What does a VPN hide? 6 common identifiers VPNs disguise
VPNs don't just hide your IP address — they encrypt all your internet traffic, helping to mask your identity and prevent your online activity being tracked. Read on to discover everything a VPN can hide and how it enhances your online privacy. Then, get a VPN with bank-grade encryption to experience these benefits firsthand.

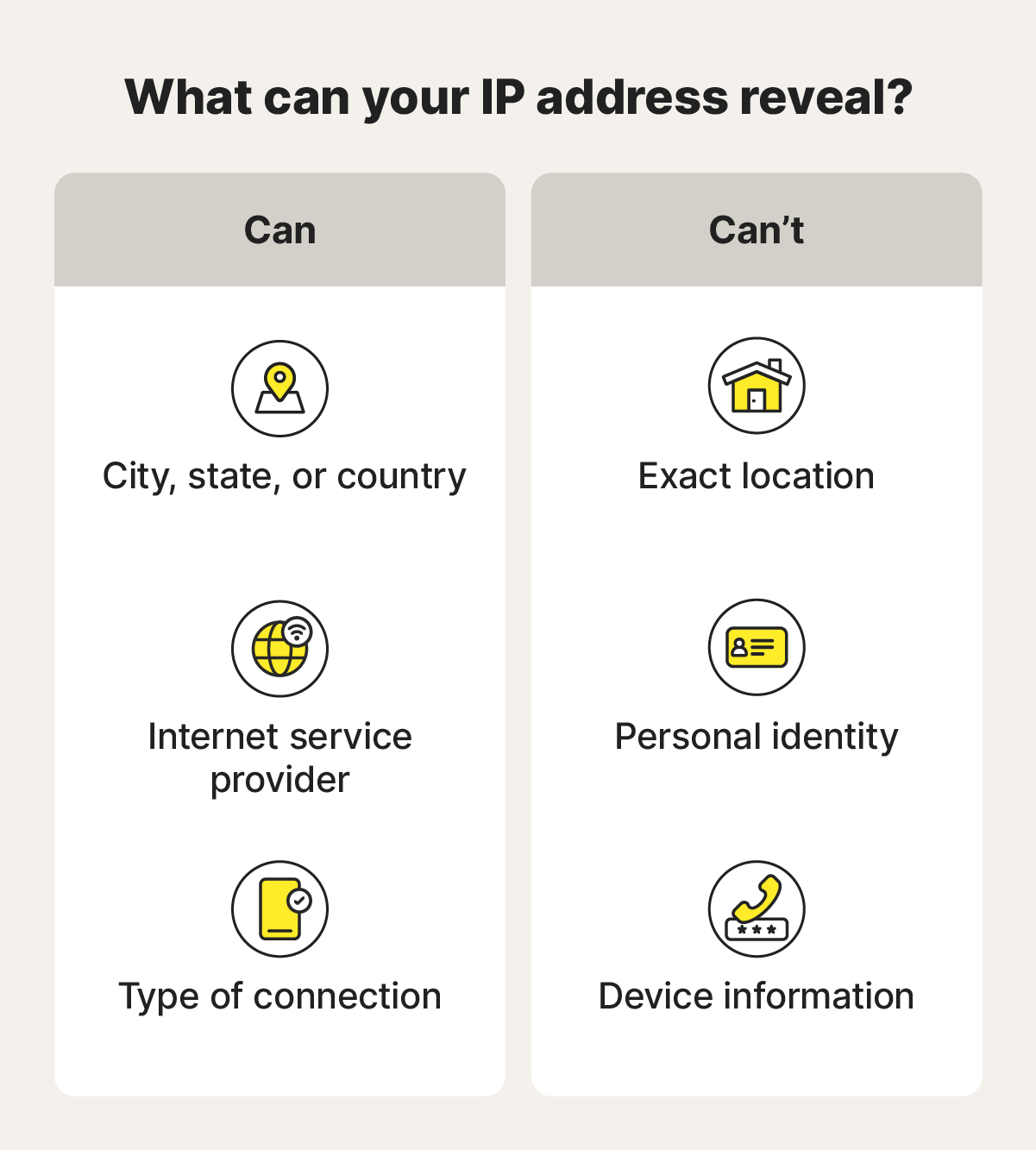
All online activity leaves a trail — but a VPN can make some of your digital footprints virtually untraceable by hiding your IP address, location, browsing history, and even the files you download, giving you true digital privacy. The best VPNs can even hide the fact that you're using one.
This means a VPN can empower you to browse, buy, and communicate over the web without fear of third-party trackers, snoops, or hackers seeing what you get up to or peeking at the data you send and receive. But VPNs don’t guarantee total anonymity — there are limits to what they can keep private.
Let’s start by taking a look at what a VPN does hide.
1. IP address
VPNs hide your IP address by routing your internet traffic through an encrypted tunnel to a remote server. This masks your real IP address by assigning you a virtual IP address that’s not tied to your network or device — helping to prevent websites, advertisers, and other third parties from identifying and tracking you.
Spoofing your IP address to hide your identity online also makes it more difficult for hackers to target you specifically with malware, phishing, or other social engineering attacks. Some VPNs also come with IP rotators to help prevent site trackers from gathering your data.

2. Physical location
Sites and services use your IP address to determine your location and tailor content accordingly. By changing your location on your iPhone or other device with a mobile VPN, you can avoid dynamic pricing that varies by region, and access content freely.
This allows you to stay informed with global news, use social media freely, and stream your favorite media without restrictions — even on vacation.
3. Search history
One of the main benefits of a VPN is that it encrypts all of your internet traffic, preventing your internet service provider (ISP) and other third parties from seeing your search history.
While it won’t erase past searches — or clear your cookies and browser history — it can keep your future browsing habits more anonymous, and help avoid targeted ads or surveillance based on your personal information and online behavior. Some VPNs can even block ads so you don’t have to see them.
4. Online activities
Even with a VPN, your online activity might still leave traces. By securing your internet traffic with powerful encryption, VPNs help keep your online activities private, making it difficult for anyone to keep tabs on you by monitoring your web traffic.
Even your own ISP isn’t able to see what you get up to while you’re using a VPN — this has the added benefit of preventing bandwidth throttling, allowing you to enjoy consistent, high-speed internet even when video streaming or gaming.
5. Downloads
By channeling the online data you send and receive through an encrypted tunnel, VPNs can mask downloads and other forms of file sharing. Without this protection, other users on P2P networks may be able to identify you, and your downloads can be tracked, potentially exposing you to targeted attacks or data theft.
6. Itself
A VPN that can hide itself adds an extra layer of privacy and security by making it harder for websites, network administrators, and ISPs to detect, monitor, and block VPN connections. This is crucial for journalists and others who may be working in restrictive areas and need to bypass barriers and access the internet freely without drawing undue attention.
Beware that VPNs are illegal in some countries, so be sure to research local rules and regulations carefully if you’re considering using a VPN while traveling abroad.
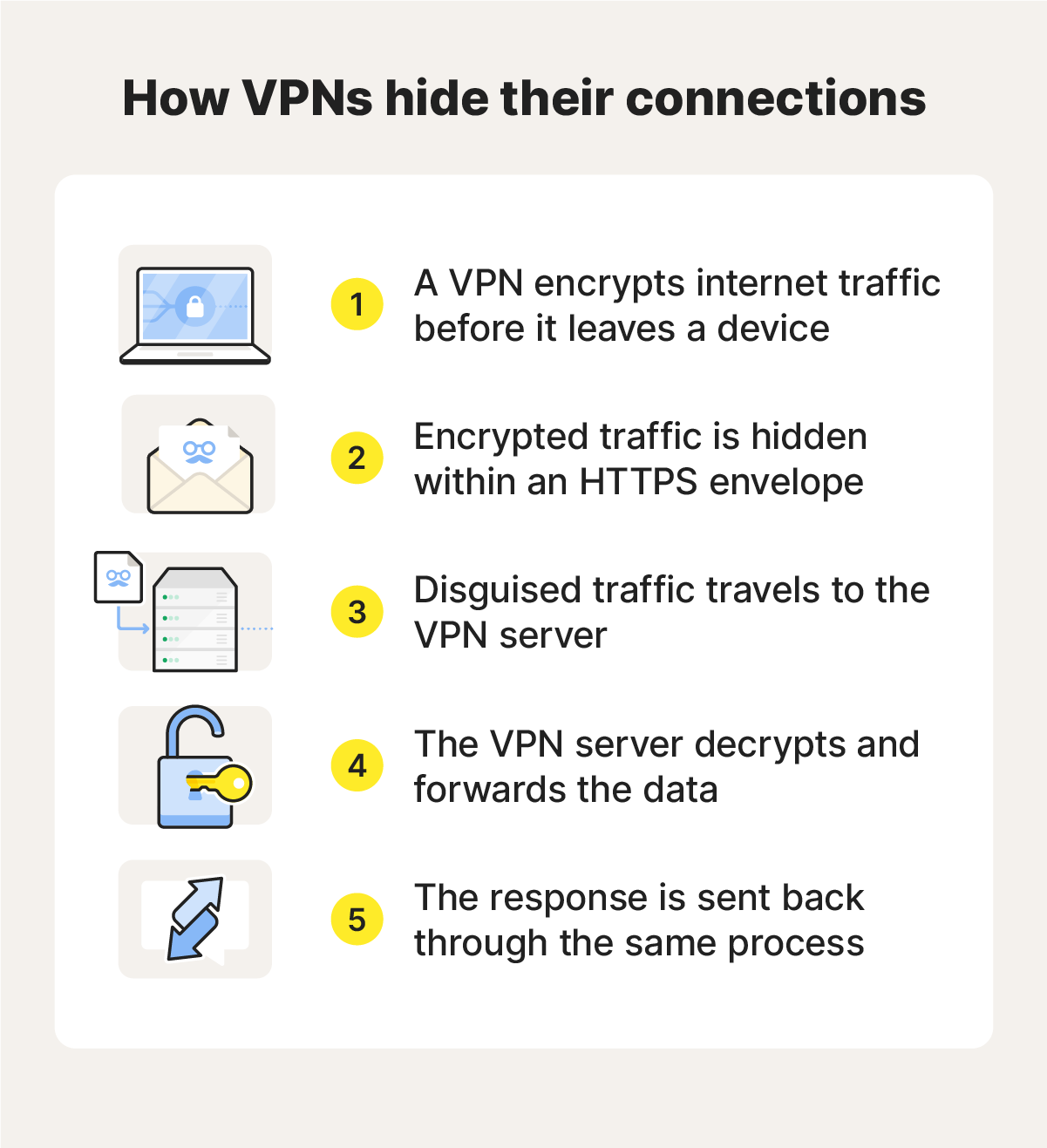

Norton VPN uses a proprietary VPN protocol called Mimic, which masquerades as a regular HTTPS-encrypted web connection. This means that not only is your browsing activity anonymized, but your VPN usage flies under the radar too, blending with normal internet traffic to evade firewall detection and take your privacy to another level.
What can’t a VPN hide?
VPNs can help mask (or change) your IP address and the contents and nature of your internet traffic, but they can’t completely hide your online identity or activities. To make the most of these powerful privacy tools, it’s also important to understand their limitations.
Here’s a rundown of some of the online activity and information that a VPN can’t hide:
- Account activity: If you're logged into an account like Google or Facebook, those companies can still track your activity, even with a VPN.
- Cookies and trackers: Websites can use cookies and internet tracking to monitor your behavior, regardless of your IP address.
- Payment and banking details: Financial transactions made through an encrypted VPN connection can still be linked to you through your bank or payment provider.
- Website submissions: If you enter personal information on a website, even inadvertently, a VPN won’t prevent the site from collecting it.
- Data consumption: Your ISP can still see how much data you're using, even if they can't see what you're doing or which sites you’re visiting.
- Digital fingerprinting: Websites may be able to identify you based on unique device characteristics like screen resolution, browser settings, and installed fonts.
- VPN logs: Unless you use a no-log VPN, the government can still trace your online activities if the VPN service provider shares the data it collects and logs.
While a VPN can’t hide everything, it remains a powerful tool for keeping your browsing, streaming, and downloads more private. Combined with smart browsing habits and other cybersecurity tools, a VPN helps you take control of your digital footprint.
Protect your privacy with a VPN
Any VPN worth its salt covers up many of the digital breadcrumbs used to track your internet activities. But ours can even mask its own connection.
Norton VPN shields your IP address, encrypts your traffic, and blocks trackers, helping to ensure your online activity stays private. With cutting-edge VPN protocols, a strict no-log policy, and other advanced security features, you can enjoy top-tier data protection, anonymized browsing, and seamless access — all in one. Get ironclad online privacy protection now.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.






Want more?
Follow us for all the latest news, tips, and updates.