Clicked on a phishing link? Here’s what to do
If you clicked a link you shouldn’t have, your data or device might be at risk or already compromised. Learn what to do to help keep your data safe and protect against further harm. Then, get comprehensive security software to defend against malware and other potential threats following a phishing attack.

A phishing link is a misleading web address scammers send to targets in the hope that they’ll click it. Instead of leading to legitimate websites, phishing links may trigger a malware download or direct you to a malicious fake website designed to steal your personal information.
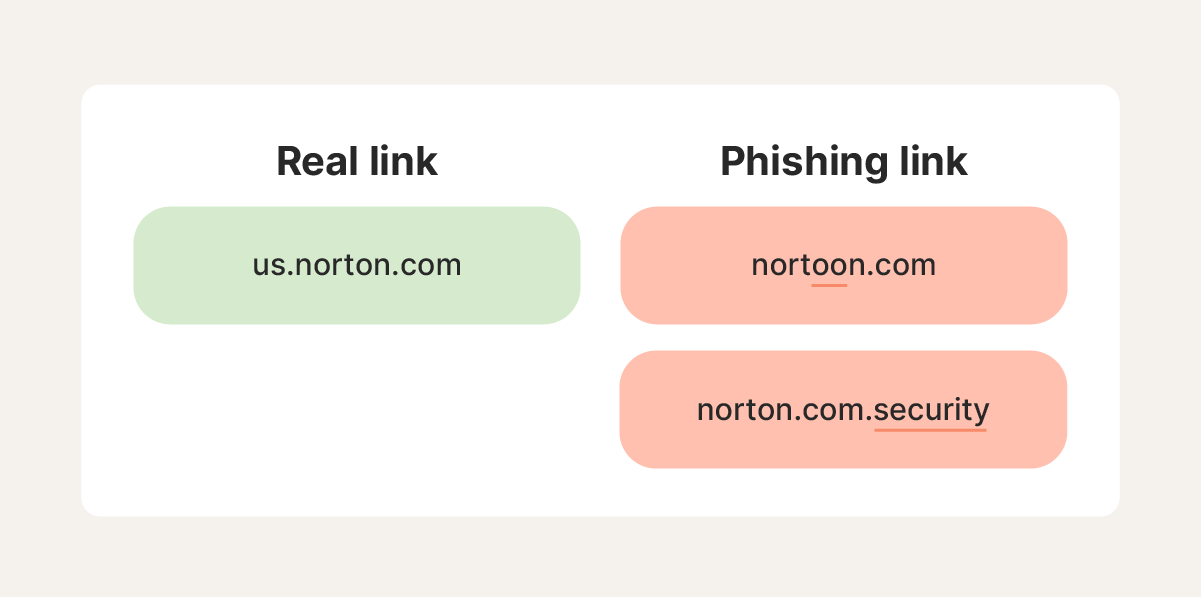
Fake links are designed to look like their real counterparts, but can often be identified by extra letters, misleading URL structures, shortened URLs, non-Latin script, numbers, or symbols.

While clicking a phishing link doesn't guarantee immediate danger, you should still understand potential risks and how to limit them. Follow along for more information about likely consequences and actionable steps you can take to safeguard your data, finances, and online accounts.
What happens if you click on a phishing link?
Clicking on a phishing link could trigger a drive-by download, infecting your device with malware like a keylogger or Remote Access Trojan (RAT). Alternatively, the link could send you to a spoofed website containing a fraudulent form designed to trick you into revealing sensitive information.
Either of these attack vectors can give cybercriminals access to the data they need to attempt to steal your identity, drain your bank or credit card balance, or lock you out of online accounts. They may also try to make money off your data by selling it on the dark web or holding it for ransom.
A device that’s compromised with malware following a phishing attack can also expose other devices on the same network to infection, giving the cybercriminals access to even more data they can use in fraud or identity theft.
Here’s a more detailed look at some of the key ways attackers might try to steal your information after you click on a phishing link.
Spoofed websites
A spoofed website is a fraudulent imitation of a legitimate website that attackers use to trick users into sharing sensitive information. Clicking a phishing link may send you to one of these sites, where you’ll be prompted to enter sensitive data like your password, Social Security number, or credit card details. If you provide this information, cybercriminals may use it to steal your identity, hijack your accounts, or commit financial fraud.
Data exfiltration
Data exfiltration is the unauthorized transfer of sensitive information from a compromised device or network to a remote server or cloud storage account. If a phishing link infects your device with malware, an attacker may be able to steal personal, professional, or financial files that expose you to identity theft, financial fraud, reputational damage, and potential legal repercussions.
Keystroke logging
A keylogger, or keystroke logging software, records what you type in real time and sends the data to a cybercriminal. Clicking a phishing link may download and install a keylogger onto your device. Once in place, it’ll run quietly in the background capturing information like passwords and credit card numbers as you type. The attacker can then use this stolen data to commit fraud.
Remote control
Clicking a phishing link could infect your device with a Remote Access Trojan (RAT), a type of malware that grants attackers the ability to control your computer remotely. With a RAT in place, a cybercriminal can potentially track your activity, access or delete files, turn on your webcam or microphone, take screenshots, or lock down your entire system.
Session hijacking
Whenever you're logged into a website or application, you have an active session. Attackers who trick you into clicking a phishing link that steals your session cookies or tokens may be able to hijack this session to take over your account without your password. Sites use cookies and tokens to identify you, so a cybercriminal with access to them may be able to bypass the login process.
Network breaches
A network breach involves an attacker gaining fraudulent access to a private home or business network. Clicking a phishing link that installs malware on your device could leave you at risk of a network breach, as the infection can spread to other devices on the network, including a router. This can give cybercriminals access to even more sensitive data.
What to do after clicking on a phishing link
If you’ve clicked a phishing link, avoid sharing sensitive information, stop any in-progress downloads, disconnect from the internet, take steps to protect your files, scan for threats, work on securing any potentially compromised accounts, and consider filing a report with the Federal Trade Commission (FTC) and the Internet Crime Complaint Center (IC3).
Here’s a more detailed step-by-step guide to protecting your data, devices, and identity if you’ve clicked a phishing link:
- Don’t enter any personal information: If you’re directed to a spoofed website after clicking a phishing link, don’t enter any sensitive information like passwords, credit card numbers, or your Social Security number. This could lead to identity theft, financial fraud, or unauthorized access to your accounts. Instead, leave the page and close your browser window right away.
- Stop any automatic downloads: Stopping active downloads can help keep malware off your device. Check that no files are being downloaded via your browser and look at the most recent files in your downloads folder to make sure you’ve not accidentally infected your device with malware.
- Disconnect from the internet: Disconnecting from the internet after clicking a phishing link can prevent any installed malware from transmitting data back to the attacker. This can stop them from accessing information they could use to commit fraud or steal your identity.
- Back up your device: Backing up your device after clicking a phishing link can help preserve your data in case malware corrupts or deletes files during another attack. Just make sure to only back up essential files to avoid accidentally copying any malicious programs, so you can restore your system to a clean state if needed.
- Scan for malware: If you manually scan for malware and remove it, you should still run a malware scan to confirm your device is clean. Norton 360 Deluxe can help detect and remove hidden malware, as well as provide real-time protection against future threats.
- Protect against fraud: To help prevent attackers with access to sensitive data like your Social Security number or credit card details from assuming your identity or taking out credit in your name, place a fraud alert or credit freeze on your credit reports with all three major credit bureaus. If your financial information was compromised in the attack, also notify your bank or credit card company.
- Update your passwords: Updating your passwords after clicking a phishing link can help protect your at-risk accounts from being hijacked by cybercriminals, keeping your data and finances safer. Focus on updating your passwords for accounts that you may have accidentally shared data about, but also consider creating new passwords for other important accounts.
- Report the phishing attempt: Finally, once you’ve taken steps to protect your data and devices, report the incident to the FTC and the IC3. Both organizations can provide resources that help you recover from harm after clicking a phishing link.
How to recognize phishing links
There are several ways to recognize a phishing link before clicking it, including checking for misspellings or errors in the URL compared to the real website. If the URL has been shortened or spoofed, make sure to preview the actual destination it’ll send you to. If it doesn’t match where you expect to be sent, don’t click the link.
You can also use the context of the link to get clues as to whether it might be a phishing attack, assessing whether you’d expect to receive a link from the sender, and checking whether their message sounds legitimate.
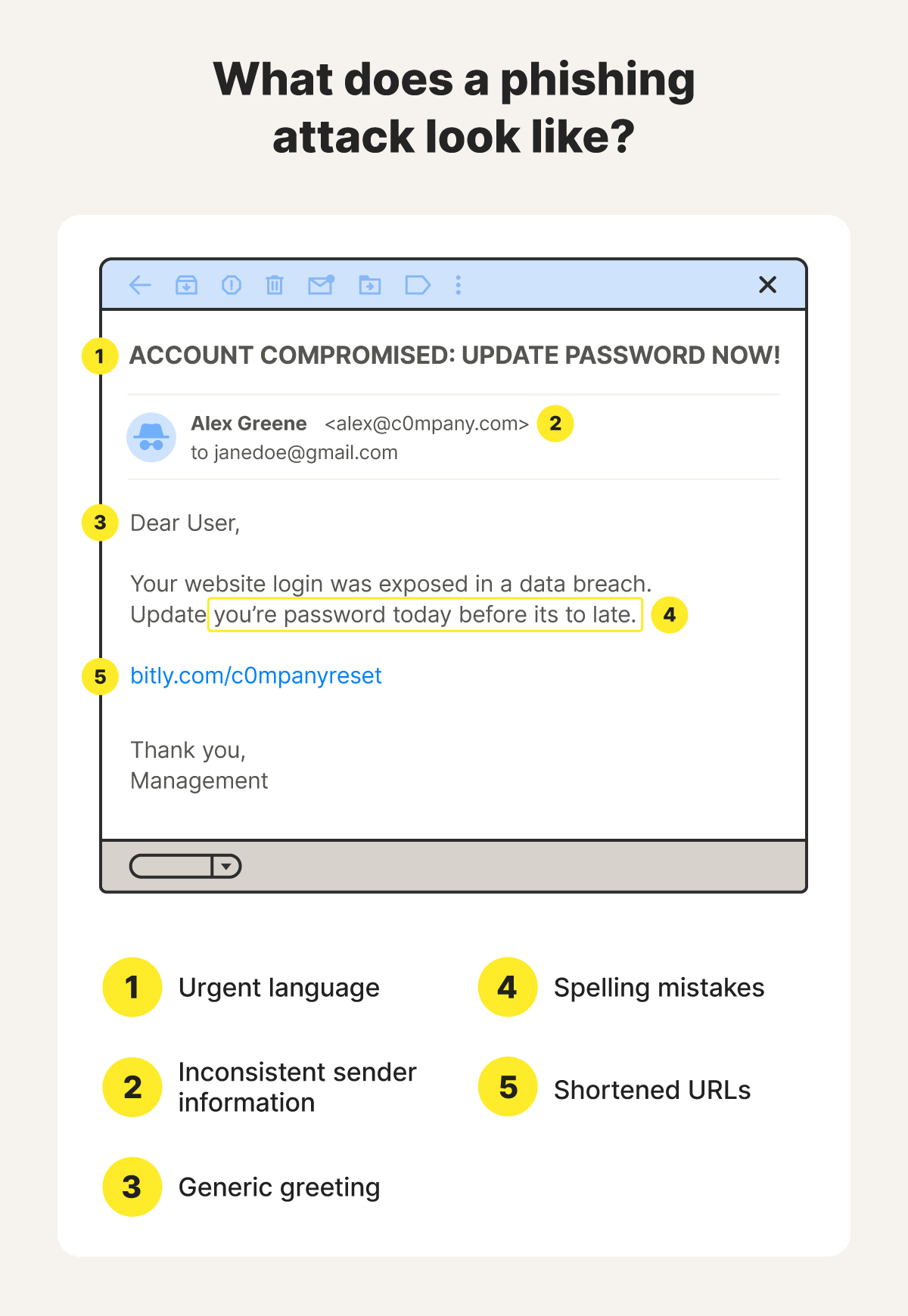

Here’s a more detailed overview of how to recognize phishing attacks:
- Shortened URLs: Attackers may use URL shortening tools like bit.ly, tinyurl.com, or bl.ink to obscure the actual destination of a link, making it difficult to determine whether it leads to an authentic website or a malicious one. While shortened URLs can be legitimate, make sure to check the full destination address before clicking them.
- Misspelled URLs: Scammers may create fake websites with similar domain names to the real version they’re imitating (like nortoon.com instead of norton.com) to trick users into believing they’re visiting legitimate websites. Before clicking a link, check carefully that the URL matches the real website you expect to be sent to.
- Unknown sender: Messages containing links that come from unknown senders are a big phishing red flag. However, scammers often impersonate legitimate organizations or trusted people to trick you into revealing sensitive information or installing malware, so don’t rely solely on the sender being recognizable as a warning sign.
- Inconsistent sender information: Inconsistent contact information, like an email address that doesn’t match the organization the sender claims to be from, is a warning sign. Legitimate companies will contact you via their official email addresses, which are usually listed on their websites.
- Urgent language: Attackers often use urgent phrases like “immediate action required,” “your account will be suspended,” or “limited-time offer” to pressure you into acting quickly without thinking. Don’t fall for it. Take your time and, if you’re ever in doubt, contact the organization the message claims to be from directly to check if it’s legitimate.
- Poor spelling and grammar: Messages that come from legitimate companies are highly unlikely to include spelling and grammar errors. If you receive a message that contains poor language, it might be part of a scam that’s been rushed, crafted by a non-native speaker, or part of a strategy to filter out skeptical individuals early.
- Generic greetings: Generic greetings like “Dear Customer” or “Hello” can be a warning sign of a phishing attack. Legitimate organizations typically personalize their messages, often including your real name in the greeting, to create a more trustworthy tone.
One of the best ways to detect phishing scams is to use AI-powered scam detection tools, which help you determine if you’re dealing with a phishing attack by scanning for suspicious language and links. If you’re ever unsure whether a message is real or part of a phishing scheme, try running it through Norton Genie to get a strong indication of how cautious you should be.
How to protect against phishing scams
Knowing how to spot phishing links is the best way to avoid falling for them, but you can also take steps to help protect your data and devices if your guard slips.
These are some of the best ways to build a more robust defense against phishing scams:
- Take your time: Whenever you’re sent a link from a sender you don’t trust, take a minute to assess the risks and investigate whether it could be a phishing attempt. Avoid panicked or impulsive actions, even if the message sounds urgent.
- Use filters: Set up spam filters on your text messaging app and email client to help block or quarantine future phishing attempts, lowering the likelihood you’ll accidentally fall for them and compromise your personal information.
- Keep software up to date: Software updates often patch security gaps that hackers could otherwise exploit to install malware on your device, after convincing you to click a fake link. Keep both your operating system and individual apps up to date for the best protection.
- Use 2FA: Two-factor authentication (2FA) adds an extra layer of security to your online accounts by requiring additional verification to log in. This makes it harder for attackers to access your accounts if they steal your password in a phishing attack.
Find malware on your device
Even when you know what to look for, sophisticated phishing attacks can catch you off guard. If you’ve clicked a phishing link, help protect yourself by getting Norton 360 Deluxe to scan for and remove malware that could give cybercriminals access to your sensitive data. You’ll also benefit from scam detection tools and fake website blocking features that help you defend against future threats.
FAQs
What should I do if I clicked a phishing link on my iPhone?
Apple has strict security protocols in place that mean it’s difficult for malware to infect iOS devices. Unless your iPhone is jailbroken, you probably don’t have to worry about malware after clicking a phishing link. However, you should still take precautions like enabling airplane mode to disconnect from networks, changing your Apple ID password, and running a mobile security scan to help protect against other attack vectors.
Am I at risk if I clicked a phishing link but didn’t enter information?
Yes. Even if you don’t enter any details, fraudulent websites that you’re directed to by phishing links might trigger automatic malware downloads that compromise your device security.
Is there anything I can do to protect myself if I entered information on a spoofed website?
The best ways to protect yourself after accidentally giving information away to a phishing scammer include changing your passwords for any compromised accounts, contacting your bank to help protect your finances, and freezing your credit to limit potential damage from identity theft.
Can phishing links hack your phone?
Phishing links can install malware on your phone, which could mean your phone gets hacked and a cybercriminal steals your sensitive data. However, malware infections are generally less common on mobile devices.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.










Want more?
Follow us for all the latest news, tips, and updates.