Personal cybersecurity resolutions for 2022: A month-to-month guide
Elevate your personal cybersecurity this year with this month-to-month guide on how to adopt cybersecurity best practices over time, plus pointers for how to help prevent a cyberattack.

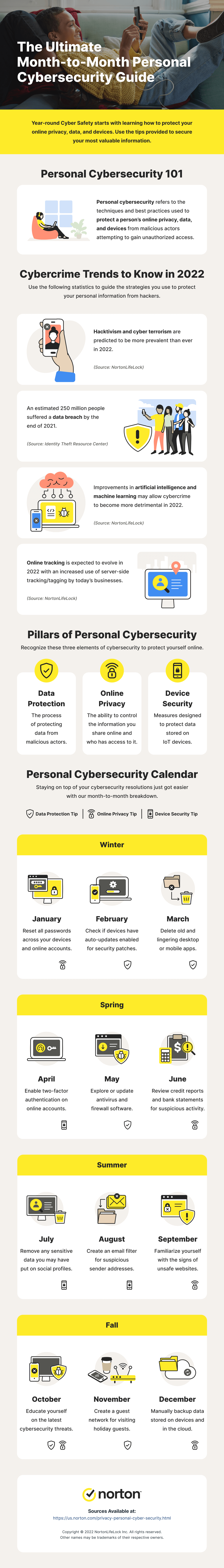
As the COVID-19 pandemic continues to force everyday people and working professionals to entangle their lives with the digital world, personal cybersecurity becomes even more important for the Cyber Safety of our devices and online privacy. From data stored in the cloud to the information shared on social media sites, there is a lot of personal information in need of protection against today’s cybersecurity threats. And with hacktivism and cyberterrorism expected to become more prevalent in 2022, taking the time to educate yourself on how to devise a proper cyber defense may be more valuable than you think.
We want to help you in your efforts by offering an all-in-one guide to personal cybersecurity. You’ll be able to learn about what personal cybersecurity is and what it entails, along with cybersecurity tricks that can make safeguarding your data pain-free all year round. We’ve even included a month-to-month breakdown for your personal cybersecurity resolutions to help you stay on track with your goals this year. So, read on to find the different ways you can reinvent what it means to be cybersecure in the new year.
What is personal cybersecurity?
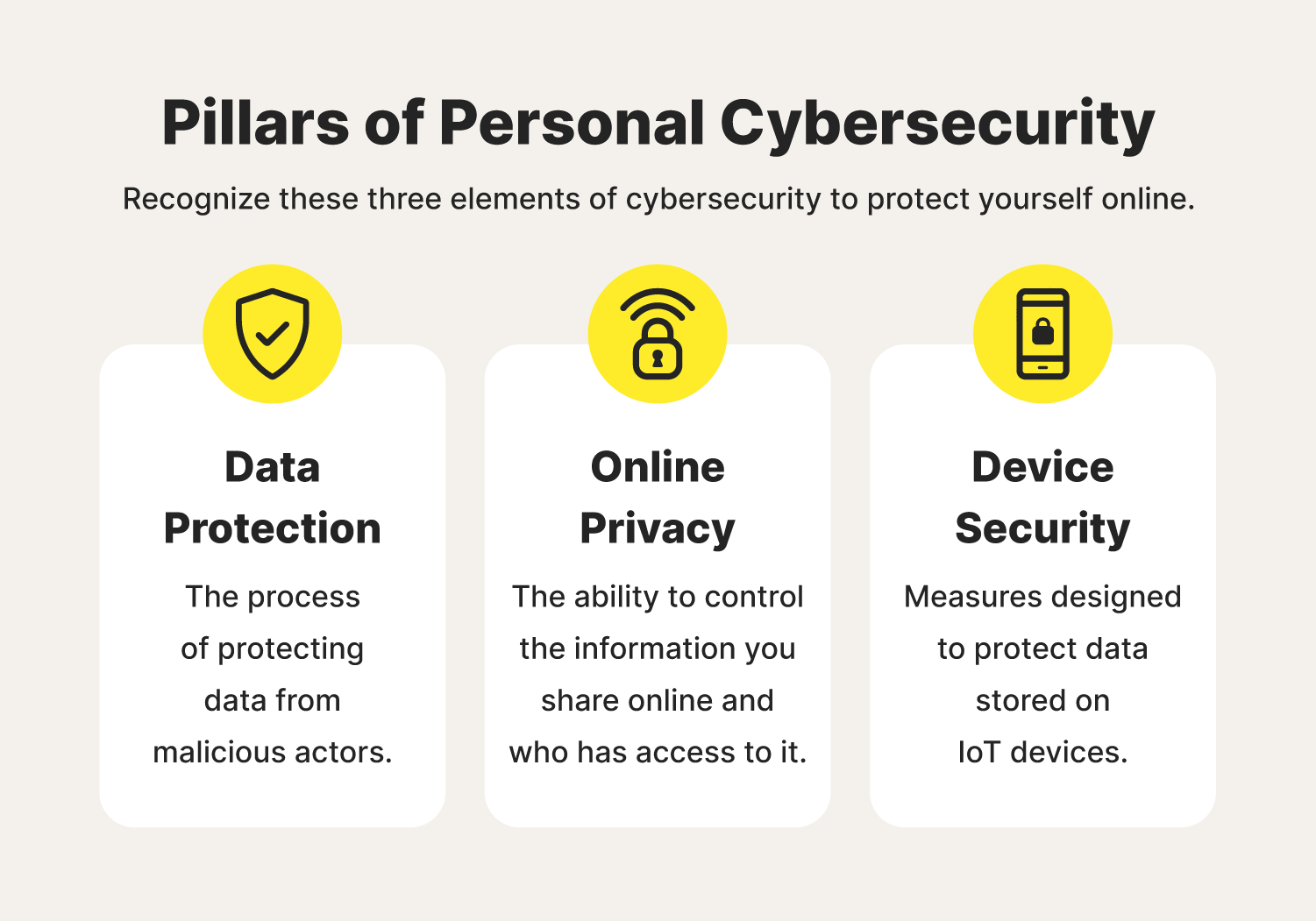
Personal cybersecurity involves the techniques and best practices used to protect your privacy, data, and devices from unauthorized access and malicious cyberattacks. You might think of personal cybersecurity as being made up of three pillars:
- Online privacy: The ability to control the information you share online and who has access to it, including protecting your identity.
- Data protection: The process of protecting your online data from malicious actors, along with the ability to restore such data if rendered unusable.
- Device security: Measures designed to protect data stored on smartphones, laptops, and other IoT devices, as well as these physical devices as a whole, from malicious actors looking to corrupt information for personal gain.
Online privacy and personal cybersecurity
You could think of your online privacy as one of the main ingredients to the most decadent personal cybersecurity cake. With access to details such as credit card and banking information saved online, hackers could destroy the credit history you worked so hard to build — even potentially selling such information on the dark web for other cybercriminals to use.
And seeing as almost 10 million people have their identity stolen each year, everyone should be aware of how to protect themselves against these cybersecurity threats.
Use the following cybersecurity best practices to help support your online privacy and security in 2022 and beyond.
Be aware of cybersecurity trends
Think of personal cybersecurity as a home security system. Even though there are policemen ready to respond in case of an emergency, it is still your responsibility to turn on your alarm before you leave. Cybersecurity tools like antivirus software are great for warning you of cyberattacks if they arise — however, everyone has a part to play in the protection of their life’s most valuable data.
Educating yourself on the latest cybersecurity issues impacting the safety of your digital identity can help you spot problems that some technology can't, as new cyberthreats and malware emerge almost every day.
Personal cybersecurity resolution: Educate yourself on the latest cybersecurity threats by doing online research regarding newly emerging threats impacting the safety of online data.
Prioritize password security
One of the best things you can do to fend off hackers is prioritize your password security. With strong, unique passwords in place, methods like password spraying and credential stuffing have the potential of becoming useless against your network and devices.
- Personal cybersecurity resolution: Reset all your passwords across your devices and online accounts at least every three months.
Avoid suspicious links anddomains
Clicking on unknown links sent via email or found online could open you up to social engineering scams or drive-by downloads that could compromise your personal cybersecurity. Hackers use fake links to install malware and/or trick people into willingly handing over sensitive information that cyberthieves can use to their advantage.
- Personal cybersecurity resolution: Save and bookmark all frequently visited websites used to access sensitive information.
Safeguard personal identifiable information (PII)
Personal identifiable information (PII) refers to any kind of information that cybercriminals could use to locate or identify you. This includes birth dates, Social Security numbers, addresses, phone numbers, IP addresses, and other forms of identification. Always be cognizant of the things you share on social and company accounts and adjust privacy settings so that only specific individuals can view profile details.
- Personal cybersecurity resolution: Review all social profiles and remove any PII that may be viewable by the public.
Data protection and personal cybersecurity

A great rule of thumb is that all data stored digitally—whether that be on physical devices or in the cloud—should receive adequate protection against current cybersecurity threats. There are a number of ways to go about this, but the overall objective of each is to prevent hackers from using your information for fraudulent activities like identity theft or blackmail.
Within the last year alone, the amount of compromised digital assets rose by 27%—further cementing the importance of your personal cybersecurity. Take advantage of these data protection and personal cybersecurity tips to safeguard your files and protect the data you care about most.
Use two-factor authentication
Two-factor authentication is a cybersecurity tool that you can use to add an extra layer of protection to personal and/or financial accounts viewed as valuable by cybercriminals. The use of biometrics like fingerprint scanning and facial recognition make impersonating a target incredibly challenging for even experienced hackers.
- Personal cybersecurity resolution: Take time to enable two-factor authentication on all online accounts with the capability to do so.
Create a guest network
Guest networks are excellent for protecting more vulnerable IoT devices in your home. They are separate Wi-Fi networks used for devices such as gaming consoles, speakers, and smart TVs — products known for being more susceptible to infection because of the less frequent security updates sent to hardware. This separation helps prevent the spread of malware to your primary network, which probably hosts devices with your more sensitive data.
- Personal cybersecurity resolution: Establish a guest Wi-Fi network for more vulnerable IoT devices and/or visiting friends and family.
Know the red flags of malware
Knowing what to look out for when it comes to suspicious activity can be a lifesaver. Here are some of the signs that you’ve potentially stumbled across a dangerous form of malware:
- Spam warnings: When browsing the web, warning notifications will likely pop up if you try to enter a site considered potentially dangerous to your device. Take these warnings seriously and avoid the website raising concerns.
- Unsecure connections: Secure websites will have “https://” located in the beginning of their URL. Those containing “http://” are not considered trustworthy domains for people to visit regularly.
- Redirects: Browser hijackers are cybercriminals known for embedding malware onto websites that automatically redirect victims to potentially harmful websites. If you come across this tactic, immediately close all the windows.
- Pop-ups: If you visit a webpage that generates a ton of unwanted pop-ups, this could be a sign hackers embedded malvertising or adware onto the site to attack online visitors.
Perform routine data backups
Data backups can be a saving grace when it comes to data loss or destruction. With duplicates secured on an external hard drive or cloud storage system, the likelihood of you losing important information because of a targeted cyberattack could go down significantly.
- Personal cybersecurity resolution: Make a consistent routine of backing up device data at least once a week.
Monitor credit reports and online accounts
Hackers often carry out their cybersecurity attacks in hopes of gaining access to financial information they can use for their own benefit. For that reason, it’s important to routinely check credit card and banking statements for unauthorized transactions. This could be an indicator that a cybercriminal succeeded in gaining access to the information stored on your network.
- Personal cybersecurity resolution: Regularly review monthly bank statements for unauthorized
purchases made on your account.
Device security and personal cybersecurity
Hackers have a passion for finding security flaws in the devices we use daily. Though having most of your information in front of you or in the palm of your hand is beyond convenient, these pieces of technology aren’t impervious to corruption. Within the last two years alone, macOS malware saw an increase of over 1,000%.
Consider the following cybersecurity tips to protect the data you keep stored on your beloved devices.
Operate mobile devices securely
With the average person spending between five and six hours on their phone a day, it’s important to know how to keep them—and other mobile devices—safe from cyberthreats. A few easy-to-use tips you apply today include:
- Enabling lock screens
- Creating complex PINs
- Avoiding third-party apps
- Performing system backups regularly
- Never sending PII via text or email
- Personal cybersecurity resolution: Review all devices and delete any old or lingering apps installed on your desktop or homescreen.
Enable automatic software updates
One of the best ways to mitigate the danger of cybersecurity attacks is by enabling automatic updates. Because hackers target systems and devices riddled with security flaws, having a system readily equipped with the latest security features can be a saving grace for your overall Cyber Safety. This takes the work out of reviewing all your devices — all you’ll need to do is just sit back, relax, and browse securely.
- Personal cybersecurity resolution: Set system preferences to allow security updates to take place automatically once available.
Avoid public Wi-Fi
Public Wi-Fi is not considered a secure internet connection. That’s because these networks often lack encryption, making your online activity trackable by others on the network, including hackers looking to potentially infect devices with different types of malware. If you do find yourself on public Wi-Fi, use a VPN to encrypt your activity. This gives you a kind of anonymity as you use your device.
- Personal cybersecurity resolution: Find a VPN you can utilize if you need to operate on a public Wi-Fi network.
Install antivirus and firewall protection
Antivirus software and smart firewalls are some of the most widely used methods to fend off cybercriminals and their malicious malware. With a watchful eye monitoring your devices and network activity, you’ll be able to browse securely without fear of a threat slipping past you.
- Personal cybersecurity resolution: Explore antivirus and firewall protection that will help fight against today’s cyberthreats.
Now that you have an understanding of the basics of personal cybersecurity, resolve to boost your own personal cybersecurity through 2022 and beyond. After all, no one’s going to fight harder to protect your data, devices, and online privacy more than you.

Cyber threats have evolved, and so have we.
Norton 360™ with LifeLock™, all-in-one, comprehensive protection against viruses, malware, identity theft, online tracking and much, much more.
Try Norton 360 with Lifelock.
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.





Want more?
Follow us for all the latest news, tips, and updates.