Docusign email scam: How to spot fake Docusign emails
Scammers impersonating Docusign may send you fake invoices, phish for your personal information, or try to install malware on your device. Learn how Docusign scam emails work, how to spot a fake email, and what to do if you open one. Then, get advanced scam and malware protection to keep your devices and data safer.

Docusign is a popular and legitimate electronic signing service that makes it easy for multiple parties to digitally sign documents on almost any device.
The problem? Some cybercriminals use Docusign’s good reputation to achieve their own malicious objectives, whether that’s to obtain sensitive information or directly steal money from victims. Docusign scams come in a variety of forms, including:
- Fake invoices: Scammers send a fake invoice through Docusign, pretending to be a reputable company like Norton or Geek Squad. They aim to trick you into thinking the invoice is real, hoping to receive a direct payment. However, they may also use the opportunity to get you to click a link to “dispute” the invoice, in the process revealing sensitive information.
- Urgent signature requests: Some Docusign scam emails claim you need to sign a document related to a legal matter or transaction to avoid penalties or delays. Attackers create a sense of urgency to make you act without thinking critically, potentially giving away sensitive information or installing malware on your device.
- Employment documents: Attackers pose as HR departments or recruiters, sending employment contracts or NDA documents via Docusign. Their goal is to trick you into revealing personal information, like your Social Security number or banking details, which they can use to commit identity theft.
- Refund notifications: Scammers send you an email posing as a trusted brand, claiming they owe you a refund. They’ll include a fake Docusign link that supposedly leads to a refund approval form. However, the link will lead you to a phishing site designed to steal your banking details.
These tactics, though often recognizable as scams upon closer inspection, can still be effective due to their ability to catch victims off guard.
Before you interact with any signature requests, learn how to tell if a Docusign email is real or a scam.
How can you tell if a Docusign email is fake?
Some telltale signs that you’re being targeted by a Docusign scam include unexpected emails containing signature requests, suspicious sender addresses, links to websites other than Docusign in emails, suspicious attachments, and generic greetings.
Remember, you may not always be able to spot a fake Docusign email based solely on what it looks like. Sophisticated attackers can make their scam emails look legitimate by adding the Docusign logo or trademark symbol and using email spoofing techniques.
Unsolicited communication
Receiving a completely unexpected request for your signature should be an immediate red flag. You will generally only receive a Docusign email after coming to an initial agreement with the sender. An email appearing out of the blue should ring alarm bells.
If the sender is someone you know or a company you’ve heard of, reach out to them through an official communication channel to confirm if they need anything from you. If you don’t know who’s sent it, ignore it and block the sender to help prevent further attempts to trick you.
Not sure if a Docusign email is real, but don’t want to miss something important? Use Norton Genie to analyze the email and any links it contains for signs of threats. Our AI-powered assistant analyzes the message for suspicious patterns and indicators of phishing or malware, to help you decide if it's legitimate and safe to interact with.
Alternatively, navigate directly to docusign.com and log in to your account — or create one if needed — to access any pending documents. That way, you avoid clicking potentially dangerous links in the email.
Bogus sender address
Some attackers run scams that involve malicious documents sent through the Docusign platform, meaning their emails will come from an authentic Docusign address. More commonly, however, cybercriminals use spoofed or personal email addresses, designed to look like a real Docusign address at a glance.
Real Docusign notifications will always come from an email address that ends in @docusign.com or @docusign.net. To trick targets, impersonators may make small changes such as:
- Misspelling the email address, like docusin.net or docsign.net.
- Adding symbols or characters, like docu-sign.net.
In some cases, criminals resort to using a free personal email account. In this case, you may receive scam emails from addresses like docusign-notification@gmail.com or docusign.signature@outlook.com.
Fake links
Scammers often include fake links to redirect you to malicious websites or trigger malware downloads on your device. If they’re successful, they may steal personal information and use it in fraud or identity theft.
You can help protect against these kinds of attacks by checking where links will send you before clicking them. To do this, hover over the link with your cursor (or long-press it on a mobile device) and review the URL that appears in the bottom left corner of your screen (or the pop-up window on a mobile device).
If it doesn’t match the real URL you’d expect to see, whether it’s misspelled, too long, or says “http” instead of “https” — don’t trust the link.


Suspicious attachments
Docusign doesn’t allow senders to add incomplete or external attachments to signature requests. The only attachments you should expect to see in an email from Docusign are PDFs of complete documents — never .zip, executable, HTML, or screensaver files.
Generic greetings
Legitimate Docusign emails usually include your name or company name. They shouldn’t open with vague openers like “Dear customer” or “Hello user.” Awkward or informal greetings should be treated as a red flag that you’re being targeted by a scam.
Poor grammar and spelling
Professional companies and contractors proofread their emails. While anyone can make an occasional typo, phrasing, or formatting mistake, frequent errors throughout a Docusign email could signal that the message was created hastily or by someone unconcerned with quality standards.
Alternatively, attackers may deliberately misspell certain words to avoid spam filters that scan for specific phrases and patterns common in malicious content.
Urgent language
Scammers often try to pressure you into acting without thinking by using phrases like “Immediate action required” or “Your account will be closed.” This level of urgency is rarely legitimate, unless you’re dealing with a genuinely time-sensitive matter, such as a legal case or important business deadline.
Pop-ups
Docusign never uses pop-up boxes in emails because they aren’t secure from threats like phishing. However, attackers impersonating the e-signature company may include them in their emails, designing pop-up forms to trick you into entering your login credentials or other sensitive information.
QR codes
Avoid scanning QR codes in unsolicited emails. While they can provide easy access to important resources, it’s impossible to preview the destination, making them ideal tools for cybercriminals. In so-called quishing attacks, the QR codes redirect you to data harvesting sites or install malware on your device.
Since Docusign also provides traditional links to relevant resources, it’s easy enough to avoid QR codes and limit your risk.
Docusign phishing email example
While poor spelling or urgent language alone might not guarantee that you’re dealing with a scam, noticing multiple indicators of a fake Docusign email should put you on alert. Here's an example of a Docusign phishing email, which shows what some common red flags might look like in practice.
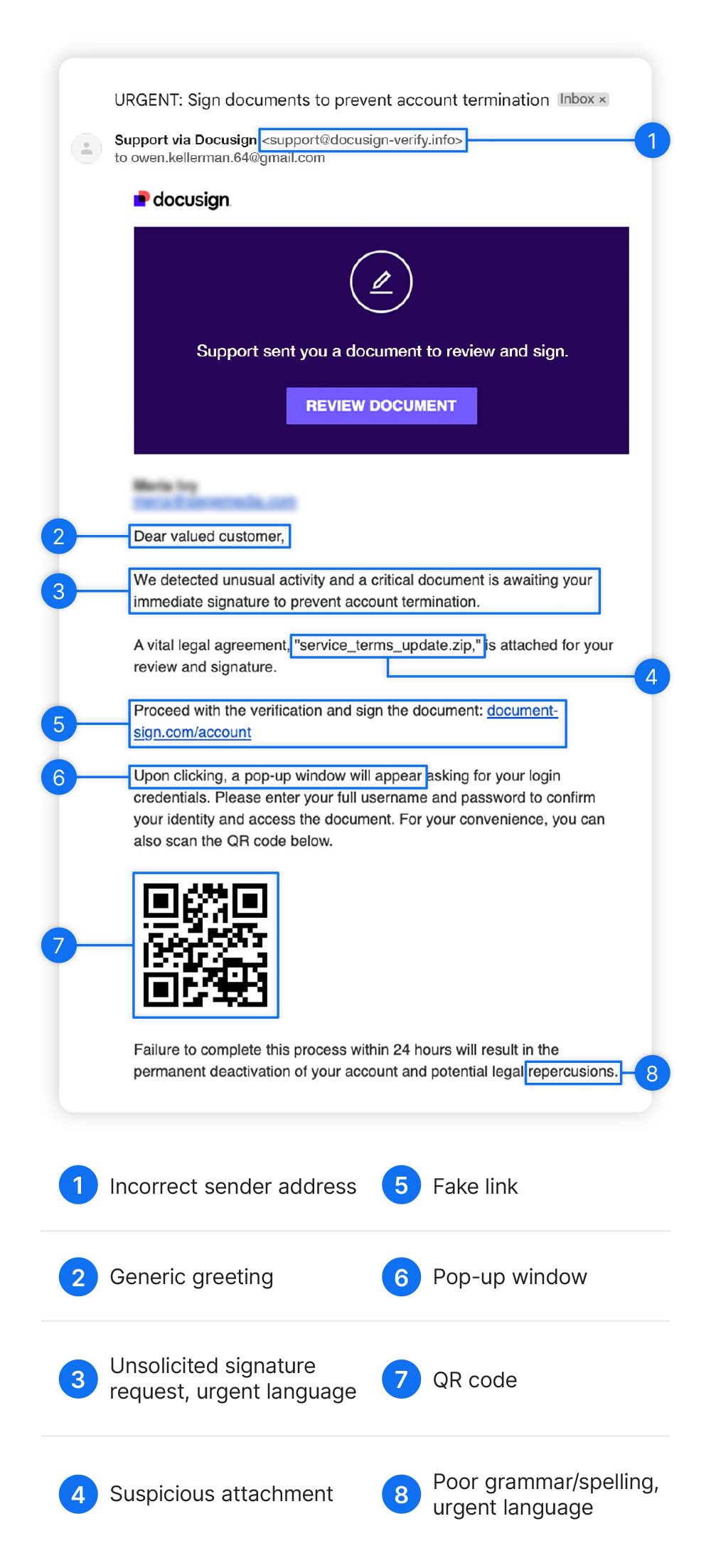

What does a legit Docusign email look like?
A real Docusign email will come from an official Docusign email address, generally be personalized with your name, and won’t urge you to take action immediately.
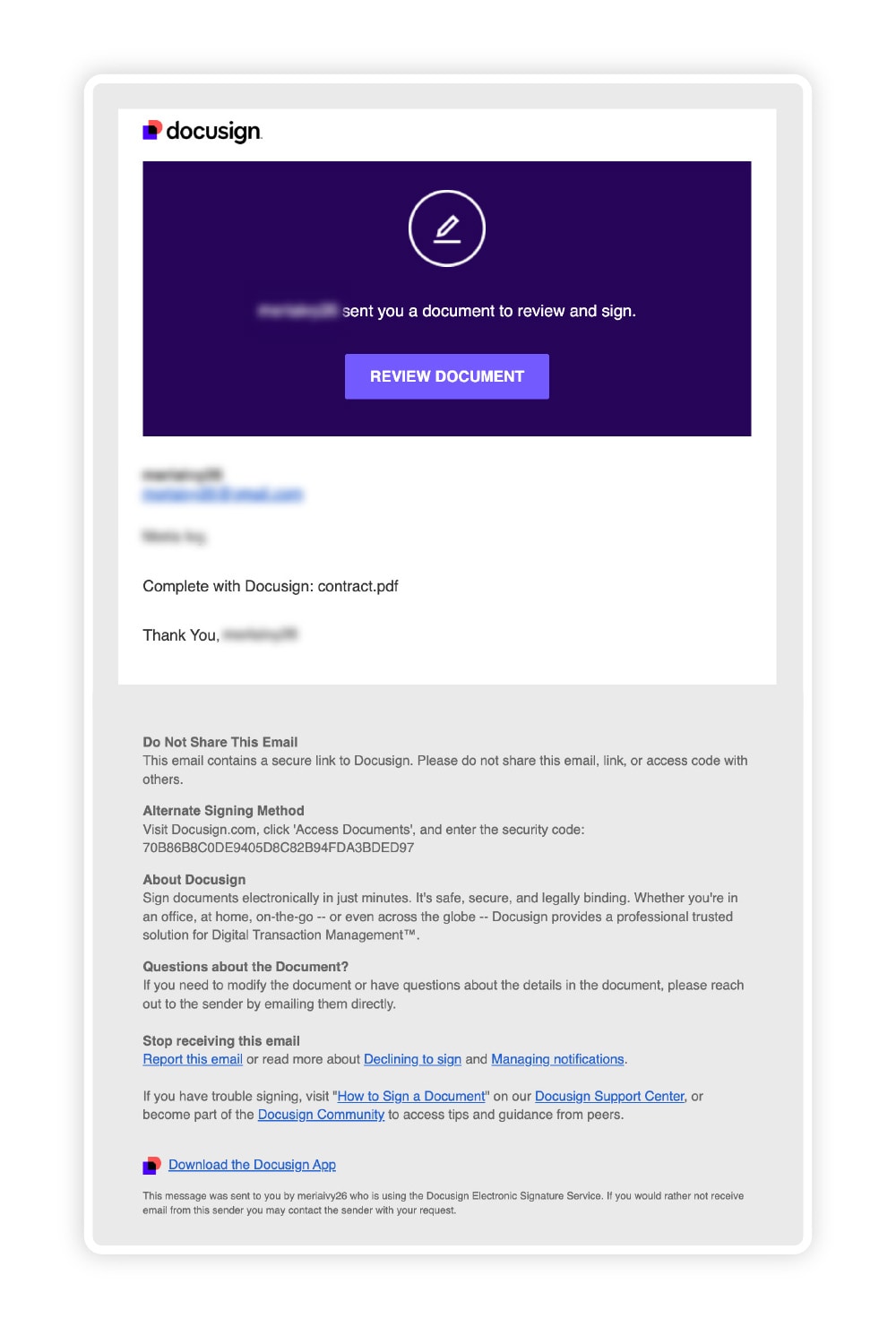

Before deciding if you can trust that email sitting in your inbox, double check that it meets these criteria.
A real Docusign email will:
- Come from the official @docusign.net or @docusign.com domain.
- Provide a secure link to the document you need to sign.
- Contain links that lead to docusign.com or account.docusign.com.
- Have a security code under the “Alternate Signing Method” section that allows you to access documents directly on the Docusign website.
It won’t:
- Contain external attachments.
- Have embedded pop-ups.
How to report a fake Docusign email
Report any suspicious Docusign emails you receive — even if you’re not 100% certain that they’re a scam. If they’re a real threat, filing a report will ensure they’re investigated and could help protect others from being targeted in the future.
- Report Docusign scams to Docusign: Forward spoofed emails to spam@docusign.com, with a note if needed. If you receive a suspicious signature request on the Docusign website, you can click the three vertical dots in the right corner and choose the “Report Abuse” feature in the dropdown.

- Report Docusign scams to your email service provider: Use the “Report phishing” or “Report spam” option to flag suspicious emails to your provider and help prevent the sender from contacting you again.
If you fell for a Docusign scam email that put you at risk of fraud or identity theft, you should also file a report with the Federal Trade Commission. Visit reportfraud.ftc.gov and follow the on-screen prompts to file a complaint about phishing attempts or identity theft.
What to do if you click on a Docusign phishing email
If you clicked a phishing link in a fake Docusign email, act fast but don’t panic. Key steps to take to help protect against the potential consequences include running a full antivirus scan, updating your passwords, enabling two-factor authentication (2FA) on potentially vulnerable accounts, and monitoring for any signs of fraud.
Here’s a closer look at the most important actions to take if you fall for an email scam:
- Run a full antivirus scan: Immediately scan your device to detect and remove any malware that might have downloaded when you clicked a malicious link.
- Change your passwords: Generate new and strong passwords for your banking, email, and Docusign accounts. Also, update any other accounts where you reuse the same password, and keep them all unique going forward.
- Enable 2FA: Secure sensitive accounts with two-factor authentication to make it harder for attackers to gain access, even if they get hold of your password.
- Monitor your accounts: Keep an eye on your social media, credit, and bank accounts to help catch any unauthorized activity early so you can take further protective steps, like freezing your credit.
If you clicked a malicious link on a work device, notify your IT department immediately. They can help resolve malware infections and secure company resources.
Known Docusign phishing attacks
Scammers are getting more sophisticated. Some even leverage Docusign’s legitimate tools, like its application programming interface (API), to make their attacks seem more authentic. Below are real-world examples of high-profile phishing campaigns that misused Docusign to target individuals and businesses.
Scammers abusing Docusign APIs to impersonate government agencies
Some attackers invest in paid Docusign accounts to access professional templates and create realistic-looking documents. They may also use Docusign’s API (which allows different programs to communicate) to send documents through the official servers and bypass email security filters.
These attacks may involve scammers posing as a government agency, like the HHS (U.S. Department of Health and Human Services) or DOT (Department of Transportation), to collect payments for made-up expenses, like driver’s license renewals or back taxes.
PayPal scammers use Docusign APIs to send phishing emails
Attackers have also impersonated PayPal using Docusign’s API and document templates to trick victims with realistic invoices or refund notices. These messages often use PayPal logos and prompt users to “cancel” an unauthorized transaction by entering their account details on a fake site.
Defend against email scams
Docusign email scams are just one type of threat you need to be on the lookout for. To help protect against email scams of all varieties, get Norton 360 Deluxe with a built-in AI assistant. Just copy and paste the email or upload a screenshot in the tool and we’ll analyze it for potential threats.
Norton 360 Deluxe will also help you block hackers, detect malware risks, and keep your device running smoother, for better protection against diverse cyberthreats.
FAQs
Is docusign.net legit?
Yes, docusign.net is a legitimate domain used by Docusign, and the primary domain used for authentic signature request emails. However, to be safe, you should still verify the full link and sender context before clicking any links on emails from this address.
How can I stop getting Docusign scam emails?
You can sometimes stop Docusign scam emails from getting through by using a strong spam filter. However, the best strategy is to keep your email address as private as possible by reducing your digital footprint and only sharing it with people you trust.
Does Docusign send emails?
Yes, Docusign sends legitimate emails for signature requests and account notifications. These should come from an address containing @docusign.net or @docusign.com, like dse_na4@docusign.net.
However, remember that an email from these addresses isn’t guaranteed to be safe, since hackers sometimes send documents containing phishing links through Docusign’s official servers.
How does legitimate Docusign electronic signing work?
In a real Docusign signature request email, you’ll be provided with a secure link to view the document that needs to be signed. Once you click, the document will open in a new window or tab, not a pop-up. There, you can read it, select or draw a signature, and sign.
Docusign is a registered trademark of Docusign, Inc.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.









Want more?
Follow us for all the latest news, tips, and updates.