How to use Tor: Benefits and risks explained
Tor is a powerful tool for enhancing your online anonymity, but it’s not a complete privacy solution. Learn how to set it up, explore what it does best (and where it falls short), and discover why pairing it with a trusted VPN could give you stronger, layered protection against prying eyes.

Want to explore the dark web and browse more anonymously? You’ll need a specialized dark web browser like Tor, which lets you access hidden parts of the internet while protecting your identity. Tor works by routing your traffic through multiple encrypted servers, masking your location, and making it much harder to track your online activity.
How to set up and use Tor for the first time
If you’re new to Tor, setting up the browser software and connecting to the network might seem intimidating, but it’s actually straightforward. We’ll guide you through how to connect on Windows, Mac, Android, and even iOS.
Windows
1. Navigate to the Tor Project’s Download page, select Download for Windows, and then double-click the downloaded .exe file to install the browser.

2. Launch the Tor Browser from your desktop or Start menu, then click Connect on the welcome screen to establish a secure connection to the Tor network.

Mac
- Navigate to the Tor Project’s Download page and select Download for macOS.
- Open the .dmg installer file once the download has finished.
- Drag the Tor Browser app to the Applications folder in the pop-up window.
- Open Tor Browser and click Connect to connect to the Tor network.
Android
- Search for Tor Browser in the Google Play Store and tap Install.
- Once the app is installed, open it and click Connect to join the Tor Network.

iPhone
Due to certain requirements from Apple, Tor Browser is not available for iPhones, but there are still ways you can connect to the Tor network when using an iOS device.
The Tor Project recommends using the Onion Browser app in tandem with a VPN as the best way to connect to the Tor network, although this app’s privacy protections are somewhat less robust than those of the Tor Browser. Here’s how you can download and install Onion Browser:
- Open the App Store and search for Onion Browser.
- Tap Get and wait for the app to install.
- Open the app and tap Connect to connect to the Tor network.
What is Tor?
Tor, short for “The Onion Routing project,” is a free, open-source network built to protect online privacy and enable access to the dark web. It routes your internet traffic through multiple server “nodes,” each adding a layer of encryption. This process makes it extremely difficult for websites, internet service providers, or other network observers to trace your activity or pinpoint your location.
Originally developed to protect U.S. intelligence communications online, Tor is now used by the public for a wide range of purposes, both legal and illegal. These include bypassing government censorship, whistleblowing anonymously, conducting covert communications, and accessing or trading illicit goods and services. Many users, however, are simply everyday people who value privacy and choose to browse anonymously as a matter of principle.
But while Tor encrypts your traffic, it doesn’t hide the fact you’re using it. That’s why savvy Tor users go a step further, encrypting all their internet data via a VPN first — a set-up known as “Tor over VPN” — adding a powerful extra layer of privacy that masks both your IP and Tor usage.
Advantages
Tor offers valuable benefits for a wide range of privacy-conscious users, including journalists, activists, political dissidents, those with heightened security concerns, and everyday individuals who simply prefer to keep their internet browsing private.
Here are some of the benefits of using Tor:
- Censorship avoidance: Tor can help bypass censorship by governments and other entities by helping you overcome certain website restrictions while remaining anonymous.
- Enhanced privacy: By using multi-layered encryption and ensuring that no single node in the network knows both the source and destination of your traffic, Tor keeps your online activity more private.
- Free and open source: You can trust the code behind Tor because it’s open source and available for anyone to inspect, audit, or contribute to.
- Tracking resistance: Tor does not retain user data or logs, and it helps stop websites from tracking users based on their IP address. The Tor browser also limits browser fingerprinting.
- Access to hidden services: Tor lets its users access hidden services on the dark web. Both the user and the service remain anonymous when these services are accessed, further enhancing privacy.
Disadvantages
While Tor offers strong privacy protections, it comes with notable drawbacks that can make it impractical for everyday use, and the dark web content it grants access to can put users at risk.
Here are some of the main disadvantages of using Tor:
- Sluggish performance: Tor’s multi-layered encryption and routing slow down browsing speeds significantly compared to standard web connections.
- Restricted website access: Many websites block Tor traffic due to abuse from bad actors. Exit nodes are often blacklisted, which can limit functionality. For example, you may have trouble doing your online banking over Tor.
- Stigma and scrutiny: While legal in most countries, Tor’s association with criminal activity can trigger suspicion from ISPs or law enforcement, even when used for legitimate privacy.
- Exposure to harmful content: The dark web hosts a high volume of illegal and malicious material. Files may contain malware or spyware, and accessing certain content can lead to legal consequences. Always proceed with caution.
- Not foolproof: Tor boosts anonymity but isn’t flawless. Logging into personal accounts, downloading files, or connecting without a VPN can expose your identity or IP address via the entry node, if it’s compromised or monitored.
How does the Tor Browser work?
The Tor Browser works by routing internet traffic through a global network of server nodes to mask your IP address and activity. It encrypts data multiple times, each layer peeled off by a different node, helping to enhance user privacy and making tracking or surveillance extremely difficult.
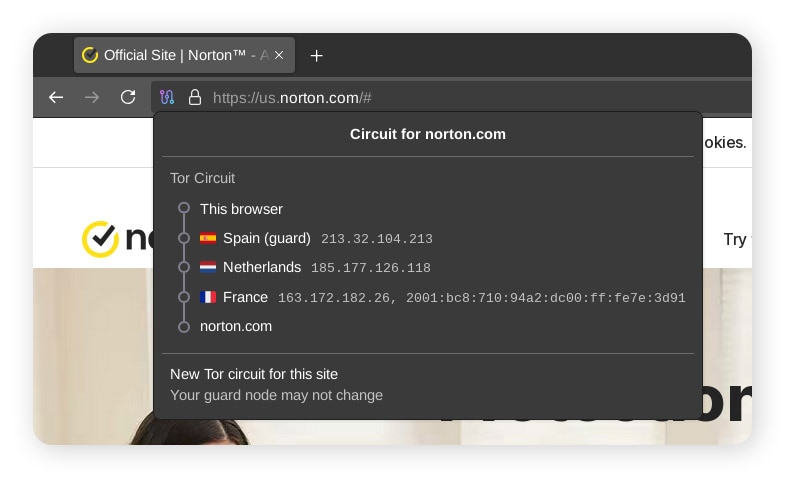

For a more detailed look at how Tor works, let’s take a look at the three nodes in a Tor circuit:
- Entry node: Also called the guard node, this is the first server your device connects to. It sees your real IP address (unless you’re using a VPN) but doesn’t know the website or service you’re accessing — only the IP address of the next node in the network.
- Middle node: This relay acts as a bridge, passing your encrypted traffic from the entry node to the exit node. It knows only the previous and next hop in the chain, not your identity or the final destination.
- Exit node: The last server in the Tor circuit decrypts the traffic and sends it to the destination website. While it can see the content being accessed if the connection isn’t encrypted, it doesn’t know who originally requested the data.
Each node in the Tor circuit only knows the IP address of the node directly before and after it, never the entire path. This segmented design makes it extremely difficult for any observer, whether it’s a website, ISP, or malicious actor, to trace your traffic back to you. However, they may still be able to detect that you’re using Tor.
How is Tor different from a VPN or proxy server?
Tor, VPNs, and proxy servers all enhance privacy and anonymity in different ways, and in some cases, they can be combined for stronger protection. Here’s an overview of the main differences between Tor, VPNs, and proxies:
- Tor routes your traffic through a decentralized network of encrypted nodes, providing strong anonymity. Because no single point knows both your identity and destination, it's difficult to trace activity back to you. However, Tor is slower than a VPN and may not work with all websites.
- VPNs encrypt your traffic between your device and the VPN server, hiding your search history and browsing activity from your ISP and local network. VPNs are typically faster than Tor and more user-friendly, but you must trust the provider not to log your data.
- Proxy servers change your IP address by routing traffic through an intermediary server, but offer no encryption. While fast, proxies leave your data visible to both your ISP and the proxy operator. The main difference between a proxy server and a VPN is that proxies don’t secure your traffic.
Use Norton VPN to maximize your privacy when browsing with Tor
Tor offers strong protection against network surveillance and website tracking, but without a trusted VPN, your ISP or network admin may still see that you’re using Tor, and your real IP address could be exposed.
Norton VPN bolsters your privacy and security when using Tor by encrypting your internet traffic before it reaches the Tor network, cloaking your IP address and adding an extra layer of powerful protection against network surveillance. Get Norton VPN today to start browsing the web more freely and anonymously.
FAQs
Can I be tracked while using Tor?
Potentially, yes. Tor greatly enhances anonymity, but if an attacker controls both the entry and exit nodes, they could attempt traffic correlation to link your identity to your activity. You can also be tracked by logging into personal accounts, downloading unsafe files, or modifying browser settings that expose your digital fingerprint. Using Tor with a VPN adds an extra layer of protection by masking your IP from the Tor entry node.
Is Tor illegal?
Tor is completely legal in many places, including the U.S., EU, UK, and Australia, but illegal in others, like China and Russia. Due to illicit activities and dark web criminality, anonymous browsing is looked at with suspicion in certain countries. As with VPN legality, you should always check yourself and see if the dark web is legal in your country.
Is Tor safe?
Using Tor and the Tor Browser is considered relatively safe if you use the default security settings, but keep in mind that Tor does not provide end-to-end encryption. Likewise, it will not protect you from common digital threats like malware or phishing attacks. When using Tor, practice good security hygiene by avoiding suspicious links and using reliable antivirus software.
Is Tor a VPN?
No, Tor is not a VPN. While both tools enhance online privacy, they work differently. Whereas Tor routes your traffic through a decentralized network of encrypted relays, helping to mask your identity, a VPN encrypts your internet connection and tunnels data via a single server. They serve similar goals but use distinct technologies with different benefits.
Are there any Tor alternatives?
There are alternatives to Tor, including the Invisible Internet Project (I2P), Lokinet, and Psiphon. Research what they offer and assess your privacy needs to make a decision about which dark web browser works best for you.
Do you need a VPN if you use Tor?
You don’t technically need a VPN to use Tor, but using one can offer enhanced privacy by hiding Tor usage from your ISP and masking your real IP address from the Tor entry node. This so-called “Tor over VPN” set-up adds an extra layer of security, which can be especially important on monitored or public networks.
Tor is a trademark of The Tor Project.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.







Want more?
Follow us for all the latest news, tips, and updates.