How to choose antivirus software
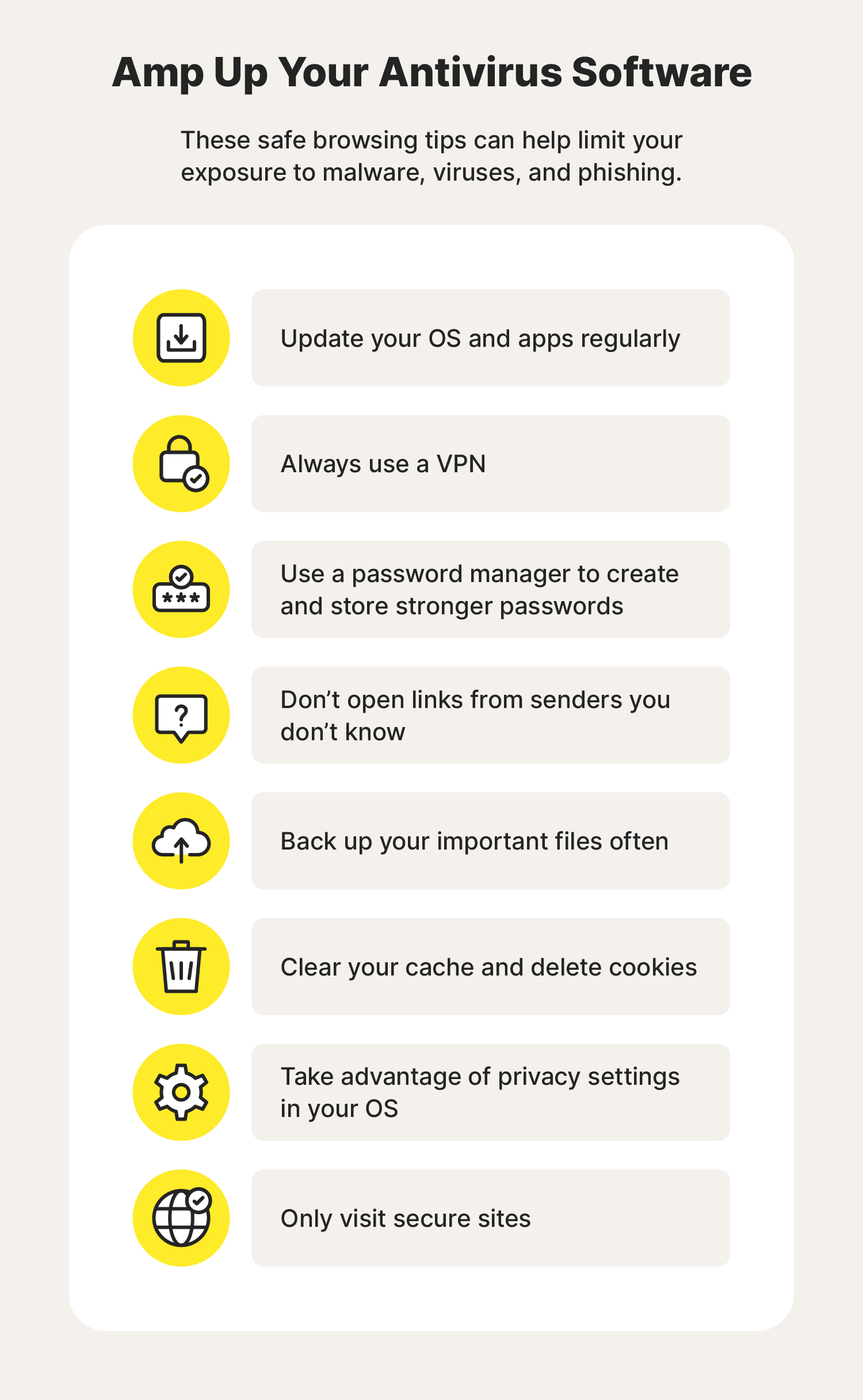
Protecting your digital life can sometimes feel overwhelming. Thankfully, there are security tools that can do the hard work for you. Learn how to pick the right antivirus software, like Norton 360 Deluxe, to help block viruses, prevent threats, and stay safer online.

Spending a little time learning how to pick the best antivirus software now can save you a lot of time, hassle, and money in the future. Learn how to choose the right antivirus software by evaluating the features, coverage, and price that fit your needs.
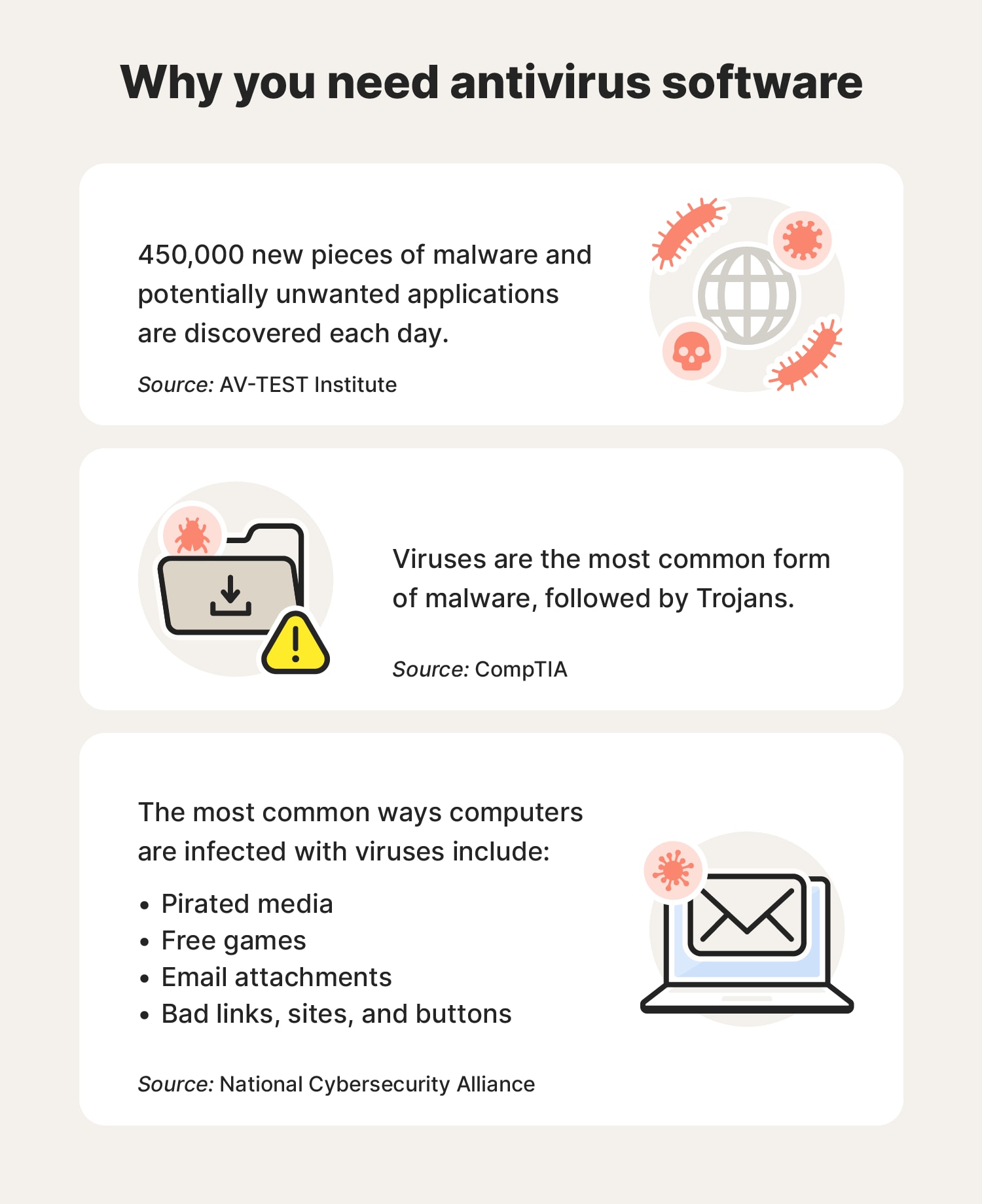
Why you need antivirus software
Using antivirus software is important because it helps secure your digital information and prolong the lifespan of your devices. Modern security software goes above and beyond to:
- Protect against malware and viruses: With millions of new viruses and malware created every year, it’s never been more important to protect yourself from these kinds of threats.
- Safeguard personal and financial information: As we spend more time online doing everything from socializing to banking, keeping your information secure is more important than ever.
- Prevent unauthorized access and identity theft: Some of the most insidious types of malware are designed to access your personal information in order to steal your identity.
- Enhance the security of online activities: Shopping, gaming, and using social media are all potential sources of viruses and malware.
- Shield against ransomware attacks: Ransomware holds your data hostage, encrypting it until you pay to have it released back to you.
- Ensure the safety of your digital files and data: Some viruses and malware will damage or delete your data, while others can steal your data to use it against you if you don’t have protection.
Consider the right factors when looking for the best antivirus software
When you’re trying to figure out how to choose a good antivirus software suite, start by breaking down the factors that are most important to you and your family’s unique requirements.
| What to look for when choosing antivirus software | |
| Features | Real-time protection, low system impact, and additional security tools are important antivirus software features. |
| Depth of Protection | Software that covers everything you need without skimping on what you want is vital. |
| Ease of Use | A user-friendly setup and interface ensure you can navigate your antivirus software with ease. |
| Reliability | Dependable antivirus software should consistently protect your system from threats. |
| Devices Covered | Ensure your chosen software safeguards all your devices, including computers, phones, and more. |
| Data Privacy Policy | Review the antivirus provider's data privacy policy to safeguard your personal information. |
| Customer Support | Quality customer support can be a lifesaver when you face issues or have questions. |
| Price | Balance your budget with the level of protection and features the software offers. |
| Free Trial Availability | Look for software with a free trial to test its suitability for your needs. |
Here are the most important factors to consider when choosing the best antivirus software for your needs:
Features
For antivirus software to be effective, it needs to have the right combination of features. Ideally, any solution would have most or all of the following features to keep malware at bay:
- Real-time protection: You shouldn’t have to manually scan your device for security software to identify and stop a virus from entering or deploying on your system. To stop malware from getting a foothold into your system, your antivirus software should be running in the background at all times.
- Full system scanning: In addition to checking new files for infection, your antivirus software should scan your devices from top to bottom. These full system scans can look for and eliminate existing problems.
- Regular updates: To keep up with the millions of new viruses created each year, look for antivirus software that updates regularly. For signature detection and heuristic detection to work, it needs to have the most current information possible.
- Low system impact: When using any kind of software, you don’t want it slowing down your device; the same is true with antivirus software. During a free trial, pay attention to how quickly your computer or device opens programs and performs normal tasks.
- Phishing protection: Anti-phishing features verify websites and keep your personal information secure. Look for security software suites that specifically offer phishing protection or some kind of identity theft protection.
- Added security tools: Because digital privacy and security can be complicated, look for a security software suite that offers extra tools, including:
- VPNs
- Password managers
- Parental controls
- Expanded privacy controls
- Firewalls
Depth of protection
The depth of protection in antivirus software is vital because it determines the extent to which your digital environment is shielded from a wide range of ever-evolving threats. Ideally, you’ll want to find software that protects your systems from a variety of threats (malware, ransomware, phishing, etc.) without being so feature-heavy that it becomes difficult to use or too expensive.
Good antivirus software will protect you from viruses while also offering features that are easy enough to use that they improve your overall cybersecurity habits.
Ease of use
Easy-to-use software is especially important when it comes to antivirus protection because it will encourage you to use it. Complicated software can be frustrating, especially because you don't want your malware protection getting in the way of using your device. If you’re frustrated, you’re less likely to use it, which limits its ability to protect your data.
Difficult software also increases the number of user errors, further reducing its effectiveness. To help you get in the habit of using it regularly, look for user-friendly software that updates easily. The key to any good cybersecurity practice is consistency.
During a trial, see how quickly you’re able to get the program running. If it takes a while or you have to search for answers online or in a knowledge base, it might be too complicated to be effective. Evaluate the interface, too. Are the most important features easy to find?
Reliability
Reliability is one of the most important criteria for almost anything you buy, but when it comes to antivirus software, knowing it's going to work when you need it most is non-negotiable.
Reliable antivirus software does these things:
- Offers better threat detection: The best malware protection uses multiple methods for detection, testing, and elimination. Multiple detection methods cover the limitations that may exist in any one individual method.
- Minimizes false positives: If your antivirus software frequently misidentifies threats, you’ll be less likely to trust it when it actually sees something dangerous.
- Consistently updates: When new and emerging threats arise, you want your software to be ready to find and block it.
Devices covered
We’ll be blunt: smartphones and tablets need security software. Because these devices are how many people access the internet a majority of the time, hackers are building malware to exploit and infect these devices alongside computers. That’s why you need to consider all of your devices when looking for protection.
Any software you consider should offer protection for the devices you currently use or think you’ll use in the future. There are many advantages to choosing a security software suite that offers protection for multiple devices and operating systems, including:
- A wider range of coverage
- The ability to use all of your devices safely
- The ability to add new devices
Data privacy policy
Because security software needs access to your devices at all times and at the deepest levels, choose a provider with data security practices and policies that keep your information safe. While it’s impossible to prevent all data breaches and information theft, a strong privacy policy limits your exposure by reducing how much of your information is stored on your software company’s servers.
Reading through a privacy policy is tough for anyone who isn’t an attorney, so check out some online reviews of the options you’re considering. Professional reviews should cover data privacy.
Customer support
Having a way to get help if something goes wrong with your software is another factor to consider when you’re looking at antivirus protection options. Customer support goes beyond just having a phone number to call (though that’s important, too) and includes things like satisfaction guarantees and help with billing issues.
Online reviews are a good way to find out how a company treats its customers, and they might also illuminate other support features like:
- Knowledge banks
- Chat support
- Forums
Price
There are free antivirus options available, but if you want the best protection, paying for antivirus software makes sense. When you pay for security software, it supports the teams of people who are monitoring emerging threats, writing new code to stop malware, and updating your antivirus software.
Paying for this software has some other benefits, too, including:
- Multiple device coverage
- Better or expanded features
- More comprehensive customer support options
Look into the options that meet your needs, then compare prices to see which companies offer the best value for your dollar. If they’re all priced competitively, try them out before committing.
Free trial availability
A free trial is a great way to pick the right antivirus software because it allows you to test exactly how easy it is to download, update, and use. As you try it out during the trial period, you’ll also be able to see how it affects the performance of your devices and whether or not you’re using all of the included features.
Know when to buy antivirus software
If you aren’t sure when the right time is to invest in a suite of antivirus and security software, consider how you use your devices. Here are a few reasons it might be time to sign up for comprehensive protection, which can help protect you from malware and hackers:
- You use your devices for banking: Not only does your financial information have a lot to do with your day-to-day activities, but it’s also important for your future. If a hacker gains access to your banking app logins because of a piece of malicious software, it could have long-term consequences.
- You shop online: Reputable online stores spend a lot of time and money making sure their sites are safe for you to use. But there’s no perfect system for stopping hackers from exploiting vulnerabilities and stealing customer information.
- You have kids who use the internet: While kids are generally pretty savvy when it comes to computers and smart devices, they’re just as susceptible to accidentally clicking malicious links or browsing unsafely. Security software can help you protect them when they’re online.
- You use your personal devices for work: The more you use your devices, the more exposure you have. If you use your personal phone, computer, or tablet for work, you could inadvertently be exposing your workplace to additional threats if you don’t use security software.
- You use devices for private communication: Whether you’re texting friends, sharing photos with your family, or chatting with people using messaging apps, it’s important to keep your correspondence private. Antivirus software can help identify unsafe links, spyware, and phishing attempts that could make your private life public.

Get the best antivirus software today
When you want the best defense against viruses and malware, you want Norton 360 Deluxe. In addition to strong protection against hackers, viruses, malware, and ransomware, you get a secure VPN for private browsing, a password manager for creating and safely storing stronger passwords, and parental controls to keep your kids safer online.
FAQs about how to choose the right virus protection
Want to learn more about picking the right security software? We’ve got answers.
Is it worth paying for antivirus software?
Yes, it is worth paying for antivirus protection. Very few devices, if any, are 100% safe from hackers, malware, and viruses, and for a relatively low cost (especially when compared to the cost of paying a ransomware demand or buying a new computer), you can get real protection that works.
How many antivirus programs should I have?
One is all you need. If you have multiple antivirus programs running simultaneously, it could dramatically slow down your device or cause them to negatively interact with each other.
How does antivirus work?
Antivirus software works in several ways. It can look for and stop malware that contains code from known viruses, isolate suspicious programs, and run them in a secure environment to see what they will do. It can even look for and stop programs and code that look suspicious based on known malware examples.
What happens if I don't use antivirus?
It depends. You might never download a virus or another piece of malware onto your devices, or you might have a lot of problems with hackers and viruses that slow down your computer and compromise your personal information. Antivirus software gives you peace of mind and a convenient way to protect your devices and your information when you’re online.
Editorial note: Our articles are designed to provide educational information for you. They may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review the complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc. For more details about how we create, review, and update content, please see our Editorial Policy.







Want more?
Follow us for all the latest news, tips, and updates.