What is identity management? A guide for users
Identity management (ID management or IdM) is a set of principles and technologies that ensure the right people have appropriate access to digital resources. Learn what identity management is, how it works, and how tools like Norton™ 360 with LifeLock™ Ultimate Plus can strengthen this security framework and help catch unauthorized access attempts.

Identity management definition
Identity management—sometimes referred to as identity and access management (IAM or IdAM)—is a set of technologies, processes, and best practices that help identify and authenticate users. Individuals and organizations use identity management to share files and resources while keeping unauthorized users away from critical networks, accounts, and systems.
ID management often works in tandem with access management, which involves digital identity creation, user authentication, and verification. Identity access management is mainly handled by software, but typically also involves oversight from someone who can manually approve, restrict, deny, and define permissions based on individual credentials.
What is the difference between identity management and identity access management (IAM)?
The main difference between identity management (IdM) and identity access management (IAM) is that IdM oversees users and devices on a network, while IAM determines which users or devices can access specific resources or networks.
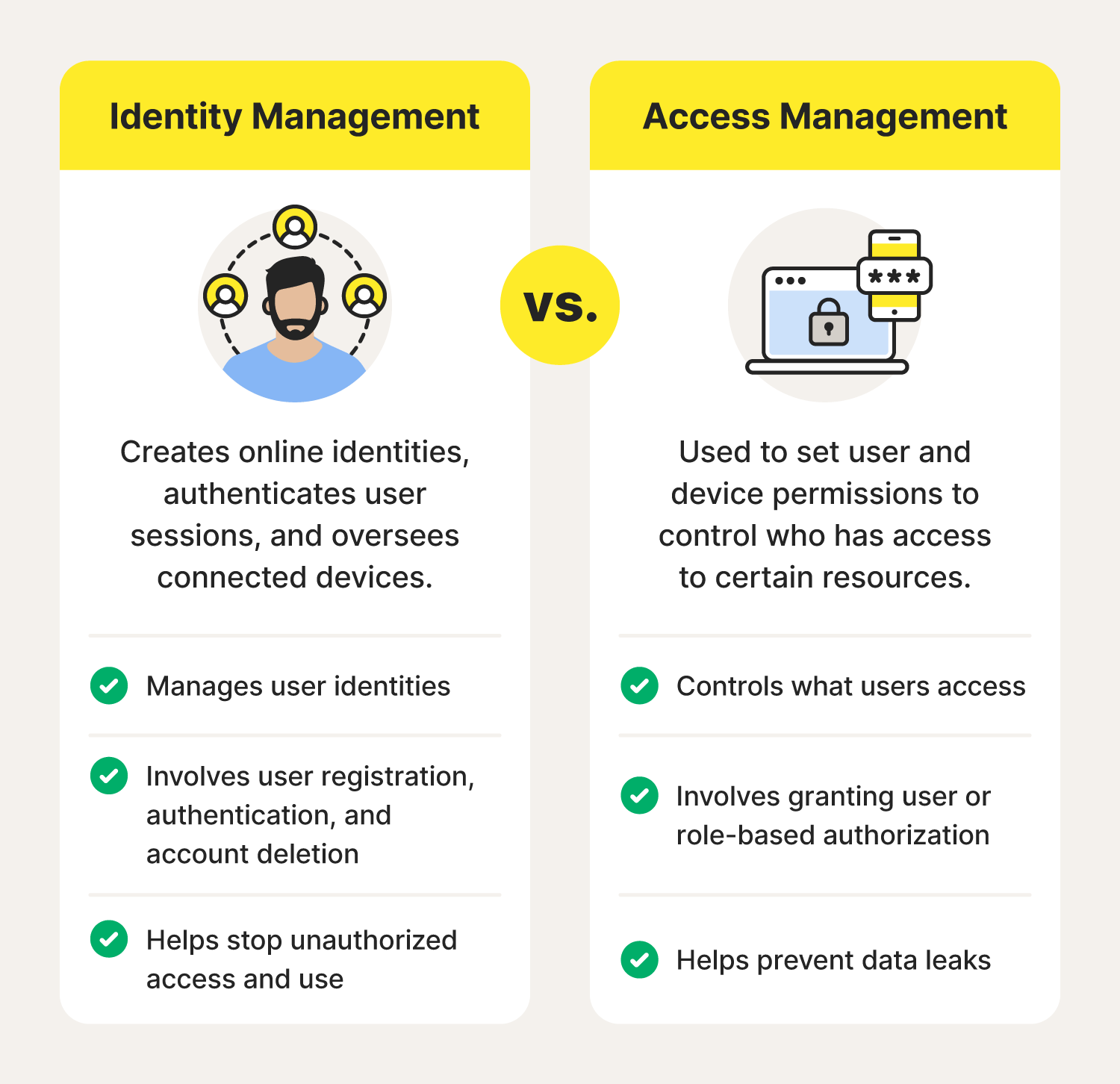
Here are the key distinctions between the two, and examples of how they can help defend against online threats in daily life:
- Identity management: IdM leverages security software and features like strong passwords, two-factor authentication (2FA), and encryption to help secure online information in healthcare portals, work files, social media accounts, and more.
- Identity access management: IAM involves controlling who can access certain accounts, networks, and platforms. This could mean setting up Face ID to log into your smartphone rather than manually inputting a PIN—something anyone can do without verifying their identity.
How does identity and access management work?
Identity and access management works when a digital identity (username or account) is created within an organizational network and then used to manage permissions, authenticate users, and monitor activity to help prevent unauthorized access and data leaks.
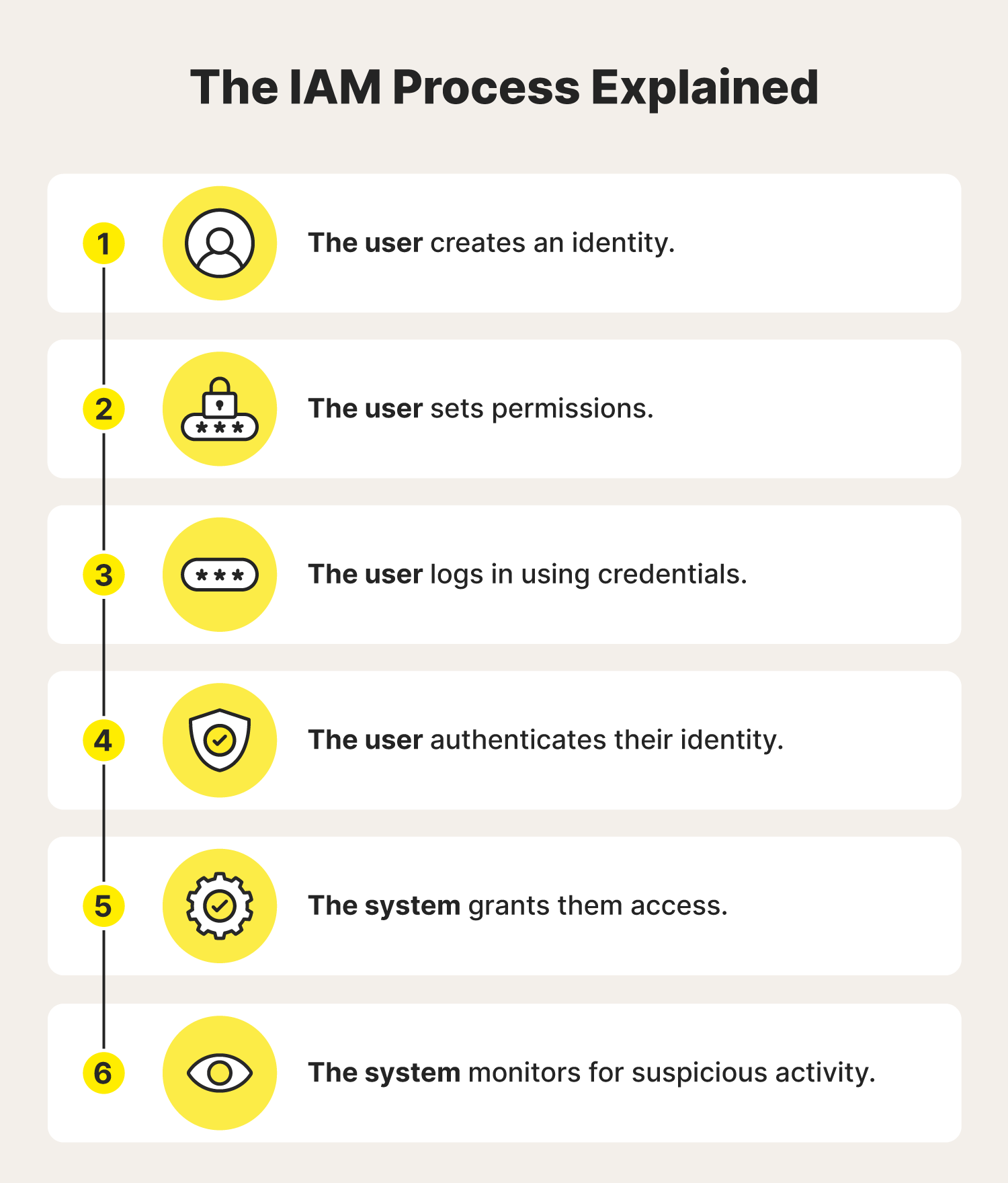
Here’s a closer look at how the IdM and IAM processes work for everyday users looking to protect their accounts and private information.
Identification and identity authentication
The identity creation and authentication process is the key to ensuring users in possession of correct credentials are actually authorized users. This can help protect you, even if somebody steals your data in a data breach. Follow along to see how the process works:
- User registration: At this stage, you create your online identity, whether it's a username, email address, or account number.
- Permissions: Once your account is ready, you choose who else can access your account, data, or resources. This is the equivalent of adding an authorized user to your credit card or sharing a Google Doc with a classmate.
- External authentication: For extra security, require users to prove their identities using their phone, biometrics like face scans and fingerprints, or some other form of multi-factor authentication.
- Continuous authentication: Finally, watch for suspicious activity and investigate any unauthorized access alerts you receive to help ensure your personal information doesn’t get leaked.
Access management and authorization
Access management involves controlling permissions to limit who can access specific resources and what they can do. This helps with damage limitation if there’s a data breach, because the digital trespasser won’t be able to access all of your personal information. Here’s more on what access management and authorization entails:
- Settings configuration: Protect your accounts by reviewing and updating your privacy settings.
- User authorization: Grant access to specific individuals when sharing files online, like documents, media, and other resources.
Benefits of identity management
Identity management offers numerous advantages, including enhanced data security, privacy, and streamlined access to online accounts. Some of the top benefits of using identity management in daily life and frequenting businesses that use strong identity management systems include:
- Protection from account takeovers and unauthorized access
- Financial loss risk reduction
- Enhanced privacy
- More secure networks to help keep your data safe and confidential
Strategies for more effective identity management
Take a proactive approach to managing your identity with these strategies designed to protect your personal information and reduce the risk of unauthorized access:
- Implement 2FA: Add an extra layer of security to your sign-ins by requiring two or more forms of verification to authorize login access.
- Use single sign-on (SSO): Make it more convenient to securely access multiple applications with a single set of login credentials.
- Set strong passwords: Create unique and secure passwords to make it harder for cybercriminals to break in with a lucky guess. And use a password manager to help keep track of them.
- Keep software up-to-date: Update software, devices, and applications regularly to ensure the latest security patches are in place to minimize your vulnerability to cyberattacks.
- Learn to identify cybersecurity threats: Educate yourself about common warning signs and cybercrime tactics like phishing to help identify potential threats via email, websites, social media, and messaging.
- Investigate suspicious activity: Take a proactive approach to identity management by checking your credit score and free credit report for unauthorized activity.
- Get a VPN: Use a VPN to encrypt your internet connection and help protect sensitive information you send and receive online.
- Invest in identity theft protection: Choose an identity management tool like Norton 360 with LifeLock Ultimate Plus that can help protect against identity theft and that offers restoration services to assist if a cybercriminal does steal your identity.
Keep your identity under lock and key
Staying on top of potential threats can be easier with dark web monitoring, data breach notifications, and other features in Norton 360 with LifeLock Ultimate Plus. Invest in a comprehensive identity theft protection service with robust security, identity management features, and fraud recovery services today.
FAQs about IdM
Still have questions about identity and access management? Here’s what you need to know.
What is identity and access management?
Identity and Access Management (IAM) is a framework of procedures and technologies that govern who can access certain resources and to what extent. Identity management leverages software to authenticate users while access management involves setting permissions. Together, these systems enable authorized users to utilize relevant resources while shielding sensitive data from unauthorized users.
How can I control identity management?
IdM is first and foremost an organizational process. However, users can help by practicing strong password hygiene, enabling multi-factor authentication, and updating the privacy settings on their online accounts.
Where can I find identity management solutions that are GDPR-compliant?
To find an identity management solution compliant with the General Data Protection Regulation (GDPR), explore offerings from reputable cybersecurity companies or cloud service providers. Given the scope of GDPR, most service providers develop their products accordingly.
What is Identity Management Day?
Identity Management Day promotes the importance of identity management and the need for individuals to safeguard their digital identities. It’s held annually on the second Tuesday of April.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.








Want more?
Follow us for all the latest news, tips, and updates.