What is data security? An overview + 10 data protection strategies
What is data security? Consider this your go-to guide for all things data security, including data security risks and data protection tips to look out for.

Data security is the practice of safeguarding corporate and personal information from unauthorized users or malicious actors potentially looking to steal or destroy sensitive digital data.
This is an especially relevant topic if you or your business relies on the cloud to store valuable information. With the added convenience of being able to store some of your most important data in one place comes an increased responsibility to protect that information from potential cybersecurity threats.
Learn how to do just that by turning to this guide on data security and data protection. You’ll leave with an understanding of the importance of data security along with real-world data security risks that you should be aware of. We also go a step further by providing different types of data security best practices that businesses and individuals can incorporate to improve their Cyber Safety.
Why is data security important?

The importance of data security is clear: In addition to improved protection against data breaches, unauthorized exposure, and cyberattacks such as credential stuffing, keylogging, and session hijacking, data security also serves as your first line of defense against today’s hackers. And with over 280 million people in the U.S. affected by data breaches this year alone, there has never been a better time to start taking it a little more seriously.
Examples of data security risks
To help you grasp the true danger of not protecting your data, here are some examples of data security risks that could put your personal information in harm's way.
Ransomware
Ransomware is a type of malware that locks and encrypts sensitive files and then holds them for ransom. Usually delivered through vehicles like malicious emails and drive-by downloads, ransomware is a data security issue because hackers could potentially sell stolen information to the highest bidder on the dark web or continue to hold the bait over you until they get everything they want.
- Data security tip: Consider the use of external hard drives to safeguard data.
Data loss in the cloud
Companies and individuals alike have seen and reaped the benefits of shifting their digital property to the cloud. However, it is also important to acknowledge that this storage method could lead to data loss, as cloud-based systems are still relatively new and people are still getting accustomed to them. People may also access data through unsecure internet networks, like public WiFi, opening them up to infection by any hackers lurking on that network.
- Data security tip: Avoid public Wi-Fi networks when logging into cloud-based data storage systems.
Social engineering attacks
Cybercriminals favor social engineering attacks to gain access to private data housed on personal and corporate networks, often by creating fake websites or login platforms to trick everyday people or employees into handing over personal information and/or login credentials. This, in turn, provides hackers a direct pathway to the data and files you want to protect most.
- Data security tip: Download antivirus software to alert your computer of potential threats.
Insider threats
Posing more of a threat to today’s companies and organizations, insider threats are employees who accidentally — or intentionally — jeopardize highly sensitive files. By ignoring data security policies put in place, they can compromise not only company information, but also the private details of valuable customers.
- Data security tip: Keep employees up to date on data security policies designed to protect customer and company information.
Unintended exposure
As you can imagine, not many people at home or work browse the web with the intention of handing over information for hackers to steal. Most of the time, this occurs unintentionally by clicking a malicious link, unknowingly connecting to a compromised Wi-Fi network, or being negligent to certain data security policies.
- Data security tip: Be cognizant of data security policies and tools that you can use to protect your data.
Types of data security for individuals
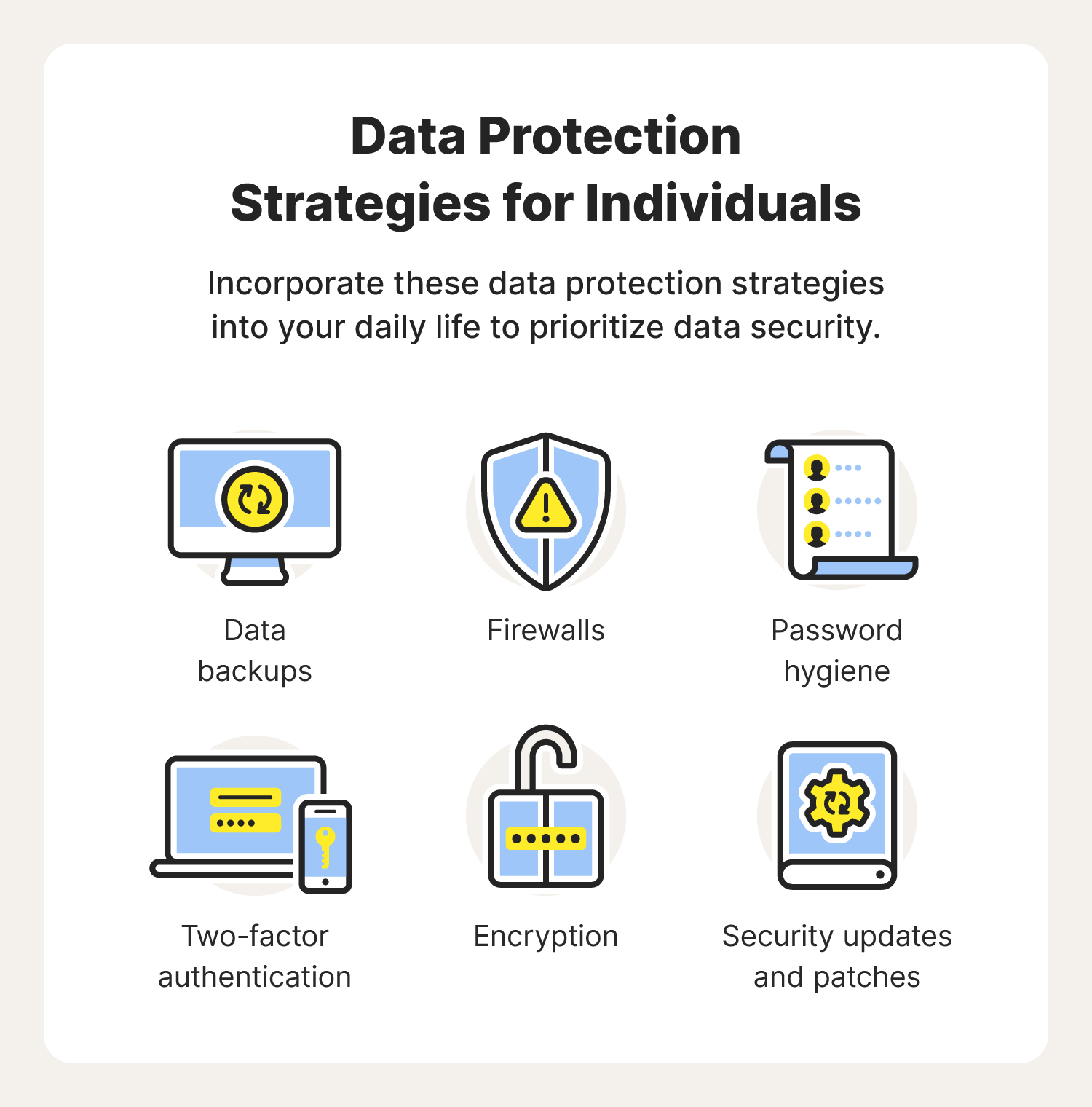
To help improve your knowledge around data protection and security, here are some different types of data security hacks you can use to secure the information you care about most.
Data backups
One of the easiest ways to avoid losing information or having it destroyed is remembering to back up your data. Whether it be on your physical device or an external hard drive, having a duplicate copy of your information can ensure that you’ll be able to recover anything lost should you fall victim to a cyberattack or unexpected system malfunction.
Firewalls
Firewalls can help mitigate data security issues by acting as the gatekeeper to your home network. They work by filtering traffic and restricting access from unauthorized parties. Only recognized IP addresses can interact with the devices connected to your Wi-Fi and will alert you if suspicious activity arises.
Password hygiene
The use of strong, differentiated passwords is key to protecting data you care about most. Passwords act as your first defense against hackers using techniques such as credential stuffing and password spraying to get their hands on your personal information.
Two-factor authentication
The use of wo-factor authentication adds an extra layer of security on accounts and devices holding data not meant for public viewing. It can incorporate biometrics to verify the identity of the user attempting to gain access. And with facial structures and fingerprints being almost impossible to replicate, hackers have tremendous trouble finding their way around it.
Encryption
Encryption allows people to mask their network activity so hackers can’t monitor their every move. With the help of encryption tools such as VPNs, people can hide their IP address, leaving no trail for cybercriminals to follow. Without this trail of breadcrumbs, hackers would have to take a shot in the dark to get anywhere near your private data.
Security updates and patches
Keeping the operating systems on your computers, tablets, and other IoT devices up to date can help them fight against infectious malware. These updates often come with security patches that fix system vulnerabilities that could put your information at risk.
Types of data security for businesses
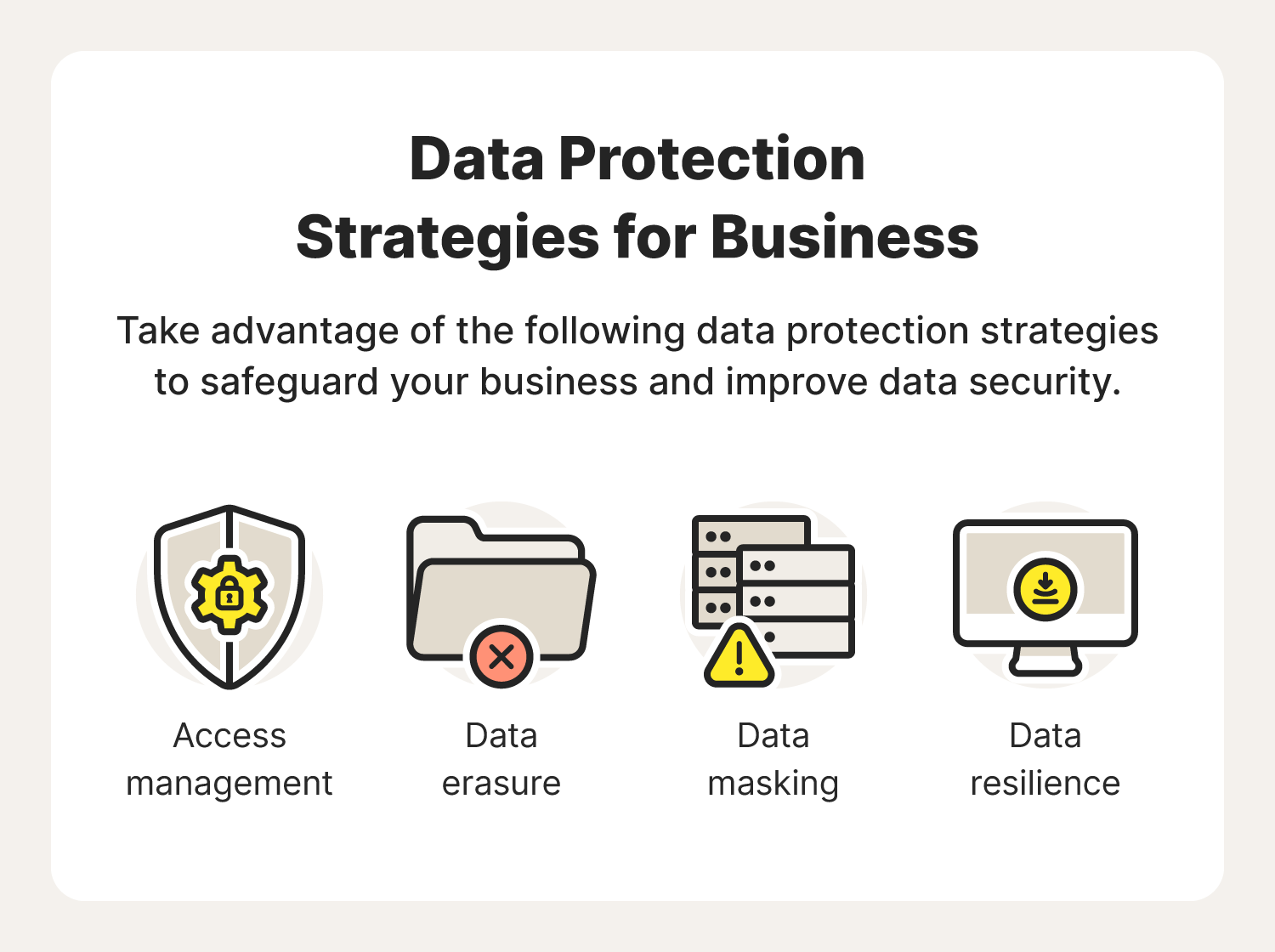
Businesses need to think strategically about protecting data. In addition to satisfying their customers’ data security standards, there are also government-enforced regulations companies need to abide by. These include rules surrounding the storage of card payment and health information along with the systems used to do so.
To help improve your understanding around the protection of valuable information, here are some ways businesses can prioritize data security.
Access management
Identity and access management involves regulating who has the ability to view certain types of data and where they’re allowed to access it. Usually outlined in a data security policy, these guidelines help ensure that confidential data remains inaccessible to unauthorized parties and mitigates the potential of malware infections.
Data erasure
With loads of customer and competitor analytics data stored on business servers, some of that information does eventually become irrelevant. Data erasure is a secure method of permanently disposing that information to keep customer information and trade secrets hidden. Unlike simple deletion, this process ensures files are completely unreadable and unrecoverable by prying eyes.
Data masking
Similar to encryption, data masking software is able to hide data by interchanging the numbers and letters used with fake characters. This hides targeted information from cybercriminals trying to gain access. Once the intended party opens or receives the data, it reverts back to its original form.
Data resilience
Data resilience refers to a company’s ability to build a data infrastructure that can withstand and recover from system failures.
Due to the importance of the information stored on servers, the data security software and hardware a business uses should be able to survive external threats like natural disasters or power outages without compromising information. Companies want to ensure that valuable information remains accessible and protected so business operations aren’t negatively impacted and customer loyalty remains unwavered.
So, what is data security? Well, it can be considered every move you make online to protect your privacy, identity, and digital property. Use this guide to take control over your Cyber Safety and better protect the information you care about.
Data security FAQs
What is data security and why is it important?
Data security is meant to safeguard corporate and personal information from unauthorized access and malicious actors. Without it, hackers would be able to steal, encrypt, or destroy your most valuable data.
Are there different types of data security?
Yes, there are many different techniques that you can use to prioritize data security, such as practicing password hygiene, using two-factor authentication, and encryption.
What are data security threats?
A data security threat refers to any malicious actor that attempts to access, steal, destroy, or damage your data.
What is the difference between data privacy and data security?
While data security protects data from external threats and malicious actors, data privacy deals with how individuals or companies collect, share, and use their information.
What are the top three data security and protection risks?
The top three data security risks include unintended exposure, social engineering attacks, and data loss in the cloud.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.