Norton Cyber Safety Pulse Report: Scams in the digital age
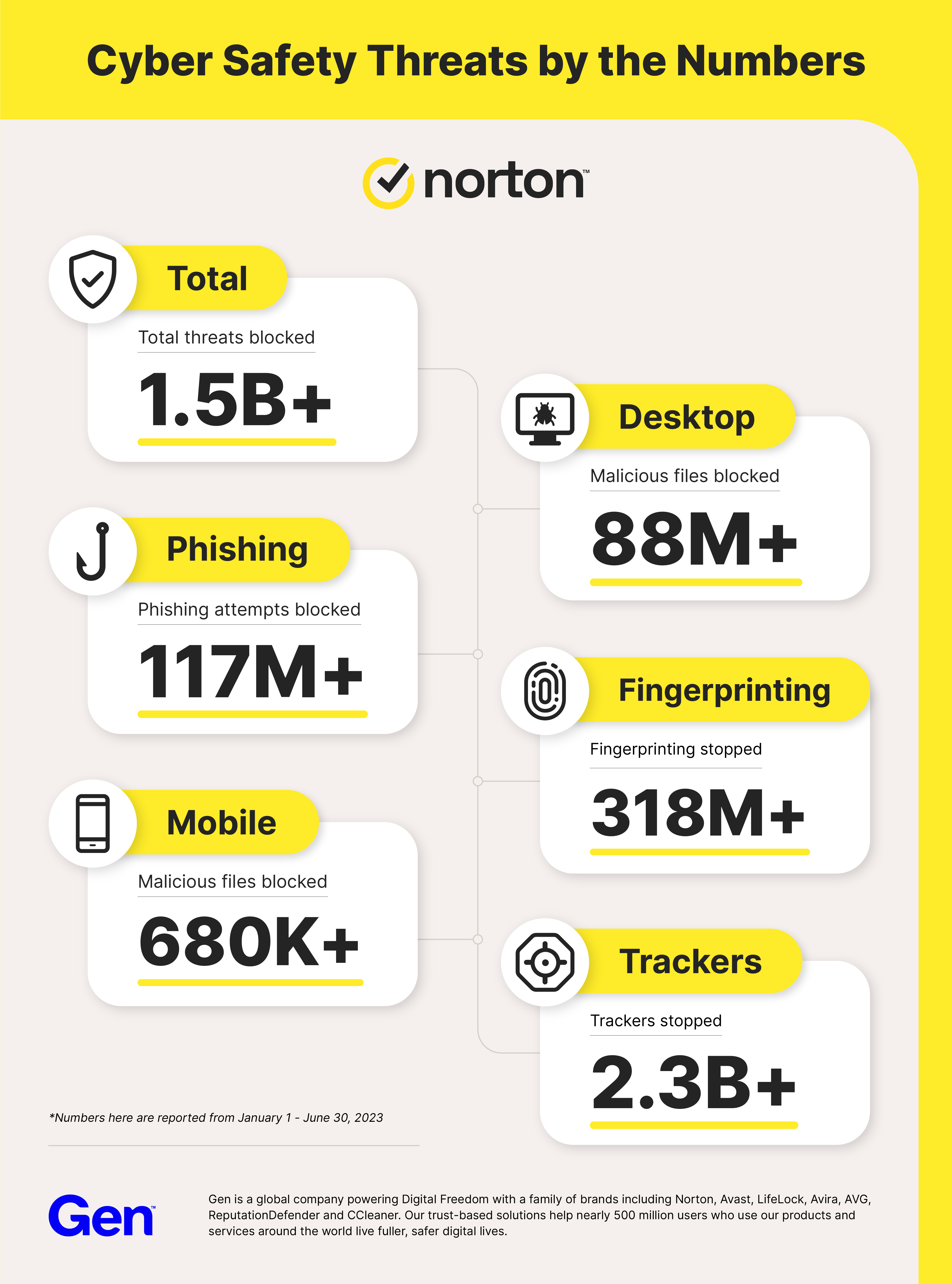
As our digital lives continue to expand, the threat landscape also evolves, presenting new challenges to people worldwide. The latest data from our telemetry shows scams are both the most significant threat, and have also reached an all-time high. In fact, our data shows scams, phishing and other forms of human manipulation make up more than 75% of all digital threats.

Our recent early access launch of Genie, Norton’s newest scam detection tool, shows much of the same findings. We’ve found scammers are leaning on old methods to lure victims, but they now have a more sophisticated arsenal at their disposal to make these schemes more realistic. Leveraging advancements in artificial intelligence (AI), criminals are creating scams that are not only more credible but alarmingly real. This abuse of technology paints a grim picture, where the lines between reality and fabrication are becoming increasingly blurred, ushering in scams that are more convincing and harder to detect.
In this issue of the Norton Cyber Safety Pulse Report, we delve deeper into these new takes on old scams that are still prevalent in today's digital landscape and advice for how to help avoid falling victim.
Online Retail Scams
E-shop scams have proliferated with the rise of online shopping. Our engines detect over a thousand new fake online shops that are emerging every day. Scammers create fake online stores, offering products at unbeatable prices. Once a purchase is made, the product is never delivered, and the website disappears. Consumers must verify the legitimacy of online stores and be cautious with unfamiliar sites.

Advice for Consumers
- Verify the website: Check the website's legitimacy by reviewing the domain. Look for an SSL certificate. Legitimate websites will also have privacy policies, but also check the branding colors of the page.
- Secure payment methods: Use secure payment methods, such as credit cards, which offer fraud protection.
Sextortion Scams
Sextortion scams are particularly insidious, involving threats to release private or compromising information unless a ransom is paid, usually in cryptocurrencies. These scams often begin with phishing emails and exploit human emotions like fear and shame. Awareness and skepticism toward unsolicited communications are key defenses.
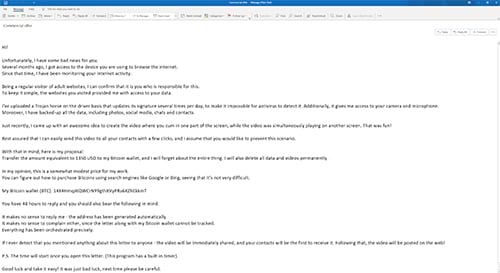
Example email:
"Hi! Unfortunately, I have some bad news for you. Several months ago, I got acccess to the device you are using to browse the internet. Since that time, I have been monitoring your internet activity. Being a regular visitor of adult websites, I can confirm that it is you who is responsible for this. To keep it simple, the websites you visited provided me with access to your data. I've uploaded a Trojan horse on the driver basis that updates its signature several times per day, to make it impossible for antivirus to detect it. Additionally, it gives me access to your camera and microphone. Just recently, I came up with an awesome idea to create the video where you [describes a sexual act] in one part of the screen, while the video was simultaneously playing on another screen. That was fun! Rest assured that I can easily send this video toa ll your contacts with a few clicks, and I assume that you would like to prevent that scenario. With that in mind, here is my proposal: Transfer the amount equivalent to 1350 USD to my Bitcoin wallet, and I will forget about the entire thing. I will also delete all data and videos permanently. In my opinion, this is a somewhat modest price for my work. You can figure out how to purchase Bitcoins using search engines like Google or Bing, seeing that it's not very difficult. My Bitcoin wallet (BTC): 14X4HmqJKQWCrNY9gthXVyPRa6KZhEkkmT. You have 48 hours to reply and you should also bear the following in mind: It makes no sense to reply to me - the address has been generated automatically. It makes no sense to complain either, since the letter along with my Bitcoin wallet cannot be tracked. Everything has been orchestrated precisely. If I ever detect that you mentioned anything about this letter to anyone - the video will be immediately shared, and your contact will be the firsto to receive it. Following that, the video will be posted on the web! P.S. the time will start once you open this letter. (This program has a built-in timer.) Good luck and take it easy! It was just bad luck, please next time be careful."
Advice for Consumers
- Don't engage: Ignore the communications and report them to the authorities.
- Protect personal information: Be cautious about sharing personal information online.
- Update passwords: Regularly change passwords to enhance security.
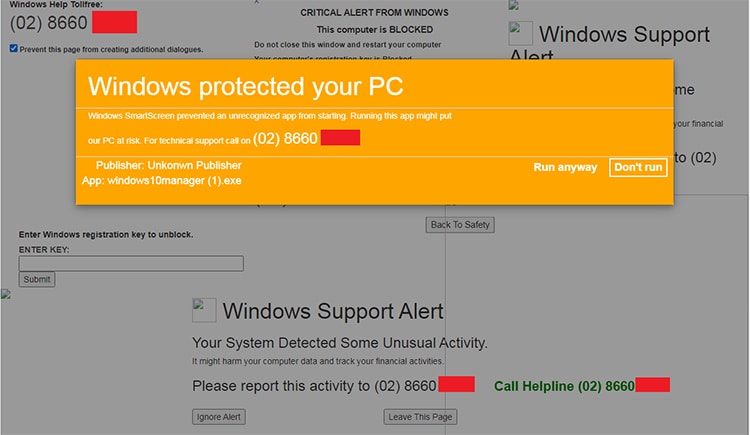
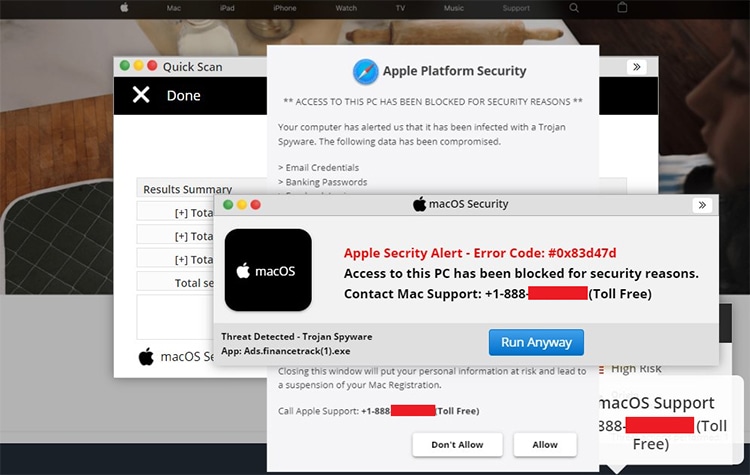
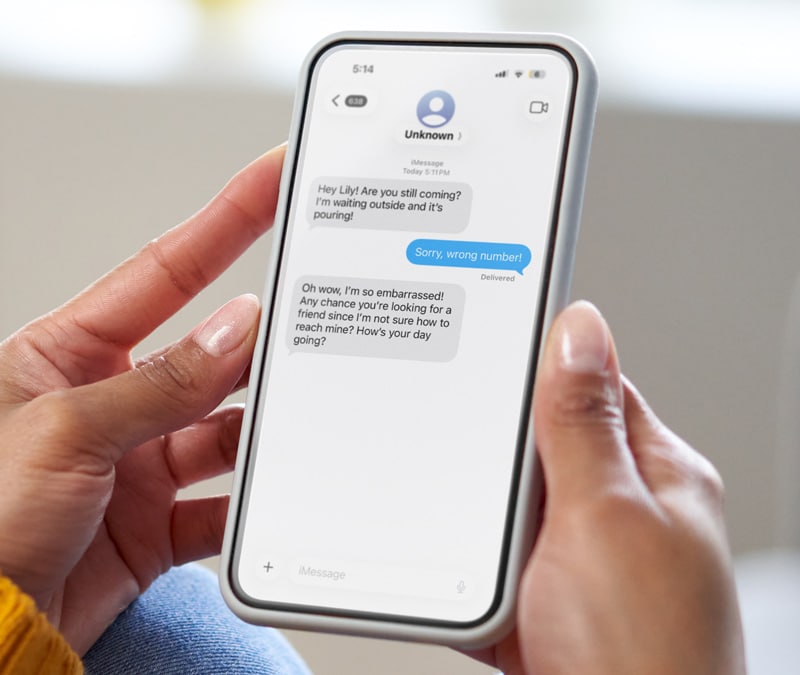
Tech Support Scams
Tech Support Scams involve fraudsters posing as tech support agents from reputable companies. They deceive victims into granting remote access to their computers, leading to data theft or ransom demands. Education about legitimate tech support procedures and vigilance against unsolicited contact can prevent these scams.
Advice for Consumers
- Verify the contact: If contacted by "tech support," verify their identity by contacting the company directly through official channels.
- Install reputable antivirus software: Utilize security software from trusted sources to protect your system.
- Never share remote access: Avoid sharing remote access to your computer with unknown individuals.
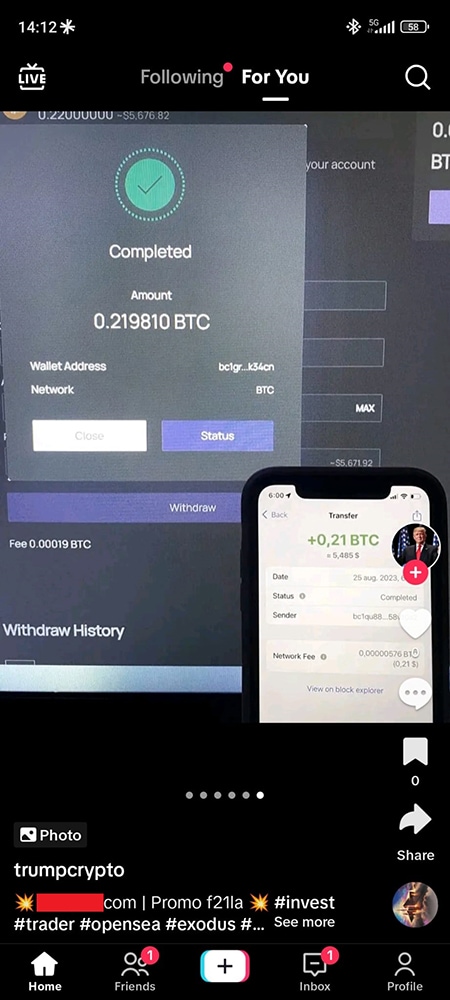
Crypto-Investment Scams
Celebrity impersonation on social media platforms like TikTok is being used to promote fraudulent investment opportunities. The allure of quick riches from cryptocurrencies has given rise to crypto-investment scams. These scams are elaborate and convincing, requiring consumers to verify information through trusted sources.
Advice for Consumers
- Research: Conduct thorough research before investing in any scheme.
- Beware of celebrity endorsements: Be skeptical of celebrity endorsements, as they can be fabricated.
- Consult a financial advisor: Seek advice from a professional financial advisor before making investments.
Business Email Compromise (BEC) Scams
Small and medium-sized businesses (SMBs) are particularly vulnerable to BEC scams. Cybercriminals impersonate company executives or vendors, manipulating employees into transferring funds or revealing sensitive information. The use of deepfake audio and video with the help of AI is boosting these attacks. Regular training, well-stablished policies and procedures and multi-step verification processes can mitigate the risks.
Advice for Consumers
- Multi-step verification: Implement multi-step verification processes for financial transactions.
- Training: Regular training sessions to educate employees on identifying potential scams.
- Report suspicious activity: Encourage reporting of suspicious communications to prevent scams.
The Double-Edged Sword of AI and LLMs
In the ever-evolving landscape of digital technology, AI and Large Language Models (LLMs) stand as both guardians and potential threats. While these technologies power solutions like Norton Genie to safeguard users, they have also opened doors to a new generation of scams, adding a layer of complexity that is unprecedented.
Crafting Convincing Narratives
Scammers are leveraging AI and LLMs to craft highly convincing narratives that mimic legitimate communications to a tee. The ease of access to AI tools means that scammers without a deep technical background can now impersonate real people convincingly, creating a pressing need for continuous monitoring and AI-driven detection tools. The education of users becomes a pillar in this defense, equipping individuals with the knowledge to discern the real from the fake.
Deepfakes and Social Media: The New Frontier in Scams
We are standing at the cusp of a new frontier in scams, witnessing the rise of deepfakes—hyper-realistic videos created to deceive. These deepfakes, often featuring celebrities, are circulated on platforms like Instagram and TikTok, convincing people to part with their money or personal information under false pretenses.



The technology powering deepfakes has evolved to a point where creating convincing fake videos is within the reach of many, not just tech-savvy individuals. This democratization of technology forebodes an increase in advanced scams, potentially leveraging fake news to manipulate markets and alter the valuation of publicly traded companies.
As we navigate this complex landscape, it becomes imperative to stay a step ahead, fostering a culture of vigilance and critical thinking to safeguard ourselves in the digital age.
Advice for Consumers
- Stay informed: Regularly update oneself on the latest scam trends.
- Use technology: Norton Genie, an AI-powered assistant, offers an additional layer of protection. Learn more about Scam Protection.
- Verify information: Always verify information through trusted sources, especially if it involves financial transactions.
Scams continue to evolve, leveraging new technologies and exploiting human psychology. The battle against scams is not just technological but also educational. Norton remains committed to empowering consumers with the knowledge, tools, and resources needed to navigate the digital world securely.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.




Want more?
Follow us for all the latest news, tips, and updates.