.
- Compromised accounts: Check for any unauthorized logins or changes to your accounts, especially administrative accounts.
- Data breaches: If you get a notification that your sensitive data has been leaked or stolen, it may be a sign of a successful zero-day attack.
How to help protect against zero-day exploits
Because zero-day exploits take advantage of unpatched software bugs, there’s no way to prevent them entirely. However, there are some steps you can take to improve your personal cybersecurity and reduce your exposure to zero-day threats and other attack types.
1. Always update systems and software
Using only the latest software versions helps make sure you’re all patched up against known exploits, because software updates often include critical fixes to vulnerabilities and other bugs. The longer you use unpatched programs or operating systems, the greater the risk of being impacted by a zero-day exploit.
2. Delete unnecessary software
Removing software you no longer use eliminates potential entry points for zero-day hackers. Unused applications—particularly those from third-party app stores—are also more likely to harbor unpatched vulnerabilities, further increasing the risk they pose. Delete unnecessary software to reduce your device’s attack surface.
3. Use a firewall, antivirus software, and a VPN
Using a firewall, antivirus software, and a VPN enhances protection against the effects of zero-day attacks by helping to filter malicious traffic, detect suspicious behavior, and secure internet data. While zero-day exploits can’t be prevented, this powerful combination limits attackers' ability to spread malware, steal sensitive information, and stay undetected—and it reduces the overall damage and exposure you may have during an attack.
Get powerful hacking protection
Norton 360 Deluxe combines an array of advanced antivirus tools with a secure VPN to provide a rock-solid defense against advanced hacking threats. With a global threat-detection network, automatic updates, and state-of-the-art heuristic detection methods, Norton helps proactively block even previously unencountered attacks. Get real-time hacking protection right now.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.